Data Protection
In the age of ransomware and digital transformation, your company’s data is even more critical than ever to keep your business running. While avoiding data loss is the main priority of backups, it can often be hard to balance that with the cost of those backups. On top of all that, data is harder to manage and control than ever due to multi-cloud infrastructure and workers more often working remotely.
So how do you deal with all of that and still have a trusted backup in case the worst should happen? You need a single, robust solution for data management that can protect your data through all phases of its lifecycle.
Veeam has been a leading player in the backup space for a while now. It has really stepped up when it comes to addressing new challenges in data protection. It has a host of different products, enterprise to consumer, that make it easy for businesses big and small to tackle the issue. They continue to innovate and keep your data secure while remaining flexible enough to fit into any environment. This year is no different with the release of Veeam version 11.
So what is new in the newest version of Veeam?
Continuous Data Protection, or CDP
It integrates with VMware environments to eliminate downtime and minimize data loss with a host of new features. CDP will eliminate the need for VM snapshots with I/O level tracking, and reduce the bandwidth needed for replication. It works on any OS or application as long as they are running in a vSphere VM. CDP will also schedule your jobs for you, just define the required RPO and CDP will take care of it. Depending on the amount of data, CDP can also offload data processing from your hosts to proxies. It calculates the required bandwidth to eliminate guesswork.
Hardened Repositories
This keeps your backups safe from malware and hackers with immutable backups. Single-use credentials are never stored in the configuration database eliminating any possibility of those credentials being extracted from a compromised backup server.
Expanded Object Storage Support
This feature reduces the cost of long-term archives. Veeam now integrates with Amazon S3 Glacier and Azure blob archive storage which are best for very long-term storage. These repositories can be made immutable, and are policy-based, so no management required.
Expanded Instant Recovery
It makes even more of your workloads instantly available. Instant recovery has been a feature of Veeam for a while, but now it has been expanded to include SQL and Oracle databases. Regardless of size, databases are made available to production applications and clients in minutes. You can then finalize those recoveries either manually, or by scheduling them to switch as soon as synchronization catches up, or even scheduling the switch during maintenance hours.
More Improvements
Veeam has made many more improvements with Version 11, enhancing many aspects of the program. GFS and Archive backups have added functionality. Powershell is now more powerful. Backup speeds have increased. Compliance with WORM backups has been added. As well, the GUI has seen some improvements. All of these features are included with normal licenses, you don’t need to pay extra for any of this stuff.
I am barely even scratching the surface on what is in the new version. I am most excited about the steps Veeam is taking to make their product more resilient against viruses and ransomware. Ransomware attacks have ramped up over the last few years. Keeping good copies of data in case of such an attack has been a struggle. Companies like Veeam have been in an arms race against hackers. Things like immutable backups are a huge leg up in the fight. Maybe someday, we won’t have to worry about that stuff, but for now, at least we have Veeam.
Contact Zunesis to find out more about Veeam V11.
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.
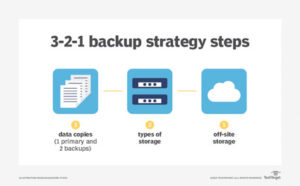
The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.

The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
Veeam Backup and Replication
The Threats are Many and so are the Protection Methods
In a modern society, the need for cyber security touches a surprisingly large portion of our day-to-day lives. Because of the Internet of Things (IoT), we can scarcely climb out of bed each morning before we use a device that is connected to the internet in some way. Whether it’s our smart phones, Alexa, Siri, tablets, laptops, television or even our automobiles, we are potentially putting personal data out on the internet before we’ve even had our first cup of coffee (or even as we order our coffee for pickup as we head into work). We pay our bills online, we use our phones to deposit checks and we even have wi-fi enabled automobiles.
As individuals, we are responsible for looking out for our own security. As IT Professionals, we are responsible for protecting the data our company produces and collects. In many cases, the data we are protecting in our professional role is personal data, possibly our own. But, the recent Equifax breach is a harsh reminder that, even companies we associate with security are vulnerable. If there is any lesson we can take away from our personal experiences, and the stories behind the headlines, it’s that there is not single solution that will protect us from the threat of our data ending up at the mercy of people with bad intentions. Those of you reading this post are intimately familiar with the steps needed to protect company data. From the network to the desktop, and all points in between, there are many layers to a data protection strategy. One such layer is the Data Backup solutions we use.
Backup, the Original Data Protection
Decades ago, during simpler times, data protection meant being diligent about performing regular backups of data in case a file was accidentally deleted, corrupted or the hard drive crashed. Back in that simpler time, the media to which businesses directed those backups was almost always Tape, lots of tape! This process typically included keeping a set of tapes onsite for immediate restore needs and sending a second set offsite in case of catastrophe and for longer term retention. However, over time, Tape has been increasingly replaced by disk-based backup targets (think HPE StoreOnce, Data Domain, ExaGrid).

Disk-based backup targets started out as a faster way to get data backed up. Tape was still used but typically as a secondary backup target and for longer term retention offsite. The need to go to an offsite backup for file recovery was rare and so tape became that insurance policy that was never going to be needed. As use of disk-based backups became more prevalent, the technology employed to store data evolved. Improvements in compression, deduplication, and replication improved the efficiency of storing larger amounts of data (in the petabytes) and replicating that data to offsite facilities. In fact, with the ability to replicate data from one disk-based target to another over distance, we have started to see Tape being replaced at offsite facilities as well.
Backups As Our Last Defense
While we originally used backup for recovery from accidentally deleted files, random corruption and the occasional disk crash, the world we live in today requires a broader definition for Data Backup. Today, we may need to leverage our backups to recover from a Cyberattack that has either corrupted our data or rendered it unusable as part of a Ransomware attack. Because these kinds of attacks target files on volumes that are persistently mounted to hosts, the vulnerability of disk-based backup targets has come under some scrutiny lately.
Of course, many question whether the risk to disk-based backup targets is very high. After all, backup environments are typically isolated from other, more accessible, areas of the IT infrastructure. Moreover, because of the potential for Cyberattacks on the disk-based backup targets, other processes have been documented and are being implemented to mitigate the risk further. We are starting to see some of these added protections built into the backup software we use and many manufacturers of the disk-based backup devices are providing their own best-practice processes.
Despite the fear of risk for disk-based solutions, we aren’t seeing a trend away from disk-based backup, but we are hearing reports that some companies are once again turning to Tape as their last form of defense against the type of Cyberattacks that would corrupt, delete or encrypt their data. And while disk-based technology has been evolving, tape technology has also continued to evolve. LTO7 technologies provide capacities as high as 15TB (compressed) per tape cartridge. In addition to high capacities and a low TCO, Tape offers encryption at-rest, can be kept offsite and most importantly offline.
So, as we implement safeguards to keep the bad guys out of our IT infrastructure, we need to remember that our plans should include multiple layers. We also need to prepare for the possibility that our best efforts will be thwarted and that our data will be compromised. So, as part of our protection against malicious behavior and risk to our data, we need to carefully plan our Backup processes by taking the layered approach as well.

