HPE Worldwide Ambassador Summit
Over the last several years, I have been lucky enough to be invited to attend the Hewlett-Packard Enterprise Worldwide Ambassador Summit. This is an invitation-only event where invitees learn about the strategy, products and programs HPE is currently working towards. We are asked to provide feedback on what is working, what is not working and how the programs are impacting the channel. There were several takeaways from the event which are summarized below.
Everything As a Service
Everything as a Service. All the executive sessions had the same overall message, HPE is the Edge-to-Cloud Platform-as-a-Service company. They are moving to an Everything as-a-Service model, from the Aruba Intelligent Edge to the HPE Hybrid Cloud. The target is to be open, cloud-native, intelligent, autonomous and secure at every level.
One of the key components to Everything as a Service is Greenlake. Greenlake is a program that brings the cloud experience on-premise. It is a true consumption model that provides Cloud like agility and economics, while keeping control on-premise. The customer achieves many cloud-like benefits. This includes rapid deployment, scalability, and consumption-based economics while maintaining control.
The catalog offers pre-designed, end-to-end solutions along with fully customizable options. Flex Capacity allows you to design and customize your own infrastructure solutions. One can select from a broad range of HPE and partner technologies and services.
Artificial Intelligence
Similar to most industry news, analytics and artificial intelligence (AI) was a major topic. HPE is incorporating AI into every technology, from the edge to compute to storage and networking. AI in the infrastructure is essential in the hybrid cloud world to simplify and reduce the complexity in managing infrastructure and ensure optimal performance and efficient resource use. HPE InfoSight is one of those AI solutions that predicts and prevents problems across the infrastructure stack. It ensures optimal performance and efficient resource use.
Clearpass Device Insight
With the introduction of cloud applications and software, plus the adoption of Internet of Things (IoT) devices, networks have become extremely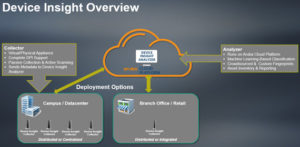 important to business and have become more complex. Aruba ClearPass Device Insight provides visibility across the network and provides the context of all connected devices. With Device Insight, attributes such as device type, vendor, hardware version and behavior and accessed resources are available. This allows the more granular information when creating access policies, reducing security risks and meeting key compliance requirements.
important to business and have become more complex. Aruba ClearPass Device Insight provides visibility across the network and provides the context of all connected devices. With Device Insight, attributes such as device type, vendor, hardware version and behavior and accessed resources are available. This allows the more granular information when creating access policies, reducing security risks and meeting key compliance requirements.
Composability
The last topic we spent a lot of time discussing was Composability. HPE introduced the concept with the introduction of the Synergy platform. They didn’t stop there. Today they also have the Composable Rack and Composable Fabric.
 The Composable Rack can Automate IT operations and deliver applications and services faster. It uses standard HPE Rack mount servers, current management tools, along with the Composable Fabric. This solution enables rapid deployment of your choice of HPE SimpliVity, VMware virtual machines, Red Hat OpenShift containers, or bare metal workloads for new cloud-native workloads. HPE Composable Fabric provides flat, wire-once, and top-of-rack 25G server connectivity. It features programmatic control, easy rack-to-rack scaling, and broad compatibility with existing data center networks.
The Composable Rack can Automate IT operations and deliver applications and services faster. It uses standard HPE Rack mount servers, current management tools, along with the Composable Fabric. This solution enables rapid deployment of your choice of HPE SimpliVity, VMware virtual machines, Red Hat OpenShift containers, or bare metal workloads for new cloud-native workloads. HPE Composable Fabric provides flat, wire-once, and top-of-rack 25G server connectivity. It features programmatic control, easy rack-to-rack scaling, and broad compatibility with existing data center networks.
This fabric not only enables composable element connectivity but also directly affects the integrity and performance of the underlying infrastructure and applications. Traditional, enterprise networks focus on north/south workload traffic between clients and servers. They are not designed to handle the distributed and varied nature of modern scale-out applications that require machine-to-machine communication over the network.
Our solution architects at Zunesis are knowledgeable in all of these areas. Reach out to Zunesis today to find out more about these focus areas.
“Keep the malware, ya filthy animal” is NOT a line uttered in the 1990 Christmas Classic, Home Alone….but it should be!
Well…not really. The internet was still in its infancy in 1990 and infection of computers and networks by malicious software was still a relatively new concept (the term “malware” was first coined only months before Home Alone’s theatrical release). The line would DEFINITELY apply today, however. As nearly everything is operated online, to some extent, and network security is becoming more important than ever!
Thankfully, there are high-end tools we use today to ensure that we can control and monitor what devices are accessing our networks. Review how these devices are behaving while on the network. Give the ability to remove said devices if malicious activity is detected.
Little Human ClearPass
There are numerous blogs and articles that explain how the entire plot of Home Alone would not have occurred had the technology that we use today been available. I’m not going to go down that rabbit hole here. Instead I am going to use the film as an analogy for technology itself…namely Aruba Network’s security platform “ClearPass”.
I’m doing this because I think it makes some of the nuances of the technology easier to understand and because I just feel like it, ok? So, sit back, grab a cheese pizza, and put on some after-shave…I’m about to tell you all about the story of Kevin McCallister, “The Little Human ClearPass”.
For those of you that don’t know, Aruba ClearPass is a policy management platform that allows network admins to onboard new devices, grant varying access levels, and help keep their networks secure. It can be dissected into three primary security functions: Identify, Enforce and Protect. And I will use Kevin McCallister to demonstrate each process.
Identify
Much of Kevin’s success in thwarting full-grown men who are attempting to rob his parent’s house, stems from the fact that he is a very observant little fella. He notices the highly suspicious “Wet Bandits” following him. Kevin monitors their behavior and overhears their conversations. Preemptively, he defends his family home based on his findings. His observations operate in much the same way as ClearPass. ClearPass helps identify what devices are trying to access the network. These findings include where the devices are connecting from and device-specific information such as IP address, OS, type and model name etc.
Enforce
The key for the “Wet Bandits” to successfully loot all of the luxurious homes in Kevin’s neighborhood while they are all vacant for the holidays. If  you’re a burglar…you’re not going to attempt to waltz into a house full of people and hope you go unnoticed, are you? Remember when Kevin turns on every single light in his house and makes it look like there’s an epic party occurring there? Bingo. The burglar policy seems to be: “if the place is occupied, don’t risk it.”
you’re a burglar…you’re not going to attempt to waltz into a house full of people and hope you go unnoticed, are you? Remember when Kevin turns on every single light in his house and makes it look like there’s an epic party occurring there? Bingo. The burglar policy seems to be: “if the place is occupied, don’t risk it.”
Networks have policies too. Ones that can similarly prevent unwanted visitors. ClearPass allows you to enforce these network policies during the onboarding of new devices. Rules can be put into place that define what type of devices users can onboard, how many, and who may onboard a device. After this, access can be enforced in a number of ways. A simple portal can be used or the more secure method of using encryption in the authentication process.
Protect
The final area of focus in ClearPass security is “Protect”. With ClearPass OnGuard, one can define the “health level” a device must have in order to gain access to the network. The health of individual devices that are connected to the network is crucial to network security. If a device that is attempting to connect does not meet these requirements, it is not allowed on the network. Moreover, policy controls and threat remediation give real-time insight into the activity on the network, allowing threats to be quickly identified. This allows the IT staff to quickly block traffic or disconnect devices if unusual network behavior is detected.
 What does all that mean in layman’s terms and can I use a metaphor? Sure thing! If you see suspicious folks skulking around your residence, you better ice down your steps, heat your doorknobs and place Christmas ornaments by the windows to discourage unwanted entry. If those crafty villains still a manage to gain entry, you better have some Micro Machines strewn across the floor and have a tarantula handy. It worked for Kevin McCallister and it can work for you and your network!
What does all that mean in layman’s terms and can I use a metaphor? Sure thing! If you see suspicious folks skulking around your residence, you better ice down your steps, heat your doorknobs and place Christmas ornaments by the windows to discourage unwanted entry. If those crafty villains still a manage to gain entry, you better have some Micro Machines strewn across the floor and have a tarantula handy. It worked for Kevin McCallister and it can work for you and your network!
Aruba Networks is just one of the many great vendors that Zunesis works with daily. Contact us today for all of your IT needs. Including, but not limited to, cyber security. If you find yourself “home alone” just think, “what would Kevin do?”.
Thanks for reading and have a Merry Christmas!

