Over $500 Million Pledged to Computer Science Education
A recent article from staff reporter, Emily Tate at the Scoop News Group, announced that Computer Science has picked up a concerted cross-sector support with the Trump administration and a slew of private sector companies collectively committing more than half a billion dollars to K-12 and post-secondary STEM programs.
President Donald Trump signed a memorandum directing Education Secretary Betsy DeVos to prioritize high-quality STEM education- and in particular, computer science- within her department. She was instructed to spend at least $200 million per year in existing grant funds on that priority.
The directive, which also asks DeVos to explore other ways the administration can support computer science education, will not establish a new grant program or draw from new funds. Instead, STEM initiatives will warrant extra consideration as the Education Department chooses where to allocate existing grant money.
In announcing the directive, the White House emphasized the growing role of technology in the economy, saying that “Technical knowledge and skills are more important than ever.”
More than half of American schools – about 60 percent – do not offer computer science courses today, according to Code.org, but the demand for trained computer programmers and computer science graduates continues to climb. Seventy-one percent of all new jobs in STEM are in computing, yet only 8 percent of STEM graduates have computer science backgrounds.
“Greater access to STEM and computer science programs will ensure that our children can develop the skills they need to compete and to win in the workforce of tomorrow. ”
– President Trump
Following the president’s lead, nearly a dozen private-sector companies together pledged more than $300 million to K-12 computer science programs at an event in Detroit with Ivanka Trump, who released a video on Twitter extolling the White House’s effort and calling it “enormously important.”
Amazon, Facebook, Google, Microsoft and Salesforce each earmarked $50 million. Lockheed Martin, whose CEO was in Detroit for the event, pledged $25 million. Accenture, General Motors and Pluralsight offered $10 million or more each. Other businesses, individual and foundations dedicated funds as well.
“This money prioritizes and shines a light on computer science as a need,” said Dave Frye, Associate Director of the Friday Institute, an education resource center based out of North Carolina State University’s College of Education. “Even within STEM, computer science needs some attention. It doesn’t have the presence in schools other than STEM curricula have.”
Other organizations, including the Consortium for School Networking (CoSN), applauded Trump’s directive but questioned why the administration didn’t show that same support for STEM in its suggested budget, which proposed cutting $9 billion from the education department and would have affected key educational technology programs. “CoSN appreciates the Administration’s focus on STEM education and computer science. We hope the directive now signals a serious commitment from the Administration to educational technology investments, and in particular, the Student Support and Academic Enrichment grant program,” Keith Krueger, CEO of CoSN, said in statement. “Full funding of the program would help equip all students and schools with the resources they need to excel in modern learning settings.”
The Threats are Many and so are the Protection Methods
In a modern society, the need for cyber security touches a surprisingly large portion of our day-to-day lives. Because of the Internet of Things (IoT), we can scarcely climb out of bed each morning before we use a device that is connected to the internet in some way. Whether it’s our smart phones, Alexa, Siri, tablets, laptops, television or even our automobiles, we are potentially putting personal data out on the internet before we’ve even had our first cup of coffee (or even as we order our coffee for pickup as we head into work). We pay our bills online, we use our phones to deposit checks and we even have wi-fi enabled automobiles.
As individuals, we are responsible for looking out for our own security. As IT Professionals, we are responsible for protecting the data our company produces and collects. In many cases, the data we are protecting in our professional role is personal data, possibly our own. But, the recent Equifax breach is a harsh reminder that, even companies we associate with security are vulnerable. If there is any lesson we can take away from our personal experiences, and the stories behind the headlines, it’s that there is not single solution that will protect us from the threat of our data ending up at the mercy of people with bad intentions. Those of you reading this post are intimately familiar with the steps needed to protect company data. From the network to the desktop, and all points in between, there are many layers to a data protection strategy. One such layer is the Data Backup solutions we use.
Backup, the Original Data Protection
Decades ago, during simpler times, data protection meant being diligent about performing regular backups of data in case a file was accidentally deleted, corrupted or the hard drive crashed. Back in that simpler time, the media to which businesses directed those backups was almost always Tape, lots of tape! This process typically included keeping a set of tapes onsite for immediate restore needs and sending a second set offsite in case of catastrophe and for longer term retention. However, over time, Tape has been increasingly replaced by disk-based backup targets (think HPE StoreOnce, Data Domain, ExaGrid).

Disk-based backup targets started out as a faster way to get data backed up. Tape was still used but typically as a secondary backup target and for longer term retention offsite. The need to go to an offsite backup for file recovery was rare and so tape became that insurance policy that was never going to be needed. As use of disk-based backups became more prevalent, the technology employed to store data evolved. Improvements in compression, deduplication, and replication improved the efficiency of storing larger amounts of data (in the petabytes) and replicating that data to offsite facilities. In fact, with the ability to replicate data from one disk-based target to another over distance, we have started to see Tape being replaced at offsite facilities as well.
Backups As Our Last Defense
While we originally used backup for recovery from accidentally deleted files, random corruption and the occasional disk crash, the world we live in today requires a broader definition for Data Backup. Today, we may need to leverage our backups to recover from a Cyberattack that has either corrupted our data or rendered it unusable as part of a Ransomware attack. Because these kinds of attacks target files on volumes that are persistently mounted to hosts, the vulnerability of disk-based backup targets has come under some scrutiny lately.
Of course, many question whether the risk to disk-based backup targets is very high. After all, backup environments are typically isolated from other, more accessible, areas of the IT infrastructure. Moreover, because of the potential for Cyberattacks on the disk-based backup targets, other processes have been documented and are being implemented to mitigate the risk further. We are starting to see some of these added protections built into the backup software we use and many manufacturers of the disk-based backup devices are providing their own best-practice processes.
Despite the fear of risk for disk-based solutions, we aren’t seeing a trend away from disk-based backup, but we are hearing reports that some companies are once again turning to Tape as their last form of defense against the type of Cyberattacks that would corrupt, delete or encrypt their data. And while disk-based technology has been evolving, tape technology has also continued to evolve. LTO7 technologies provide capacities as high as 15TB (compressed) per tape cartridge. In addition to high capacities and a low TCO, Tape offers encryption at-rest, can be kept offsite and most importantly offline.
So, as we implement safeguards to keep the bad guys out of our IT infrastructure, we need to remember that our plans should include multiple layers. We also need to prepare for the possibility that our best efforts will be thwarted and that our data will be compromised. So, as part of our protection against malicious behavior and risk to our data, we need to carefully plan our Backup processes by taking the layered approach as well.
Recently, Twitter had their 10 year anniversary of their first tweet. 12 years ago, Facebook officially went live as a product we know of today. Today, both of these major platforms have a combined total user base of over 2 billion people and businesses. When you add in other social upstarts and apps such as Instagram, WhatsApp and Snapchat, you can add in another 1.6 billion users. And even with these staggering user stats and singular places to reach a massive audience, businesses all over the world are still reluctant to invest more in social media, or even make a leap into social media at all. Much of it stems from time and staffing levels, an inability to see value from higher-ups in many organizations, monetary constraints, lack of knowledge in their use, or just a failure to see or have the ability to measure ROI of social media as a whole. We hear a lot of these responses, but the question of ROI seems to be a major factor in determining social media’s place in an organization’s marketing strategy.
So how you determine social media ROI?
It’s a very tricky question to answer for any business but much of it has to do with trying to determine what the goals of your business and marketing efforts are in the first place. If you are basically any business, branding and brand recognition should nearly always be at or near top of your marketing and social media goals. Even Coca Cola and McDonalds never stop in their own branding efforts as evidenced by their TV ad spend, and especially their investment into their social media efforts among other campaigns. Look at companies like Red Bull who plaster their brand over an ever-growing stable of extreme athletes. An eCommerce business probably has an additional goal where they can utilize social media for branding purposes as well as drive traffic to their website which will ideally lead to a web sale. So, the first place to start for any business is to determine your goals, determine what the metrics are to measure these goals and then start to determine the ROI of your social media efforts.
Setting Goals

Facebook Reach
As branding should be the goal of nearly every business, there are a few good metrics you can use to help determine if social media is working in your favor. Reach on Facebook is one great metric to review. Reach is simply the number of fans and followers that had the opportunity to see your post. So how do you boost reach? Since the life of the average post on Facebook is around 1-3 hours, you should be posting when your fans are online the most. Your Facebook Insights is the best place to look for this data. Insights is a great metric to look at on a regular basis. Just like a TV commercial, you want the as many people to see your posts as possible.
Engagement
This is the actual interactions that people have with your posts across all your social networks. To calculate, add up all these interactions such as Reactions, Comments, Shares, Retweets and so on and divide that number by your total number of fans across all these social networks.
Why is this an Important Metric to Track? Many studies show that users who engage most often with a brand tend to view the brand in a positive light. And those people are also more likely to make a purchase from that brand and recommend that brand to their friends. And while most social networks these days have made it harder for brands to increase “organic” engagement through algorithm changes, one can improve the engagement of their posts in large part to one central theme: Better Content Equals More Engagement. In other words, give people what they want or solve pain points and you will see engagement go up.
Traffic To Your Website (or Store)
Driving traffic to your website shouldn’t be your only goal or your primary source of content. Ultimately, you should track how people are coming to your website by way of social media channels. One easy way to track this is looking at your Google Analytics account and look at the Social Network Referrals page. This wills how you exactly how many people came to your website by clicking on a link within a given social media channel. From there you can see which links people clicked on in that social channel. This can tell you not only the number of referral clicks from that channel but also what type of content is resonating with people. If you want to dial in even deeper, you can create individual link campaigns in Google Analytics. You can do this by creating unique tracking URLS for each social channel to see which channel is working best and also which is leading to the most sales or conversions. This way you can get even more granular about which social channels are driving click-thrus.

Measuring
Conversions
A conversion is simply defined as an action on your website that you want people to take. It could be an email sign up, a PDF download, a new potential lead, a completed sale, time spent on a page or even a video view. While many businesses want sales directly from social media, this attitude is gradually changing and greater importance is being placed on non-financial aspects of social media marketing. Conversions are another metric that can be tracked within Google Analytics once you have determined what conversions you want to track and creating those goals to track. That entire process is for another day but setting up goals and conversion tracking in Google Analytics is imperative in measuring effectiveness for your social media ROI.
Revenue/Sales
While this may not be a primary goal of your social media efforts, or even a goal you create to determine ROI, there will be some who want to know exactly how much in sales is directly attributable to your social media efforts. One caution would be to not only use sales as measurement of social media ROI. This might be a tougher sell to some CEOs who are primarily focused on top line growth. While this can be a key metric to track for businesses who sell products or services directly on their website, it might not be a metric for someone like a restaurant whose sales come 100% from offline activity. There are ways for restaurants, storefronts, bars and other offline business to at least measure individual campaigns that you may run from a Facebook page for example. A good example might be running a coupon or offer where social media is the only place to pick up such a deal. From there, you can calculate how many coupons/offers were brought in and how much in sales those tickets generated. But for those wishing to measure sales in their online channels where they can attribute to social media efforts, it can be slightly more daunting. Utilizing Google Analytics and under Reporting/Acquisition/Social/Conversion tabs, you will be able to see whose people who were referred by a social network and consequently those visits which led to a sales conversion. This is just one way to measure revenue attributable to social media activity or sales ROI.
You can see from some recent surveys from current CMOs which metrics are most important to measure social media ROI. A few metrics are revenue related.

Cost Calculation
To figure a true cost, or ROI, of your social efforts as it relates to sales or actual revenue generated, you also need to know what you are spending in and on for your social media efforts. But again, this is but one aspect of social media ROI; using revenue as metric to track. The easy and most basic way to calculate this is a simple math formula:
Social Media Revenue ROI(%) = (Revenue Generated from social media – Cost of social media marketing)/Cost of social media marketing
So if you generated $1000 in sales and spent $800 in marketing dollars, your ROI would be 25%.
You also need to determine which costs are associated with these efforts and campaigns. Examples of costs would include time or labor, agency costs, advertising spend and any other additional marketing spend such as product giveaways or subscriptions.
Reporting
It is advised to use 3-5 metrics that are important to your business goals, especially when you have higher-ups who want to know what the value of social media is on a regular basis. This list and article is not an exhaustive list on the metrics you can use to help determine an ROI of your social media efforts but it should at least get you started in the right direction.
A report is something you can create in an Excel sheet, but I always recommend using graphs and graphics whenever possible as a way to better visualize the data, and make it more consumable. In this case, a PowerPoint might give you the power to show how your efforts are helping your ROI and prove the worth of your efforts. If you don’t have the time or ability to create the proper reporting on measuring your goals and specific metrics, it may be time to consider hiring an agency for some or all of your social media efforts.
When utilizing an agency, you have the advantage of not only years of expertise but also the software and platforms to dig deeper into the data and how you measure your social media ROI. We have the ability to look at the things that matter the most to your CMO or marketing executives. Things like social influence, brand sentiment, brand mentions across the internet, virality, competitive analysis and many other deeper dive indicators that can elevate your social media across all channels.

Zunesis’ Stream platform allows you to take a deeper dive into what is driving your social audience, brand sentiment, influencers and responding to them in real-time. You might wonder how you lived without it after you start using it.
Conclusion
While vanity metrics such as Likes or Reactions seem to consume most of any business’ social strategy, taking the time to sit down and create a set of metrics to track those goals will not only help you determine an ROI of your social media efforts, it will also give you a path to elevate your social media efforts and even surpass your goals. The data is there, now it’s up to you to make the time to use it, report it and make actionable insights for optimum results. You will not only save time, but you will become more productive and most likely you will see an increase in revenue as a result. But if you don’t have the time or expertise, don’t throw darts at a wall and hope for the best! Hire someone who can do this and you will reap the benefits. Social media is here to stay, so you might as well use it to grow your business.
What is Meridian?
Meridian is the newest and one of the fastest growing technologies within Aruba, giving their customers a truly location aware platform. Meridian is capable of engaging users from a marketing perspective in real time while they walk the floor or simply guiding them where they need to go within a large public venue.
The Meridian solution is built on open API’s, giving its customers the flexibility to leverage their existing investment in their wireless solution and allowing it to integrate into virtually any modern device application.
Who Does Meridian Help?
Meridian is built for any large public venue or large retail environment. The goal of Meridian is to bridge the gap between its customers’ marketing departments and their users. This gives Meridian clients a better understanding of their users while also giving the users a better experience with the venue.
Conference centers are a great use case, as Meridian allows the venue to provide indoor blue-dot wayfinding to their guests (think Google Maps for indoor environments) as well as analyzing the most traversed paths throughout their building. This allows their marketing teams to develop more effective advertising.
Nebraska Furniture Mart uses Meridian for indoor wayfinding as well as some marketing applications, giving users push notifications with coupons when they linger by certain displays.
Levi’s Stadium, perhaps the most invested Aruba customer in the world, uses Meridian in a number of different ways including:
-
- Guest Wayfinding – blue dot for guests to find seats/bathrooms/concessions/etc.
- Predictive Analytics – which bathroom has the shortest line or which vendor has the shortest wait
- In-Seat Ordering – Guests order food/beverages from their seats and a vendor will bring it to them even if they get up and walk around
- Geofencing – Utilize Meridian to validate that a guest is actually in the stadium, which gives them access to replay cameras not available to anyone else
Watch the video below to see how the Royal Botanical Gardens in Madrid uses Meridian to enjoy an interactive app experience at their venue.
Aruba beacons are NEMA rated for outdoor and indoor use.
Why Choose Meridian?
The main advantage to Meridian is that it can leverage existing investments in technology. Customers will not have to forklift to upgrade their wireless environment to make it “Location Aware,” and they will have not have to completely re-write an existing application to integrate the beacons if one is already in place. There are services available through HPE to help integrate the Meridian solution with an existing application or they can design a new application for the customer if they do not already have one.
Additional Resources
As we find more and more of our clients are asking about E-Discovery, it seems appropriate to use this post to call out a product that has been doing well in the market. It’s called SourceOne and it’s a standalone product from EMC.
EMC SourceOne Discovery Manager allows for discovery and secure legal hold of archived content in response to legal and regulatory notices and corporate policy complaints. Discovery Manager has an easy-to-use interface that allows users to quickly find, review and produce archived information relevant to an inquiry.
Discovery Manager is built around a legal “matter” or case metaphor. It supports secure, authorized investigator access, defensible collection results and chain of custody of content archived. It does a full text-based index allowing for easy searching and it also supports the Electronic Discovery Reference Model (EDRM) XML export standard for easy data transfer to final e-discovery production applications.
Borrowing from EMC’s own notes on the product, EMC SourceOne Discovery Manager delivers the following benefits:
|
Features |
Benefits |
|
Secure-matter lifecycle management |
Manage active and closed matters and designate authorized users and roles throughout the discovery process |
|
Simple, wizard-driven interaction |
Improve investigator productivity, effectively search large email volumes, and securely hold email content |
|
High-volume search and collection |
Reduce the time and effort to find relevant email by searching EMC SourceOne archives and metadata attributes |
|
Secure legal hold |
Prevent spoliation and restrict permissions to matters with predefined user roles |
|
Customizable tags |
Apply tags to easily filter or narrow large volumes of collected content |
|
Flexible export options |
Export relevant email for external review and filter export on the basis of applied tags |
|
EDRM XML export standard support |
Support downstream e-discovery processing and production according to the Electronic Discovery Reference Model (EDRM) |
|
Web User Interface |
Allows customers instant access to archived data through one centrally managed console from any common Internet browsers |
If E-Discovery has become an area of interest for your organization, SourceOne from EMC is worth your time to investigate. If you would like to know more about the potential of this product to address your specific security and discovery needs, contact us today.
Ensuring that all wireless clients get the service levels they need is a major challenge, especially when smartphones, tablets and other devices control their own connectivity and roaming decisions on the network.
ClientMatch® is a RF management technology developed by Aruba Networks that puts the connectivity and roaming control back into the wireless solution. The idea behind this is that the wireless solution will have a much better idea of which access point is the most appropriate client, based on the information the Access Points are constantly collecting. This allows the controller (or Instant Controller) to make these decisions about what to do with a client in real time, which drastically increases performance of a wireless network.
Client Steering
The old adage of “one bad apple spoils the bunch” is especially true in wireless networking, particularly now with the greater than gigabit speeds of 802.11AC. Once attached to an AP, clients tend to stay attached even when the user begins to walk away from the AP and the device signal weakens. When these devices do not roam to a new access point, it drags down the throughput of everyone else on the access point they are “stuck” to.
We call these devices “sticky clients,” and a few of them can even bring modern wireless networks to their knees if they do not know how to handle these clients. The process of moving clients to more appropriate AP’s within a network is called Client Steering.
Band Steering
In addition to addressing the problem of sticky clients, ClientMatch® also helps devices connect to the best available radio. Let’s say a dual-band client attempts to connect to a 2.4GHz radio on an access point with a 20MHz channel, ClientMatch® will steer that client to an avaiable 40MHz channel on a 5GHz radio – provided there is one in the client’s range with good signal strength. This allows the wireless system to take full advantage of the client’s capabilities to essentially double its throughput by forcing it to connect to the correct radio. This feature within ClientMatch® is called Band Steering.
Dynamic Load Balancing
Whether we are talking about Band Steering or Client Steering, Aruba always takes the Access Point Load into account when making these calculations. Dynamic Load Balancing addresses client density problems by dynamically distributing clients across available AP’s and Channels, ensuring that individual APs aren’t overloaded and client performance is continually maximized. This is a very important feature in client dense environments like auditoriums.
An analogy I like to use to explain all of this is the highway analogy. A true BYOD network will have a diverse set of devices that all need access, similar to a highway and its diverse set of cars and drivers. One or two slow drivers can cause serious delays in your morning commute, as all of the traffic behind them begins to pile up. However, simply steering these “slow drivers” to the correct lane will increase the total speed of the highway (user experience) immensely.
ClientMatch® is included in both Instant and Controller deployments. It is a base, unlicensed feature of the Aruba Operating System. It is available as part of AOS 6.3 and higher. For more information download this tech brief.
In today’s hectic and time-pressed technology environment, IT leaders often don’t have the time to work with multiple technology manufacturers for purchasing, confirming compatibility with existing infrastructure solutions and of course the importance of post-sales/implementation support.
Hewlett Packard Enterprise (HPE) have come up with an innovative solution for organizations to make their entire IT solution purchases with one trusted organization; under a program called “Complete”. What is Complete you may ask?
HPE Complete
HPE Complete is a resource that enables customers to purchase best-in-class, third-party branded products through their trusted solution partners like Zunesis. HPE Complete benefits include:
- One-stop shop: Purchase complete solutions from Hewlett Packard Enterprise on a single Zunesis purchase order.
- Validated solution: Confidence of the HPE interop assurance validation for third-party branded products that complement HPE Storage and Server Solutions.
- Customer Experience: HPE helps ensure complete customer satisfaction by troubleshooting the solution and facilitating third-party expertise for the installation, support and warranty of their products.
- Unique Value: Minimize risk, complexity and cost when deploying multi-vendor products and technolgies into the HPE ecosystem.
- Contract Facilitation: In many cases, using HPE Complete can assist with lack of procurement vehicle as the HPE SKUs may be eligible for existing Public Sector Contract applications, such as NASPO ValuePoint, E&I, MHEC, etc.
What are some of the top HPE Complete partners whom Zunesis works with today?
Veeam
Veeam Backup and Replication is a powerful, easy-to-use and affordable backup and availability solution. It provides fast, flexible and reliable recovery of virtualized applications and data which brings virtual machine backup and replication together in a single software solutio. Veeam Backup and Replication delivers award-winning support for VMWare vSphere and Microsoft Hyper-V virtual environments.
NVIDIA GRID
NVIDIA GRID is a graphics virtualization platform that extends the power of NVIDIA GPU technology to virtual desktops and applications. The software delivers an immersive, high-quality user experience for users from designers to mobile professionals to office workers. NVIDIA GRID technology lets IT organizations tap into a powerful graphics-accelerated cloud solution to centralize applications and data with virtual workspaces for improved security, productivity and cost-efficiency.
Carbonite Double-Take
Carbonite Double-Take Availability is a proven, simple, scalable high availability solution for Windows and Linux that defends your business’ profitability and reputation by providing protection from data loss and downtime. Carbonite Double-Take Availability offers exceptional application and data protection in virtual, cloud and physical computing environments. Carbonite Double-Take moves quickly and easily migrates physical, virtual and cloud server workloads over any distance with minimal risk and near zero downtime.
Zerto
Zerto Virtual Replication enables alignment across customer’s IT strategy with hypervisor-based replication, allowing you to fully realize the benefits of virtualization. The benefits of a virtualized application carry through to your business continuity and disaster recovery solutions. Zerto moves replication from the array or host, up to all the hypervisor. This provides flexibility, better asset utilization and reduced operational and maintenance costs – all to reduce your overall TCO.
Qumulo Core
Qumulo Core is a modern scale-out storage system designed from the ground up to address customer challenges for the new ear of multi-petabyte data scale on premises and in the cloud. Qumulo Core uses storage capacity much more efficiently than legacy scale-out NAS. At scale, Qumulo Core’s rebuild times in the case of disk or node failure are faster. This allows technology administrators to greatly reduce the level of redundancy needed to achieve target MTTDL standards, thereby increasing storage efficiency. Enabled by Qumulo Core’s flash-first hybrid design, cost and performance are optimized which simultaneously provides the speed benefits of SSD and the economic advantages of HDD. Qumulo Core does not require any disk space be left available for its internal use. This means user files can occupy 100 percent of provisioned capacity, while legacy scale-out recommends only using 80 percent.
These five partners represent only a fraction of the partner networks which HPE Complete have together. For more information: HPE Complete and other partner networks
Aruba Operating System (AOS) 8.0
Aruba Operating System (AOS) 8.0 code recently went “GA” to all of Aruba’s customers. AOS 8.0 is a complete ground-up rewrite of the Aruba Operating System, giving it a better scalability and increased network performance. Here are some of the more visible enhancements to the platform.

Adaptive Radio Management (ARM) Changes
ARM is Aruba’s proprietary feature that allows AP’s to automatically negotiate power levels and broadcasting channels to avoid co-channel interference and ensure optimal performance for all clients and applications. The biggest limitation of ARM in the past was that it would not negotiate channel width (20, 40, 80MHz), leaving a lot of unused channels in the higher-width frequencies unused. Another past quirk of ARM was that it would calculate about every 5 minutes. With calculations happening that frequently, it was possible for a microwave running in the break room (which creates interference on the 2.4GHz band) to completely change the channel assignment of a building.
To address these issues, Aruba has overhauled the ARM protocol in 8.0 – and it even comes with a new name: AirMatch. AirMatch was designed with the modern RF environment in mind. It is tuned for noisy and high density environments, as well as areas where free air space is scarce. (Remember, we only have so many channels available over Radio Frequency; and the FCC has reserved their fair share for the government and emergency services, leaving businesses even fewer available channels).
AirMatch gathers RF statistics for the past 24 hours and proactively optimizes the network for the next day. With the automated channel, channel widths and transmit power optimization, AirMatch ensures even channel use, assists in interface mitigation and maximizes system capacity.
Zero Touch Provisioning (ZTP):
ZTP automates the deployment of APs and managed devices. Plug-n-play allows for fast and easy deployment and simplified operations, reduces costs and limits provisioning errors. ZTP was introduced in 70xx Mobility Controllers; and now in AurbaOS 8, we are extending the capability to include 72xx Mobility Controllers. The Mobility Controller receives its local configuration, global configuration and license limits from the master controller or the Mobility Master and provisions itself automatically.
Simplified Operation:
In contrast to ArubaOS 6, which operates on a flat configuration model containing global and local configuration, ArubaOS 8 uses a centralized, multi-tier architecture under a new UI that provides a clear separation between management, control and forwarding functions. The entire configuration for both the Mobility Master and managed devices is configured from a centralized location- providing better visibility and monitoring as well as simplifying and streamlining the configuration process and minimizing repetition.
Centralized Licensing with Pools
IT teams can manage all their licenses from a centralized location with centralized licensing, either from the Mobility Master or the master controller. In the new AOS 8, we have extended ability to include centralized licensing with Pools. For some customers who have separate funding for different groups inside their corporation, they have the option of simply assigning licenses for each group to manage and consume themselves. This will drastically simplify licensing, especially troubleshooting licensing issues!
To summarize, AOS 8.0 is the future platform for all Aruba development. Great amounts of time have been spent re-writing everything to ensure performance and scalability going forward – this project was started before the HPE acquisition took place! Instead of bolting-on updates to the aging 6.0 platform like most vendors tend to do, Aruba has made a huge investment in the future by re-writing the underlying Operating System. This shows their commitment to being the #1 vendor in the wireless space for years to come.
For a better understanding of what upgrades were made in 8.0, download this tech brief.
[qodef_button size=”small” type=”default” text=”Download” custom_class=”” icon_pack=”font_awesome” fa_icon=”” link=”http://www.arubanetworks.com/assets/ds/DS_ArubaOS8.pdf” target=”_self” color=”#ffffff” hover_color=”#004f95″ background_color=”#30c7ff” hover_background_color=”#ffffff” border_color=”#30c7ff” hover_border_color=”#004f95″ font_size=”” font_weight=”” margin=””]
There were far too many features and platform advancements for me to cover in a single blog (especially changes made to the deployment models), but you would like to have a discussion about these changes, feel free to Contact Zunesis.
(Drum roll, please!) Citrix has announced LTSR!
What is LTSR?
Long Term Service Release. LTSR is all about stability and supportability when it comes to ongoing maintenance and support.
I’ll let Citrix take the intro on this one: “As a benefit of Software Maintenance, Long Term Service Releases of XenApp and XenDesktop enable enterprises to retain a particular release for an extended period of time while receiving minor updates that provide fixes, typically void of new functionality. This provides customers with greater predictability and simplified on-going maintenance. Today, Citrix is announcing our first-ever Long Term Service Release of XenApp and XenDesktop 7.6 available for download on Citrix.com.”
So, what does all that actually mean? What they are basically saying is this: LTSR is their most stable, robust and Enterprise worthy release of the XenApp/XenDesktop 7.x platform to date.
It has been thoroughly tested and used for extended periods of time within large, heavily utilized environments. 7.6 is the current LTSR version supported with Citrix. In my opinion, it really is the first version that has been ready for prime time.
Customers are still using older versions that date back 7 plus years! This is Citrix’s way of getting those customers to a newer version without having them wonder if it will be just as reliable, secure, and stable as their older version.
Now, as 7.6 does not officially support Windows 10, they have done some solution Tetris to support Windows 10. This requires the latest version of the VDA client, Citrix receiver, UPM and PVS. This also allows clients time to adapt and adjust to the new Citrix architecture without having to continually update every 9-12 months.
In addition, the LTSR version will continue to get ongoing updates and support whereas the regular versions will stop receiving updates as soon as a newer version comes out. By using LTSR, an organization will receive at least 5 years of extended support when needed and/or desired.
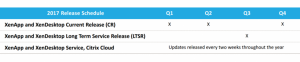
The lists below provide details into the differences between the new LTSR and the current release.
Long Term Service Release:
- A Long Term Service Release guarantees 5 years of mainstream support and an optional 5 years of extended support. Thsi includes cumulative updates every 4 to 6 months, a new LTSR version of XenApp/XenDesktop every 12 to 24 months and any potential (hot)fixes.
- Every new LTSR will probably be preceded by at least 3 to 4 CR’s.
- A valid Software Maintenance (SM) contract is needed to make use of the LTSR servicing option.
- As soon as Citrix releases a new LTSR version of XenApp/XenDesktop, customers can upgrade to that specific version as part of their current LTSR / Software Maintenance contract. Upgrading is always optional, not mandatory. Five years of support will start over for the new LTSR version.
- Citrix is currently working on a compliance tool to help organizations check if their current environment is eligible for a LTSR.
- Customers can have the LTSR as well as the CR servicing options in use as the same time.
- Switching form a LTSR to a CR servicing, and vice versa, is always optional as well.
- Citrix does not recommend mixing and matching non-compliant CR components in a LTSR environment.
- Citrix offers full downloadable packages including all LTSR components, fully up-to-date, patched, supported and ready to go.
- When dealing with support, they may ask clients to install the latest update for their current LTSR if not done so already.
- If it is new functionality and innovative features you are looking for, then go with the Current Release instead.
Current Release:
- With a CR supported version, you have the ability to upgrade to the latest version of XenApp/XenDesktop, making use of all the new and innovative features and functionalities that Citrix has to offer. (IE nothing changes.)
- New versions of XenApp/XenDesktop will be released every 3 to 9 months following the standard product lifestyle.
- No cumulative updates will be made available.
- Clients will need a valid Subscription Advanatage contract to make use of Current Release version.
If you have further questions about LTSR, please see the links for further reading below, or contact your Zunesis representative.
- https://www.citrix.com/support/programs/software-maintenance/xenapp-and-xendesktop-servicing-options.html
- https://support.citrix.com/article/CTX205549
(Drum roll, please!) Citrix has announced LTSR!
What is LTSR?
Long Term Service Release. LTSR is all about stability and supportability when it comes to ongoing maintenance and support.
I’ll let Citrix take the intro on this one: “As a benefit of Software Maintenance, Long Term Service Releases of XenApp and XenDesktop enable enterprises to retain a particular release for an extended period of time while receiving minor updates that provide fixes, typically void of new functionality. This provides customers with greater predictability and simplified on-going maintenance. Today, Citrix is announcing our first-ever Long Term Service Release of XenApp and XenDesktop 7.6 available for download on Citrix.com.”
So, what does all that actually mean? What they are basically saying is this: LTSR is their most stable, robust and Enterprise worthy release of the XenApp/XenDesktop 7.x platform to date.
It has been thoroughly tested and used for extended periods of time within large, heavily utilized environments. 7.6 is the current LTSR version supported with Citrix. In my opinion, it really is the first version that has been ready for prime time.
Customers are still using older versions that date back 7 plus years! This is Citrix’s way of getting those customers to a newer version without having them wonder if it will be just as reliable, secure, and stable as their older version.
Now, as 7.6 does not officially support Windows 10, they have done some solution Tetris to support Windows 10. This requires the latest version of the VDA client, Citrix receiver, UPM and PVS. This also allows clients time to adapt and adjust to the new Citrix architecture without having to continually update every 9-12 months.
In addition, the LTSR version will continue to get ongoing updates and support whereas the regular versions will stop receiving updates as soon as a newer version comes out. By using LTSR, an organization will receive at least 5 years of extended support when needed and/or desired.

The lists below provide details into the differences between the new LTSR and the current release.
Long Term Service Release:
- A Long Term Service Release guarantees 5 years of mainstream support and an optional 5 years of extended support. Thsi includes cumulative updates every 4 to 6 months, a new LTSR version of XenApp/XenDesktop every 12 to 24 months and any potential (hot)fixes.
- Every new LTSR will probably be preceded by at least 3 to 4 CR’s.
- A valid Software Maintenance (SM) contract is needed to make use of the LTSR servicing option.
- As soon as Citrix releases a new LTSR version of XenApp/XenDesktop, customers can upgrade to that specific version as part of their current LTSR / Software Maintenance contract. Upgrading is always optional, not mandatory. Five years of support will start over for the new LTSR version.
- Citrix is currently working on a compliance tool to help organizations check if their current environment is eligible for a LTSR.
- Customers can have the LTSR as well as the CR servicing options in use as the same time.
- Switching form a LTSR to a CR servicing, and vice versa, is always optional as well.
- Citrix does not recommend mixing and matching non-compliant CR components in a LTSR environment.
- Citrix offers full downloadable packages including all LTSR components, fully up-to-date, patched, supported and ready to go.
- When dealing with support, they may ask clients to install the latest update for their current LTSR if not done so already.
- If it is new functionality and innovative features you are looking for, then go with the Current Release instead.
Current Release:
- With a CR supported version, you have the ability to upgrade to the latest version of XenApp/XenDesktop, making use of all the new and innovative features and functionalities that Citrix has to offer. (IE nothing changes.)
- New versions of XenApp/XenDesktop will be released every 3 to 9 months following the standard product lifestyle.
- No cumulative updates will be made available.
- Clients will need a valid Subscription Advanatage contract to make use of Current Release version.
If you have further questions about LTSR, please see the links for further reading below, or contact your Zunesis representative.




