It will take some time for things to get back to normal. The term, new normal has been popularized but is not far from the truth. The way we do business and approach activities of leisure will have to change for a while. How can we maintain some semblance of normalcy while engaging in the activities we once enjoyed? Activities like going to restaurants or the library have become seemingly dangerous propositions to undertake.
How can technology help to facilitate social distancing and encourage safer conditions for all of us?
The tools already exist to change the way we do business and approach the world. Technologies that would lessen the need for physical contact and allow for non-contact transactions are available. They are inside our cell phones and many of the wireless technologies currently deployed. The issue lies in the adoption of these technologies. We will explore a few technologies that can guide our return workplace.
Location based services – tracking social distancing
Inside every Aruba access point since the 3xx series, there are Bluetooth beacons. The beacons triangulate the position of people by tracking the location of their personal devices. Some applications for this technology include way finding, location-based marketing and access control.
In the future, this technology would count the number of people in a specific place to understand if social distancing standards are being followed. Aruba networks has a product called ALE or analytics and location engine that can be used to track and aggregate data about the location of each person within a building while using Aruba wireless access points.
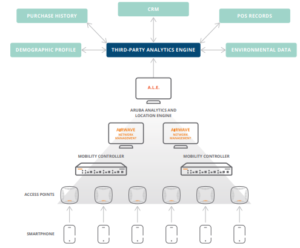
The graphic above is a generic topology for how the environment would look when leveraging the ALE. Utilizing the components in the graphic, a company identifies where in the building people are. Also, it can track possible issue areas. Using this tool as a guide to rearrange offices or cubicles, it assists support in the distancing measures when people return to their workplaces.
Uses in Public Venues
 In a public venue where the connectivity to the wireless networks cannot be relied upon, the system utilizes passive scanning of any devices that has WIFI or Bluetooth turned on. This enables one to accurately triangulate the position of this person. Aruba describes this capability by saying that the system can; “Calculate location for associated and unassociated clients based on received signal-strength information or simply indicate the presence of a device in proximity to a specific AP.”
In a public venue where the connectivity to the wireless networks cannot be relied upon, the system utilizes passive scanning of any devices that has WIFI or Bluetooth turned on. This enables one to accurately triangulate the position of this person. Aruba describes this capability by saying that the system can; “Calculate location for associated and unassociated clients based on received signal-strength information or simply indicate the presence of a device in proximity to a specific AP.”
The ability to passively identify user devices is very important for a business to approximate the current occupancy of a space. Locations for this device include restaurants, department stores or any other building where occupancy requirements may be a concern.
The accuracy of this system is directly dependent on the density of deployment of the access points or standalone Bluetooth beacons. If more APs or beacons are deployed in a space, then the accuracy of the system is greatly improved. It takes three access points or Bluetooth beacons to detect a device for accurate triangulation of a device to occur.
Distanced transactions with outdoor WIFI
Several businesses are trying to find a way to support retail transactions without the need for people to go inside the actual brick and mortar store. In some cases, restaurants and other food service-based businesses would like the ability to process a credit card on their patio without the employee physically interacting with the payment method.
Outdoor wireless would provide a greatly appreciated internet service to their patrons. It facilitates the ability to have a battery powered WIFI point of sale tablet negotiate the transaction. This would lessen the physical contact the patron and the employee would have in this setting.
With the newest Aruba 5xx series outdoor access points, a business could blanket their existing outdoor seating areas with secure wireless. The ability to deliver secure wireless for the patrons and the company assets is invaluable. It further supports the initiative to reduce physical contact.
Additionally, by leveraging outdoor WIFI, a company could extend their current outdoor seating space. This helps to maximize their ability to generate revenue. The possibilities for using secure outdoor access are limitless.
Rethink How We Do Business
In this time of uncertainty, we need to continue to innovate and rethink the way we do business. Giving up on interaction isn’t good for any of us. We should continue to pursue ways to retool our businesses. Augment how we measure occupancy so that we can stay safe but productive. My hope is that by leveraging technology we can find some semblance of normalcy again.
Contact Zunesis for more information on outdoor access points and other solutions to keep your business moving.
Using Aruba Dynamic Segmentation will help keep the Boogeyman away
 One reality terrifying most business owners is the thought of someone compromising their network and their data. Companies spend gratuitous amounts of money and time to protect themselves from cyber threats. They configure edge firewalls and multi-factor authentication mechanisms to protect their most sensitive data in the cloud. The thing that is often left untouched and overlooked are the data ports which are physically accessible to the public.
One reality terrifying most business owners is the thought of someone compromising their network and their data. Companies spend gratuitous amounts of money and time to protect themselves from cyber threats. They configure edge firewalls and multi-factor authentication mechanisms to protect their most sensitive data in the cloud. The thing that is often left untouched and overlooked are the data ports which are physically accessible to the public.
If the business operates in a public or shared office space, the risk of intrusion from an unprotected or unmanaged port is astounding. Aruba Networks have developed a technology that can now extend the same role-based firewall policies that are applied to the enterprise wireless to the wired ports. By enforcing the same role-based policies, administrators can simplify the deployment and management while also staying consistent across the network.
Is this a new threat?
In truth, the threat has always existed. The difference is that now more than ever, IOT devices require a hard-wired connection to function. This is because many of them do not support the same security and encryption standards we enforce on the wireless network. Some devices simply require the low voltage power supplied from the switch port to function. These devices include security cameras, lighting controllers, intelligent HVAC devices and some printers or scanners.
Another common scenario is when there is a need for a wired port for a special event. The port is configured for one purpose but then it is forgotten about. Then, anyone who plugs into that port has whatever access it was originally configured for. The reality is that these devices and circumstances are not going away any time soon. The best way to protect the network and the switch ports is to secure and isolate the clients and the devices from your sensitive networks and services.
What have engineers and administrators done about this attack vector?
From a management perspective, port security has always been the bane of network engineers and administrators. It has never been very practical or scalable to deploy. One must define clear attributes to distinguish each device from another. Then, you tell the switch port to change the network the device it is connected to or to simply block the port all together.
Often the unique attributes used to distinguish these devices are easy to counterfeit. Deploying the configuration on only the public facing ports takes planning and insight. This often falls through the cracks after the initial deployment. Furthermore, the deployment of these settings must be done on each switch in the environment that may be connected to from a public facing port. Aruba’s Dynamic Segmentation takes a different approach. It unifies policy enforcement and delivers the same seamless experience that people come to expect of wireless connectivity.
How does it work?
The technology leverages many of the same security and profiling mechanisms that exists in the Aruba wireless world. It applies them to the switch port adding a scalable security solution without the complexities of deploying another costly security product. It works by treating an Aruba network switch like an access point. The switch tunnels the switch port traffic to the Aruba mobility controllers. It profiles the connected devices in the same manner it would a wireless client.
If the device passes certain authentication criteria, then it is granted the same access as if it were on the wireless network. If the device has certain attributes but does not pass specific authentication criteria, than it is treated differently. It will be assigned the same role and given the same privileges as it would on the wireless network. In isolating these devices or unknown users, we can better protect the environment at large while not limiting the connectivity some users may need.
What else can Aruba Dynamic Segmentation do?
By tunneling the traffic to the mobility controllers, Dynamic Segmentation provides greater visibility of the traffic from IOT devices and guests users on your network. You can enforce a captive portal with email registration for guest users. This can add some accountability to a visiting contractor or guest speaker.
If an employee brings in a consumer device from home and plugs it in, you can distinguish what the device is, where it is plugged in and what it is communicating with. The most valuable use-case for this technology lies in the constant struggle of BYOD and onboarding of employee devices. If an employee chooses to use their own computing device and company policy allows it, you can check the security posture of the device before granting it access to any resources on your network. Ideally those users would have a policy enforced that would allow them to reach only the least sensitive resources and the internet.
Why should network/security engineers and administrators be excited about Dynamic Segmentation?
Unlike traditional port security which normally rely on 802.1x and radius authentication to authorize access on a single VLAN, Dynamic Segmentation does not require unique network segments to be defined to physically separate users. Aruba uses the term VLAN sprawl to describe the never-ending creation of new VLANs and subnets to create new layer 2 boundaries to physically segment user and device traffic.
With this solution, all the unknown devices and users could reside on the same network segment. Because the traffic is tunneled, all the traffic is subject to deep packet inspection, stateful firewall policies, layer 7 application visibility including web content filtering. Most IT professionals usually wouldn’t believe that their wireless controllers are capable firewalls. They would be wrong where Aruba is concerned.
What Aruba components are necessary to make it all work?
If you are already an Aruba wireless customer, you may already have what it takes to start leveraging this technology today. Listed below are the solution ingredients directly from the Aruba Solution Overview.
- Aruba wireless access points
- Aruba network switches
- Models 2930F/M, 3810M, 5400zl2
- Aruba Gateways or Mobility Controllers
- Running AOS 8.1 or later
- Aruba Clearpass Policy Manager with profiling
Overall, the solution will simplify your efforts at securing the network edge and unifying security into one manageable platform. Why spend time configuring and deploying a solution that you would have to duplicate with the wireless infrastructure? Save yourself from that spooky nightmare.
To learn more, contact your local Zunesis sales representative.
Additional Resources
Dynamic Segmentation Solution Brief

