Zunesis Honored on the 2023 CRN Tech Elite 250 List
Englewood, Colorado — Zunesis, announced that CRN, a brand of The Channel Company, has honored Zunesis on its 2023 Tech Elite 250 list.
This annual list features solution providers of all sizes across the U.S and Canada that have differentiated themselves by achieving the highest level and largest breadth of certifications and specializations from key technology vendors in the infrastructure, cloud, and security spaces.
 Businesses rely on solution providers to maintain the highest levels of technical prowess across critical products and services to help them meet today’s IT challenges and take advantage of the benefits of cutting-edge solutions. To meet these demands, solution providers such as strategic service providers, systems integrators, managed service providers and value-added resellers strive to maintain high levels of training and certification from IT vendors and achieve the highest tiers within those vendors’ partner programs.
Businesses rely on solution providers to maintain the highest levels of technical prowess across critical products and services to help them meet today’s IT challenges and take advantage of the benefits of cutting-edge solutions. To meet these demands, solution providers such as strategic service providers, systems integrators, managed service providers and value-added resellers strive to maintain high levels of training and certification from IT vendors and achieve the highest tiers within those vendors’ partner programs.
“CRN’s Tech Elite 250 list features the leading solution providers in the IT channel with the most in-depth technical knowledge, expertise, and certifications for providing the highest level of service for their customers,” said Blaine Raddon, CEO of The Channel Company. “These solution providers have continued to extend their aptitudes and abilities across various technologies and IT practices, demonstrating their commitment and value to their customers.
Coverage of the Tech Elite 250 will be featured in the April issue of CRN Magazine and online at www.CRN.com/techelite250.
About Zunesis
Zunesis can help your organization compete in the digital economy with infrastructure transformation aligned to your business goals. We have more than 18 years of experience serving customers throughout the Rocky Mountain Region and Southwestern U.S., including Colorado, Montana, Wyoming, and Nevada. Our staff of solution architects have decades of expertise and in-depth product knowledge to customize IT solutions with success. www.zunesis.com
Follow Zunesis: Twitter, LinkedIn, and Facebook.
Zunesis Contact:
Rachael Stiedemann
Zunesis
rachael.stiedemann@zunesis.com
About The Channel Company
The Channel Company enables breakthrough IT channel performance with our dominant media, engaging events, expert consulting and education, and innovative marketing services and platforms. As the channel catalyst, we connect and empower technology suppliers, solution providers, and end users. Backed by more than 40 years of unequalled channel experience, we draw from our deep knowledge to envision innovative new solutions for ever-evolving challenges in the technology marketplace. www.thechannelcompany.com
Follow The Channel Company: Twitter, LinkedIn, and Facebook.
© 2023. CRN is a registered trademark of The Channel Company, LLC. All rights reserved.
The Channel Company Contact:
Natalie Lewis
The Channel Company
Artificial Intelligence (AI) is revolutionizing the world of storage and data management at an unprecedented pace. This emerging technology is not only streamlining the way organizations store, process, and manage enormous volumes of data, but it’s also significantly improving the insights gleaned from this information. Offering advanced algorithms and machine learning capabilities, AI is powering the future of storage and data management—and is expected to transform the way businesses handle and use their data.
Here are six ways AI is changing the game:
- Improved data analysis: By identifying intricate patterns and trends in large datasets, AI improves the accuracy and speed of data analysis, leading to quicker and more precise insights. With this higher caliber of insights, you can make quick, well-informed decisions that align with your business goals and support profitability and growth.
- Predictive maintenance: With the ability to analyze historical data and real-time usage patterns, AI algorithms can be used to predict when equipment failures are likely to occur and proactively flag them to the right people, mitigating the risk of expensive downtime and devastating data loss.
- Intelligent data storage: AI can analyze data usage patterns and automatically move less frequently accessed data to more cost-effective storage tiers. It also makes it easy for you to quickly locate specific data by indexing and tagging information for easy search and retrieval. With critical data that’s readily available and accessible when you need it, AI technology powers more efficient operations, better resource allocation, and more informed decisions.
- Better data security: With the ability to identify potential threats and anomalies in data usage patterns, AI technology allows you to take immediate action to prevent major security breaches. Additionally, using AI-driven encryption methods, you can ensure your sensitive data is protected both at rest and in transit, making it infinitely more difficult for hackers to access or steal important information.
- Automated routine tasks: With the ability to automate routine data management tasks, AI can streamline workflows, minimize processing time, reduce human error, and enhance the overall efficiency of data management processes, ultimately leading to cost savings and increased productivity.
- Enhanced disaster recovery: AI not only automates backup and recovery processes, but it can also identify potential risks and vulnerabilities and deliver real-time alerts and notifications in the event of an outage or data loss. With a higher degree of control and reliability in your disaster recovery efforts, your business can recover from disasters more quickly to reduce the impact of unexpected events, improve business continuity, and ensure critical operations can be resumed quickly.
Harnessing the Potential of AI-Driven Storage
As organizations generate and store ever-increasing amounts of data, AI will continue to play a crucial role in helping businesses manage and utilize that data to drive innovation, optimize operations, and make data-driven decisions that fuel growth.
Hewlett Packard Enterprise (HPE), with solutions like HPE InfoSight, is leading the charge in harnessing the potential of AI-driven storage and data management technologies. At Zunesis, we are committed to helping you capitalize on HPE’s AI-powered solutions to ensure a seamless, optimized, and forward-thinking data management strategy tailored to your specific needs and objectives.
For more information about how to transform your storage and data management processes with HPE powered by AI, contact us here.
In today’s digitally driven world, businesses are becoming increasingly reliant on network connectivity to operate effectively. But with increased connectivity also comes increased risk exposure. Cyberattacks are on the rise, and more businesses are succumbing to security breaches, data loss, and other security-related issues. In fact, cybercrime damages are expected to reach $10.5 trillion by 2025.
Your ability to protect your network from cyberattacks and unauthorized access while maintaining network performance and compliance with regulatory requirements is not a nice-to-have—it’s essential. With a Network Access Control (NAC) system in place, you can safeguard your network infrastructure and your data while maintaining business continuity.
5 Reasons to Implement a Network Access Control System
NAC is a security solution that restricts access to network resources based on users’ identities, roles, and devices. Today, more businesses are turning to NAC solutions, and here’s why:
- Improve security: Cyberattacks are a significant threat to businesses of all sizes. Cyber hackers are always looking for new vulnerabilities that make it easy to install malware, access sensitive data, and disrupt business operations. By preventing unauthorized access to your network to protect sensitive data and prevent malicious attacks, network access control systems provide an added layer of security for greater peace of mind. NAC systems can also be used to enforce security policies that ensure only authorized users can access the network. Even if a cyber hacker gets through one layer of security, they will be faced with additional security measures that make it infinitely more difficult to launch an attack.
- Comply with regulatory requirements: Many industries have strict data protection and privacy regulatory requirements—and failure to comply can result in lofty fines and a tarnished reputation. NAC systems enforce security policies that restrict access to the network based on predefined rules, ensuring only authorized users and devices can access the network. Plus, with the ability to deliver greater visibility and control over all devices that connect to the network, NAS makes it easy for you to monitor and manage the access of devices across the network—and automatically remove a non-compliant or malicious device. And with simpler auditing and reporting capabilities, NAS also simplifies auditing and reporting to support various regulations and standards.
- Improve performance: Offering a secure and efficient network environment, NAC solutions can help businesses optimize network performance and productivity. As network traffic increases, its performance can take a hit, disrupting operations. By reducing the number of unauthorized devices that connect to the network and ensuring critical business traffic receives priority over non-critical traffic, NAC solutions help to reduce network congestion to boost performance. And with the ability to identify and address issues with connected devices before they create a problem, NAC also improves uptime.
- Simplify network management: NAC solutions offer a centralized approach to network security, making it easy for administrators to easily control and monitor access to the network and enforce security policies. By automating the process of identifying and authenticating users and devices, NAC eliminates the need for manual configuration and management of network devices, which minimizes the risk of human error, reduces the workload on IT teams, and improves overall network security.
- Boost productivity: NAC solutions ensure only authorized users can access the resources they need, which reduces the risk of data breaches and other security incidents that can lead to network downtime and lost productivity. By providing visibility into all devices that connect to the network, your IT team can quickly resolve issues and enforce security policies, which allows employees to work with confidence and without interruption.
By implementing an NAC system, your IT team can ensure the network is secure, reliable, and always available, while supporting regulatory compliance, network management, and network performance.
At Zunesis, we can help you protect your network infrastructure, safeguard sensitive data, and maintain business continuity with ClearPass from Aruba, a leading provider of NAC solutions that help businesses secure their network infrastructure while ensuring compliance with regulatory requirements. Providing robust network access control with granular role-based policies for authentication, authorization, continuous monitoring and enforcement, Aruba ClearPass gives you anywhere, anytime connectivity while supporting simplified network security operations and enforcing security policies.
Downtime costs businesses an average of $84,650 per hour. A natural disaster or cyber-attack can result in weeks of downtime for a business that’s not prepared, delivering a massive financial blow. Even worse, according to the Federal Emergency Management Agency, 40% of small and mid-sized businesses never reopen after a natural disaster, and an additional 25% reopen but fail within a year. These statistics are staggering—and sadly, we’ve seen scenarios like these play out many times with our clients.
The threat of man-made and natural catastrophes is real—and in most cases, it’s something you can’t control. What you can control, however, are the safeguards you have in place to help your business recover when disaster strikes.
Enter Disaster Recovery-as-a-Service (DRaaS).
DRaaS is a pay-as-you go cloud service model that delivers backup services in a managed data center to ensure access and functionality to IT infrastructure after a disaster. It gives an organization a total system backup for rapid restoration of data servers and applications in the event of system failure. By replicating and backing up all cloud data and applications, DRaaS protects data, limits downtime, and shortens Recovery Point Objectives (RPOs) when a disaster happens.
7 Benefits of Disaster Recovery-as-a-Service:
- Cost savings: According to Gartner, 55% to 65% of I&O leaders say they overspend in backup and recovery by at least 30%. With DRaaS, you get the same capabilities and reliability as the more costly on-premise DR systems, but in a pay-as-you-go model whereby you only pay for what you use. Plus, with the ability to rapidly recover from a disaster, you stand to save your business hundreds of thousands of dollars—or more—from unplanned downtime or lost data.
- Immediate recovery: The longer it takes for your business to recover following a disaster, the more money your business will lose. By backing up your data to a secondary infrastructure, DRaaS offers instantaneous failover, so your business can return to normal operations within minutes—not hours or weeks.
- Secure data backup storage: DRaaS offers a multi-layer security approach designed to address most vulnerabilities. Employing the latest security protocols, with frequent patches, multi-factor authentication, encryption, ongoing audits, and more, DRaaS providers ensure comprehensive data security.
- Peace of mind: With redundancy for all your critical business information systems, DRaaS eliminates the worry and pressures associated with meeting recovery point objectives (RPO) and recovery time objectives (RTO), while helping you stay GDPR compliant.
- Reduced administrative burden: Managing disaster recovery eats up a lot of time for your internal staff—and keeps them in react mode. By outsourcing your disaster recovery to a third-party provider who will manage all DR planning and maintenance activities, you free up internal staff to proactively focus on other critical IT functions, achieve greater levels of productivity, and realize greater efficiencies.
- Specialized expertise: A DRaaS provider has advanced expertise in backup, recovery, and data security. With access to a team who knows everything there is to know about implementation, replication, failover, and more, you can unload a heavy and complex burden while letting the experts do what they do best.
- Scale on demand: Because you only pay for what you use, not only do you avoid overprovisioning for an in-house solution, but you also get the flexibility to scale up or down as needed. If your needs grow, you can quickly, easily, and efficiently upgrade your service
At Zunesis, we can help you achieve modern data protection with HPE GreenLake for data protection. Ask us about how your company can install a free trial of HPE Greenlake backup and recovery.
For more information about HPE’s industry-leading backup, recovery, and ransomware protection capabilities, contact us today.
According to IDC research, businesses are prioritizing resiliency and agility as foundational elements of their IT strategy. They want more visibility, cross-platform control, better data management, and protection from the edge to the core. While consumption-based models are playing an increasingly important role in powering those goals to accelerate digital transformation, many business leaders are hesitant when it comes to Network-as-a-Service (NaaS). Some still think of as-a-service in terms of software, compute, and storage. However, as budgets grow tighter amid an inflationary economic environment, organizations need a better way to predict the ebbs and flows of the network, with flexibility to adapt as business needs change. That’s where NaaS comes into play.
Among the newest as-a-service approaches, NaaS combines hardware, software, services, and support in a pay-as-you-go model that delivers network services on a subscription basis. Allowing users to consume network infrastructure through flexible OpEx subscriptions, NaaS helps businesses shift their focus from managing their architecture to driving business outcomes.
If you haven’t transitioned to Network-as-a-Service yet, here are five reasons why you should:
- Cost savings: Network-as-a-Service allows you to acquire the network you need, when you need it, to avoid overprovisioning—in a pay-as-you-go OpEx model. Because you’re not locked into expensive infrastructure and rigid contracts, Naas allows you to more predictably manage costs and align budgets to business priorities. Additionally, with insights into all aspects of usage, including power, capacity, bandwidth speeds, and service levels, you can make more profitable financial decisions about workloads and upcoming projects.
- Security: As the prevalence of data breeches and ransomware continues to soar, enhancing network security is crucial. With proactive network monitoring, preventative maintenance, and real-time insights into network performance, the NaaS model offers enhanced network infrastructure protection with enterprise-grade security. With that, any nefarious activity can be immediately identified—and patches can be applied to address the breech before it becomes a problem.
- Performance and Productivity: Network-as-a-Service ensures your network operates efficiently by assessing traffic volume and making necessary adjustments. A better performing network means less downtime and greater staff productivity. Additionally, by outsourcing the full lifecycle of your enterprise network deployment, day-to-day operational management, upgrades, monitoring and troubleshooting activities to a NaaS partner, you free up your internal IT resources to focus on business-enabling tasks that add measurable value.
- Keep up with the pace of business: NaaS provides the financial flexibility to shorten planning cycle times and the agility to keep pace with changing conditions. By ensuring your network technology is refreshed as needed to support new workloads and changing requirements, a NaaS model makes it easy to scale your network as needs change.
- Environmental impact – NaaS offers a more sustainable way to consume network technology. With the ability to rent sustainable networks from a NaaS provider on a subscription basis, you don’t have to worry about where and how to dispose of old equipment. Plus, NaaS providers are committed to sustainable ‘reuse and retirement’ practices—and also well versed at configuring networks that are purpose-built to optimize energy consumption. By turning to a NaaS solution, you are making an environmentally sound decision that reduces your carbon footprint.
As market conditions continue to change at a rapid clip, your business needs to be one step ahead of your competition. With NaaS solutions from Aruba, Zunesis can help you move from reactive network management to a proactive approach that uses the network to deliver innovation and power profound business outcomes.
For more information about how you can accelerate business outcomes with Aruba’s subscription-based network consumption model, contact us here.
Securing or Hardening
Securing or Hardening aims to protect and secure your IT infrastructure against cyberattacks by reducing the attack surface. The attack surface is all the different points where an attacker can to attempt to gain access or damage the equipment. This blog is focused on securing Servers and storage.
The goal of server hardening is to remove all unnecessary components and access in order to maximize security. This is easiest when a server performs a single function. For example, a web server needs to be visible to the internet whereas a database server needs to be more protected. It will often be visible only to the web servers or application servers and not directly connected to the internet.
If a single server is providing multiple functions, there may be a conflict of security requirements. It is best practice not to mix application functions on the same server.
Implementing Hardening Policies
The information below provides a starting point for implementing hardening policies. Some of these only apply to the servers, but others apply to all devices on the network (Servers, Storage, Networking).
All Devices:
- Change default credentials and remove (or disable) default accounts – before connecting the server to the network.
- Disable guest accounts, setup accounts and vendor accounts (Vendor accounts can be enabled when necessary).
- Install security patches and firmware updates on a scheduled basis. My recommendation is to review devices firmware, virtualization layer software, and operating systems a minimum of every 6 months. If possible, review them every quarter.
- If possible, sign up for service update notifications from all vendors. You will be notified of critical updates. Depending on the update, Critical Security updates may require immediate implementation.
- Develop a patch/firmware management process that includes what gets updated, when it gets updated, outage window required, can it be automated, process for patching/firmware upgrade, etc. Some devices may be updated quarterly, others monthly.
- Accurate time keeping is essential for some security protocols to work effectively. Configure NTP servers to ensure all servers, storage and network devices share the same timestamp. It is much harder to investigate security or operational issues if the logs on each device are not synchronized.
- Ensure all devices are located in a physically secured location and restricted to approved staff only. Review and disable access for anyone that has left or changed roles.
- Review user and administrator level access to all devices. Ensure all default userids and passwords have been changed. Remove all users that are not on the approved list. If possible, use roles-based access using Active Directory or the equivalent.
- For connection to all devices, use Secure Shell Protocol (or SSH) when possible. This enables you to make a secure connection to your network services over an unsecured network. Avoid using FTP, Telnet and rsh commands. Use a secured protocol.
Servers:
- Turn off services that are not required – this includes scripts, drivers, features, subsystems, file systems, and unnecessary web services. Remove all unnecessary software.
- On Windows systems only activate the Roles and Features required for that host to function correctly.
- On Linux systems remove packages that are not required and disable daemons that are not required.
- Remote Access (Windows RDP) is one of the most attacked subsystems on the internet – ideally only make it available within a VPN and not published directly to the internet. For Linux systems, remote access is usually using SSH. Configure SSH to whitelist permitted IP addresses that can connect and disable remote login for root.
- Configure operating system and application logging so that logs are captured and preserved. Consider an SIEM Solution to centralize and manage the event logs from across your network.
- Review Administrator Access to host operating systems. Administrator accounts should only be used when required by approved personnel.
- Set password settings to require “Strong and Unique” passwords. Force password changes periodically according to internal security practices (usually 30 to 90 days).
- Configure account lockout policies. Lockout user accounts after failed attempts.
- Consider using Multi-Factor Authentication (MFA) if feasible to improve the level of security.
- Review backup policies to ensure all servers are being backed up correctly according to company retention policies. Periodically test the backup to be sure recovery is possible.
- Review monitoring requirements and be aware of any activity on each system.
- Set up custom admin accounts. They can be an Active Directory (AD) account or a local account in the administrators group.
- Limit security context on accounts used for running services. By default, these are Network Service, Local System, or Local Service accounts. For sensitive application and user services, set up accounts for each service and limit privileges to the minimum required for each service. This limits the ability for privilege escalation and lateral movement.
- For Linux systems, use Secure Shell Protocol (or SSH) when possible. This enables you to make a secure connection to your network services over an unsecured network. Use a secured protocol.
- Enable UEFI Secure Boot will further ensure only trusted binaries are loaded during boot.
- If not in use, disable the IPv6 protocol to decrease the attack surface.
- Keep partitions separated can help decrease the radius of any attack. Separate the boot partition from the user data and application data will help protect your data.
Contact Zunesis today if you would like more information on hardening your infrastructure.
It’s that item on your to do list that you often ignore and say you will do later – software updates. Not only may you be missing out on the latest improvements, but you can create a major security risk for your organization by ignoring these updates.
One of the largest data breaches on record is the Equifax data breach in 2017. It exposed the personal information of 147 million people. Hackers were able to get in due to a known system vulnerability for which a security patch had been issued two months before the breach. Unfortunately, no one at Equifax applied the patch. It cost the company $700 million in a settlement reached with the FTC.
60% of data breaches in 2019
were the result of unpatched vulnerabilities.
Before you get distracted by another project or think that you can wait to do your next update, here are a few reasons why software updates matter.
Security
Security is the number one reason to make sure you take care of updates as soon as possible. Software vulnerabilities often give cyber criminals access to one’s computer and plant malware. Malware enables one to take control of computers and steal information. It also can encrypt files, documents and other programs so they are unusable. Security patches block these open doors in the software to protect a device from attacks.
Risks from third-party vendors account for over two-thirds of all data breaches today. Third-party applications often interact with the internet. This makes them highly vulnerable to ransomware. Hackers know companies often overlook updating various programs that don’t seem important.
Cybercriminals want to exploit the most vulnerabilities as possible simultaneously. They are constantly searching for popular third-party programs. They will jump on an opportunity to hack millions of users who delayed updating their software.
New Features
On a positive side, software updates can give you access to the latest improvements and remove the old ones that are out of date. A software program may get a new shot of stability — no more crashing. Or an update might boost program performance — more speed. Some of these new features could save you time and most importantly enable the software to keep working and not shut down.
Protect Your Data
Your Data is your most valuable asset at any organization. Often hackers will search for personal data such as financial information, passwords, usernames or other documents with sensitive information. They will look to sell this information to the dark web and commit crimes. Allowing your customer’s information to be vulnerable can impact your company’s reputation and future business.
Improve Performance
Just like your vehicle needs regular maintenance to help improve its performance, your software can benefit from updates. Bugs are often found in programs or enhancements are made to improve the overall experience.
Ensure Compatability
With technology constantly changing, often older software will not be compatible with new technologies without the appropriate update. Microsoft, Google and Apple are frequently updating their technology interfaces. Most of us use multiple devices so compatibility is essential.
Don’t Fall for Fake Update Messages
It important to update your software but beware of fake messages or popups out there. Pop-ups are typically a scam to get you to click somewhere that you should not. Close the pop-up and go directly to the vendor website to look for downloads. There a suspicious emails making their rounds stating that your updates are past due and make an update now. It is best to reach out to the vendor directly.
You may have the option with some software to do automatic updates. Some software makes it possible to choose the time of day you update or even how often. Scheduling and automating your updates this way will make them less of a nuisance.
Take Time to Update
Like ignoring the check engine light on your car is something you shouldn’t do, the same goes for software updates. They can help protect personal information as well as company data. Contact Zunesis to find out more about how we can help.
Keeping on topic with how our country is fairing, I thought I would touch on one of the many elephants in the room that often goes unnoticed or is ‘conveniently’ forgotten about. That elephant is named Disaster Recovery, and an organization might be called a ‘Dumbo’ if they don’t have a Disaster Recovery Plan in place.
What Constitutes a Disaster?
First, what constitutes a disaster in the IT world? A disaster in the IT world is defined by many different categories:
- Natural Disasters
- Hardware Error / Thefts
- Virus / Malware Attacks
- On-site Disaster (i.e. fire)
- Power Outages
- Server Room Environment Issues (i.e. Air conditioner breaks)
- Unexpected Updates and Patches
- Human Error
All of the above seem to be happening on a daily basis. The question is no longer if this is going to happen to an organization, it’s WHEN is it going to happen to an organization? There’s plenty of natural disasters all year long, and they seem to continue to increase in severity.
Thieves are getting more and more creative and are constantly thinking of innovative ways of hacking into even some of the most fortified infrastructures. Just ask Epsilon, Facebook, Sony, Yahoo, etc. Ransomware is nerve-racking to say the least. An organization could shell out hundreds, if not millions of dollars on the hope of possibly getting data back. Talk about a gamble! You’d have better luck at the Blackjack table. Power Outages seem to be more frequent now than ever. Rolling blackouts seems to be the trend in many states, and it’s only mid-June!
And, then there is the human race and our ability to be create a cataclysmic mistake because he or she might have been having a bad day. We’ve all been there, and we all know that sometimes the slightest little thing will set us off and put a constraint on our ability to focus on the smallest of details. Even worse, there are many times where an organization knows they need to do something as soon as possible, but instead they try to wish it away or the problem will go away by itself. Disasters are like a Cancer; they aren’t going away unless treated.
These stats from Markel Insurance Company are shocking and should open some eyes.

Steps to a Disaster Recovery Plan
Now, I am not here to sell insurance to you, but to create more awareness out there that if an organization doesn’t have a plan in place, many will be filing unemployment WHEN that day happens.
Before that plan is created, it may be a good idea to have an overall Disaster Recovery Assessment which will look at a company’s Server, Storage and Network Infrastructure. What usually happens is that a specialized Engineer will be onsite and also remote-in to a specific infrastructure and document the existing environment. From that environment, an Engineer will provide recommendations based on best practices and a ballpark figure of what it’s going to cost to make sure that the Disaster Recovery Plan will minimize the pain from the actual disaster as much as possible.
There are some organizations out there whose pride is bigger than their brains. Don’t let ego get in the way and be a know-it-all. The reality is that organizations don’t know-it-all. Employees have been doing the work of two or three people since the early 2000s. This Disaster Recovery Plan should not be added to their list of daily duties. Swallow the pride and get a team out there who specializes in Disaster Recovery. They know what to look for, ask the right questions, uncover a weakness or threat that has gone unnoticed and may even reduce the risk of a disaster that was right around the corner.
I am not an alarmist, but a realist. It’s going to happen to every organization. How prepared are you if it happens tomorrow? Good luck sleeping with that floating around in your head tonight. Contact Zunesis for an assessment of your current environment and for recommendations on Disaster Recovery solutions.
A Brief History of Workplace Changes
How many changes or transformations has IT undergone in the past decade?
- Evolution of the World Wide Web – from JavaScript to Squarespace.
- Virtualization brings on consolidation.
- AI and machine learning.
- Big Data becoming bigger and faster.
- Centralized model vs decentralized model vs Cloud model.
- Cloud, cloud, cloud.
Microsoft’s Workplace Change
Business has been historically transacted in the traditional sense, on premises offices, on premises staff, and on premises infrastructure (both hardware and software). Sure, there have always been the need for remote users, but always the outlier. Business has strived for collaboration. This was typically done again through on premises means: a conference room, a white board, face to face communication, and that old dinosaur, the printer.
In 2017, Microsoft launched an initiative to achieve a mission of empowering every person and every organization on the planet to achieve more. To accomplish this mission, they decided they would need to transform the way they do IT. Microsoft had operated like a traditional IT shop, highly reactive to circumstances and more focused on the technology and the experience. The team transformed to be “vision-led” focused on building and deploying the right solutions to meet the needs of people, not just deploying the latest technology.
“That transformation culminated with our transition to becoming Microsoft Digital Employee Experience. At the core of that transformation is an obsession with the needs of our employees that transcends tools and infrastructure and extends to the entirety of their daily experience, from the day they’re hired to their eventual retirement. We steward their digital experience through every dimension of their employment, ensuring they have the devices, applications, services, and infrastructure needed to be productive on the job no matter where they are or what they do.” (Microsoft, 2022)
From that experience, Microsoft introduced The Modern Workplace in 2018. Virtualizing the workplace utilizing Microsoft 365, and other online work platforms that provide all the applications, storage, and communication solutions a team needs to get their work done from wherever they have an internet connection.
Then, not a foreign concept but definitely not mainstream.
Enter the pandemic.
Now, a very mainstream concept, in fact, most every organization on the planet is already there or trying to figure out how to get there. The pandemic was a massive shove for the technology world, a shock to the system which required immediate access for teams to get their work done from wherever they have an internet connection – the very definition of Microsoft’s Modern Workplace. One great example of this shove was Microsoft Teams – the ability to have a meeting and collaborate from anywhere with a connection. Many a business were able to get through the pandemic with the help of Microsoft Teams.
What is The Modern Workplace?
As previously stated, the Microsoft Modern Workplace is made up of online platforms which provide applications, storage, and communications to provide the employees they need to be successful. These tools reside within Microsoft 365 and Microsoft Azure. For this blog, we are focusing on Microsoft 365.
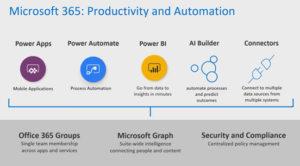
Microsoft 365 can be broken down into two segments: Communication and Collaboration; and Productivity and Automation.
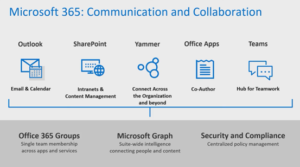
Communication and Collaboration products are best known by their common names: Exchange Online, SharePoint Online, Office Suite (Word, Excel, PowerPoint, etc.) and Teams.
Productivity and Automation products are best known by the Power Suite (Power Apps, Power Automate, and PowerBI).
Both groups riding atop Office 365 Groups, Microsoft Graph, and Security and Compliance.
Microsoft Modern Workplace Licensing
Navigating Microsoft licensing can be a very daunting task. Organizations are often unsure of where to begin when going through the licensing options. Achieving the Modern Workplace comes in many different shapes and sizes, and most of the time there are different licensing options for each.
Most case studies referenced by Microsoft share the same beginning steps. 1. Establish anywhere working and collaboration and 2. Microsoft Teams. Step 1 is usually Office/Microsoft 365 and Step 2 is self-explanatory, Microsoft Teams.
Now the trick is figuring those out:
Microsoft 365 Business Premium
-
- For SMBs 1-300 employees
- Apps
- Outlook, Word, Excel, PowerPoint, OneNote
- OneDrive (1 TB storage per user)
- Teams
- Services
- Exchange Online
- SharePoint Online
- Additional
- Intune
- Microsoft Defender
- Azure Information Protection
- Azure AD Premium P1
- Azure Virtual Desktop
Office 365 E3
-
- Unlimited number of employees
- Apps
- Outlook, Word, Excel, PowerPoint, OneNote
- OneDrive (1 TB storage per user)
- Teams
- Services
- Exchange Online
- SharePoint Online
Office 365 E5
-
- Everything included with Office 365 E3 plus:
- Microsoft Teams Phone System
- Power BI Pro
- Cloud 365 App Security
- Audio Conferencing
- Microsoft Defender for Office 365 Plan 2
- Advanced compliance
- Everything included with Office 365 E3 plus:
Microsoft 365 E3
-
- Unlimited number of employees
- Apps
- Outlook, Word, Excel, PowerPoint, OneNote
- OneDrive (1 TB storage per user)
- Teams
- Services
- Exchange Online
- SharePoint Online
- Additional
- Intune
- Microsoft Defender
- Azure Information Protection
- Azure AD Premium P1
- Azure Virtual Desktop
- Power Apps for 365
- OneDrive for Work
- Endpoint Configuration Manager
- Many more
Microsoft 365 E5
-
- Everything included with Microsoft 365 E3 plus:
- Microsoft Teams Phone System
- Power BI Pro
- Cloud 365 App Security
- Audio Conferencing
- Microsoft Defender for Office 365 Plan 2
- Advanced compliance
- Everything included with Microsoft 365 E3 plus:
Obviously, these are some summary explanations of common license packages. But it does show how complex the choosing the right licenses can be? I definitely recommend having an expert, a Microsoft CSP Partner, such as Zunesis to assist in your version of the Microsoft Modern Workplace.
From Challenges to Improvements
As the saying goes April Showers Bring May Flowers. Better yet, the IT hurdles of 2020 brought much needed improvements in technology today.
As we all know, the dark days of 2020 caused much chaos and angst across the world. It affected industries and people in a myriad of ways. The IT industry was, of course, not omitted from the all-of-the-sudden-problems. Leaders in the industry scrambled for answers and resolutions to issues that seemed to arise overnight.
The beauty of hardships, however, is that they create resiliency. The silver lining from 2020 is that issues of yesterday bring knowledge and technological enhancements of today. Namely, we are dealing with improved security, flexibility of remote working, and the much-anticipated receipt of previously purchased goods.
Ransomware boom of yesterday creates new and improved security features of today
In the world of IT, if we are not growing and changing, we are dying. Evolving is a major part of the industry. This is partly due to the nature of the beast. In this case, it is also due to the people and crisis that threaten company and individual livelihood – otherwise known as ransomware attacks and cyber hackers.
A few (of many) advances in technology that have taken off over the past few years are:
End users:
- Multi factor authentication
- Fingerprint scanners to unlock devices
- VPN’s
Companies:
- Single Sign On for apps/devices
- Trusted platform module
- Infosight style management platforms (more streamlined and easier to use alerts and logging, automatic updates, proactive alerts and patching)
Randomized MAC addresses:
- Originally introduced by Apple, this new feature randomizes your MAC address when connecting to wireless connections.
Now, of course, much of the above was around prior to 2020, but the focus on making these things higher quality with increased functionality has taken off.
Chaos of enabling a remote work environment creates flexibility and improvements to company policy
Creating a remote work environment is not easy. It’s not easy when you have the time and resources on your side to do-so, but without thorough planning to execute, it seems almost impossible. Aside from lacking time and resources, we can’t forget about the difficulties in getting our hands on the needed technologies to make this happen too.
As companies struggled to work through the difficulties of enabling a remote work environment in 2020/2021, we are now able to reap the benefits of IT’s hard work.
Positives that have come from a rushed remote set-up include:
- Flexibility that has come from the ability to work remote if need be
- Change in (some) corporate policy – leaders identifying that often times, employees are more productive at home
- Knowledge of a remote set-up – Now that, for the most part, companies have learned how to create a remote work environment. They have already either completed the procedure on how to do this, or at least gotten a taste of what needs to be done. The learning curve is less steep.
Supply chain issues – your patience of yesterday is being rewarded with the goods of today:
In 2021, depending on the product and the manufacturer, some customers were waiting in line for goods to arrive anywhere from 3-12 months out from the purchase date. Some of the many challenges with this, include :
- Public Sector entities that, due to rules and regulations, require product onsite before fiscal year-end
- The need for product to arrive immediately in order to enable a remote working environment
- Technology refresh cycles being pushed out, which of course causes security issues and can threaten support needed on any given product
In 2022, we have slowly started closing the gap between purchase date and arrival of product. Though we are not to the finish line quite yet. Again, depending on product and manufacturer, we are seeing ship dates creep back down. The most exciting thing about shipment of product that you bought 12 months ago? You likely finally have that in your hands, and that’s a great feeling! Companies are becoming more familiar with how to handle this (Purchasing further in advance, changing the way we timeline future projects, and understanding the right questions to ask when it comes to support on product).
The silver lining is alive and well and the hope is that we only continue to grow past the hardships of yesteryear! Reach out to Zunesis today to find solutions to help your organization bloom.




