Reliable Cloud Platforms?
2019 has been filled with extensive outages from prominent cloud platforms including Google and AWS. These outages impacted huge numbers of end users and businesses. This resulted in a myriad of issues including missed opportunities and significant revenue loss.

With 2020 around the corner, it seems only natural that your company revisit the reliability of the infrastructure you have deployed in the public cloud.
Loss of Visibility and Accountability
It is inevitable that outages will happen. The critical question is how your company responds to an outage. Because you need to be accountable to your clients and end-users, you must have some level of control over your data. However, as data migrates into a shared cloud space, you lose visibility into its exact whereabouts, into the actual infrastructure that is supporting it. You are essentially losing control over your infrastructure.
If you are outsourcing your infrastructure, you are also outsourcing accountability. Your mission-critical data no longer lives in the server down the hall or in a nearby colocation facility. It is no longer monitored by people you can call by name, on the phone, or contact in the middle of the night. This loss of visibility and control has serious implications for businesses.
When an outage happens in the cloud, it can be exponentially more difficult to trace the source. Downtime can be much longer and costlier as a result. You may find yourself at the mercy of circumstances you cannot control or mitigate. This threatens your ability to be accountable to your clients and users.
Hybrid IT Option
Many companies today are born in the cloud but even for these companies there are some options that will maximize control, accountability and the ability to mitigate an inevitable outage. The solution lies in diversification or hybridization of one’s IT infrastructure. You can achieve this by adopting a hybrid IT or a multi-cloud strategy. A diversified approach allows you to achieve greater control and greater accountability as your company will no longer be outsourcing all of the accountability for your infrastructure.
When it makes sense to retain a significant amount of on-premises IT infrastructure, you can still improve the quality and efficiency of those operations by operating them as a private cloud.
Consider your options, most notably using Microsoft’s Azure Stack. By bringing consistent services on premises, you can run on your own hardware that meets its requirements. The benefit is that Azure is a proven platform with a vast ecosystem of third-party support and expertise available. If you don’t have the right skillset for Azure cloud, you may need help from outside experts.
The hybrid cloud is best defined as the combination of your public and private cloud assets, both on and off prem. A hybrid cloud is an effective way of hedging your bets on the big trends in technology. You may think a public cloud can do all you need for your organization. But, it is possible that some of the use cases for on-premises IT will take hold in your organization. A hybrid cloud environment gives you the resources, skillsets, processes, and tools to deploy new systems where they belong.
Contact Zunesis for an assessment on what strategy works best for you infrastructure.
HPE InfoSight
With the purchase of Nimble, HPE gained a great storage platform. It also gained the valuable asset of InfoSight. InfoSight is an AI-driven predictive analytics tool which enables customers to gain higher efficiency and reliability with smarter, easy to manage infrastructure. HPE InfoSight automatically predicts and resolves 86 percent of issues before a problem is identified.
Since that time, HPE has extended the InfoSight predictive analytics and recommendation capabilities to the HPE Server line This includes Proliant, Apollo and Synergy compute products.
Benefits
InfoSight will enable a smarter, self-monitoring infrastructure. This helps to drive down operating costs. It analyzes millions of sensors across the installed base across the globe. Using this data, it will provide trend insights, forecasting and recommendations, to predict and prevent problems.
HPE storage customers are already enjoying the benefits of HPE InfoSight. They are seeing operational costs decreased by as much as 79 percent. Trouble tickets are resolved in 85 percent less time. Above all, 86 percent of issues are automatically predicted and resolved before a problem is identified.
The Infrastructure for Servers will provide Global Visibility into the Server Infrastructure through the wellness monitoring dashboard. Predictive Analytics on parts failures, and recommendations based on patterns or signs of abnormality will be available to eliminate performance bottlenecks on servers.
Capabilities
A foundational set of capabilities that can be augmented over time has been delivered by the first release of HPE InfoSight for servers.
The Capabilities includes:
1) Predictive data analytics for parts failure
2) Data analytics for server security
2) Global Operational Dashboard with a consolidated view of the status, performance, and health of their server infrastructure. This includes system information, server warranty, and support status
4) Global Wellness Dashboard with a consolidated view of the health of the server infrastructure, including recommendations
5) Recommendations to eliminate performance bottlenecks on servers
6) Support for HPE ProLiant servers, HPE Synergy compute modules and HPE Apollo systems (Gen10, Gen9, and Gen8 with iLO 5 and iLO 4)
HPE Infosight improves the customers infrastructure management experience. When combined with HPE OneView, it can simplify the on-premises experience. HPE OneView provides compute lifecycle management and template driven infrastructure deployment. It transforms the infrastructure to software-defined. This allows customers to deploy infrastructure faster, simplify lifecycle operations and increase productivity.
How to Install
To start using HPE InfoSight for servers, you’ll need to download and install the iLO Amplifier Pack which serves as the aggregation point for the collection of the data for all of the servers. In addition, it passes the health, configuration, and performance data of each server to InfoSight. Should InfoSight need to take any action on the servers, InfoSight will communicate the action to iLO Amplifier Pack to perform the action.
Contact Zunesis to see how InfoSight can improve your current infrastructure.
Ransomware
In May 2017, the National Health Service of England and Scotland was hit with the largest ransomware attack at that time. The attack affected an estimated 200,000 computers across 150 countries. The estimated economic loss ranges from hundreds of millions to four billion dollars. This attack, dubbed the WannaCry ransomware attack, catapulted network security to the top of many organization’s priority list. It brought to light the amount of damage that could be done by a malicious virus.
What is Ransomware?
Ransomware is a type of malicious software, or malware. It is designed to deny access to a computer system or its data until a ransom is paid. It is typically spread through phishing emails or by visiting an infected website. The virus works by encrypting all the data on the user’s hard drive. Then, it requests a payment, usually in the form of cryptocurrency, to be sent to the hackers. However, there is no guarantee the user will recover their files if they pay that ransom.
Ransomware can be devastating for users and organizations. Currently, we are seeing a lot of government agencies, education organizations, and healthcare organizations targeted by these attacks.
What precautions can you take?
In order to protect your user’s and organization’s data, there are a number of precautions you can take. Most of which are best practice even without the threat of ransomware.
First, keep all applications and operating systems up to date. Outdated apps and OS’s are the target of most attacks. This was the case in the WannaCry attack.
Second, train users to avoid phishing emails. These are emails designed to look legitimate at first glance but have links that redirect you to an infected site, or attachments that download the malware directly. Phishing emails and sites are also associated with social engineering attacks designed to steal credentials. It is always a good idea to train users to never click on links or open attachments in unsolicited emails.
Next, backup your data on a regular basis. Backing up your data is a good idea for a myriad of reasons. It can really save you in the case of a ransomware attack. Best practice would be to keep 3 copies of your backups, with one offline and another in a geologically separate location. These backups should also be regularly tested.
A great way to control what is installed on your organization’s computers is access control. Restricting privileges may not allow malware to be installed on a system without an administrator’s approval. This will limit the spread of the malware through a network.
Similarly, another useful tool for fighting malware is a spam filter on your emails. A strong spam filter will prevent most phishing emails from making it to users’ inboxes. It will authenticate inbound emails to prevent spoofing.
What to do when you’ve been infected by ransomware
The first thing anyone should do when infected by ransomware is to contact law enforcement immediately. You should report the infection to the FBI’s cyber task forces and internet crime complaint center.
Currently, the FBI does not recommend paying any ransom. While it could cost organizations large sums of money to be down for any length of time, there is no guarantee that paying the ransom will restore your data. There are numerous cases of this happening. Some victims who have paid the ransom have even been targeted again. Other victims have even been asked to pay more after the original ransom to get all their data back. Paying may inadvertently encourage this criminal business model. This makes it more prevalent in the future.
Once you have found out that you are infected, you should isolate any infected machines immediately. In addition, one should take any unaffected machines offline so they don’t get infected. Same goes for backups. They should be taken offline immediately to stop the ransomware from spreading into your backups.
From there, you should follow your organization’s incident response plan. Follow any instruction given to you by law enforcement.
There will never be any way that you can guarantee you won’t fall victim to one of these attacks. Malware is always evolving, just like security practices are. It will always be an arms race between hackers and security experts. Your best bet is to always follow best security practices, and to always have a plan to recover from any successful attacks.
Where to report Activity
FBI
Internet Crime Complaint Center
United States Secret Service
Contact Zunesis to have an assessment done on your current infrastructure. Ask us about helpful hints to help keep your data secure.
New Ransomware Focus
Ransomware has a new focus. Recent studies and surveys report that ransomware attacks have sky rocketed against government agencies, public healthcare providers and schools in the first nine months of 2019.
A report published by Emsisoft noted that at least 68 state, county and municipal entities have been affected by ransomware attacks this year. In addition, at least 62 ransomware attacks have involved School Districts. Healthcare providers reported 491 ransomware attacks.
This report also cited the following trends in 2019:
- Cybercriminals Target MSPs: Cybercriminals are increasingly targeting software used by MSPs and other third-party service providers. They simultaneously attack service providers and their customers.
- Ransoms Are Increasing: Cybercriminals want to maximize their profits, and as such, are increasing their ransom requests.
- Cyber Insurance Drives Ransom Payments: Organizations that leverage cyber insurance are more prone than others to pay cybercriminals’ ransoms.
- Cybercriminals Prioritize Email and Remote Desktop Protocol(RDP): Emails and RDP attachments represent the top choices for cybercriminals to launch ransomware attacks.
Credibility & Sophistication
Ironically, Ransomware cybercriminals consistently operate with integrity by following through on their commitment to decipher encrypted data once a ransom is paid. These criminals understand that for their crimes to continue to be profitable, they must follow through and make the data available to their victims after they have received payments.
Local Governments and School Districts find themselves in a tough situation. They often are forced to rapidly make arrangements for the ransom payment because their IT systems completely stop working.
To ensure that their damage is inflicted, cyber-criminals are making their attacks more sophisticated. Today’s ransomware attacks often include “time delayed fuses”. These attacks are designed to infect not only an organization’s primary data storage but also their replicated data sets and backups. When an organization attempts to recover from a ransomware attack using their backup data, they soon find that their backup data is also infected and encrypted. As countermeasures against ransomware become increasingly sophisticated, so do the attacks.
The Voice of America: Ransomware Focus
A report just published by IBM Security-Morning Consult showed the following:
- 79% of Americans are concerned about the threat of ransomware to cities across the US. While 68% are concerned about the threat of ransomware to their specific city. 75% are worried about threats to their personal data.
- 56% of Americans would disapprove of their local government using tax dollars to pay a ransomware hacker. When given an explicit choice, 63% of respondents would prefer to pay higher repair costs and not pay a ransom rather than using taxpayer dollars to pay for a ransom.
- More than 50% of Americans would not be willing to pay additional taxes to protect their city, county, or town from ransomware attacks. Among those who are unwilling to pay additional taxes for cyber-security, respondents are split 50/50 on whether they would support cutting funding from other local priorities for cyber-security.
- Nearly half (49%) of the respondents view the Federal Government as having the greatest responsibility to protect cities from ransomware attacks. 22% seeing it as a state-level responsibility. 28% view it as the responsibility of the local Government.
These statistics explain the complexity that our civic leaders face when addressing the threat of ransomware. Public policy will evolve over time and likely make substantial progress as knowledge is gained. Unfortunately, the threat to our local governments and public institutions is very real today.
A Step in the Right Direction
Organizations of all sizes can take a meaningful first step to reduce their risk to ransomware. They need to assess their data backup and data protection policies. Having the right processes and technology in place will substantially lessen the risk of ransomware.
Zunesis specializes in helping organizations evaluate and assess their backup and data protection policies. This includes retention policies and “air gaps”. This is one step in providing greater overall security for Government agencies, schools and healthcare providers. Often considered to be the important first step.
Using Aruba Dynamic Segmentation will help keep the Boogeyman away
 One reality terrifying most business owners is the thought of someone compromising their network and their data. Companies spend gratuitous amounts of money and time to protect themselves from cyber threats. They configure edge firewalls and multi-factor authentication mechanisms to protect their most sensitive data in the cloud. The thing that is often left untouched and overlooked are the data ports which are physically accessible to the public.
One reality terrifying most business owners is the thought of someone compromising their network and their data. Companies spend gratuitous amounts of money and time to protect themselves from cyber threats. They configure edge firewalls and multi-factor authentication mechanisms to protect their most sensitive data in the cloud. The thing that is often left untouched and overlooked are the data ports which are physically accessible to the public.
If the business operates in a public or shared office space, the risk of intrusion from an unprotected or unmanaged port is astounding. Aruba Networks have developed a technology that can now extend the same role-based firewall policies that are applied to the enterprise wireless to the wired ports. By enforcing the same role-based policies, administrators can simplify the deployment and management while also staying consistent across the network.
Is this a new threat?
In truth, the threat has always existed. The difference is that now more than ever, IOT devices require a hard-wired connection to function. This is because many of them do not support the same security and encryption standards we enforce on the wireless network. Some devices simply require the low voltage power supplied from the switch port to function. These devices include security cameras, lighting controllers, intelligent HVAC devices and some printers or scanners.
Another common scenario is when there is a need for a wired port for a special event. The port is configured for one purpose but then it is forgotten about. Then, anyone who plugs into that port has whatever access it was originally configured for. The reality is that these devices and circumstances are not going away any time soon. The best way to protect the network and the switch ports is to secure and isolate the clients and the devices from your sensitive networks and services.
What have engineers and administrators done about this attack vector?
From a management perspective, port security has always been the bane of network engineers and administrators. It has never been very practical or scalable to deploy. One must define clear attributes to distinguish each device from another. Then, you tell the switch port to change the network the device it is connected to or to simply block the port all together.
Often the unique attributes used to distinguish these devices are easy to counterfeit. Deploying the configuration on only the public facing ports takes planning and insight. This often falls through the cracks after the initial deployment. Furthermore, the deployment of these settings must be done on each switch in the environment that may be connected to from a public facing port. Aruba’s Dynamic Segmentation takes a different approach. It unifies policy enforcement and delivers the same seamless experience that people come to expect of wireless connectivity.
How does it work?
The technology leverages many of the same security and profiling mechanisms that exists in the Aruba wireless world. It applies them to the switch port adding a scalable security solution without the complexities of deploying another costly security product. It works by treating an Aruba network switch like an access point. The switch tunnels the switch port traffic to the Aruba mobility controllers. It profiles the connected devices in the same manner it would a wireless client.
If the device passes certain authentication criteria, then it is granted the same access as if it were on the wireless network. If the device has certain attributes but does not pass specific authentication criteria, than it is treated differently. It will be assigned the same role and given the same privileges as it would on the wireless network. In isolating these devices or unknown users, we can better protect the environment at large while not limiting the connectivity some users may need.
What else can Aruba Dynamic Segmentation do?
By tunneling the traffic to the mobility controllers, Dynamic Segmentation provides greater visibility of the traffic from IOT devices and guests users on your network. You can enforce a captive portal with email registration for guest users. This can add some accountability to a visiting contractor or guest speaker.
If an employee brings in a consumer device from home and plugs it in, you can distinguish what the device is, where it is plugged in and what it is communicating with. The most valuable use-case for this technology lies in the constant struggle of BYOD and onboarding of employee devices. If an employee chooses to use their own computing device and company policy allows it, you can check the security posture of the device before granting it access to any resources on your network. Ideally those users would have a policy enforced that would allow them to reach only the least sensitive resources and the internet.
Why should network/security engineers and administrators be excited about Dynamic Segmentation?
Unlike traditional port security which normally rely on 802.1x and radius authentication to authorize access on a single VLAN, Dynamic Segmentation does not require unique network segments to be defined to physically separate users. Aruba uses the term VLAN sprawl to describe the never-ending creation of new VLANs and subnets to create new layer 2 boundaries to physically segment user and device traffic.
With this solution, all the unknown devices and users could reside on the same network segment. Because the traffic is tunneled, all the traffic is subject to deep packet inspection, stateful firewall policies, layer 7 application visibility including web content filtering. Most IT professionals usually wouldn’t believe that their wireless controllers are capable firewalls. They would be wrong where Aruba is concerned.
What Aruba components are necessary to make it all work?
If you are already an Aruba wireless customer, you may already have what it takes to start leveraging this technology today. Listed below are the solution ingredients directly from the Aruba Solution Overview.
- Aruba wireless access points
- Aruba network switches
- Models 2930F/M, 3810M, 5400zl2
- Aruba Gateways or Mobility Controllers
- Running AOS 8.1 or later
- Aruba Clearpass Policy Manager with profiling
Overall, the solution will simplify your efforts at securing the network edge and unifying security into one manageable platform. Why spend time configuring and deploying a solution that you would have to duplicate with the wireless infrastructure? Save yourself from that spooky nightmare.
To learn more, contact your local Zunesis sales representative.
Additional Resources
Dynamic Segmentation Solution Brief
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.
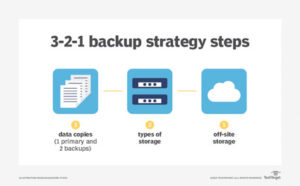
The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
Veeam Backup and Replication
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.

The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
REST for the Weary – RESTful APIs
As the expression goes, “no rest for the weary.” A lot of us in the IT industry can relate to that statement. We are often needing to work long hours with heavy workloads.
Why is it then, that at least in my observation, many systems and network engineers still have not jumped on the automation train? We’re so busy being busy, that we don’t take the time to save time. Some of us still think RESTful APIs are something that only “devs” use. Luckily for our sanity, many of us are picking up this much needed skill.
If you haven’t played with RESTful APIs yet, and are in IT operations, I highly encourage you to check out RESTful APIs and get some lab time. By sharing some personal experience, I’d like to argue that there really can be “REST for the weary.”(Pun intended)
A slightly better way
I remember before RESTful APIs were something that more vendors were supporting. I had to do write Expect scripts in Linux to do my automation. Really, this was just screen scraping terminal output and brute forcing automation. It was messy at best, especially trying to automate devices that weren’t made for automation.
This wasn’t a whole lot of fun, but it was worth the pain involved since it still saved mountains of time. There was quite a bit of pain with some vendors. They needed weird keystroke combinations before it would allow CLI access even after SSH’ing in. Implementing “CTRL+Y” through an SSH session via script was way more of a headache than you’d think it should be.
Complaining aside, spending time writing Expect scripts was certainly MUCH easier than doing things manually. As an example, in a large environment I previously worked in, my co-workers spent time manually SSH’ing to literally hundreds of switch stacks. They had to run some commands and capture output to save.
I was asked on a regular basis by management to get MAC address/switchport/dot1x info, and other data which could be queried for historical data in a database. This was in preparation for a forklift upgrade on the network. The use case was to get a history of devices, interface information, and all other relevant historical data. Pulling MACs from the cores via uplinks wouldn’t give necessary detail.
This wasn’t an option. We had to go to the switches as a source of truth. The idea was also to compare to data from other sources (the IP-PBX system was one example) in preparation for the upgrade. They wanted to make sure network cut-overs were un-noticed by end users, aside from the downtime to swap equipment of course. I spent quite a bit of time writing and tuning Expect scripts, but still much less than doing things the old fashioned way.
The actual better way
Fast forward to my next job managing literally thousands of server nodes in a high uptime environment. I started getting asked to do things like update BIOS settings ON EVERY SERVER. To make things worse, as software engineering changed their code, they’d ask me to change BIOS settings multiple times. There was no way I was going to iLO into every one of those servers, reboot, wait, press F9 to access system utilities, select BIOS/Platform configuration(RBSU)… etc. Thankfully, I didn’t have to draw a line in the sand and explain that I was unwilling to do this.
After some research, I learned that HPE makes a RESTful API available on their Gen9 and Gen10 servers. Lucky for me, we were using Gen9 servers at the time.
Managing BIOS settings isn’t the only thing you can do by the way. You could probably integrate this into your monitoring system if it allows, for non responsive devices as an example. We’ve all seen servers where the lights are on but nobody is home. They seem dead, but respond to pings…intermittently and with high latency. You could use your monitoring system to poll services, and metrics like CPU and RAM utilization. Then, reboot the server via iLO RESTful API, if it is really locked up. No more waiting for a human to notice alerts, escalate if needed, then reboot the server manually.
One Interface for Integrated Control
HPE Integrated Lights Out (iLO) server management provides intelligent remote control automation through scripting or an API. Gain even more capabilities that go beyond scripting by leveraging one API to manage your complete lifecycle of HPE Gen9 and Gen10 servers—iLO RESTful API.
A single API interface integrates server management components and full compute power. Use it with HPE iLO 4 and iLO 5 to perform remote server provisioning, configuration, inventory and monitoring to industry standards through Redfish API conformance.
This was a game changer. I was able to prepare some standard JSON files with standardized BIOS settings. Then, write a script utilizing HPE’s RESTful API, and push settings described in the JSON file to every server (or subset of servers for testing) with ease.
Some settings still required a reboot to take effect. This was easily handled by scheduled reboots during a maintenance window. I also didn’t need to patch together a solution to script iLO changes with the software equivalent of duct tape and bubble gum, but instead utilized a RESTful API. Something that would have taken FOREVER, was accomplished with ease using something very well documented by HPE.
Give it a try!
Ready to give RESTful APIs a chance on your HPE servers and Aruba networking? Check out these resources:
Not using RESTful API capable servers or networking? The seasoned professionals at Zunesis can assess your environment, and recommend an appropriate refresh path utilizing the latest Aruba networking equipment and Gen10 HPE servers.
2020 IT Budget Forecast
Spiceworks recently released their 2020 Spiceworks State of IT Report. They surveyed more than 1,000 technology buyers in companies across North America and Europe. The study focused on how organizations will be spending their technology budgets for next year.
According to their report, replacing outdated infrastructure will be the biggest IT spend next year. Most businesses are anticipating top-line revenue growth. As revenue grows, typically IT budgets increase as well.
What will be the key areas of focus in organizations’ 2020 IT Budget Forecast?
Other key findings include:
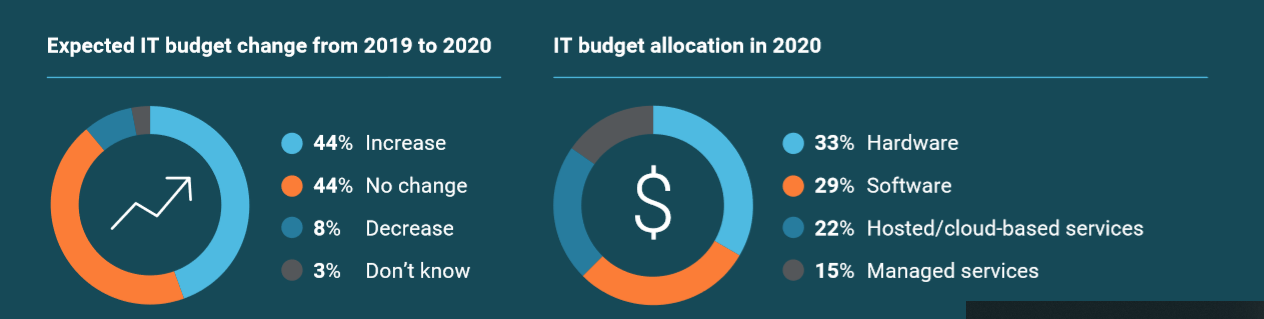
- IT BUDGET GROWTH : IT budgets rise as businesses replace outdated technology. 44% of businesses plan to increase tech spend in 2020 which is up from 38% in 2019.
- BUDGET DRIVERS: One in four enterprises (1,000+ employees) are increasing 2020 IT spend due to a recent security incident.
- EMERGING TECH TRENDS: Business adoption of AI-powered technologies is expected to triple by 2021, while adoption of edge computing is expected to double. Large enterprises are adopting emerging technologies 5 times faster than small businesses.
- FUTURE TECH IN THE WORKPLACE: Two-thirds of large enterprises (5,000+ employees) plan to deploy 5G technology by 2021.
88% of businesses expect IT budgets to either grow or stay steady over the next 12 months. Compared to 2019, we’re seeing more upward acceleration.
44% of businesses plan to grow IT budgets in 2020. This is an increase from 38% in 2019. Organizations that expect IT budget growth next year anticipate an 18% increase on average. Only 8% of companies expect IT budgets to decline in 2020.
Key Categories for IT Spend
These categories represent more than half of the total IT Spend in businesses today.
- Security: 7% of Total IT Budget Spend. Pain points include identifying the right solution for their needs and comparing multiple solutions.
- Collaboration and Communication: 6% of Total IT Spend. Paint points include finding the right solution and quantifying the business problem that is trying to be solved.
- End-User Hardware: 22% of Total IT Budget Spend.
- Server Technology: 9% of Total IT Budget Spend. Pain points include identifying the right solution and seeing if the purchase will require other system upgrades.
- Networking: 4% of Total IT Budget Spend.
- Storage and Backup: 10% of Total IT Budget Spend.
Top 5 IT Challenges Expected in 2020
Businesses are looking for technology vendors and service providers to be an additional tool in their arsenal. They need additional help to navigate through all the pain points out there.
These challenges include:
- Keeping IT infrastructure up to date
- Balancing IT Tasks and Improvement Projects
- Upgrading outdated software
- Following security best practices
- Convincing Business Leaders to Prioritize IT
Small businesses need more guidance than large enterprises when it comes to security best practices and maintaining disaster recovery policies. Whereas, enterprises will need more help with implementing new tech into their environment.
Future Tech
As for new tech adoptions, there are a few categories that are expected to be adopted by 2021. Enterprises with 5000+ employees will be the ones adopting these tech solutions first.
- AI Technology
- Hyperconverged Infrastructure
- Edge Computing
- 5G Technology
- Serverless Computing
- Blockchain Technology
In Conclusion
To summarize, the results show a healthy global economy. Aging technology in the workplace and more sophisticated security threats has IT spending up year-over-year.
We at Zunesis, are prepared to assist you with your 2020 technology initiatives. From assessments to support and more, schedule a meeting with Zunesis to discuss how we can help you reach your technology goals.
What is Synergy?
HPE Synergy is the next generation server architecture replacing the highly successful C7000. It is a software-defined solution that enables you to compose fluid pools of physical and virtual compute, storage, and fabric resources into any configuration for any workload. It allows for a quick deployment through a single interface, which creates efficiency and allows you more control.
What Are People Saying?
IT professionals often struggle with old technology that cannot fit all of the dynamic organizational needs of their company. Along with ease of deployment, valuable features of the Synergy solution include effortless management and integration with OneView. OneView allows everything to be managed on one dashboard.
Synergy gives you more control over firmware and how physical servers are managed, along with providing online firmware updates, which minimizes windows downtime.
Check out the latest technology refreshes for Synergy in this video from HPE Discover:
Benefits
With the ever-growing need for more bandwidth, Synergy midplane offers a bandwidth of over 16Tbps. The latest C7000 midplane is only capable of 7Tbps of bandwidth. Above all, this is three times the bandwidth from each compute node when compared to BladeSystem. It can support 100Gbit Ethernet and beyond, technology that the C7000 is not capable of supporting.
The Photonics-ready solution (able to support network bandwidth requirements well into the future as they’re developed) offers up to 200 drives (HDD and SSD) of storage. These drives can be allocated, as needed, individually to compute nodes within the same Frame. A second option is pooled, to allow the storage to be shared by other Frames.
Covering up to 60 blades, this solution allows two VC modules (plus satellites). This provides network virtualization for up to five Synergy Frames. Whereas before, two modules were needed in every blade enclosure, covering only 16 blades.
Money Talks
Synergy has been known to reduce IT Infrastructure costs by as much as 50%. When you consider the capacity enhancement, the time it takes to deploy this solution, and simple management component, the transition is a no-brainer!
In addition, a recent IDC analysis showed that organizations will realize value with HPE Synergy. The value will translate into more than a three-to-one return on their investment (223% five-year ROI).
Get Moving with Synergy
If you would like to learn more about Synergy and how it can add value to your IT infrastructure, please reach out to Zunesis to schedule an appointment.




