Zunesis Earns Recognition on the 2022 CRN® Tech Elite 250 List
Denver, CO March 21, 2022 — Zunesis, today announced that CRN®, a brand of The Channel Company, will feature Zunesis on its 2022 Tech Elite 250 list. This list recognizes solution providers across the U.S. and Canada that have earned the highest level of technical certifications from leading technology suppliers such as Hewlett Packard Enterprise, Dell Technologies, Cisco and more. Companies chosen for the Tech Elite 250 list have distinguished themselves as dedicated and passionate solution providers willing to go above and beyond for their customers by ensuring they have the training and technical know-how necessary to provide expert-level service.
 These solution providers know their customers depend on their training and expertise to help them overcome today’s IT challenges and achieve full digital transformation across the enterprise. In order to provide that expert service and care, solution providers must maintain consistently high levels of training and certification from IT vendors and achieve the highest tiers within those vendors’ partner programs.
These solution providers know their customers depend on their training and expertise to help them overcome today’s IT challenges and achieve full digital transformation across the enterprise. In order to provide that expert service and care, solution providers must maintain consistently high levels of training and certification from IT vendors and achieve the highest tiers within those vendors’ partner programs.
“CRN’s annual Tech Elite 250 list recognizes solution providers that have earned top-level certifications from key technology suppliers and proven their ability to consistently meet the high standards of their customers and partners,” said Blaine Raddon, CEO of The Channel Company. “Solution providers featured on this list have maintained a consistent focus on innovation and have built a comprehensive understanding of the ever-evolving technologies and practices that enable ongoing success in the IT channel. We’re proud to honor them in this manner.”
Coverage of the Tech Elite 250 will be featured in the April issue of CRN Magazine and online at www.CRN.com/techelite250.
About Zunesis
Zunesis can help you compete in the digital economy with infrastructure transformation aligned to your business goals. We have more than 17 years of experience serving customers throughout the Rocky Mountain Region and Southwestern U.S., including Colorado, Montana, Wyoming, and Nevada. Our staff of solution architects have decades of expertise and in-depth product knowledge to customize IT solutions with success. www.zunesis.com
Follow Zunesis: Twitter, LinkedIn, and Facebook.
Zunesis Contact:
Rachael Stiedemann
Zunesis
rachael.stiedemann@zunesis.com
About The Channel Company
The Channel Company enables breakthrough IT channel performance with our dominant media, engaging events, expert consulting and education, and innovative marketing services and platforms. As the channel catalyst, we connect and empower technology suppliers, solution providers, and end users. Backed by more than 30 years of unequalled channel experience, we draw from our deep knowledge to envision innovative new solutions for ever-evolving challenges in the technology marketplace. www.thechannelcompany.com
Follow The Channel Company: Twitter, LinkedIn, and Facebook.
© 2022. CRN is a registered trademark of The Channel Company, LLC. All rights reserved.
The Channel Company Contact:
Jennifer Hogan
The Channel Company
jhogan@thechannelcompany.com
Wouldn’t it be nice to receive a non-disruptive upgrade on your emotional well-being? We all understand that we are energy undergoing a physical, human, material experience. Enjoying this experience while doing less and receiving more is the topic of conversation.
What You Resist Will Continue to Persist!
This is not a feel-happy saying commonly found on a coffee mug. It is the fundamental, universal law upon which all quantum physics is based. What we focus our attention on expands, what we resist persists, and what we do not give energy to will eventually de-manifest from our experience.
Put in other words, nobody owes you anything except you owning yourself! No matter which way you spin it, everything comes down to solidifying and strengthening your connection with that connection to your higher self. None of what I do today – managing multiple businesses, consoling three tiny humans, being personally connected to some of the most intelligent people in the western hemisphere – would be possible without my chief focus of gratitude for self-love.
Love of self is the most potent energetic vibration existing in the 3D realm. It cannot be handed to you by any external thing or person. More importantly, we can escape the “hamster wheel” trap of constantly comparing our material accomplishments and possessions to those of others. We can have less stressful lives when we begin to understand the fundamental law of quantum physics.
The RASHA
What you’re about to discover will accelerate your soul’s conscious evolution!
If you haven’t noticed, we are all going through a major upheaval in our country (and on the planet). Finding the energy, time, or focus for meditation, yoga, or self-love is, to say the least, difficult. As we put these things on the back burner, the World Health Organization and American Medical Association say up to 90% of all illnesses in modern society are stress-related. In today’s world, each of us is constantly under stress. Stress has become part of our everyday routine. Sure, some pills we take will temporarily alleviate the symptoms, but putting a band-aid over these symptoms is not the solution. The honest answer is to get to the core of the problem, balance our bodies and reduce stress.
 A remarkable tool to help us get back on track is a scalar energy therapy. Scalar waves have the power to influence the morphogenetic field—the blueprint of our physical body. Rasha is a scalar plasma technology that harmonizes and balances the autonomic nervous system to move from fight-or-flight stress response to a more restful and relaxed state where healing can occur.
A remarkable tool to help us get back on track is a scalar energy therapy. Scalar waves have the power to influence the morphogenetic field—the blueprint of our physical body. Rasha is a scalar plasma technology that harmonizes and balances the autonomic nervous system to move from fight-or-flight stress response to a more restful and relaxed state where healing can occur.
Nikola Tesla, a genius mind, and an exceptional inventor, said, “If you want to find the secrets of the universe, think in terms of energy, frequency, and vibration.” Scalar waves transmit energy and information, and they occupy space. Patented Tesla coils used in the RASHA can generate scalar energy. By harnessing the power of scalar energy, RASHA allows you to re-discover your natural yet dormant power of consciousness expansion leading to deeper and more meaningful consciousness.
Other benefits of scalar energy are:
- Weight Loss
- Energy Boost & Loss of Chronic Fatigue
- Muscle & Joint Pain Release
- Sleep Disorders
- Depression Support
- Focus & Clarity
- Mind Expansion
Frequency Accretion in Progress
I have recently used the RASHA, and I’m told that each time you use it is better than the last. The immediate effects are genuinely profound. At first, you fight the belief that a machine can adjust your stress. Once you give in, you leave with a centered and emotionally balanced self. The set up is simple. You sit in a relaxing lounge chair and place a pair of headphones on your head that play a series of vibrational tones. The chair begins to resonate the tones and immediately your whole body is relaxed. Thoughts begin to rush in and after so long the busy monkeys quite down. The core of your ancestral DNA begins to wake up. New thoughts, feelings, and emotions begin to float in, and a sense of peace lingers.
Coherence Technology
While I don’t currently have the means to sell this brilliant technology, I have many other meaningful ways to eliminate the stress from managing your busy IT environment. Zunesis can consciously guide you with the following IT stack assessment, upgrades, migrations, architectural designs, and data center refreshes. Once you’ve upgraded, we can monitor and manage your environment 24/7.
Our senior Microsoft engineer can help eliminate the frustration of figuring out your next license purchase or Share Point migrations. We work closely with many industry-leading manufacturers to provide you the best fit for your organization’s needs. If you don’t have time or access to the RASHA, the next best thing is to call us here at Zunesis to eliminate the noise. If you would like to learn where you can find a RASHA studio in the Las Vegas area, please contact me.
Education and Technology
I recently had the pleasure of attending the 2022 Colorado Association of Leaders in Education Technology (CALET) “Winter Leadership Conference” as a sponsor (on behalf of Aruba Networks and Zunesis.) This annual event brings together Information Technology leaders from primary education institutions all over the state of Colorado. They discuss new innovations, challenges, best practices, and ideas for the future.
Technology has helped aid education for decades. Its significance has increased substantially over the last few years, especially so after the onset of the COVID-19 Pandemic. While manning the Aruba/Zunesis booth, I had great conversations with IT Directors, Network Admins, CTO’s and others, about technological challenges they face in today’s K-12 education landscape. I shared with attendees about the many ways that we are trying to help K-12 education customers navigate these challenge. I wanted to share with the rest of you some ways that we can help. Particularly with Aruba Networks.
High-Performance Wireless Networks for K-12 Student Success
- Aruba’s Wi-Fi 6 (802.11.ax) infrastructure is designed to support schools of any size with always-on secure connectivity. Seamless roaming allows network access on the move. While high-density capabilities support large classrooms, auditoriums, and outdoor facilities. Learning management and unified communications systems can be prioritized to deliver latency-sensitive data, voice, and video without delay, loss, or jitter.
- Unified infrastructure: Aruba offers a unified infrastructure from edge to core with wired and wireless networks that work together to deliver a consistent and secure network experience. Aruba designs its own semiconductors so its switches can provide blazing fast and highly granular visibility into the performance of the switching fabric. SmartRate power-over-Ethernet (PoE) allows Wi-Fi 6 access points to operate at >1Gbps over existing cabling, eliminating the need to rip and replace cable plants to obtain multi-gigabit wireless performance.
- The Network Analytics Engine (NAE), included with AOS-CX, provides a built-in framework for monitoring and troubleshooting networks. NAE detects problems in real-time and analyzes trends using the time-series database so IT can predict future performance and security issues.
- With ClearPass Policy Manager, devices are profiled, authenticated, authorized, and tightly managed network access using granular, policy-based access controls once they are identified on the network. Users and devices have restricted access to only those network, IT, and application resources for which they have been approved. ClearPass also ensures that users and devices are compliant with regulations governing student privacy and personally identifiable information
- Aruba Wi-Fi 6 access points include radios for wayfinding, geofencing, location tracking, sensor monitoring, door locking, and actuator control. These capabilities transform Aruba access points into secure, multi-purpose communication systems that are both network access on-ramps and full-fledged IoT platforms.
- AI-based Maching Learning: Aruba delivers customized recommendations through AI-based machine learning to improve network and application performance based on anonymized comparison with peer environments. If a change could increase performance by 10%, it is recommended to the Network Admin who can then authorize the settings to change. Aruba User Experience Insight provides IT a real-time view of the end-user experience and clear action steps to resolve any issues before a service ticket is opened. These powerful tools bring much-needed help to enable already overwhelmed IT staff to take necessary action and stay ahead of issues.
E-rate
I covered some key technological solutions that Aruba Networks is offering but I didn’t even get to the best part: E-rate. School districts across the country depend on E-rate funding to make infrastructure systems and telecommunication more affordable. Aruba not only has an entire catalog of E-rate eligible networking solutions but even provides an entire team of E-rate professionals to guide customers through the process and maximize their IT spend.
Contact Zunesis to find out how we can assist K-12 schools.
Additional Resources:
Aruba Solutions for Primary Education
Aruba Solutions Primary Education E-rate
The Pandemic has disrupted supply chains around the world for a wide range of goods, including electronics and other crucial pieces of IT equipment. Supplier relationship management has been put to task. Companies struggle to source needed parts, manage inventories and more. The current situation is undoubtedly causing stress for IT leaders. This unique situation also gives organizations the opportunity to reset their IT supply chain visibility and security policies.
Demand + Shortages = Extended Lead Times
The initial pandemic-driven remote-work mandate appears to be a permanent shift in many workers converting to a hybrid or full-time telework. This in turn led to a surge in electronics sales. With both increased demand and the fallout from recovering closures and continuing understaffed factories in China, this created a domino effect of shortages of both laptops and datacenter to edge supporting architecture. As 2022 kicks off, average lead-times for laptops and displays are 16 weeks, 8 to 16 weeks for servers and storage and 8 weeks to 9 months for networking gear.
Security Risks and New Requirements
The supply chain shortages create several risks for IT professionals. This includes third-party service providers’ physical or virtual access to information systems, software or intellectual property; poor information security practices at lower-tier suppliers; compromised software or hardware purchased from suppliers; and software security vulnerabilities in supply chain management or supplier systems.
To combat these new risks, many agencies are incorporating new security requirements into every request for proposal and contract, including the following:
- Having a security team work onsite with any new vendor to address any vulnerabilities or security gaps
- A “one strike and you’re out” policy regarding vendor products that are either counterfeit or do not meet specifications.
- Tightly controlled component purchases
- Secure software lifecycle development programs and training for all engineers in the product lifecycle
- A security handshake between software and hardware. This is where a secure booting process looks for authentication codes and will not boot if the codes are not recognized.
Most importantly, working together with suppliers is more important than ever. Especially this is prevalent in small or mid-size private companies who want to be nimble enough to juggle resources to help one customer without hurting another. Small to mid-sized private suppliers are often more flexible with financial options. These options include accelerating payments and changing contract terms so receivables are more easily factored, providing a dynamic discounting program or leveraging supply-chain finance programs.
Long-Term Order Forecasts
Letting the supplier have longer-term order forecasts will ensure priority status for supply delivery. Likewise, make a point to report supply constraint updates monthly. This will allow insight into the changing supply recovering times. The more a supplier can rely on and trust what it’s hearing from a customer, the more it can make the critical business decisions that can help it get through the crisis.
By addressing supply chain visibility and security now, companies will get through the current crisis. This will make their IT supply chains more resilient and secure in the years to come.
Pearl Harbor
Dec 7th….The day Pearl Harbor was attacked. The day that the United States was thrust into World War II. It is a day that shaped an entire generation. This began somewhat of a chain reaction all through American society and culture. It spawned many books and movies that retold this fateful day. Some of these were good and some of them were bad (we are looking at you Ben Affleck). But, there was always one overriding message in all of these retellings: the American spirit shone through. Our Armed forces stood up as one. They collectively went to avenge and defend their country and their fellow brothers in arms. There were volunteers to join the Armed Forces lining up around the block of any recruiting station, just days after the attacks. Our factories, research, and development all immediately went into over-drive.
One interesting by product of this happening, American factories never scaled back once the war was over. America stepped in to a global vacuum after the war. Americans helped supply and rebuild much of the war torn world. This, of course led to other long term issues of war and strife, but that is a blog for another day.
Impact of Innovation and Technology
As many of you may already know, Pearl Harbor could have been much worse. The American aircraft carriers were not at port. These carriers ended up being the single most important ship of the war. Had they been there and sunk, WWII would most likely have gone drastically (or even tragically different).
America also had a fledgling technology called radar. While this was not used to quite the effect it should have been, it still provided an advanced warning that was not available only a few years earlier. It has since gone on to become an extremely important technology in not just armed forces applications, but also in our air traffic control, weather, and geological fields.
This was not the only innovation that came out of World War II. Jeeps became the standard for light transportation and support vehicles in this war. The basic design behind these vehicles carries on to one of the most popular car brands on the road today. And of course, the atomic bomb was also developed and used to devasting effect.
The Jet Engine
It could be argued that the jet engine was the single most historical and culturally significant innovation that came from WWII. This technology was used sparingly in actual combat. After the war was completed, this technology went on to change many aspects of both military and civilian life. The jet engine paved the way for us to see and visit countries, and it revolutionized the way we do business. Because of the jet engine, American culture spread very quickly (for good or for bad) throughout the world.
But was it more of a significant innovation than the atomic bomb? It is an interesting discussion, partially because both are so closely related. They were both used so thoroughly by our armed forces and politicians for many years, even still to this day.
Birth of the Computer
All this being said, I would like to introduce one more piece of technology that I feel give them both a run as being the most vital, important, and culturally significant innovation that came from WWII. This technology definitely got a much slower start out of the gate. It was used in only one specific way for so long that some of you out there might not realize that it was first developed during WWII. The technology I am referring to is the computer.
The term “computer” was actually a reference to a group of mostly women who performed advanced calculations by hand. During the war, the armed forces developed machines for advanced calculations to use in ballistics and to determine trajectories. The group that had been doing these calculations by hand were now employed to program these machines. Obviously, these machines stayed locked away for military uses for some time before companies started working with this same group of people to develop these machines for other uses.
Computers stayed in the background as technologies like jet engines really took off (pun intended). It stayed like this until the personal computer was developed. This was the first stepping stone to the computer not just becoming a vital piece of our work life, but changing the way we live. The jet engine may have introduced us to communities from around the globe, the computer created an actual global community. Computers have also improved upon the jet engine and air travel in general. They make them more efficient and safer. This has in turn allowed the price of airline tickets to be more affordable and used more widely.
A Day To Remember
December 7th, will and should always live on in the collective memory of the American people. As it has been so eloquently put, it is “a day that will live in infamy”. We also should not forget the tragic loss of life on this day, but the entirety of the second world war. I give my heart felt thanks to all that were there, and all that continued to serve, and all that serve today.
I also give my thanks to the men and women who used technology to help win that war and then bring this to our everyday lives. They, and all those that have come after (both civilian and military), are an ongoing example of bravery, brilliance, and determination. I, for one, take pride in those who have come before, and I hope that this generation will continue to strive to help make this world a better place.
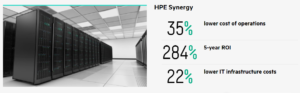
HPE Synergy- Six Years of Innovation
It has been a while since we talked about the Hewlett Packard Enterprise Synergy platform. It is hard to believe it was announced in 2015 and is already 6 years old. This platform was definitely built with the future in mind. It was designed from the ground up to support future technologies and communications bandwidth. Server hardware has taken a back seat to the conversations around Cloud, Hybrid Cloud, HyperConverged, Security, Ransomware and Anything as a Service.
Since 2015, the Compute Modules have migrated from the Gen9, to the Gen10 and now the Gen10 Plus. We still have a lot of conversations around hardware in the data center. The goal around the Synergy platform is to provide a “cloud-like” (on demand resources) experience in your data center.
Cloud-Like Experience
The HPE Synergy platform is defined as a composable, software-defined infrastructure that allows you to provide that cloud-like experience. This platform enables you to compose fluid pools of resources (physical or virtual compute, storage, and fabric) to meet the requirements of your workload. This can be done using the unified API to simplify and automate deployments. Using this API, you can provision the required resources with a single line of code.
The design of the Synergy platform allows you to manage one infrastructure that can quickly scale and reduce complexity in your environment. This infrastructure will support current- and next-gen apps, each with vastly diverse infrastructure requirements and service-level objectives. The applications can run on physical hardware, virtual hardware or containers, all in the same frame.
Industry Leading Security
As will all HPE Servers, the Gen10 and Gen10 Plus has provided industry leading security. They have designed and implemented an enhanced, holistic, 360-degree view to security that begins in the manufacturing supply chain and concludes with a safeguarded, end-of-life decommissioning.
This all starts with the Silicon root of trust that is built into all Gen10 and Gen10 Plus servers. The Silicon Root of Trust from Hewlett Packard Enterprise (HPE) has been designated a 2019 Cyber Catalyst cybersecurity solution. It protects against firmware attacks, detects compromised firmware or malware, and helps to rapidly recover the server in the event of an attack. This starts with the HPE developed and proprietary iLO 5 management. The iLO 5 ensures all firmware and the BIOS have the proper signature before it allows the machine to power on.
This level of security protects all firmware and BIOS through a key programmed into chip silicon at a TAA compliant chip production facility. It also integrates security with HPE Secure Start and Secure Boot to protect all BIOS, firmware, SPS, IE and boot sequence. The recovery process automatically quarantines compromised BIOS and firmware, then re-flashes with a known good image.
Budget Savings
With composable compute delivered as an on-premises cloud service, you’ll gain agility and avoid costly manual configuration and management of compute resources. When coupled with HPE GreenLake, you will have a powerful, software-defined, composable compute infrastructure that composes physical and virtual compute, storage, and fabric pools into any configuration for any application. If you choose the pay-per-use model for on-premises compute assets, it will enable you to align IT spend with actual usage. You only pay for what you use above a reserve. This model will provide you with near-real-time visibility into your usage data, and you can set budgets, create reports, and build rules-based insights.
What’s New in HPE Synergy?
So what’s new in HPE Synergy? The latest compute modules announced is the HPE Synergy 480 Gen10 Plus. This new compute module is an all-new design around Intel 3rd Generation Xeon Scalable Processors. It can provide up to a 40% increase in performance over earlier processor generations. This performance gain is achieved with improvements to the product line design around the processor, memory, storage, and boot options.
The HPE Synergy 480 Gen10 Plus compute module delivers the performance, efficiency, and flexibility of a 2-socket server to support the most workloads. The Gen10 Plus provides more cores for a new level of workload performance and expanding ESXi VMs, expanded the memory DIMM socket count to 16 slots per socket, with 8 channels @ 3200 MT/S increased speed. The new Gen10 Plus has also expanded the capacity and persistence of the Intel Optane 200 memory support.
There are many additional upgrades and improvements to the Synergy Frame, more information can be found at HPE Synergy Composable Software Defined Infrastructure Platform | HPE.
Contact Zunesis today to find out more about HPE Synergy.
High Availability
High availability has been a staple feature in datacenters for years. Keeping the infrastructure running and the lights on is imperative for companies in a world where small amounts of downtime can result in massive losses. As a company’s data becomes more valuable, it becomes even more important to extend that high availability to include their storage.
Storage-Based Replication
This is where storage-based replication comes in. Immediate access to data becomes crucial in case of a failure at the primary location.
Replication is an approach to high availability that stores data in multiple locations. Data is immediately replicated to those multiple sites whenever a change is made or data is added. This allows you to retrieve that data from any of the sites. These sites could be physical datacenters owned by the organization, or geographically separate cloud instances like Azure or AWS.
Since data is immediately replicated to secondary storage as it is written to primary storage, losses can be minimized to seconds, or even eliminated completely should the primary site go down. Generally, this is controlled by software, but more and more storage arrays are being built with integrated replication making it more efficient and easier to set up.
Typically, integrated replication requires storage arrays to be either connected physically, or in a storage area network or SAN. The arrays need the ability to talk to each other at all times in order to send data to the other array as soon as it is written on the first. These replication times tend to be measured in milliseconds.
HPE Alletra’s Peer Persistence
HPE Alletra’s peer persistence is a great example of storage-based replication. Two Alletra arrays that exist on the same subnet can become replication partners. With response times under 5 ms, the arrays can get any data written to one array copied over to the other almost instantaneously. Add in some extra features like load balancing between storage pools and a 99.9999% uptime, companies can be sure their data is always safe.
Another way of setting up replication is to use software. There are many vendors, and even windows server can be used. This type of replication usually involves clustering hardware together to make identical environments that mirror each other and can be used interchangeably.
How is this Different from Backups?
So how does this differ from backups? A backup is a copy of data from a certain point in time. Replication is copied immediately. Any change to primary data is immediately replicated and no restore points are created. Backups create and store restore points from multiple times allowing you to recover from past data sets if needed.
Backups are critical in the event of corrupted or lost data. So, if a hacker encrypts your data, or an employee deletes files, you can recover all that from a previous point in time. You can’t rely on replication for data recovery. This is because any encryption or deletion is immediately replicated, making your second copy useless.
Both are critical to ensuring access to a company’s data at all times. As data is becoming more and more valuable to data-driven companies, so are the technologies used to safeguard that data.
Contact Zunesis to learn more about data storage protection offerings.
The sun is getting lower on the horizon of my time with Zunesis. After 17 years as the CEO of the company, I will be retiring in a few months. We had the good fortune of selling Zunesis and merging with a great company headquartered in Boulder, CO – Absolute Performance Inc. I am confident that the future for the combined company is very bright.
The past 17 years have been filled with excitement and challenge, great days and tough days, and every emotion and experience in between. As I reflect on the past 17+ years, my heart is filled with gratitude for the employees of Zunesis. I am confident that Zunesis and all of the employees with whom I’ve worked side by side will continue to do ever bigger and better things as the future unfolds.
I’d like to take this opportunity to express my gratitude to the employees of Zunesis current and past. The success of the company is 100% linked to the quality, professionalism and hard work of many Zunesis employees over the years. Our mission has always been to make the life of our customers better. Thankfully, we were able to attract individuals who shared this value. We also strongly believe in teamwork and sharing in success and adversity along the way. Our engineers have always been ready and willing to jump on a call to help one of their fellow engineers or one of our customers in a time of need.
I have really enjoyed leading the sales team and watching individuals grow and develop. I have also enjoyed being a small part of developing strategies and plans to bring greater value to our clients. We would get deals done in a way that created a win-win for everyone. Working together as a unified team to make the life of our customers better cultivated a higher purpose and an enjoyable environment in which to work and deliver spectacular business results.
17 years is a long time to be together. Over these years, we celebrated the birth of children and grandchildren and grieved the loss of parents and other loved ones. We watched employees battle life threatening disease and personal challenge. We watched marriages take place and enjoyed great celebrations together at the Broadmoor for annual Christmas parties. We worked together for many years to make a huge difference in our community through Habitat for Humanity.
Over the years, I have felt the support and encouragement of so many Zunesis employees. I have laughed and enjoyed your sense of humor, wit, and the way you enjoy life. I have also had employees who cared enough for me to point out my blind spots and hold me accountable. I sincerely appreciate the patience that Zunesis employees showed to me as God worked to sand off the many rough edges of my leadership.
When the sun does set on my career, I will reflect on my time with the people of Zunesis with great satisfaction, tremendous joy, and most importantly, immense gratitude. Thanks to the all the employees for making my life better and for being a friend, co-worker, and inspiration to me for so many years. You are the best of the best and you made me much better. God bless you and never forget how much you mean to me.
Stranger Danger
I’m sure all of us when were younger were taught Stranger Danger. We needed to be cautious of any strangers we met while walking to and from school or in any new places. Today, the strangers that some of us fear the most are of the cyber kind. They can steal our livelihood, identity and more with a few clicks.
Businesses are becoming victims of this Stranger Danger every day. Cyber crime rose by over 600% during the pandemic. It is estimated by 2025, the cost of cybercrime worldwide for companies will be $10.5 trillion. Unfortunately the pandemic amplified cybercrime due to the uncertainty around remote working and how to protect your business.
Many businesses are not prepared for cyber attacks and do not educate their employees on best practices to help prevent these attacks from happening. The month of October celebrates cybersecurity awareness. Education is the one of the biggest tools going forward to fight the Cyber Stranger.
Current State of CyberSecurity
There are some staggering stats surrounding businesses today and the safety of their data. The numbers are only increasing as new threats appear and businesses do not offer the appropriate resources to combat this problem.
A study by Accenture reports that 43% of cyber attacks target small businesses, and under a sixth are equipped to prevent those attacks.
On average, it takes a company 197 days to discover a cybersecurity breach. Needless to say, the longer it takes to discover a security breach, the more a company’s reputation and assets suffer.
A few more stats:
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Email is responsible for around 94% of all malware.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps are blocked daily on the internet.
Common Types of Cyber Attacks
64% of companies worldwide have experienced at least one form of cyber attack in the past year. What are the most common ones that businesses and their employees see?
- Phishing: A type of online scam that involves sending an email or other virtual communication impersonating a source that would usually be seen as reputable, such as a bank or an internet service provider. 91% of all cyber attacks start with a phishing email.
- Malware: Malicious software that gets downloaded onto devices without one’s consent. It causes devices to crash or can allow hackers to view computer activity, access files, and steal information. 27% of malware infections originate from infected USBs.
- Man-in-the-middle (MITM) attack: This occurs when a user intercepts communication between two people, or between one person and a machine. For example, a hacker might guide a user into a fraudulent site that appears to be the user’s bank’s website to collect their data. According to Netcraft, 95% of HTTPS servers are vulnerable to these attacks.
CyberSecurity Best Practices
A recent survey found that 61 percent of employees failed a basic quiz on cybersecurity fundamentals. With the average company spending only 5 percent of its IT budget on employee training, it’s clear that education is an opportunity for many organizations in the future.
Here are just a few best practices to follow:
- Avoid Pop-ups, unknown emails and links: Malware infections are among the most common cybersecurity threats organizations face. Having up-to-date virus scan and spam detection software is a great safety net, but it’s also critical that all users are trained to understand the dangers of clicking on unusual links, pop-ups or emails.
- Use strong password protection and authentication: It’s important to require all users to create strong, difficult-to-guess passwords and credentials for their accounts and change them often. Consider multifactor authentication (MFA), which requires an additional token of identifying code to access systems. 63% of data breaches result from week or stolen passwords.
- Enable firewall protection at work and at home: Firewalls are important gatekeepers, restricting traffic in, out or within a private home or business network.
- Back up data: Regularly backing up critical data is key to defeating ransomware and to business continuity in general.
- Control physical access: Preventing access or use of desktops, laptops and mobile devices should be a high priority as these can be easily stolen or lost. Make sure such devices are set to lock when unattended and grant only limited administrative privileges for such hardware.
- Minimize data transfers: Be mindful of how many devices contain important data and try to make transfers as minimally as possible.
- Verify download sources: Before making any downloads, scan the website you’re downloading from to ensure that it’s verified, and only click on legitimate download links.
- Keep software updated: Update software whenever updates are available is a great way to protect against cyber attacks.
- Encrypt where possible: Encryption tools can be used to protect data from unwanted individuals. When encryption isn’t possible, password protection is a great alternative. Be sure to choose passwords with a mix of letters, numbers, and characters, and to update your passwords regularly.
- User activity monitoring and behavior analytics: This can give insights on when there is suspicious activity around your data. These tools can help you prevent data theft in real-time.
- Practice robust and continuous employee awareness programs: Even with the best technology in place, human error is often the weakest link. Constant education programs is the most important best practice when it comes to cyber resilience. Human error is responsible for 90% of all security breaches.
What Will You Do Next?
Cyber threats are not going away and will continue to be a major concern for all businesses no matter the size. Contact Zunesis to find out how our solutions can provide extra protection. Reach out to find out about our assessments which may discover holes in your current IT environment.
Want to find out how knowledgeable your employees are on the topic of cyber security? Take this quiz from the Cyber Readiness Institute to find out how cyber ready they are.
Hewlett Packard Enterprise recently started transitioning their support offerings from HPE Foundation Care and Proactive care to HPE Pointnext Tech Care. This new service goes beyond problem identification and resolution by helping customers get the most from their HPE technology. New innovations include fast multi-channel access to product-specific experts, an AI-driven digital experience, and general technical guidance to help customers achieve operational efficiency.
Standard features of the HPE Pointnext Tech Care experience
Product-Specific Expertise
Gone are the days of navigating complex escalations. With HPE Pointnext Tech Care, you get fast access to experts who specialize in the specific product you need support on. You can also benefit from HPE-assisted forums for community sharing, best practices and answers to common questions. And HPE’s library of hundreds of videos and configuration guides developed by HPE engineers will help to enable quick self-resolution of many issues.
General Technical Guidance
With HPE Pointnext Tech Care, you can gain expert technical advice for the operation and management of your products. Our experts augment skills gaps on your teams and can help your staff leverage best practices based on a knowledge base of thousands of other IT organizations. You have the freedom to engage experts beyond break fix by talking to an expert to brainstorm how to do things better, and by leveraging best practices and approaches to common issues.
AI-Driven Digital Experience
HPE Pointnext Tech Care delivers a data-driven and modern customer experience, featuring a powerful AI-based virtual agent, personalized task alerts and self-serve digital case management. The experience is optimized by the data coming from your HPE products, helping you to take action as quickly as possible. Streamline contract and warranty management by receiving faster and more complete visibility of your services and what resources are available to you. And HPE’s unique Visual Remote Guidance augmented-reality support can help on-site staff work with remote experts to get to solutions faster.
Pointnext Tech Care Support Offerings
Regardless of your coverage window, incidents with covered hardware or software can be reported to HPE via telephone, web portal, chat, or forums as locally available. An automated equipment reporting event uses HPE electronic remote support solution 24 hours a day, 7 days a week.
For HPE products covered by HPE Pointnext Tech Care, HPE offers three service levels tailored to the Customer’s operational requirements:
Basic
- 2-hour response 9×5 (standard business hours) Next business day on-site attendance
Essential:
- 15-minute response 24×7 for severity 1 incidents (direct connect to product specialist where available)
- 24×7 4-hour on-site attendance
Critical:
- 15-minute response 24×7 for severity 1 incidents (direct connect to product specialist where available)
- Outage management for severity 1 incidents
- 24×7 6-hour hardware repair commitment (where applicable)
Optional features include
- DMR (Defective media retention)
- CDMR (Comprehensive Defective media retention)
- Preventive maintenance (only with HPE contractual services)
- Hardware Exchange Service
All service levels provide 24×7 access to online self-serve and self-solve capabilities and 24×7 incident logging. For supported devices, 24×7 HPE InfoSight analytics and automated incident submission are available.
HPE Pointnext Complete Care
HPE Pointnext Complete Care is a modular, edge-to-cloud IT environment service. It provides a holistic approach to optimizing your entire IT environment. It works to achieve agreed upon IT outcomes and business goals through a personalized and customer-centric experience. All delivered by an assigned team of HPE Pointnext experts.
For assistance with selecting current support, please see the guide, below:
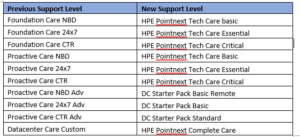
Our Renewals and Professional Services Team at Zunesis is available to assist you. We identify the best service level and options for your unique environment. If you are a current Zunesis customer, we will notify you within 30-90 days of support expiration. We will assist in helping you select a customized service level to meet your support requirements. Contact Zunesis with any questions you may have.




