What Is Azure Site Recovery?
Business outages are caused by natural events and operational failures. Organizations need a business continuity and disaster recovery (BCDR) strategy that keeps apps and data safe and available during both planned and unplanned downtime. It also needs to be able to recover those apps and data to normal working conditions as soon as possible. Azure Site Recovery meets these needs through the following avenues:
- Simple, automated protection and disaster recovery in the cloud
- Orchestrated disaster recovery as a service (DRaaS)
- Replication and disaster recovery to Azure
- Continuous health monitoring with Site Recovery
Why Site Recovery?
There are a host of reasons why Azure Site Recovery is an excellent option for BCDR, including recovery in the cloud, resiliency, testing, flexible failover, and continuous monitoring.
Disaster Recovery in the Cloud
 Replicate workloads running on VMs and physical servers to Azure, rather than to a secondary site. This eliminates the cost and complexity of maintaining a secondary data center. With Site Recovery, you have the ability to replicate any workload running on-premises, Hyper-V VMs, and Windows/Linux physical servers.
Replicate workloads running on VMs and physical servers to Azure, rather than to a secondary site. This eliminates the cost and complexity of maintaining a secondary data center. With Site Recovery, you have the ability to replicate any workload running on-premises, Hyper-V VMs, and Windows/Linux physical servers.
Resilience
Site Recovery orchestrates replication and failover, without intercepting application data. Replicated data is stored in Azure storage, with the resilience that provides. When failover occurs, Azure VMs are created based on the replicated data.
Testing Without Disruption
Azure Site Recovery allows you to easily run test failovers to support disaster recovery drills without affecting production environments.
Rich Recovery Plans with Flexible Failover and Recovery
Recovery plans allow modeling to customize failover and recovery of multi-tier applications spread over multiple VMs. Order groups within plans, and add scripts and manual actions. Recovery plans can be integrated with Azure automation runbooks. You can run planned failovers for expected outages with zero data loss, or be prepared for unplanned failovers with minimal data loss. Easily fail back to the primary site when it’s available again.
Continuous Health Monitoring
Site Recovery monitors the state of your protected instances continuously and remotely from Azure.
Interested in learning more about how Azure Site Recovery can improve (or even become) your “plan for a rainy day”? Please contact us today to learn more about this exciting solution!
What Is EMS for Office 365?
In this mobile-first, cloud-first era, questions around security dominate the conversations about moving to the cloud. EMS provides an identity-driven security solution that offers a holistic approach to security challenges by not only protecting the organization but also identifying breaches before they cause damage.
How Do You Know If EMS Might Be a Fit for Your Organization?
As with most solutions, EMS is built to solve real problems that organizations are facing in order to help them be more efficient, productive, and secure. Below are some issues that many IT organizations face, and EMS is specifically built to address these problems:
- How to help users who have too many passwords to keep track of them all
- How to secure data across mobile devices
- How to manage BYOD
- How to ensure sensitive data is protected, even on users’ mobile devices
- How to create and enforce proactive threat protection
 How Does EMS for Office 365 Address These Issues?
How Does EMS for Office 365 Address These Issues?
EMS is a rather robust solution. However, in a nutshell, below is a list of the ways in which EMS addresses the organizational concerns listed above.
Identity Management
- Single Sign-On (SSO)
- Cloud applications
- Azure supports SSO for over 2,500 SaaS application
- On-Prem applications
- Using Microsoft Identity Manager
- Cloud applications
- Multi-Factor Authentication
- Provide users an extra layer of security – force users to prove their identity using password in a combination with mobile phone (app/text/email)
- Advanced Reporting
- Track SSO utilization and identify anomalies
- Self-Service Password Reset
- With write-back capabilities
- Users can reset their own passwords, reducing Help Desk calls
Mobile Device Management (MDM)
- Microsoft Intune
- Manage all mobile devices in the mobile ecosystem
- Utilize Mobile Application Management (MAM) without requiring devices to be enrolled
- Manage corporate data on user owned device
- Utilize the same Office Applications used on-prem
Information Protection – Formerly Called Rights Management
- Classify, label, and protect data
- Apply persistent protection which travels with the data
- Enable safe sharing
Identify Driven Security
- Microsoft Threat Advanced Analytics
- Protection from advanced targeted attacks by applying user and entity behavior analytics
If you find yourself facing any of these issues in your IT organization, I strongly suggest looking into EMS from Microsoft. We would be happy to walk you through any questions you might have about the solution or talk about how it could improve your specific environment. Contact us today.
What Is EMS for Office 365?
In this mobile-first, cloud-first era, questions around security dominate the conversations about moving to the cloud. EMS provides an identity-driven security solution that offers a holistic approach to security challenges by not only protecting the organization but also identifying breaches before they cause damage.
How Do You Know If EMS Might Be a Fit for Your Organization?
As with most solutions, EMS is built to solve real problems that organizations are facing in order to help them be more efficient, productive, and secure. Below are some issues that many IT organizations face, and EMS is specifically built to address these problems:
- How to help users who have too many passwords to keep track of them all
- How to secure data across mobile devices
- How to manage BYOD
- How to ensure sensitive data is protected, even on users’ mobile devices
- How to create and enforce proactive threat protection
 How Does EMS for Office 365 Address These Issues?
How Does EMS for Office 365 Address These Issues?
EMS is a rather robust solution. However, in a nutshell, below is a list of the ways in which EMS addresses the organizational concerns listed above.
Identity Management
- Single Sign-On (SSO)
- Cloud applications
- Azure supports SSO for over 2,500 SaaS application
- On-Prem applications
- Using Microsoft Identity Manager
- Cloud applications
- Multi-Factor Authentication
- Provide users an extra layer of security – force users to prove their identity using password in a combination with mobile phone (app/text/email)
- Advanced Reporting
- Track SSO utilization and identify anomalies
- Self-Service Password Reset
- With write-back capabilities
- Users can reset their own passwords, reducing Help Desk calls
Mobile Device Management (MDM)
- Microsoft Intune
- Manage all mobile devices in the mobile ecosystem
- Utilize Mobile Application Management (MAM) without requiring devices to be enrolled
- Manage corporate data on user owned device
- Utilize the same Office Applications used on-prem
Information Protection – Formerly Called Rights Management
- Classify, label, and protect data
- Apply persistent protection which travels with the data
- Enable safe sharing
Identify Driven Security
- Microsoft Threat Advanced Analytics
- Protection from advanced targeted attacks by applying user and entity behavior analytics
If you find yourself facing any of these issues in your IT organization, I strongly suggest looking into EMS from Microsoft. We would be happy to walk you through any questions you might have about the solution or talk about how it could improve your specific environment. Contact us today.
Primary education has come a long way. Classrooms with desks, notebooks, textbooks, and content-centric curriculums have evolved to a more student-centered learning experience. Several technology trends are further driving the need for mobile computing within the classroom.
4 Trends Driving Adoption of Mobile Technology in the Classroom
 E-learning has grown into a multibillion-dollar market in the primary education (K-12) arena.1 Educational publishers are seeing their revenues from digital materials (electronic textbooks and other tools) eclipse revenues from printed textbooks.2 The upside for publishers, as well as research into best practices for e-learning, have led to four important trends driving adoption in the classroom:
E-learning has grown into a multibillion-dollar market in the primary education (K-12) arena.1 Educational publishers are seeing their revenues from digital materials (electronic textbooks and other tools) eclipse revenues from printed textbooks.2 The upside for publishers, as well as research into best practices for e-learning, have led to four important trends driving adoption in the classroom:
- Licensing models — Publishing companies offer cost-effective e-licensing models for schools to present students with the most current information.
- Supplementary tools — Other materials beyond traditional textbooks are now available to supplement the curriculums to help students have access to as much information as possible.
- Gamification — This enhances learning, as students enjoy the challenges and competitive aspects that stimulate learning.3
- Personalized learning — Students learn at different rates, and they more effectively acquire the collaboration and innovation skills required for college and beyond when learning environments are augmented with technology.
While all this is good news for students, one of the biggest challenges for 1:1 learning initiatives is the need for teachers to embrace the technology. If the technology or software is perceived to be too cumbersome, teachers will not willingly support it. Therefore, for any district-wide or school-wide implementation of mobile technology, teachers need to feel comfortable and find value in it.
So, What Makes a Good Mobile Solution for K-12 Education?
Built for Students
 Modern learning is often project-based, which requires reading and creation of content, collaboration, and presentation. More schools recognize that preparing students for technology-based fields — such as engineering, computer science, and vocations that require either coding or math calculation — requires the use of mobile technology that supports this sort of functionality.
Modern learning is often project-based, which requires reading and creation of content, collaboration, and presentation. More schools recognize that preparing students for technology-based fields — such as engineering, computer science, and vocations that require either coding or math calculation — requires the use of mobile technology that supports this sort of functionality.
However, students are tough on most things, including their own smartphones and textbooks. Therefore, devices need to be rugged and able to withstand drops, spills, and shocks. Devices should also be thin enough to fit easily in a backpack.
Built for Teachers
We’ve highlighted the important aspects of personal devices, such as laptops, from a student’s perspective. However, to be successful, teachers need solutions that accomplish the following:
- Enable teachers to differentiate instruction so students at different levels can learn successfully at their own rate.
- Facilitate instruction through software and collaborative tools. Solutions should help teachers orchestrate their classrooms, and save time with easier lesson planning, administrative and assessment workflows.
- Monitor student progress. Software that links the students’ devices with those of teachers can help teachers discern areas where students are individually or collectively having trouble.
1:1 Solutions Designed Specifically for Schools
HP has invested time and money in understanding the education market and gathering feedback from thousands of teachers, students, and school administrators to created impactful education technology. HP Education solutions, such as the HP ProBook x360 11 G1 Education Edition, are designed and built for dynamic learning environments to enable anytime, anywhere creativity, collaboration, and critical thinking while meeting lean budget requirements. Their goal is to create richer educational experiences, improve learning outcomes, and save teachers time.
If you are interested in implementing a 1:1 learning initiative in your school district, consider how convertible laptops from HP can cost-effectively enrich your curriculum and better prepare your students for the next part of their journey, whether it’s college or a job, as well as save your teachers time and help them engage their students more effectively.
In this post, I want to take a look at Aruba’s latest addition to their switching portfolio – the 2930m.
The 2930m is the modular brother to the 2930f (fixed) switch, which been selling for a number of months. The 2930m is the long-awaited replacement for the older 2920 switch, one of the best-selling switches ever for HPE networking, and includes some configurable options that are not available on the 2930f.
The new 2930m has configurable redundant power supplies, modular backplane stacking, higher stacking density, extremely high PoE capabilities, and a more advanced (but still not complete) layer 3 feature set for the modern edge network. The uplinks are also configurable on the 2930m, allowing for 1x 40G QSFP+ port, 4x 10G SFP+ ports, or 4x 10G SmartRate ports (1, 2.5, 5, or 10G copper ports depending on the capabilities of the device plugged into each port).
In addition to the data sheet below, I wanted to supply you with some information for quick reference. The best way to depict this information will be in table format, so we can compare the older 2920, the fixed configuration 2930f, and the new 2930m:
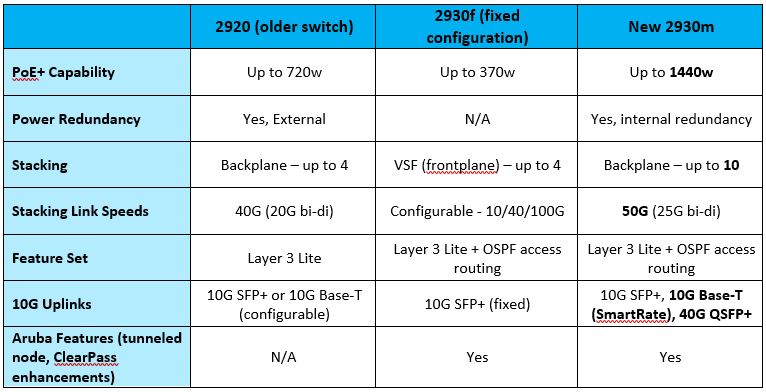
For more detailed information on this new switch, please download the data sheet here.
In recent months, HPE has announced two acquisitions that significantly impact their online storage portfolio. In January, it was announced that HPE would be acquiring SimpliVity, a leader in the hyperconverged space. Just two months later, in March, we heard that HPE would be acquiring Nimble, a manufacturer of all-flash and hybrid-flash storage solutions backed by a powerful predictive analytics tool called InfoSight. The acquisition of these two solutions gives HPE one of the strongest storage portfolios in the industry.
The HPE online storage portfolio now includes the following:
• MSA
• StoreVirtual (LeftHand)
• Nimble
• SimpliVity
• 3PAR
So, with so many options, the questions you may be asking are, “Where does each fit into my IT Infrastructure?” or “How do I determine which of these is right for my environment?” There is certainly some overlap amongst these options, but there are also clear reasons why you might choose one over the other.
In this post, I want to provide a summary of each of the solutions and include a few thoughts on why you might consider each as a solution for your environment. I will not cover the XP in this post because it is a solution that has a very narrow set of use cases, and most infrastructure needs will be met by the other online storage solutions in the HPE portfolio.
The solutions are organized here from entry-level to enterprise class.
MSA
 The MSA is a family of storage solutions that’s been around for some time and continues to evolve as storage technologies change. This is generally considered an entry-level array. The MSA two controller array offers Block storage over SAS, Fibre Channel, or iSCSI. Despite its entry-level categorization, the MSA is a solution that can provide up to 960TB of RAW capacity and nearly 200,000 IOPS.
The MSA is a family of storage solutions that’s been around for some time and continues to evolve as storage technologies change. This is generally considered an entry-level array. The MSA two controller array offers Block storage over SAS, Fibre Channel, or iSCSI. Despite its entry-level categorization, the MSA is a solution that can provide up to 960TB of RAW capacity and nearly 200,000 IOPS.
In addition to the capacity and performance, this array provides some impressive features, including:
– Thin Provisioning
– Automated Tiering
– Snapshots
– Array-based Replication
– Quality of Service
Consider the MSA if you are trying to meet the needs of a few hosts with a predictable workload profile. This solution is designed with smaller deployments in mind and where affordability is a key factor. If you are looking for deduplication, compression, or plan to scale your environment significantly, the MSA is not for you. We have used the MSA for small VMware environments and as Disk Targets in a backup solution.
StoreVirtual
 StoreVirtual defines an operating system for providing scale-out, software defined storage solutions. StoreVirtual is based on the LeftHand operating system. LeftHand was a company HP acquired in October of 2008 to give them an iSCSI solution in their portfolio. The LeftHand Operating System is designed to run on most x86-based hardware and can be deployed as a virtual machine, a hyperconverged appliance, or as a dedicated storage array.
StoreVirtual defines an operating system for providing scale-out, software defined storage solutions. StoreVirtual is based on the LeftHand operating system. LeftHand was a company HP acquired in October of 2008 to give them an iSCSI solution in their portfolio. The LeftHand Operating System is designed to run on most x86-based hardware and can be deployed as a virtual machine, a hyperconverged appliance, or as a dedicated storage array.
Regardless of how it is deployed, the StoreVirtual solution provides block storage over iSCSI or Fibre Channel. Capacities can vary depending on the method that is deployed but can go up to 576TB of RAW capacity on the SV3200 Appliance Storage Node.
The StoreVirtual uses an all-inclusive licensing model, and the feature set includes:
– Thin Provisioning
– Automated Tiering
– Snapshots
– Array-based Replication
– Multi-site Stretch Clusters
– Built-in Reporting
Like the MSA, StoreVirtual is intended for smaller deployments with predictable workloads. As a scale-out solution, the StoreVirtual provides an easy path for increasing capacity and performance simultaneously by adding one or more StoreVirtual Nodes. The StoreVirtual solution is a relatively affordable solution for the features it provides. And, if you are looking to take advantage of existing compute and storage hardware, StoreVirtual may be a good choice. We see the StoreVirtual solutions deployed in smaller to mid-sized virtual environments.
SimpliVity
 To be clear, SimpliVity is not a standalone, online storage solution. It is a hyperconverged solution that provides Storage, Compute, and Networking services in one converged solution. I am including it in these summaries because it includes storage as an important part of the overall solution and would be an alternative to needing to provide a separate storage solution for your VMware environment.
To be clear, SimpliVity is not a standalone, online storage solution. It is a hyperconverged solution that provides Storage, Compute, and Networking services in one converged solution. I am including it in these summaries because it includes storage as an important part of the overall solution and would be an alternative to needing to provide a separate storage solution for your VMware environment.
SimpliVity is specifically designed to provide all the infrastructure beneath the hypervisor layer. At this time, it is specifically for VMware environments. As a converged solution, SimpliVity provides everything you would need to support your environment. (Yes, that means backup as well!)
Here is a list of the features you’ll find in a SimpliVity solution:
– Servers & VMware
– Storage Switch
– HA Shared Storage
– Backup & Dedupe
– WAN Optimization
– Cloud Gateway
– SSD Array
– Storage Caching
– Data Protection Apps (Backup & Replication)
– Deduplication
– Compression
This solution is going to be more expensive than the MSA or StoreVirtual offerings; but, again, it provides all the infrastructure for your VMware environment. It’s more than just a storage solution. So, if you are looking to consolidate your infrastructure significantly and the workloads you are supporting have all been virtualized on VMware, this solution may be worth looking at for you.
Nimble
 The Nimble solutions offer Block storage in all-flash and hybrid-flash models delivered over iSCSI or Fibre Channel. The current offering from HPE will provide up to 294TB of RAW capacity on the hybrid-flash solution. Of course, compression and deduplication will provide much greater effective capacity dependent on data types.
The Nimble solutions offer Block storage in all-flash and hybrid-flash models delivered over iSCSI or Fibre Channel. The current offering from HPE will provide up to 294TB of RAW capacity on the hybrid-flash solution. Of course, compression and deduplication will provide much greater effective capacity dependent on data types.
The all-inclusive features of the Nimble family include:
– Thin Provisioning
– Automated Tiering
– Application Aware Snapshots
– Deduplication (all-flash)
– Quality of Service (all-flash)
– Array-based Replication
– Encryption
– InfoSight Predictive Analytics
This solution is designed to handle mixed-workloads and is perfect for mid-sized virtualized environments. InfoSight Predictive Analytics is a significant part of this solution, and I wouldn’t be surprised if it were integrated with other HPE storage solutions in the future.
Taken directly from the HPE QuickSpecs, the InfoSight Analytics provide:
– Proactive resolution. InfoSight automatically predicts and resolves 86% of problems before you even know there is an issue.
– Solves storage and non-storage problems. By collecting and correlating sensors across the infrastructure stack, InfoSight uncovers problems spanning from storage to VMs. In fact, 54% of the problems InfoSight resolves are outside of storage.
– Prevents known issues with infrastructure that learns. If a problem is detected in one system, InfoSight begins to predict the issue and inoculate other systems. Every system gets smarter and more reliable through collective installed base insights.
– The support you’ve always wanted. Automation and proactive resolution put the focus on prevention, streamlining the process, and connecting you directly to support expertise. No more answering routine support questions, sending log files, or attempting to recreate issues.
Nimble should be a consideration for any virtualized environment where you are looking for ease of use, great reporting, and performance.
3PAR
 Of course, this has been the workhorse for the enterprise storage offering from HPE since 2010. Depending on the model, the 3PAR Solution can start with 2 Controllers and go up to 8 Controllers for a single array. The 3PAR has both a hybrid and an all-flash solution. Capacities can scale to 6PB RAW in the new 9000 series of the 3PAR family. The 3PAR array delivers Block over iSCSI and Fibre Channel and can also supports SMB, NFS, and FTP/FTPS natively.
Of course, this has been the workhorse for the enterprise storage offering from HPE since 2010. Depending on the model, the 3PAR Solution can start with 2 Controllers and go up to 8 Controllers for a single array. The 3PAR has both a hybrid and an all-flash solution. Capacities can scale to 6PB RAW in the new 9000 series of the 3PAR family. The 3PAR array delivers Block over iSCSI and Fibre Channel and can also supports SMB, NFS, and FTP/FTPS natively.
The all-inclusive feature set includes:
– Thin Provisioning
– Thin Deduplication
– Thin Compression
– Snapshots
– Array-based Replication (add-on license)
– File Persona (SMB, NFS, FTP/FTPS)
– Automated Tiering
– Flash Cache
– Quality of Service
– Non-disruptive LUN Migration
– Array to Array Migration
– Reporting
– Multi-Tenancy
The 3PAR Array should be considered for a multi-workload environment where performance, availability, and scale are the top priorities.
Which One Is Right for You?
As mentioned at the beginning of the post, the goal here was to provide a summary of the primary online storage solutions now offered by HPE and to give a little guidance on where they might fit. Each of these solutions represent a different architecture, and those architectures should be understood clearly before making any final decisions. At Zunesis, we can help you understand which of these solutions might fit your needs and can walk you through the architectures of each.
Network Management Suites available today through HPE
Network management has been around since the dawn of networking. In the early days, companies like Cisco and Hewlett Packard Enterprise (HPE) would create their own proprietary management software to manage their switching products (i.e. Procurve Manager was originally an HPE-only tool until it was updated with limited 3rd party support).
This all changed in the early 2000’s when a protocol called SNMP (Simple Network Management Protocol) was standardized and introduced to switches. This allowed the management plane of the switch to communicate live statistics such as response times, CPU utilization, etc., back to a centralized network management solution in an open-standards manner. It also allowed network admins to have a “single pane of glass” into the basic statistics of their multi-vendor network. SNMP has gone through various revisions to this day but the basic principle remains the same – allowing network admins to manage a multivendor network environment from one tool.
How They’re the Same:
Airwave and IMC both utilize SNMP to communicate with 3rd party devices, and both have an extensive list in the thousands of devices that are supported from 3rd party vendors from Cisco to Netgear.
How They’re Different:
The product differentiation comes down to how these tools will be utilized by the Network Admins:
Airwave
Airwave is directed more at “campus” environments (think carpeted office space, K-12, higher ed campuses, etc.) due to how easy it is to use compared to the more daunting setup involved in IMC. Another reason for this positioning is because Airwave is a much more capable wireless management tool, giving customers much better insight into the health of their wireless network then IMC can provide.
An example of this would be the VisualRF plugin in Airwave. VisualRF provides a real-time view of their RF coverage and client positioning. This visual tool allows network engineers to see their actual RF coverage inside of a building, giving them a good idea of any existing gaps in coverage that they might need to add an additional AP to support. Airwave is licensed per device on the network, and those licenses give you access to the full software suite.
IMC
Intelligent Management Center, or IMC, is committed to being a true “nuts and bolts” engineer tool, even allowing access to IMC’s APIs, giving customers the freedom to program their own modules within the platform. For this reason, HPE has started positioning this as more of a Datacenter focused “NOC” (networks operation center) tool.
Administrators can get much more in depth with the types of SNMP traps, alarms/alerting, and even the types of information that can be reported on with the tool. The initial setup is much more intensive than an Airwave deployment, and the interface is much less user friendly than Airwave, However, you can get extremely detailed real-time information out of the IMC platform – especially when it’s monitoring Aruba (ProCurve) or Comware switches. An example of this would be the QoS Manager plugin, which gives network administrators the ability to define a new global policy or make changes to an existing QoS policy and push those changes out to the network.
Currently, the only wireless management that IMC supports is for the legacy HPE wireless solutions MSM and Unified Wireless, but an “Airwave plugin” is in the works to bridge the gap to include Aruba wireless deployments. IMC is sold as modular software – the base platform is very capable; but to get some specific functionality, such as the QoS Management, you need to license the module. IMC is also licensed by device count in the base platform; however, some of the modules have different licensing schemes.
HPE has committed to continued product development on both platforms. As of right now, there are no early warning signs of one product cannibalizing the other. Choosing which product is rightyou’re your environment really depends on what you are hoping to get out of the platform. If you’re looking for something that’s easy to use with awesome built-in reporting, look into Airwave. If, on the other hand, you need an extremely customizable tool that can report on virtually any network statistic under the sun, IMC is your ticket. If you’re not sure which is the better fit for your organization, we are happy to sit down, discuss your needs, and dive deeper into the platforms in order to make the appropriate recommendation.
The success of any service oriented business depends largely on how effective its employees communicate the value they provide their customers. This becomes paramount for Big Data / Analytics service providers where identifying and communicating “actionable insight” to their customers is the value. The ability to communicate analytics and insight effectively drives the quality of the relationship between the provider and client. Effective communication has become part of the job for any tech savvy analyst.
Whether working with internal or external customers, an analyst’s ability to communicate clear messages about the data and actions needed is crucial. The quality and clarity of communication about the insight found can have a tremendous influence to drive the actions that were identified from the analysis. From my experience being in the insight business at iWeSocial and working with clients across many different industries – communicating insights effectively will dictate the success or failure of any project.
An effective analyst will be able to combine visual (show the supporting data) and verbal (communicate the insight) messages to convey the findings, empowering the end user to act on the insight.
How Do You Communicate Insight Effectively?
 Effective insight communication refers to the ability to tell a story through data to address business challenges. To be able to answer these questions:
Effective insight communication refers to the ability to tell a story through data to address business challenges. To be able to answer these questions:
- What happened?
- What is currently happening?
- What’s going to happen?
Communicating insight involves connecting the dots between the overall business challenge down to what we identify as corrective action. No matter what the deliverables, to communicate insight effectively starts with setting clear goals for the analysis.
Another key factor of successful insight communication is to know your audience. Are you speaking to an executive team focused on overall business drivers or the head of marketing or sales? Each will have their own set of questions they are wanting the data to help answer. For example, the sales executive may want to understand how to increase sales productivity or increase customer acquisition. Meanwhile, the marketing executive will want to know about marketing effectiveness and customer engagement.
From my experience in delivering insight to a variety of clients, I have noticed several themes. Specifically, to be able to communicate your insight effectively, I recommend that you keep the following in mind:
Know your audience
- Their pain-points
- Business challenges they face
- Questions they are trying to answer
Keep it simple
- Avoid technical jargon
- Simple, actionable findings
- Leverage clear visualization
Connect Insight to the Bottom Line
- Increase in revenue
- Reduction of cost structure
- Increase in average spend per customer
In summary, effective insight communication is the ability to convey your findings to key stakeholders to drive action – so they can do something differently than the way they’ve been doing it. With effective insight communication, always try to provide a clear answer to a business questions, not merely providing another piece of data. The insight should focus on the business impact; if the insight doesn’t lead to an action, then question whether to include it at all.
The success of any business depends largely on how effective they are at using data that’s turned into insight to drive their business forward. The question is: “How can we communicate these insights more effectively for greater business return?”
Winning with Purpose
I relish competition! Maybe it is because I grew up playing sports and learning that I enjoyed competing and winning way more than losing. Maybe it is because winning, in the competitive arena, demands your very best. Maybe it’s because winning in business normally requires a team effort, and I like working in a team setting. Whatever it is, competition is something I have always loved. But winning, achievement, and reaching a certain level of success can be hollow without purpose. After 30+ years of competing each and every day, I have come to the conclusion that winning is really fun, but sharing the spoils of winning creates fulfillment and purpose.
I also believe that the juices that start to flow in the midst of a competitive battle can be the same juices that ignite a compassionate responsibility for those in our community. What I have learned over the years is that capitalism and compassion can co-exist and that — gasp! — business can be a force for good.
How Can Business Be a Force for Good?
 I personally know a great many smart and good-hearted business leaders in the Colorado community. Some of the very best people I know are CEOs, business owners, and entrepreneurs. They care about their employees and the people in their communities a great deal. Most of these business leaders are willing (and wanting) to engage in helping others, but there are so many daunting questions:
I personally know a great many smart and good-hearted business leaders in the Colorado community. Some of the very best people I know are CEOs, business owners, and entrepreneurs. They care about their employees and the people in their communities a great deal. Most of these business leaders are willing (and wanting) to engage in helping others, but there are so many daunting questions:
- What organization should we support?
- How can my employees get involved?
- How much time will this require?
- Will our involvement send the wrong signal to my employees, shareholders, customers, or partners?
These are common questions that can stop us from taking action.
Getting Companies Involved
For nearly 10 years, my company has been actively involved with Habitat for Humanity of Metro Denver. Zunesis employees have worked diligently to build homes for hard working families in the Denver community. Each year we do a build day where we all put on hard hats and work together to help construct the home we are sponsoring that year – “the Zunesis home.”
 This engagement has served as a very practical way for my small business to give back and support our neighbors in our own community. We even get to work side-by-side with families who will be moving into the home when completed. Seeing the lives of hard working families in our community completely changed by having a secure, safe, and stable place that they call home is something that never loses its luster or excitement.
This engagement has served as a very practical way for my small business to give back and support our neighbors in our own community. We even get to work side-by-side with families who will be moving into the home when completed. Seeing the lives of hard working families in our community completely changed by having a secure, safe, and stable place that they call home is something that never loses its luster or excitement.
Being part of something that transcends success in business and tangibly blesses people in our community has been good for my employees and our business. I’m guessing that many business leaders and CEOs also want to get involved in supporting their communities, but they may not know how to get started. I learned that a great place to start is to ask your employees. It is likely that you will find some great ideas and maybe some passion that can be leveraged to get the ball rolling.
I would also encourage you to talk with other CEOs and business leaders about what they are doing. There are so many great ways to give back, and most organizations have a method and a process for you to get engaged. If you want to know about how to get engaged with Habitat for Humanity, I would be happy to share my personal experience and get you connected to the right people. Wouldn’t it be wonderful if Colorado became the place where Capitalism and Compassion freely found common ground?
Ransomware
Ransomware is a form of Malware that, once activated, can deny access to files on smartphones, personal computers, and servers. In some forms, a Ransomware attack will go beyond denial of service; and the Cyber Criminals will threaten to publish your data. As the name suggests, Ransomware offers to unlock your files if you pay a ransom. While modern day Ransomware attacks can be traced back to 2005, the history of Ransomware goes back as far as 1989. The pace of these attacks doesn’t appear to be slowing down. In 2016, many sources had payouts approaching $1 billion by the end of the year.
 As you might imagine, having been around for such a long time, Cyber Criminals have developed several ways to launch Ransomware attacks. Within the data center, our first goal is to keep these attacks out of our systems and away from our production data. IT Professionals protect their production environments by using firewalls, anti-virus software, proper authentication practices, and end-user education, among other measures.
As you might imagine, having been around for such a long time, Cyber Criminals have developed several ways to launch Ransomware attacks. Within the data center, our first goal is to keep these attacks out of our systems and away from our production data. IT Professionals protect their production environments by using firewalls, anti-virus software, proper authentication practices, and end-user education, among other measures.
Despite these efforts, there is always the possibility that an attack is successful and systems are compromised. In the event our corporate files do become impacted by a Ransomware event, we must be able to rely on our data backups to restore systems and not be forced to pay a ransom. However, this begs an important question:
How can we be sure that our backups are protected?
This is a question that is being asked more frequently by our clients.
First, we need to acknowledge that backups are not free from the risk of being attacked by Ransomware. However, there are steps that can be taken to reduce the risk of exposure, even if the Malware has found its way into the Production infrastructure. These steps fall generally into three categories: Security, Replication, and Isolation.
Security
- Provide a dedicated host for the backup application.
- Disable network interfaces not in use on the hosts involved in performing backups.
- Restrict the number of user accounts with access to the backup application and the host onto which it is installed.
- Disable access to communications ports and protocols not needed for the backup operation (i.e., HTTP, FTP, Telnet, etc.).
- Disable accounts not used for operation of the backup process.
- Disable services not used for operation of the backup process.
- Utilize best practices for user credentials (password complexity, aging, etc.).
- Keep Security Patches up to date on the host and the backup application itself.
Replication
 Maintain at least three (3) copies of the backup files on at least two (2) different types of media and keep at least one (1) of those copies offsite. (3-2-1 Rule)
Maintain at least three (3) copies of the backup files on at least two (2) different types of media and keep at least one (1) of those copies offsite. (3-2-1 Rule)- Consider keeping a copy of your backup on tape or on spinning disk that is not connected to the network unless backups are running. The point here is to maintain an offline copy.
- If replicating between backup appliances, consider building a delay into replication to keep from immediately replicating files infected with the Ransomware. This tactic may allow you time to discover the proliferation of an attack and keep it from spreading to your replication target.
- Utilize hardware based snapshots on Production storage arrays and backup appliances (these are not usually presented to a file system and are therefore not subject to attack).
- Maintain multiple restore points using snapshots and the backup software.
Isolation
- Maintain separate hosts for the backup infrastructure.
- Utilize offline backup media (tape or disconnected disk targets).
- Utilize hardware based snapshots.
- Utilize Cloud connected backup targets.
The steps listed above are intended to provide guidelines for protecting your backup data from Ransomware. Execution of these steps is dependent on your own infrastructure, the type of backup targets you employ, the backup software you use, etc.
There are many resources available that delve into this topic in greater detail. The intent of this post is simply to make sure you are including backups in your strategy to protect the enterprise against Ransomware attacks. And, of course, Zunesis is ready to help you design a strategy that fits your needs and is right for your environment.




