HPE Acquisition of Silver Peak
DENVER, CO October 1, 2020 – Hewlett Packard Enterprise (HPE) has completed the acquisition of Silver Peak, an SD-WAN (Software-Defined Wide Area Network) leader. For many years, Silver Peak has been a strong leader in the WAN Optimization and SD-WAN market. Silver Peak is now part of Aruba, a Hewlett Packard Enterprise company.
The acquisition will enhance and strengthen Aruba ESP (Edge Services Platform). This helps to advance enterprise cloud transformation with a comprehensive edge-to-cloud networking solution. It covers all aspects of wired, wireless local area networking (LAN) and wide area networking (WAN).
Steve Shaffer, CEO of Zunesis, a long-time Platinum Aruba and HPE Partner, says “Silver Peak provides a key piece of a comprehensive end-to-end Aruba solution offering. It creates additional value for our clients providing reliable and secure work-from-home and branch office connectivity. Work from home and branch office solutions just got a lot easier to deploy, secure and manage thanks to the combination of Silver Peak and Aruba’s SD-Branch & remote work solutions. All of us at Zunesis are very excited about these new developments.”
WAN Transformation
“WAN transformation is a key component of HPE’s Intelligent Edge and edge-to-cloud vision and growth strategy,” said Antonio Neri, president and CEO of HPE. “Armed with a comprehensive SD-WAN portfolio with the addition of Silver Peak, we will accelerate the delivery of a true distributed cloud model and cloud experience for all applications and data wherever they live.”
“I am very excited to welcome the Silver Peak team to the Aruba family,” said Keerti Melkote, president of Intelligent Edge for Hewlett Packard Enterprise and founder of Aruba Networks. “With the evolving nature of the hybrid workplace, enterprises are looking to extend connectivity to branch locations and enable secure work-from-home experiences. By combining Silver Peak’s advanced SD-WAN technology with Aruba’s SD-Branch and remote worker solutions, customers can simplify branch office and WAN deployments to empower remote workforces, enable cloud-connected distributed enterprises, and transform business operations without compromise.”
As part of the acquisition, Silver Peak founder and CEO David Hughes, will join HPE as the senior vice president of the WAN business within Aruba. “I look forward to leading the new WAN business unit within Aruba and accelerating our customers’ edge-to-cloud transformation initiatives,” said David Hughes, founder of Silver Peak and senior vice president of the WAN business at Aruba. “Digital transformation, cloud-first IT architectures, and the need to support a mobile work-from-anywhere workforce are driving enterprises to rethink the network edge. The combination of Silver Peak and Aruba will uniquely enable customers to realize the full transformational promise of these IT megatrends.”
SD-WAN Technologies
Enterprises are increasingly investing in SD-WAN technologies as legacy WAN architectures incur relatively high costs. They are cumbersome to operate, manage and secure. Aruba and Silver Peak share a common vision and goal to provide simplicity, scalability, and application-awareness at the edge of the network. Aruba’s all-in-one SD-Branch portfolio and remote worker solutions, combined with Silver Peak’s self-driving SD-WAN and WAN optimization solutions, allow Aruba to better address a wide set of customer requirements in order to capitalize on a promising and growing market opportunity.
At the same time, enterprises are also moving applications, including Internet of Things (IOT) and real-time analytics, to the edge of the network. Aruba is uniquely positioned to help organizations to support this network evolution while providing the needed connectivity to Public cloud resources. “We believe HPE Aruba are making all the right moves to help us offer the best and most reliable networking solutions for our customers large and small” says Shaffer. The next few years are going to be very exciting!
About Zunesis
Zunesis, headquartered in Englewood, Colorado has been an HPE Platinum Partner for 16+ years. Zunesis has expert engineers in HPE server, storage and networking technologies along with common software applications like VMware and Microsoft. We serve clients large and small but our sweet spot is the mid-market organization – the heartbeat of the US economy. Our mission is to make the lives of our clients and community better. www.zunesis.com
It will take some time for things to get back to normal. The term, new normal has been popularized but is not far from the truth. The way we do business and approach activities of leisure will have to change for a while. How can we maintain some semblance of normalcy while engaging in the activities we once enjoyed? Activities like going to restaurants or the library have become seemingly dangerous propositions to undertake.
How can technology help to facilitate social distancing and encourage safer conditions for all of us?
The tools already exist to change the way we do business and approach the world. Technologies that would lessen the need for physical contact and allow for non-contact transactions are available. They are inside our cell phones and many of the wireless technologies currently deployed. The issue lies in the adoption of these technologies. We will explore a few technologies that can guide our return workplace.
Location based services – tracking social distancing
Inside every Aruba access point since the 3xx series, there are Bluetooth beacons. The beacons triangulate the position of people by tracking the location of their personal devices. Some applications for this technology include way finding, location-based marketing and access control.
In the future, this technology would count the number of people in a specific place to understand if social distancing standards are being followed. Aruba networks has a product called ALE or analytics and location engine that can be used to track and aggregate data about the location of each person within a building while using Aruba wireless access points.
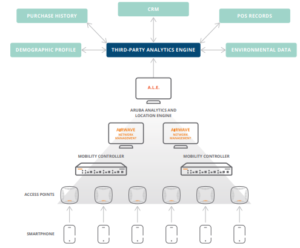
The graphic above is a generic topology for how the environment would look when leveraging the ALE. Utilizing the components in the graphic, a company identifies where in the building people are. Also, it can track possible issue areas. Using this tool as a guide to rearrange offices or cubicles, it assists support in the distancing measures when people return to their workplaces.
Uses in Public Venues
 In a public venue where the connectivity to the wireless networks cannot be relied upon, the system utilizes passive scanning of any devices that has WIFI or Bluetooth turned on. This enables one to accurately triangulate the position of this person. Aruba describes this capability by saying that the system can; “Calculate location for associated and unassociated clients based on received signal-strength information or simply indicate the presence of a device in proximity to a specific AP.”
In a public venue where the connectivity to the wireless networks cannot be relied upon, the system utilizes passive scanning of any devices that has WIFI or Bluetooth turned on. This enables one to accurately triangulate the position of this person. Aruba describes this capability by saying that the system can; “Calculate location for associated and unassociated clients based on received signal-strength information or simply indicate the presence of a device in proximity to a specific AP.”
The ability to passively identify user devices is very important for a business to approximate the current occupancy of a space. Locations for this device include restaurants, department stores or any other building where occupancy requirements may be a concern.
The accuracy of this system is directly dependent on the density of deployment of the access points or standalone Bluetooth beacons. If more APs or beacons are deployed in a space, then the accuracy of the system is greatly improved. It takes three access points or Bluetooth beacons to detect a device for accurate triangulation of a device to occur.
Distanced transactions with outdoor WIFI
Several businesses are trying to find a way to support retail transactions without the need for people to go inside the actual brick and mortar store. In some cases, restaurants and other food service-based businesses would like the ability to process a credit card on their patio without the employee physically interacting with the payment method.
Outdoor wireless would provide a greatly appreciated internet service to their patrons. It facilitates the ability to have a battery powered WIFI point of sale tablet negotiate the transaction. This would lessen the physical contact the patron and the employee would have in this setting.
With the newest Aruba 5xx series outdoor access points, a business could blanket their existing outdoor seating areas with secure wireless. The ability to deliver secure wireless for the patrons and the company assets is invaluable. It further supports the initiative to reduce physical contact.
Additionally, by leveraging outdoor WIFI, a company could extend their current outdoor seating space. This helps to maximize their ability to generate revenue. The possibilities for using secure outdoor access are limitless.
Rethink How We Do Business
In this time of uncertainty, we need to continue to innovate and rethink the way we do business. Giving up on interaction isn’t good for any of us. We should continue to pursue ways to retool our businesses. Augment how we measure occupancy so that we can stay safe but productive. My hope is that by leveraging technology we can find some semblance of normalcy again.
Contact Zunesis for more information on outdoor access points and other solutions to keep your business moving.
Working Remote
We live in a time (thankfully) where information is at our fingertips. Data can be transmitted and received from almost anywhere. And nearly all personal, and business-related, applications can be accessed remotely. As our world, our workloads, and our needed cache of data, rapidly expands; remote-accessibility has added a huge amount of flexibility.
But what if you had no other choice? The recent Coronavirus Pandemic has shown that this possibility can quickly become a reality. Let me take you on a quick little journey that should assuage any apprehension you may have about “working remote”.
The Past:
Business operates in a central office building or workspace. Employees travel to the office and operate there for the entirety of the workday. Remote work can be done for catch-up, and occasional work-from-home days are allowed. The majority of duties are conducted in the office.
The Present:
More and more companies operate a remote business model. Some businesses need to adapt a work-from-home option due to acts of nature or different unforeseen factors. While others have dissolved their office space entirely and now strictly have employees work in a remote fashion.
The Future:
Now here comes the tricky part. Where do we go from here? At the onset of the COVID-19 Pandemic, many places of business had to unexpectedly move their employees to remote functions without the means to do so. Being a technology company, Zunesis is still seeing this daily. It is an ongoing process but thankfully there are a lot of tools and services out there to help (more on that in a minute).
Some organizations may see the value and cost-reduction of moving day-to-day functions out of office buildings and into people’s homes.
What else is in store when the world begins to stabilize?
When are we all allowed to go “back to normal”?
Or is working from home “the new normal”?
The truth is…we don’t know.
 But either way, here’s a few things we DO know:
But either way, here’s a few things we DO know:
- Aruba Networks is working tirelessly to assist both corporate facilities and their newly delegated remote employees with deploying one unified network for company access.
a) With Aruba Central (Aruba’s Cloud-based management platform) a newly designed cloud gateway feature now allows organizations the ability to make their mission-critical applications remotely accessible to employees working from home or offsite locations. - Aruba has also put measures in place to help extend network coverage from data centers out to remote sites or emergency pop-up locations. This is done by using a wireless mesh solution and outdoor access points.
Zunesis has made the implementation and deployment of these solutions (and others) much easier for our customers. We are partnering with Aruba solutions architects and ensuring our in-house networking engineers are readily available.
For more information on Aruba’s strategy or Zunesis’ remote access solutions please visit the links below.
Zunesis Remote Access Solutions
In the meantime…live long and prosper, my friends. We are all in this together!
Using Aruba Dynamic Segmentation will help keep the Boogeyman away
 One reality terrifying most business owners is the thought of someone compromising their network and their data. Companies spend gratuitous amounts of money and time to protect themselves from cyber threats. They configure edge firewalls and multi-factor authentication mechanisms to protect their most sensitive data in the cloud. The thing that is often left untouched and overlooked are the data ports which are physically accessible to the public.
One reality terrifying most business owners is the thought of someone compromising their network and their data. Companies spend gratuitous amounts of money and time to protect themselves from cyber threats. They configure edge firewalls and multi-factor authentication mechanisms to protect their most sensitive data in the cloud. The thing that is often left untouched and overlooked are the data ports which are physically accessible to the public.
If the business operates in a public or shared office space, the risk of intrusion from an unprotected or unmanaged port is astounding. Aruba Networks have developed a technology that can now extend the same role-based firewall policies that are applied to the enterprise wireless to the wired ports. By enforcing the same role-based policies, administrators can simplify the deployment and management while also staying consistent across the network.
Is this a new threat?
In truth, the threat has always existed. The difference is that now more than ever, IOT devices require a hard-wired connection to function. This is because many of them do not support the same security and encryption standards we enforce on the wireless network. Some devices simply require the low voltage power supplied from the switch port to function. These devices include security cameras, lighting controllers, intelligent HVAC devices and some printers or scanners.
Another common scenario is when there is a need for a wired port for a special event. The port is configured for one purpose but then it is forgotten about. Then, anyone who plugs into that port has whatever access it was originally configured for. The reality is that these devices and circumstances are not going away any time soon. The best way to protect the network and the switch ports is to secure and isolate the clients and the devices from your sensitive networks and services.
What have engineers and administrators done about this attack vector?
From a management perspective, port security has always been the bane of network engineers and administrators. It has never been very practical or scalable to deploy. One must define clear attributes to distinguish each device from another. Then, you tell the switch port to change the network the device it is connected to or to simply block the port all together.
Often the unique attributes used to distinguish these devices are easy to counterfeit. Deploying the configuration on only the public facing ports takes planning and insight. This often falls through the cracks after the initial deployment. Furthermore, the deployment of these settings must be done on each switch in the environment that may be connected to from a public facing port. Aruba’s Dynamic Segmentation takes a different approach. It unifies policy enforcement and delivers the same seamless experience that people come to expect of wireless connectivity.
How does it work?
The technology leverages many of the same security and profiling mechanisms that exists in the Aruba wireless world. It applies them to the switch port adding a scalable security solution without the complexities of deploying another costly security product. It works by treating an Aruba network switch like an access point. The switch tunnels the switch port traffic to the Aruba mobility controllers. It profiles the connected devices in the same manner it would a wireless client.
If the device passes certain authentication criteria, then it is granted the same access as if it were on the wireless network. If the device has certain attributes but does not pass specific authentication criteria, than it is treated differently. It will be assigned the same role and given the same privileges as it would on the wireless network. In isolating these devices or unknown users, we can better protect the environment at large while not limiting the connectivity some users may need.
What else can Aruba Dynamic Segmentation do?
By tunneling the traffic to the mobility controllers, Dynamic Segmentation provides greater visibility of the traffic from IOT devices and guests users on your network. You can enforce a captive portal with email registration for guest users. This can add some accountability to a visiting contractor or guest speaker.
If an employee brings in a consumer device from home and plugs it in, you can distinguish what the device is, where it is plugged in and what it is communicating with. The most valuable use-case for this technology lies in the constant struggle of BYOD and onboarding of employee devices. If an employee chooses to use their own computing device and company policy allows it, you can check the security posture of the device before granting it access to any resources on your network. Ideally those users would have a policy enforced that would allow them to reach only the least sensitive resources and the internet.
Why should network/security engineers and administrators be excited about Dynamic Segmentation?
Unlike traditional port security which normally rely on 802.1x and radius authentication to authorize access on a single VLAN, Dynamic Segmentation does not require unique network segments to be defined to physically separate users. Aruba uses the term VLAN sprawl to describe the never-ending creation of new VLANs and subnets to create new layer 2 boundaries to physically segment user and device traffic.
With this solution, all the unknown devices and users could reside on the same network segment. Because the traffic is tunneled, all the traffic is subject to deep packet inspection, stateful firewall policies, layer 7 application visibility including web content filtering. Most IT professionals usually wouldn’t believe that their wireless controllers are capable firewalls. They would be wrong where Aruba is concerned.
What Aruba components are necessary to make it all work?
If you are already an Aruba wireless customer, you may already have what it takes to start leveraging this technology today. Listed below are the solution ingredients directly from the Aruba Solution Overview.
- Aruba wireless access points
- Aruba network switches
- Models 2930F/M, 3810M, 5400zl2
- Aruba Gateways or Mobility Controllers
- Running AOS 8.1 or later
- Aruba Clearpass Policy Manager with profiling
Overall, the solution will simplify your efforts at securing the network edge and unifying security into one manageable platform. Why spend time configuring and deploying a solution that you would have to duplicate with the wireless infrastructure? Save yourself from that spooky nightmare.
To learn more, contact your local Zunesis sales representative.
Additional Resources
Dynamic Segmentation Solution Brief
REST for the Weary – RESTful APIs
As the expression goes, “no rest for the weary.” A lot of us in the IT industry can relate to that statement. We are often needing to work long hours with heavy workloads.
Why is it then, that at least in my observation, many systems and network engineers still have not jumped on the automation train? We’re so busy being busy, that we don’t take the time to save time. Some of us still think RESTful APIs are something that only “devs” use. Luckily for our sanity, many of us are picking up this much needed skill.
If you haven’t played with RESTful APIs yet, and are in IT operations, I highly encourage you to check out RESTful APIs and get some lab time. By sharing some personal experience, I’d like to argue that there really can be “REST for the weary.”(Pun intended)
A slightly better way
I remember before RESTful APIs were something that more vendors were supporting. I had to do write Expect scripts in Linux to do my automation. Really, this was just screen scraping terminal output and brute forcing automation. It was messy at best, especially trying to automate devices that weren’t made for automation.
This wasn’t a whole lot of fun, but it was worth the pain involved since it still saved mountains of time. There was quite a bit of pain with some vendors. They needed weird keystroke combinations before it would allow CLI access even after SSH’ing in. Implementing “CTRL+Y” through an SSH session via script was way more of a headache than you’d think it should be.
Complaining aside, spending time writing Expect scripts was certainly MUCH easier than doing things manually. As an example, in a large environment I previously worked in, my co-workers spent time manually SSH’ing to literally hundreds of switch stacks. They had to run some commands and capture output to save.
I was asked on a regular basis by management to get MAC address/switchport/dot1x info, and other data which could be queried for historical data in a database. This was in preparation for a forklift upgrade on the network. The use case was to get a history of devices, interface information, and all other relevant historical data. Pulling MACs from the cores via uplinks wouldn’t give necessary detail.
This wasn’t an option. We had to go to the switches as a source of truth. The idea was also to compare to data from other sources (the IP-PBX system was one example) in preparation for the upgrade. They wanted to make sure network cut-overs were un-noticed by end users, aside from the downtime to swap equipment of course. I spent quite a bit of time writing and tuning Expect scripts, but still much less than doing things the old fashioned way.
The actual better way
Fast forward to my next job managing literally thousands of server nodes in a high uptime environment. I started getting asked to do things like update BIOS settings ON EVERY SERVER. To make things worse, as software engineering changed their code, they’d ask me to change BIOS settings multiple times. There was no way I was going to iLO into every one of those servers, reboot, wait, press F9 to access system utilities, select BIOS/Platform configuration(RBSU)… etc. Thankfully, I didn’t have to draw a line in the sand and explain that I was unwilling to do this.
After some research, I learned that HPE makes a RESTful API available on their Gen9 and Gen10 servers. Lucky for me, we were using Gen9 servers at the time.
Managing BIOS settings isn’t the only thing you can do by the way. You could probably integrate this into your monitoring system if it allows, for non responsive devices as an example. We’ve all seen servers where the lights are on but nobody is home. They seem dead, but respond to pings…intermittently and with high latency. You could use your monitoring system to poll services, and metrics like CPU and RAM utilization. Then, reboot the server via iLO RESTful API, if it is really locked up. No more waiting for a human to notice alerts, escalate if needed, then reboot the server manually.
One Interface for Integrated Control
HPE Integrated Lights Out (iLO) server management provides intelligent remote control automation through scripting or an API. Gain even more capabilities that go beyond scripting by leveraging one API to manage your complete lifecycle of HPE Gen9 and Gen10 servers—iLO RESTful API.
A single API interface integrates server management components and full compute power. Use it with HPE iLO 4 and iLO 5 to perform remote server provisioning, configuration, inventory and monitoring to industry standards through Redfish API conformance.
This was a game changer. I was able to prepare some standard JSON files with standardized BIOS settings. Then, write a script utilizing HPE’s RESTful API, and push settings described in the JSON file to every server (or subset of servers for testing) with ease.
Some settings still required a reboot to take effect. This was easily handled by scheduled reboots during a maintenance window. I also didn’t need to patch together a solution to script iLO changes with the software equivalent of duct tape and bubble gum, but instead utilized a RESTful API. Something that would have taken FOREVER, was accomplished with ease using something very well documented by HPE.
Give it a try!
Ready to give RESTful APIs a chance on your HPE servers and Aruba networking? Check out these resources:
Not using RESTful API capable servers or networking? The seasoned professionals at Zunesis can assess your environment, and recommend an appropriate refresh path utilizing the latest Aruba networking equipment and Gen10 HPE servers.
Aruba UXI Sensor
In early 2018, Aruba announced they were buying Cape networks, the developers of the Cape sensor. Rebranded as the Aruba User Experience Insight (UXI), the sensor sits on your network. It alerts you whenever your network is having problems.
It may not seem like much, but it is an amazing little device that could help IT departments everywhere. When deployed, the Aruba UXI sensor acts like a user on your network, except much smarter. No more complaints about “the internet isn’t working”. Instead, you get personalized alerts telling you exactly what is going wrong. Whether that means DNS is unresponsive, or merely yahoo.com is having an outage.

The sensor is designed to work straight out of the box on any network. It just needs to be registered to a dashboard. Then give credentials to the wifi or plug it into the ethernet. It takes so little set up. It can be mailed to a remote site and set up by anyone. All configuration is done in the web portal. All standard tests and alert thresholds come preconfigured. No set up is even needed, though you can definitely still customize it.
Aruba UXI Overview from Aruba Networks / Cape on Vimeo.
Aruba Dashboard
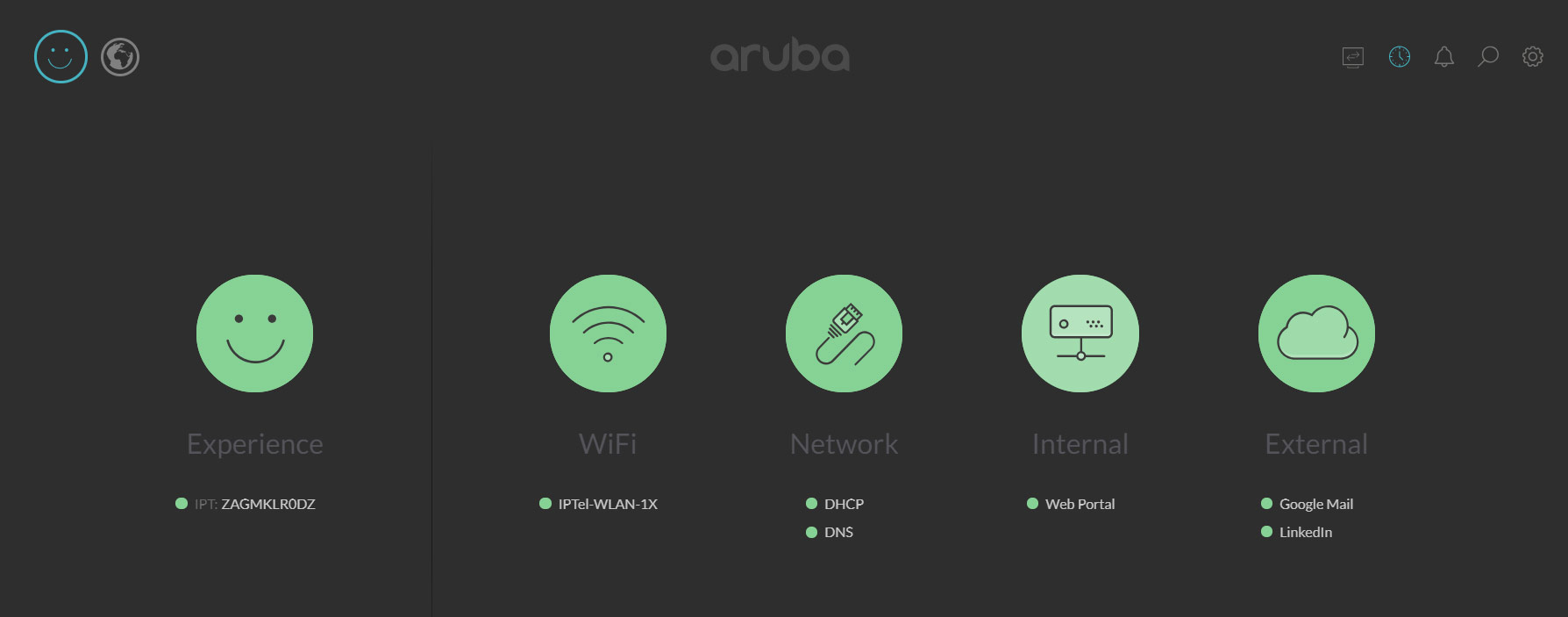
The dashboard is simple and easy to use. It gives you access to a lot of information about your network. Hover over any piece on the home page to get alert info. Then, click to drill down further and see a trove of other information, such as signal strength, channel, response times for things like dns or dhcp, even websites if you set them up.
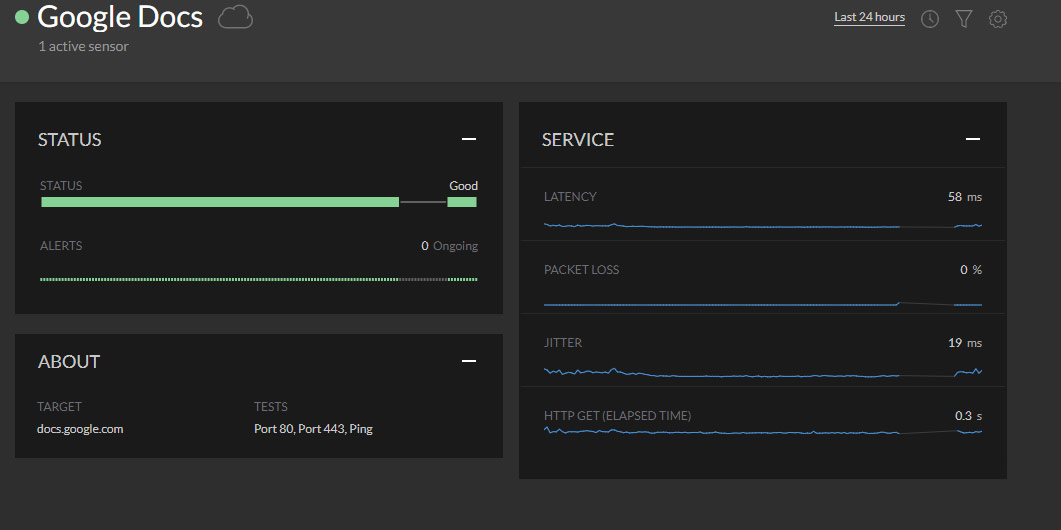
The sensor can be configured to check both internal and external services. Whether you use internal websites and fileshares, or Google docs and Microsoft OneDrive, you can test them all to be sure they are up and running. If they aren’t, the IT department is the first to know.
Proactive Alerts
Alerts are sent via email whenever certain customizable thresholds are met. This enables IT departments to know about a problem before a user has a chance to report it. They will also know exactly what went wrong without having to hunt around for the cause of the issue.
The alert says which service is down. Quickly letting IT know if the entire internet is down, or if its just the DNS service on a server. Website issues can also be shown through the alerts. Knowing exactly whats wrong, quickly enables the IT department to address the issue faster. This results in less down time and less unhappy users.
Cloud Accessibility
The dashboard and all data are hosted in the cloud. This allows for you to access it anywhere, at any time. No need to be on site to diagnose an issue. No worries about not being able to see data and alerts while a site is down.
Diagnosing issues is half the battle in the helpdesk world. Eliminating this problem, enables the IT department to be far more efficient and timely in resolving those issues.
Location, Location, Location
Arubas UXI sensor should be placed in a spot where wifi is used most, or problem areas that you would like more information on. It comes with a couple different ways to mount it. It can also be set on a desk or table just as easily.
A secure mounting bracket can be deployed in public areas without the fear of it disappearing. All it needs is power either provided by the included power adapter, or by a PoE solution. The sensor also isn’t just limited to wifi. It works over ethernet as well, so you can check all network connections at once.
A user experience sensor is a valuable tool for any company, small or large. The key feature is that it enhances the response time of any IT department. Faster response times mean less downtime, which means less time your company is running smoothly. The solution is constantly being updated with more features being added every day to make the jobs of you and your IT department easier.
Contact Zunesis for more information on this solution or other networking products for your organization.
“Keep the malware, ya filthy animal” is NOT a line uttered in the 1990 Christmas Classic, Home Alone….but it should be!
Well…not really. The internet was still in its infancy in 1990 and infection of computers and networks by malicious software was still a relatively new concept (the term “malware” was first coined only months before Home Alone’s theatrical release). The line would DEFINITELY apply today, however. As nearly everything is operated online, to some extent, and network security is becoming more important than ever!
Thankfully, there are high-end tools we use today to ensure that we can control and monitor what devices are accessing our networks. Review how these devices are behaving while on the network. Give the ability to remove said devices if malicious activity is detected.
Little Human ClearPass
There are numerous blogs and articles that explain how the entire plot of Home Alone would not have occurred had the technology that we use today been available. I’m not going to go down that rabbit hole here. Instead I am going to use the film as an analogy for technology itself…namely Aruba Network’s security platform “ClearPass”.
I’m doing this because I think it makes some of the nuances of the technology easier to understand and because I just feel like it, ok? So, sit back, grab a cheese pizza, and put on some after-shave…I’m about to tell you all about the story of Kevin McCallister, “The Little Human ClearPass”.
For those of you that don’t know, Aruba ClearPass is a policy management platform that allows network admins to onboard new devices, grant varying access levels, and help keep their networks secure. It can be dissected into three primary security functions: Identify, Enforce and Protect. And I will use Kevin McCallister to demonstrate each process.
Identify
Much of Kevin’s success in thwarting full-grown men who are attempting to rob his parent’s house, stems from the fact that he is a very observant little fella. He notices the highly suspicious “Wet Bandits” following him. Kevin monitors their behavior and overhears their conversations. Preemptively, he defends his family home based on his findings. His observations operate in much the same way as ClearPass. ClearPass helps identify what devices are trying to access the network. These findings include where the devices are connecting from and device-specific information such as IP address, OS, type and model name etc.
Enforce
The key for the “Wet Bandits” to successfully loot all of the luxurious homes in Kevin’s neighborhood while they are all vacant for the holidays. If  you’re a burglar…you’re not going to attempt to waltz into a house full of people and hope you go unnoticed, are you? Remember when Kevin turns on every single light in his house and makes it look like there’s an epic party occurring there? Bingo. The burglar policy seems to be: “if the place is occupied, don’t risk it.”
you’re a burglar…you’re not going to attempt to waltz into a house full of people and hope you go unnoticed, are you? Remember when Kevin turns on every single light in his house and makes it look like there’s an epic party occurring there? Bingo. The burglar policy seems to be: “if the place is occupied, don’t risk it.”
Networks have policies too. Ones that can similarly prevent unwanted visitors. ClearPass allows you to enforce these network policies during the onboarding of new devices. Rules can be put into place that define what type of devices users can onboard, how many, and who may onboard a device. After this, access can be enforced in a number of ways. A simple portal can be used or the more secure method of using encryption in the authentication process.
Protect
The final area of focus in ClearPass security is “Protect”. With ClearPass OnGuard, one can define the “health level” a device must have in order to gain access to the network. The health of individual devices that are connected to the network is crucial to network security. If a device that is attempting to connect does not meet these requirements, it is not allowed on the network. Moreover, policy controls and threat remediation give real-time insight into the activity on the network, allowing threats to be quickly identified. This allows the IT staff to quickly block traffic or disconnect devices if unusual network behavior is detected.
 What does all that mean in layman’s terms and can I use a metaphor? Sure thing! If you see suspicious folks skulking around your residence, you better ice down your steps, heat your doorknobs and place Christmas ornaments by the windows to discourage unwanted entry. If those crafty villains still a manage to gain entry, you better have some Micro Machines strewn across the floor and have a tarantula handy. It worked for Kevin McCallister and it can work for you and your network!
What does all that mean in layman’s terms and can I use a metaphor? Sure thing! If you see suspicious folks skulking around your residence, you better ice down your steps, heat your doorknobs and place Christmas ornaments by the windows to discourage unwanted entry. If those crafty villains still a manage to gain entry, you better have some Micro Machines strewn across the floor and have a tarantula handy. It worked for Kevin McCallister and it can work for you and your network!
Aruba Networks is just one of the many great vendors that Zunesis works with daily. Contact us today for all of your IT needs. Including, but not limited to, cyber security. If you find yourself “home alone” just think, “what would Kevin do?”.
Thanks for reading and have a Merry Christmas!
Aruba 8400: Designed from the Ground Up for Automation and Network Insight
Looking at networking gear over the past several decades, not much has really changed from a high level. Okay, we’ve gotten bigger pipes to fit the much larger volume of data that needs to pass through them. We have added more protocols to manage the control plane, but a lot of the core technology is still pretty much the same.
OSPF, BGP, VRRP, etc … hasn’t really changed much. Sure, some of us are over spanning tree and aren’t wasting half of our links anymore, but the point is that many network engineers themselves haven’t changed how they deploy and manage solutions. Specifically, many of us are still managing our networks statically via the command line, troubleshooting after a problem has caused an outage, and not automating.
In the era of mobile, cloud, and IoT, this simply isn’t scalable anymore. If you’re a forward thinker, you may have already been using ansible, python, etc. for network automation, and it definitely helps when the vendor has designed a platform specifically for this. Gone are the days of screen scraping and expect scripting over SSH.
Aruba has been disrupting the networking industry for some time now in wireless and wired, but one thing missing from the product portfolio was an offering for the core… until now.
What’s New:
- High-performance Aruba core and aggregation switch with 19.2 Tbps switching capacity and carrier-class high availability.
- ArubaOS-CX automates using built-in REST APIs and Python scripts.
- Monitor and troubleshoot with Aruba Network Analytics Engine.
- High availability, virtualization and simplicity with Aruba VSX.
- High density, line rate 10GbE/40GbE/100GbE connectivity.
- Advanced Layer 2/3 feature set includes BGP, OSPF, VRF and IPv6.
Game-Changing Business Agility
The Aruba 8400 Switch Series is a core and aggregation switch solution with an innovative and powerful approach to dealing with the new applications, security and scalability demands of the mobile, cloud and IoT era.
Fully programmable with ArubaOS-CX, it brings automation and visibility and helps troubleshoot via simple scripting.
Aruba Network Analytics Engine provides the ability to monitor and troubleshoot the network, system, application and security related issues easily, through simple python agents and REST APIs.
High-availability, high-speed architecture with 19.2 Tbps switching capacity for always on networking.
Robust security and QoS with advanced Layer 2 and Layer 3 features including support for BGP, OSPF, VRF and IPv6.
Modern Software System Simplifies and Automates
The Aruba 8400 Switch Series is based on the new ArubaOS-CX, a modern software system for the core that automates and simplifies many critical and complex network tasks.
The built-in time series database enables customers and developers to develop software modules for historical troubleshooting, as well as analysis of historical trends, to predict and avoid future problems due to scale, security and performance bottlenecks.
Includes stability, independent monitoring and restart of individual software modules, and enhanced software process serviceability functions. And it allows individual software modules to be upgraded for higher availability; and supports enhanced serviceability functions.
Delivers enhanced fault tolerance and facilitates nearly continuous operation and zero-service disruption during planned or unplanned control-plane events.
High Performance and Carrier-Class High Availability
The Aruba 8400 Switch includes a high-speed, fully distributed architecture and provides up to 19.2 Tbps switching capacity to meet the demands and bandwidth-intensive applications today and in the future.
Aruba’s new high availability technology is Aruba VSX which has been designed from ground up to deliver the continuous availability, virtualization and simplicity requirements unique to the core of the network.
Resiliency and high availability with hot-swappable, redundant and load-sharing fabrics, management, fan assemblies and power supplies.
Scalable, compact 8U chassis delivers industry-leading line rate 10GbE/40GbE/100GbE port density, very low latency, and scalability ideal for the campus core.
So how is this any different from other chassis based switches?
ArubaOS-CX
Meet ArubaOS-CX, a modern network operating system. The entire state of the system is stored in a database, and all aspects of the system interact with it, and not directly with each other outside of it. This provides much greater modularity, extensibility, and allows seamless recovery when failures are detected. If one particular daemon crashes, it simply restarts and restores it’s state back from the database with almost zero downtime. This is huge! If you’ve ever had to recover a major process like OSPF and had to deal with the consequences, you know exactly what I’m talking about. Further, the system automatically generates a REST API for all objects in the data model, and can expose all features, functions, statistics…EVERYTHING to AOS-CX applications/services and to external systems if desired.
If that wasn’t enough, Aruba has also provided us with automated monitoring and troubleshooting via the network analytics engine. This allows IT professionals to easily monitor, detect problems, analyze trends, and immediately resolve issues instead of relying on traditional tools like SNMP and CLI after the fact. If a particular condition is detected, it is possible to automatically remediate via scripted actions.
Again, ArubaOS-CX is fully programmable via REST API, and for those of you who are ready to dig in, here’s a handy reference document to help get you started.
So are you ready to switch?(Pun intended)
E-Rate – “Free Money” from the Government for Education Customer Networks!
As a “go-to” E-rate services provider for our valued networking partners, Aruba Networks and Extreme Networks, we have discovered that many hundreds of millions of unspent “E-Rate” monies are still available to customers in the Rocky Mountain Region. This includes K-12 education as well as many libraries, and some child development (pre-K) centers. E-Rate is a great way to refresh aging networking equipment in all or part of your organization and have a large portion of the costs paid for by the US government. Below are some frequently asked questions we wanted to share and answer. We find that many smaller entities may not be aware of this program or the fact that they have “money to spend”. Zunesis can help them design and implement E-rate compliant, modern, and rugged internal network connection (wired and wireless) infrastructures.
What is E-Rate?
The Universal Service Schools and Libraries Program – commonly known as the E-rate program – provides discounts on telecom, internet access, and internal connections to eligible schools and libraries. E-rate is funded through the Universal Service Fund (USF). You will see a small fee at the end of each of your land line or wireless service phone bill. This small fee is collected to help fund this program along with additional federal funding. The Federal Communications Commission (FCC) writes the rules and standards for this program. The administrator of the E-rate program is the Universal Service Administrative Company (USAC).
Have you received your E-rate funding and how is funding determined?
Did you know that all applicants who submitted an eligible and timely E-rate application in 2015 through 2019 will receive their funding? Many schools have yet to take advantage of the over $4 billion dollars in available E-rate funding. For K-12/charter schools, E-rate discounts range from 20% to 90% of eligible project costs. Discounts are district wide, and an applicant’s discount rate is determined by the percentage of students that qualify for a free or reduced-price lunch.
How do I choose a Service Provider?
A service provider like Zunesis needs to be selected as part of a specific and regimented bidding process. E-rate applicants must conduct a fair and open competitive bidding process. All applicants must select the most cost-effective service provider. The price of the eligible products and services must be the most heavily weighed bid evaluation factor. Although other factors such as local presence to the state/community, service provider expertise on the proposed product, and ability to provide a complete solution (including implementation) may be other important weighing factors.
Why apply for E-Rate funding this year?
There has never been a better time to apply for E-rate funding. Because of the increased funding cap, available roll-over funds, and remaining Category Two (aka. “Internal Connections” such as wired switches and wireless access points) maximum budget funds, it is likely that there will be enough funding to support the entire demand in the current fiscal year as well. Also, applicants that seek E-rate funding this year will not have to compete for dollars against the applicants that will have their Category Two budgets refresh in future fiscal years (2020 and beyond).
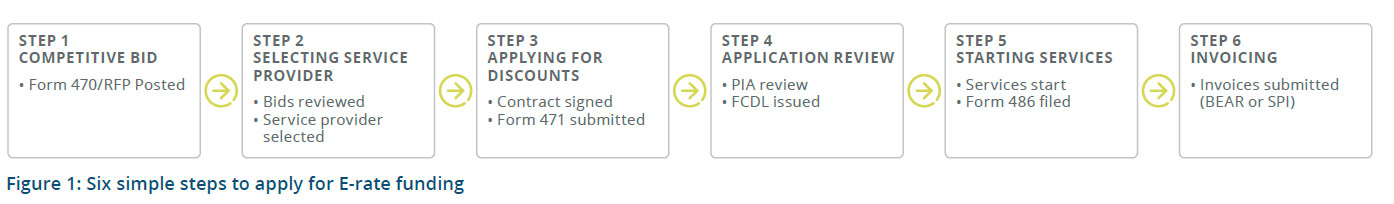
How do I apply for E-Rate funding?
To apply for E-rate funding, simply follow the 6-step process outlined in Figure 1 below:
How do I determine if product is E-rate eligible?
It’s important to note that not all networking solutions are E-rate eligible. For example, you can find eligibility of Aruba products using their E-rate Eligibility Lookup Tool.
The following table highlights products that are eligible under the current E-rate program from Aruba Networks as a for-instance.
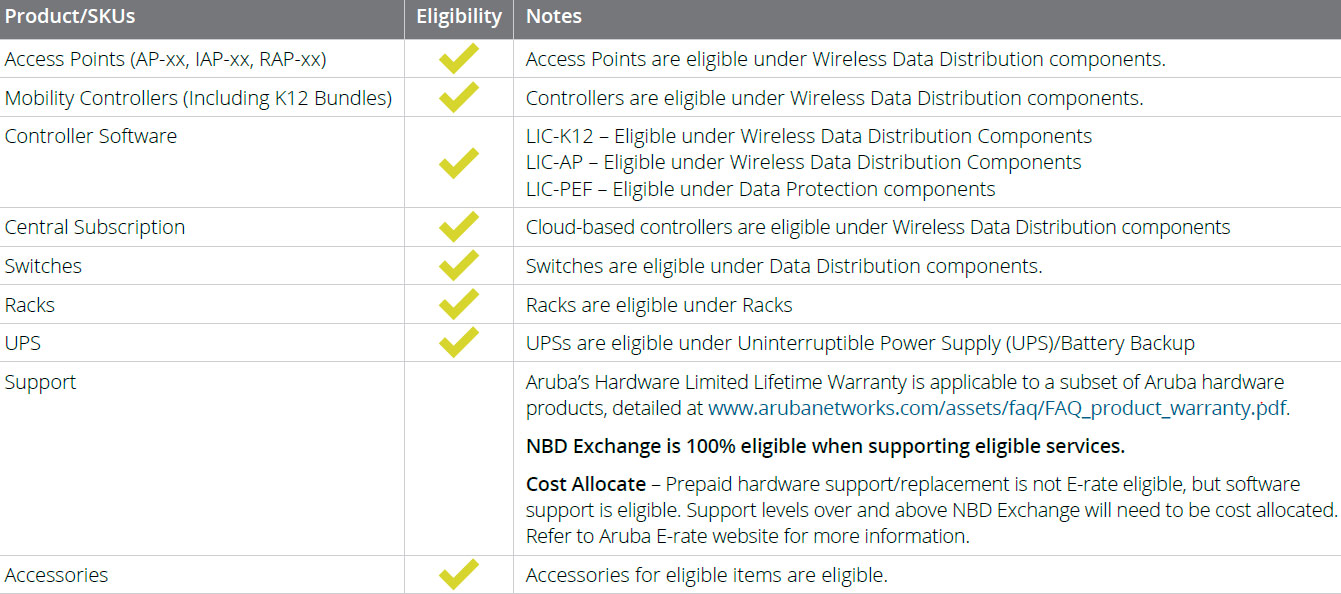
How can Zunesis help?
Zunesis believes in working with our E-rate eligible clients well prior to “step 1” of the above chart to help educate the customer on some of the best available options for their particular environments. As not all customer needs are the same, we feel it is always best to have a face to face meeting to walk through example environments, discuss customer needs, and provide valuable input into the Competitive Bid process. Please contact your Zunesis account manager to setup your E-Rate readiness review today!
Additional Resources
Aruba Networking Education Solutions
Simple, Secure, Scalable
If you follow the announcements from major networking vendors you will have noticed a trend, at least in the marketing, for new solutions that are emerging from these companies. Every whitepaper or datasheet you read will have the key words “Simple”, “Secure”, and “Scalable” littered throughout the document. The reason for this is because, from a high level, these are some of the most important factors for customers when making a purchasing decision.
One solution I have found that lives up to those key words is Aruba’s new SD Branch solution. This solution is intended to help enterprise customers modernize their branch networks for the ever-evolving network requirements that IT needs to support. According to Aruba, the new SD Branch offering is
“Ideally suited for distributed enterprises undergoing digital transformation, Aruba SD-Branch delivers optimized branch experiences with simplicity at enterprise scale and integrated, best-in-class security. Retail, hospitality, and healthcare organizations can manage SD-WAN, WLAN, LAN, and unified policy for thousands of sites in the cloud.”
But how is it delivering on those marketing key-words?
Simplicity for the Distributed Enterprise
For enterprises, this new SD-Branch solution offers cloud-based management option that allows them to provide remote, centralized provisioning and management of both wired and wireless connections within the branch and through WAN and internet connections in the SD-WAN infrastructure. The idea behind it is to give IT the ability to implement new services and make network changes quickly even across huge environments that are distributed throughout different locations and departments. So you can manage everything from one centralized console without needing multiple programs for different functions or parts of the enterprise.
Within the branch, Aruba’s new service offers granular QoS through application, user, and device contextual awareness. This functionality also extends across the WAN for SaaS, mobile UC, and other remote applications. This is meant to simplify how LAN and WAN traffic gets prioritized and routed, both inside and outside of the branches, giving IT teams the ability to deliver a consistent experience across the organization regardless of device type, user role within the organization, or physical location on the network.
Integrated Security
Of course, security is a major concern with basically any new tech offering. Aruba offers intra-branch and WAN policy enforcement capabilities that are both automated and granular. Aruba has a new set of Aruba 360 security exchange technology partners that deliver cloud-based firewall and threat protection to help IT keep all of the organization’s digital assets safe and protected.
Scalability
Aruba’s SD Branch solution is managed and configured in the cloud using a tool called Aruba Central. Central has been around for a while now and is most commonly used to manage large dispersed wireless access. The management functionality, along with the new “WAN analytics” piece I discussed above, have been extended to include the branch gateways at each location. Being a cloud management tool first and foremost Central can scale to meet the demands of any network (as they have been doing for years with some of Aruba’s largest dispersed customers), so customers have the peace of mind that their investment will be protected, no matter how large they grow, for years to come.

