So, you think you’re ready for the jump to Office 365? You have done your research; licensing, cost-savings, administration, migration strategies, best practices, etc. You have weighed the costs of doing the migration in-house or choosing a vendor to assist. What’s next?
Ensuring a stress-free migration for you and your users will need 3 things:
- Smart planning
- Smart decisions
- Time
There are many things recommended to make the migration go smoothly. One key piece of smart planning is ensuring the Active Directory accounts, which are migrating to Office 365, are prepared for the migration. Successful directory synchronization between your on-premise directory and Office 365 requires that attributes are properly configured.
 The following 5 tasks should be completed in Active Directory to plan for a smooth migration:
The following 5 tasks should be completed in Active Directory to plan for a smooth migration:
1. Active Directory Cleanup Tasks
Perform the following cleanup tasks in your on-premise directory:
-
- Ensure that each user has a valid and unique email address in the proxyAddress Field
- Remove Duplicates in the proxyAddress field
- Ensure each user has a valid and unique value for the userPrincipalName atrribute in the user’s user object
- For best use of the global address list (GAL), be sure the information in the following attributes is accurate:
- givenName
- surnamedisplayName
- Job Title
- Department
- Office
- Office Phone
- Mobile Phone
- Fax Number
- Street Address
- City
- State
- Zip
- Country
2. Directory Object and Attribute Preparation
Directory synchronization will fail if some of the Active Directory users have one or more duplicate attributes. If there are duplicate values, the first user with the value is synchronized. Subsequent users will not appear in Office 365. The following attributes should need prepared:
-
-
-
-
-
- Mail
- Attribute must be unique within the directory
- mailNickname (Exchange alias)
- Cannot begin with a period (.).
- Attribute must be unique within the directory
- proxyAddresses
- Can accept multiple values
- Value must not contain a space
- Attribute must be unique within the directory
- Invalid characters:
- [ \ “ | , / : < > + = ; ? * ]
- sAMAccountName
- Maximum characters: 20
- Attribute must be unique within the directory
- Invalid characters:
- [ \ “ | , / : < > + = ; ? * ]
- targetAddress
- Maximum characters: 255
- Value must not contain a space
- Attribute must be unique within the directory
- Invalid characters:
- [ \ “ | , / : < > + = ; ? * ]
- All SMTP addresses should comply with email messaging standards
- UserPrincipalName
- Must be in the Internet-style sign-in format: joe@contoso.com
- Invalid characters:
- [ \ “ | , / : < > + = ; ? * ]
- The @ character is required in each value
- The @ character cannot be the first character
- The user cannot end with a period (.), &, a space, or @
- Routable domains must be used, local or internal domains cannot be used
- Mail
-
-
-
-
3. Prepare the userPrincipalName Attribute
Active Directory is designed to allow the end users to sign in to the directory by using either sAMAccountName or userPrincipalName. End users can sign in to Office 365 by using the user principal name (UPN) of their work or school account. Directory synchronization attempts to create new users in Azure Active Directory by using the same UPN that’s in the on-premises directory. The UPN is formatted like an email address. In Office 365, the UPN is the default attribute that’s used to generate the email address. It’s easy to get userPrincipalName (on-premises and in Azure Active Directory) and the primary email address in proxyAddresses set to different values. When they are set to different values, there can be confusion for administrators and end users.
4. Add an Alternative UPN Suffix (if needed)
There may be a need to add an alternative UPN suffix to associate the user’s corporate credentials with the Office 365 environment. A UPN suffix is the part of a UPN to the right of the @ character. UPNs can contain letters, numbers, periods, dashes, and underscores, but no other types of characters.
5. Match the On-Premise UPN with Office 365 UPN
If directory synchronization is already setup, the user’s UPN for Office 365 may not match the user’s on-premise UPN that’s defined in the on-premise directory service. This can occur when a user was assigned a license before the domain was verified. To fix this, use PowerShell to fix duplicate UPN to update the user’s UPN to ensure that the Office 365 UPN matches the corporate user name and domain. When updating the UPN in the on-premise directory service and to have it synchronized with the Azure Active Directory identity, remove the user’s license in Office 365 prior to making the changes on-premise.
It is common for the on-premise domain to have a .local extension. In these cases, it is required to add an alternate UPN suffix to the .local domain which matches the email addresses of the users begin migrated. For example, if the local domain is contoso.local, but the email domain is contoso.com (i.e. users have email addresses of joe@contoso.com) an alternate UPN suffix is required on the local domain. In addition, the user’s primary UPN needs to be modified to reflect the UPN which needs to match the email domain.
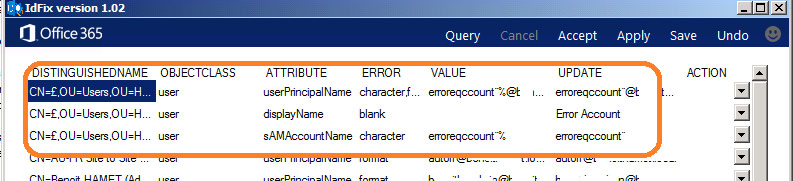
IdFix Tool
Microsoft provides a tool to make this process easier, it is called the IdFix tool. In fact, Microsoft does not recommend making the above changes without the tool. IdFix can find errors, report on errors, and even allow to take actions to edit or remove the attributes. All prior to attempting synchronization.
Conclusion
These are the main values in Active Directory which need to be validated or modified to ensure a smooth transition to Office 365, and IdFix can assist in identifying these values.
Active Directory is often compared to the central nervous system of the human body.
The central nervous system consists of the brain, spinal cord, and nerves running throughout the body. Just as the central nervous system coordinates and influences every activity of all parts of the human body, Active Directory is a database that coordinates the servers, client computers, printers, shared files, and other resources, as well as securing network resources in a Microsoft Windows network. Active Directory accomplishes these tasks by providing a hierarchy of management elements enabling administrators to organize resources, advertise these resources accordingly, and control the users who access them.
Medical doctors suggest a checkup or physical at least once a year, as well as personal monitoring of your health. Even if you are healthy, the purpose of these visits is to screen for diseases, asses risk of future medical problems, encourage a healthy lifestyle, update vaccinations, and maintain a relationship with doctors in case of an illness.
The comparison to Active Directory here can also be made. Proper monitoring and periodic checkups can keep the database functioning smoothly and without issues. It can definitely benefit from checkups, or health checks. (Download our free infographic to see what questions you can ask to see if your Active Directory could use a health check!)
Should You Engage in a Zunesis Network Health Check?
The purpose of an Active Directory health check could be for the same reasons listed above:
 Screen for Diseases
Screen for Diseases
- Verify trust relationships
- View replication failures between domain controllers
- View queued replication events between domain controllers
- Display replication partners and results of replication events
- Provide a summary of the replication state and health of the forest
- Analyze the state of all domain controllers in the forest and report problems
- Review results of Microsoft Best Practice Analyzer on domain controllers
Asses Risk of Future Medical Problems
- Discuss Microsoft Server Roadmap. Are you using the latest version? When will the next version be released? When will the oldest version no longer be supported?
- Meet with Active Directory stakeholders. Will the layout and design of database be affected by any projects or applications in the future?
Encourage a Healthy Lifestyle
- Discuss current administrative practices surrounding Active Directory. What is the process to add, change, or delete users or resources, etc.?
- Discuss and recommend monitoring strategies around Active Directory
- Discuss and recommend auditing strategies of Active Directory
- Review objects (users, computers, etc.) to check for stale/out-of-date resources, or illegal objects
Update Vaccinations
- Validate patch levels on domain controllers
- Validate anti-virus/malware on domain controllers
- Discuss security around the database
Maintain a Relationship with Doctors in Case of an Illness
- Good to have a relationship with an infrastructure provider, like Zunesis, when issues arise and advanced assistance is needed
- Good to have an independent third-party, like Zunesis, doing the health checks. You aren’t allowed to prescribe your own medication, are you?
Just like the human body, proper monitoring and care can assist in keeping Active Directory healthy. Active Directory and the Windows network can only benefit from these periodic “doctor” visits. The Zunesis Active Directory Health Check will assess your current Active Directory Infrastructure and deliver a report providing a third-party review, validation, and recommendations for improvement of the current database design and implementation, based on Microsoft best practices. The assessment can also be used as a template by which you can provide your own regularly scheduled “checks” of the environment.
Anyone who has ever worked with Microsoft’s Active Directory, either as an end user or administrator, has undoubtedly come across strangeness and unexplained occurrences. Active Directory serves many purposes: identity management, resource policy deployment, and user security management to name a few. Active Directory handles its extremely complex inter-workings in a very robust and flexible way. It is designed to resist outages and lost communication while continuing to provide services to users. While all of that is good from an availability standpoint, it also makes it easy to hide problems from its administrators.
Help Desk conversations about Active Directory can often be heard with the phrases, “I don’t know why that happened,” “That’s weird. I’ve never seen it do that before,” and “Oh well, it works now.” These conversations can lead to the realization that Active Directory isn’t totally healthy and could be performing better than it is currently. Something as simple as logging on to a workstation may generate multiple errors that aren’t visible to the end user except in the symptom of a log on delay.
The health of Active Directory can be affected in many ways. Changes to Active Directory throughout the years can add up to significant problems that seem to show up suddenly. Examples of these types of changes could be any of the following:
- Adding or removing domain controllers
- Upgrading domain controllers
- Adding or removing Exchange servers
- Adding or removing physical sites to your environment
- Extending the schema
- Unreliable communication between domain controllers
These changes, if done incorrectly, can cause multiple problems including log on issues,  replication failures, DNS misconfiguration, or GPO problems to name a few.
replication failures, DNS misconfiguration, or GPO problems to name a few.
Simple questions that you can ask yourself to determine if your Active Directory is currently not as healthy as it could be are as follows:
- Do your users complain of strange log on or authentication issues?
- Does it take an abnormally long time for users to log on to their workstations?
- Do your GPOs work sometimes and not other times?
- Do you get strange references to old domain controllers or Exchange servers that have long since been removed?
- Do you have issues resolving server’s names through DNS?
- Do your DNS servers get out of sync?
- Do DNS entries mysteriously disappear?
- And maybe most importantly, have you ever employed an admin that was given full rights to Active Directory who you later learned was not qualified?
Active Directory is integral to the IT success of just about every company. Finding issues and correcting them before they become a problem can prevent outages and future losses in revenue. Whether you are currently experiencing noticeable issues or just want a “feel good” report on the current status of your Active Directory, Zunesis can provide that peace of mind. With over 15 years supporting Microsoft Active Directory services for our customers, we have the experience and skills to get your Active Directory to a healthy state. Our proven method of using various tools to extract Active Directory information, analyze that data, and prepare and deliver a detailed report has proven very successful. Contact Zunesis today to set up an appointment to talk about your Active Directory needs.

