Artificial Intelligence (AI) is revolutionizing the world of storage and data management at an unprecedented pace. This emerging technology is not only streamlining the way organizations store, process, and manage enormous volumes of data, but it’s also significantly improving the insights gleaned from this information. Offering advanced algorithms and machine learning capabilities, AI is powering the future of storage and data management—and is expected to transform the way businesses handle and use their data.
Here are six ways AI is changing the game:
- Improved data analysis: By identifying intricate patterns and trends in large datasets, AI improves the accuracy and speed of data analysis, leading to quicker and more precise insights. With this higher caliber of insights, you can make quick, well-informed decisions that align with your business goals and support profitability and growth.
- Predictive maintenance: With the ability to analyze historical data and real-time usage patterns, AI algorithms can be used to predict when equipment failures are likely to occur and proactively flag them to the right people, mitigating the risk of expensive downtime and devastating data loss.
- Intelligent data storage: AI can analyze data usage patterns and automatically move less frequently accessed data to more cost-effective storage tiers. It also makes it easy for you to quickly locate specific data by indexing and tagging information for easy search and retrieval. With critical data that’s readily available and accessible when you need it, AI technology powers more efficient operations, better resource allocation, and more informed decisions.
- Better data security: With the ability to identify potential threats and anomalies in data usage patterns, AI technology allows you to take immediate action to prevent major security breaches. Additionally, using AI-driven encryption methods, you can ensure your sensitive data is protected both at rest and in transit, making it infinitely more difficult for hackers to access or steal important information.
- Automated routine tasks: With the ability to automate routine data management tasks, AI can streamline workflows, minimize processing time, reduce human error, and enhance the overall efficiency of data management processes, ultimately leading to cost savings and increased productivity.
- Enhanced disaster recovery: AI not only automates backup and recovery processes, but it can also identify potential risks and vulnerabilities and deliver real-time alerts and notifications in the event of an outage or data loss. With a higher degree of control and reliability in your disaster recovery efforts, your business can recover from disasters more quickly to reduce the impact of unexpected events, improve business continuity, and ensure critical operations can be resumed quickly.
Harnessing the Potential of AI-Driven Storage
As organizations generate and store ever-increasing amounts of data, AI will continue to play a crucial role in helping businesses manage and utilize that data to drive innovation, optimize operations, and make data-driven decisions that fuel growth.
Hewlett Packard Enterprise (HPE), with solutions like HPE InfoSight, is leading the charge in harnessing the potential of AI-driven storage and data management technologies. At Zunesis, we are committed to helping you capitalize on HPE’s AI-powered solutions to ensure a seamless, optimized, and forward-thinking data management strategy tailored to your specific needs and objectives.
For more information about how to transform your storage and data management processes with HPE powered by AI, contact us here.
According to IDC research, businesses are prioritizing resiliency and agility as foundational elements of their IT strategy. They want more visibility, cross-platform control, better data management, and protection from the edge to the core. While consumption-based models are playing an increasingly important role in powering those goals to accelerate digital transformation, many business leaders are hesitant when it comes to Network-as-a-Service (NaaS). Some still think of as-a-service in terms of software, compute, and storage. However, as budgets grow tighter amid an inflationary economic environment, organizations need a better way to predict the ebbs and flows of the network, with flexibility to adapt as business needs change. That’s where NaaS comes into play.
Among the newest as-a-service approaches, NaaS combines hardware, software, services, and support in a pay-as-you-go model that delivers network services on a subscription basis. Allowing users to consume network infrastructure through flexible OpEx subscriptions, NaaS helps businesses shift their focus from managing their architecture to driving business outcomes.
If you haven’t transitioned to Network-as-a-Service yet, here are five reasons why you should:
- Cost savings: Network-as-a-Service allows you to acquire the network you need, when you need it, to avoid overprovisioning—in a pay-as-you-go OpEx model. Because you’re not locked into expensive infrastructure and rigid contracts, Naas allows you to more predictably manage costs and align budgets to business priorities. Additionally, with insights into all aspects of usage, including power, capacity, bandwidth speeds, and service levels, you can make more profitable financial decisions about workloads and upcoming projects.
- Security: As the prevalence of data breeches and ransomware continues to soar, enhancing network security is crucial. With proactive network monitoring, preventative maintenance, and real-time insights into network performance, the NaaS model offers enhanced network infrastructure protection with enterprise-grade security. With that, any nefarious activity can be immediately identified—and patches can be applied to address the breech before it becomes a problem.
- Performance and Productivity: Network-as-a-Service ensures your network operates efficiently by assessing traffic volume and making necessary adjustments. A better performing network means less downtime and greater staff productivity. Additionally, by outsourcing the full lifecycle of your enterprise network deployment, day-to-day operational management, upgrades, monitoring and troubleshooting activities to a NaaS partner, you free up your internal IT resources to focus on business-enabling tasks that add measurable value.
- Keep up with the pace of business: NaaS provides the financial flexibility to shorten planning cycle times and the agility to keep pace with changing conditions. By ensuring your network technology is refreshed as needed to support new workloads and changing requirements, a NaaS model makes it easy to scale your network as needs change.
- Environmental impact – NaaS offers a more sustainable way to consume network technology. With the ability to rent sustainable networks from a NaaS provider on a subscription basis, you don’t have to worry about where and how to dispose of old equipment. Plus, NaaS providers are committed to sustainable ‘reuse and retirement’ practices—and also well versed at configuring networks that are purpose-built to optimize energy consumption. By turning to a NaaS solution, you are making an environmentally sound decision that reduces your carbon footprint.
As market conditions continue to change at a rapid clip, your business needs to be one step ahead of your competition. With NaaS solutions from Aruba, Zunesis can help you move from reactive network management to a proactive approach that uses the network to deliver innovation and power profound business outcomes.
For more information about how you can accelerate business outcomes with Aruba’s subscription-based network consumption model, contact us here.
It’s that item on your to do list that you often ignore and say you will do later – software updates. Not only may you be missing out on the latest improvements, but you can create a major security risk for your organization by ignoring these updates.
One of the largest data breaches on record is the Equifax data breach in 2017. It exposed the personal information of 147 million people. Hackers were able to get in due to a known system vulnerability for which a security patch had been issued two months before the breach. Unfortunately, no one at Equifax applied the patch. It cost the company $700 million in a settlement reached with the FTC.
60% of data breaches in 2019
were the result of unpatched vulnerabilities.
Before you get distracted by another project or think that you can wait to do your next update, here are a few reasons why software updates matter.
Security
Security is the number one reason to make sure you take care of updates as soon as possible. Software vulnerabilities often give cyber criminals access to one’s computer and plant malware. Malware enables one to take control of computers and steal information. It also can encrypt files, documents and other programs so they are unusable. Security patches block these open doors in the software to protect a device from attacks.
Risks from third-party vendors account for over two-thirds of all data breaches today. Third-party applications often interact with the internet. This makes them highly vulnerable to ransomware. Hackers know companies often overlook updating various programs that don’t seem important.
Cybercriminals want to exploit the most vulnerabilities as possible simultaneously. They are constantly searching for popular third-party programs. They will jump on an opportunity to hack millions of users who delayed updating their software.
New Features
On a positive side, software updates can give you access to the latest improvements and remove the old ones that are out of date. A software program may get a new shot of stability — no more crashing. Or an update might boost program performance — more speed. Some of these new features could save you time and most importantly enable the software to keep working and not shut down.
Protect Your Data
Your Data is your most valuable asset at any organization. Often hackers will search for personal data such as financial information, passwords, usernames or other documents with sensitive information. They will look to sell this information to the dark web and commit crimes. Allowing your customer’s information to be vulnerable can impact your company’s reputation and future business.
Improve Performance
Just like your vehicle needs regular maintenance to help improve its performance, your software can benefit from updates. Bugs are often found in programs or enhancements are made to improve the overall experience.
Ensure Compatability
With technology constantly changing, often older software will not be compatible with new technologies without the appropriate update. Microsoft, Google and Apple are frequently updating their technology interfaces. Most of us use multiple devices so compatibility is essential.
Don’t Fall for Fake Update Messages
It important to update your software but beware of fake messages or popups out there. Pop-ups are typically a scam to get you to click somewhere that you should not. Close the pop-up and go directly to the vendor website to look for downloads. There a suspicious emails making their rounds stating that your updates are past due and make an update now. It is best to reach out to the vendor directly.
You may have the option with some software to do automatic updates. Some software makes it possible to choose the time of day you update or even how often. Scheduling and automating your updates this way will make them less of a nuisance.
Take Time to Update
Like ignoring the check engine light on your car is something you shouldn’t do, the same goes for software updates. They can help protect personal information as well as company data. Contact Zunesis to find out more about how we can help.
The Pandemic has disrupted supply chains around the world for a wide range of goods, including electronics and other crucial pieces of IT equipment. Supplier relationship management has been put to task. Companies struggle to source needed parts, manage inventories and more. The current situation is undoubtedly causing stress for IT leaders. This unique situation also gives organizations the opportunity to reset their IT supply chain visibility and security policies.
Demand + Shortages = Extended Lead Times
The initial pandemic-driven remote-work mandate appears to be a permanent shift in many workers converting to a hybrid or full-time telework. This in turn led to a surge in electronics sales. With both increased demand and the fallout from recovering closures and continuing understaffed factories in China, this created a domino effect of shortages of both laptops and datacenter to edge supporting architecture. As 2022 kicks off, average lead-times for laptops and displays are 16 weeks, 8 to 16 weeks for servers and storage and 8 weeks to 9 months for networking gear.
Security Risks and New Requirements
The supply chain shortages create several risks for IT professionals. This includes third-party service providers’ physical or virtual access to information systems, software or intellectual property; poor information security practices at lower-tier suppliers; compromised software or hardware purchased from suppliers; and software security vulnerabilities in supply chain management or supplier systems.
To combat these new risks, many agencies are incorporating new security requirements into every request for proposal and contract, including the following:
- Having a security team work onsite with any new vendor to address any vulnerabilities or security gaps
- A “one strike and you’re out” policy regarding vendor products that are either counterfeit or do not meet specifications.
- Tightly controlled component purchases
- Secure software lifecycle development programs and training for all engineers in the product lifecycle
- A security handshake between software and hardware. This is where a secure booting process looks for authentication codes and will not boot if the codes are not recognized.
Most importantly, working together with suppliers is more important than ever. Especially this is prevalent in small or mid-size private companies who want to be nimble enough to juggle resources to help one customer without hurting another. Small to mid-sized private suppliers are often more flexible with financial options. These options include accelerating payments and changing contract terms so receivables are more easily factored, providing a dynamic discounting program or leveraging supply-chain finance programs.
Long-Term Order Forecasts
Letting the supplier have longer-term order forecasts will ensure priority status for supply delivery. Likewise, make a point to report supply constraint updates monthly. This will allow insight into the changing supply recovering times. The more a supplier can rely on and trust what it’s hearing from a customer, the more it can make the critical business decisions that can help it get through the crisis.
By addressing supply chain visibility and security now, companies will get through the current crisis. This will make their IT supply chains more resilient and secure in the years to come.
HPE Synergy- Six Years of Innovation
It has been a while since we talked about the Hewlett Packard Enterprise Synergy platform. It is hard to believe it was announced in 2015 and is already 6 years old. This platform was definitely built with the future in mind. It was designed from the ground up to support future technologies and communications bandwidth. Server hardware has taken a back seat to the conversations around Cloud, Hybrid Cloud, HyperConverged, Security, Ransomware and Anything as a Service.
Since 2015, the Compute Modules have migrated from the Gen9, to the Gen10 and now the Gen10 Plus. We still have a lot of conversations around hardware in the data center. The goal around the Synergy platform is to provide a “cloud-like” (on demand resources) experience in your data center.
Cloud-Like Experience
The HPE Synergy platform is defined as a composable, software-defined infrastructure that allows you to provide that cloud-like experience. This platform enables you to compose fluid pools of resources (physical or virtual compute, storage, and fabric) to meet the requirements of your workload. This can be done using the unified API to simplify and automate deployments. Using this API, you can provision the required resources with a single line of code.
The design of the Synergy platform allows you to manage one infrastructure that can quickly scale and reduce complexity in your environment. This infrastructure will support current- and next-gen apps, each with vastly diverse infrastructure requirements and service-level objectives. The applications can run on physical hardware, virtual hardware or containers, all in the same frame.
Industry Leading Security
As will all HPE Servers, the Gen10 and Gen10 Plus has provided industry leading security. They have designed and implemented an enhanced, holistic, 360-degree view to security that begins in the manufacturing supply chain and concludes with a safeguarded, end-of-life decommissioning.
This all starts with the Silicon root of trust that is built into all Gen10 and Gen10 Plus servers. The Silicon Root of Trust from Hewlett Packard Enterprise (HPE) has been designated a 2019 Cyber Catalyst cybersecurity solution. It protects against firmware attacks, detects compromised firmware or malware, and helps to rapidly recover the server in the event of an attack. This starts with the HPE developed and proprietary iLO 5 management. The iLO 5 ensures all firmware and the BIOS have the proper signature before it allows the machine to power on.
This level of security protects all firmware and BIOS through a key programmed into chip silicon at a TAA compliant chip production facility. It also integrates security with HPE Secure Start and Secure Boot to protect all BIOS, firmware, SPS, IE and boot sequence. The recovery process automatically quarantines compromised BIOS and firmware, then re-flashes with a known good image.
Budget Savings
With composable compute delivered as an on-premises cloud service, you’ll gain agility and avoid costly manual configuration and management of compute resources. When coupled with HPE GreenLake, you will have a powerful, software-defined, composable compute infrastructure that composes physical and virtual compute, storage, and fabric pools into any configuration for any application. If you choose the pay-per-use model for on-premises compute assets, it will enable you to align IT spend with actual usage. You only pay for what you use above a reserve. This model will provide you with near-real-time visibility into your usage data, and you can set budgets, create reports, and build rules-based insights.
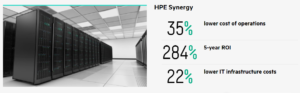
What’s New in HPE Synergy?
So what’s new in HPE Synergy? The latest compute modules announced is the HPE Synergy 480 Gen10 Plus. This new compute module is an all-new design around Intel 3rd Generation Xeon Scalable Processors. It can provide up to a 40% increase in performance over earlier processor generations. This performance gain is achieved with improvements to the product line design around the processor, memory, storage, and boot options.
The HPE Synergy 480 Gen10 Plus compute module delivers the performance, efficiency, and flexibility of a 2-socket server to support the most workloads. The Gen10 Plus provides more cores for a new level of workload performance and expanding ESXi VMs, expanded the memory DIMM socket count to 16 slots per socket, with 8 channels @ 3200 MT/S increased speed. The new Gen10 Plus has also expanded the capacity and persistence of the Intel Optane 200 memory support.
There are many additional upgrades and improvements to the Synergy Frame, more information can be found at HPE Synergy Composable Software Defined Infrastructure Platform | HPE.
Contact Zunesis today to find out more about HPE Synergy.
Every 11 seconds, a network is attacked by ransomware. Each successful attempt costs a company $80,000 on average. This adds up to over $20 billion each year. This number continues to grow each year. Cyber security is quickly becoming one of the most important investments for companies large and small.
These investments come in many forms; training, antivirus programs, spam filters, and backups to name a few. Once your data is compromised though, there is really only one thing you can do. You need to do a restore from a backup.
So, how does Veeam backup help protect data against ransomware?
Immutable backups
Immutable backups are copies of your data that cannot be changed. Veeam offers immutability in the capacity tier of their Scale-out Backup Repository (SOBR). It leverages a native function of object storage that prevents blocks of data from being changed for a set amount of time. Not even a malicious admin with full access to backups can change this data, let alone ransomware.
Air-Gapping
A related concept is air-gapping your backup repository. This basically means backups are unreachable or offline after the backup is taken. A common way of doing this is tape backups. Once the tape is written, it is physically removed from the network. It is stored in a secure location, inaccessible until the tape is moved back onto the network.
Another feature offered by Veeam that is similar is rotated media. This allows to swap hard drives for the backup chains so that one or more hard drives with backup data are offline or air gapped at all times. This protects that set of data from attacks.
Veeam ONE
Detecting ransomware in its initial stages can be difficult. Veeam ONE provides the ability to monitor your environment closely and be aware of any suspicious or abnormal activity. By analyzing CPU usage, datastore write rate, and network transmit rate, Veeam ONE can help identify higher than normal activity on a particular machine, trigger an alarm, and immediately notify you to inspect the machine.
Veeam SureBackup
SureBackup is a feature of Veeam that allows you to create a sandbox to test your backups before restoring them to production. It can run virus and malware scans on backup sets, automatically or manually. It ensures your data is not infected without the need to restore the data somewhere first.
Secure Restore
A related feature is Secure Restore, which scans your data as it is being restored. This gives you access to the latest virus definitions which helps safeguard against viruses that were previously unknown at the time of the backup.
Veeam DataLabs
Unsure of a workload, or suspect it may be infected? DataLabs gives you the ability to restore the data to a fully secured and isolated environment to test. A fully isolated sandbox lets you run any tests you want without impacting production systems, so you can make sure your workloads are uninfected before you restore them.
Ransomware protection alliance
Veeam is part of a group of leading hardware and software companies, like HPE, Cisco, and AWS, that work together to make sure their products integrate using the highest security standards possible. They bring together the most powerful recovery solutions to combat ransomware.
Veeam backup and recovery is a powerful tool in the fight against ransomware. It is completely dependent on how it is implemented and used. You should always secure your backup server, follow the 3-2-1 rule, implement Veeam’s features for ransomware detection, protect your network, and test your backups. A good backup strategy is just another piece in the puzzle in the fight against ransomware.
Contact Zunesis to find out more about Veeam backup and recovery solutions for your organization.
What are MFA, 2FA, and why do we need them?

“Something you know, something you have, something you are.” This is stated by Multi-Factor Authentication enthusiasts all over the web. They are ways of identifying yourself for the purpose of gaining access to a system. Examples of these would be your username/password combination, a OTP (One Time Password) sent be SMS or authenticator app, and biometrics. 2FA is of course a subset of MFA. It uses two factors to authenticate your logon. AND NO, USERNAME + PASSWORD ARE NOT TWO FACTORS.
Compared to single factor authentication, MFA ensures that your accounts are much better protected. “99.9% less likely to be compromised” is found on Microsoft based on their records of 99.9% of compromised accounts not using MFA. This was stated by Alex Weinert, Director of Identity Security at Microsoft at a recent cyber security conference.

Perhaps even more disturbing is that there is ONLY AN 11% MFA ADOPTION RATE AMONG ENTERPRISE CLOUD USERS. It’s not like we keep important data in our business emails. We also don’t use these same emails as recovery addresses for other business related online accounts. Joking aside, we are almost asking for security breaches.
Why aren’t you using Multi-factor Authentication?
We live in times where ransomware, social engineering, and other cyber attacks are on the rise. By not utilizing multi-factor authentication, you are doing the equivalent of using 1-2-3-4-5 as your combination on your luggage. Something almost as bad is re-using the same couple of passwords everywhere. Your password expired? Just update it from SecurePW1! to SecurePW2@ and it will meet complexity requirements and be super secure, right?
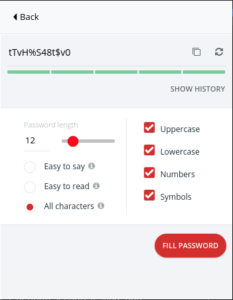
The practical issue with using very complicated passwords is that they are very difficult to remember by design. This is where a password manager is very helpful. You don’t want to be the person with a bunch of sticky notes on your monitor with login credentials written on them.

You can generate very secure passwords as seen in the LastPass example below, and store them in a vault.
Combined with a complicated password, using MFA will make it much harder for bad actors to impersonate you. Most online services these days give the option of enabling multi-factor authentication. Examples are business apps like Office 365, Google Apps/Gmail, your work’s VPN application, and even personal apps like your bank, Amazon, or Facebook offer this. Your password manager is also a very good candidate to enable MFA.
How can you get started?
First, you need another factor for authentication. Hardware devices such as RSA SecureID or Yubico’s YubiKey are good choices if you really want to take things seriously. You can also just use an app. Popular apps such as Google Authenticator, Microsoft Authenticator, Authy, and Lastpass Authenticator are all good examples.
Next, head over to your favorite application and log in. Usually in the same place in the settings area where you would change a password, there should be an option to enable 2FA/MFA/2-step verification/etc. While you’re at it, you should probably change your password if it isn’t complex or you haven’t done so in a while.
Just follow the instructions to enable MFA. This will vary slightly depending on application. In general, you’ll select your authenticator app or hardware key when prompted. If using an authenticator app, you will need to scan a QR code to add that account. Once you complete the setup, enjoy knowing that your security posture has been greatly improved.
Need help enabling MFA on your business applications such as Office 365 or your VPN client? Contact us today. Our friendly Zunesis engineers are here to help!
Security- Top Priority in Today’s World
Security is a hot button in today’s world. Now that the number of remote workers has gone up significantly due to the health crisis, the rise of ransomware attacks has followed closely behind. Remote work environments increase the number of targets for hackers. Phishing attempts are up more than 600% in the last 6 months, exploiting new vulnerabilities in the workforce.
Multiple devices in multiple locations create new opportunities for cyberattacks. With a remote workforce, the chance for unexpected risks increases dramatically. One of those reasons being, employees use “work-arounds” and personal devices when accessing or sharing private data and documents.
There are many avenues to take when considering a heightened and more secure environment. Often, the enterprise infrastructure is not top of mind. Many solutions are available to tighten up an enterprise infrastructure to ensure a more secure environment. These projects are just as imperative when it comes to protecting your company as others.
A number of Zunesis clients have shifted focus from other high priority projects to firewall implementations. This is in an attempt to mitigate the increased security risks.
Firewall
A firewall is a network security system that monitors and controls incoming and outgoing network-traffic. It is based on predetermined security rules. It typically establishes a barrier between a trusted internal network and untrusted external network, such as the Internet.
Depending on the enterprise, a firewall solution can look very different from one company to the next. All entities should be aware of their needs and choose accordingly.
Identifying and deploying a firewall solution specific to the needs of your company is a great place to start. How else can we tighten up an enterprise infrastructure to aid in the security of company information during these cyber wars?
Zunesis Services – Risk Mitigation
Zunesis has assessments available to aid in the risk mitigation of your organization.
Firewall/Network Assessment
Often times, organizations understand the importance of a firewall, and may have even purchased a firewall solution. But, organizations frequently fail to configure said solution correctly or are not using it to its full capability. Zunesis has created an assessment to help your organization with your network security firewall needs.
The Zunesis Firewall Assessment will discover the overall utilization of an organization’s current firewall and their adherence to industry’s best standards. Components of change management and administrative access to the firewall(s) will be examined. Additional focus is made to examine the strength of the existing firewall access control lists (ACLs). Recommendations will be made on how to streamline the firewall rules or leverage additional features to make them more secure.
Ransomware Readiness and Recovery Assessment:
There will be an estimated $6 trillion in damages to business by 2021 from ransomware. The advantage of being prepared, is that you can manage problems quickly and more efficiently by already having a solution ready when a problem ensues. The importance of preparation is that it is a time saver – and time is money!
Intelligent Data Protection is a comprehensive approach to data protection and copy data management. It focuses on how an organization protects and uses its data (now and in the future). Is your organization prepared? What is your backup policy? What is your Disaster Recovery plan?
Zunesis has developed an assessment that documents the readiness of an organization to recover data that may have been impacted by a Ransomware attack. Through review and analysis, a Zunesis engineer will provide observations and recommendations to better prepare your organization for future data attacks.
Recurring Data Center Assessment Services:
If limited resources within your company’s IT department is problematic, maintenance details are often the first thing to slip through the cracks. It is important to stay on top of firmware updates, device OS updates and other customer advisories.
Through RDCAS, we ensure that the most current software and firmware updates are installed across your environment. We work closely with your organization to determine the frequency of your infrastructure review.
The review is limited to the following HPE infrastructure devices including: blades and rack mount servers, HPE Storage, HPE Fibre Channel Switches, HPE Synergy Frame and HPE SimpliVity Hyper-converged platform.
What does the future hold for security innovation and advancements?
The future for security in today’s organizations will still remain a high priority. Here are a few predictions from IT experts.
- Artificial Intelligence (AI) will be a core component of cybersecurity systems
- Cyber warfare threats will be a focus
- The number of hackers will rise
- Developing cybersecurity talent becomes essential
- Legacy technology will continue to be an issue
Zunesis’ commitment is to help moderate problems and issues that arise within the industry. Our goal is to make the lives of our clients better. With risks and threats to businesses on the rise, Zunesis is dedicated to helping our clients prepare for the worst, plan for the best, and manage the present.
The New Normal
The new normal. How many times have you heard that recently? What is the new normal? Are their changes in IT being implemented as a result of the Covid-19 virus? What is changing in IT as a result of the demonstrations and riots in our society today? These are all questions I have been asked recently by friends, customers and business associates. This seems to be at the top of everyone’s conversations.
Just to be honest, I don’t like the phrase “the new normal”. Nothing about this is normal. A recent article in Forbes discussed how CTO’s are navigating this new normal. Everything going on today is changing the world of IT.
Most of my recent conversations have focused around three areas: Security, remote access and disaster recovery. These three topics have come to the forefront of every conversation I have had lately. This is nothing new, businesses have been talking about or using these for years. But they have taken on a new urgency. People are more serious about getting something in place, now.
Security
I am primarily talking about security as it relates to access security and physical security. Using video analytics, many locations are more serious about tracking people. A school may want to know who is coming and going using facial recognition. Another instance is where a store wants the count of how many people occupy a store at any given time. People are more interested in understanding how video analytics can help their business.
There are many use cases for video analytics. We have had conversations around using technology. Some uses include monitor social distancing and temperature tracking of employees and customers. A recent Harvard study estimates that social distancing restrictions are likely to remain in place long-term. “Researchers from the Harvard T.H. Chan School of Public Health have warned that, in the absence of a vaccine or an effective treatment of the coronavirus, social-distancing measures may be required through to 2022,” reported CNBC.
Another tactic is tracking who is in a school or casino or how many people are currently in a store, restaurant or casino. There are so many possibilities and way too many to list here.
Virtual Desktop Infrastructure
Many of our customers are using virtual desktop capability to some extent. What has changed is remote desktop projects are getting funded and taking on a sense of urgency. Whether this is moving to a work from home model, remote learning or something else. Many of our customers have had a project like this on the list. Now it is a top priority. We are going to see many businesses and schools move to a remote access on a permanent basis. This means a complete change in how they do business, how they connect, how they work on projects, everything.
Disaster Recovery
Disaster recovery, including Ransomware recovery, has been on the list of every IT department projects. Some companies are very good at DR and have made it a priority. Others have it on the list of projects that never seem to get done.
Recently, we spent over a month working with a customer that got hit with Ransomware. I have heard of larger customers spending many months, even up to a year trying to fully recover. We spent additional time, working with the customer to put safe guards in place. We did this so if this does happen again, the recovery time is minimal. This type of scenario is happening more often and needs to be addressed now. Before the unthinkable happens.
Contact Zunesis to for an assessment of the state of your infrastructure. Let us help you with this “new normal” and keep your business moving.
What? You still aren’t backing up your Office 365 Tenant?
Office 365 has become one of the most popular cloud-based productivity platforms. According to a recent study performed by Barracuda, “Market Analysis: Closing Backup Recovery Gaps”, more than 60% of IT professionals are using it to drive business success in some fashion. Email is the most popular (78%), followed by OneDrive (60%), SharePoint (50%), Teams (36%), and OneNote (35%).
Office 365 Security
Microsoft has done a good job in creating “Best Practices” for Office 365 Tenant Security. On January 6, 2020, they released the “Top 10 ways to secure Office 365 and Microsoft 365 Business Plans.” Its aim is to help secure organizations achieve the goals described in the Harvard Kennedy School Cybersecurity Campaign Handbook.
Microsoft recommends the following be applied to your Office 365 environment:
- Setup multi-factor authentication
- This is the easiest and most effective way to increase the security of your organization. Add a 2-step verification to all accounts. In addition to the password, there is a second component. This is usually a mobile device, which provides a code received from Office 365.
- Train your users
- Establish a strong culture of security awareness within the organization. This includes training users to identify phishing attacks. For example, don’t open the attachment just because someone you know sent it to you.
- Use separate/dedicated admin accounts
- Admin accounts are valuable targets for hackers. Admins should have a separate account for regular, non-administrative use.
- Raise the level of protection against malware in email
- Blocking of attachments with file types that are commonly used for malware.
- Protect against ransomware
- Warn users of messages originating external to the organization. Blocking of file extensions that are commonly used for ransomware. Warn users who receive attachments that include macros.
- Stop auto-forwarding for email
- Hackers who gain access to a user’s mailbox can exfiltrate mail by configuring the mailbox to automatically forward email.
- Use Office 365 Message Encryption
- Organizations can send and receive encrypted email messages between people inside and outside the organization.
- Protect your email from phishing attacks
- Configure anti-phishing protection, ATP (Advanced Threat Protection). This can help protect from malicious impersonation-based phishing attacks.
- Protect against malicious attachments and files with ATP (Advanced Threat Protection) Safe Attachments
- Helps determine whether an attachment is safe or malicious.
- Protect against phishing attacks with ATP (Advanced Threat Protection) Safe Links
- Hackers sometimes hide malicious websites in links in email or other files. Safe Links can help protect by providing time-of-click verification of web addresses (URLs) in email messages and Office documents.
Where’s Backup
 One glaring omission, not purposely according to Microsoft, is backup and retention of Microsoft 365 data. Microsoft does not hide the fact that they do not backup or provide long-term retention of Microsoft 365 data.
One glaring omission, not purposely according to Microsoft, is backup and retention of Microsoft 365 data. Microsoft does not hide the fact that they do not backup or provide long-term retention of Microsoft 365 data.
Wait……. What?
That’s right, Microsoft does not provide backup or long-term retention of Microsoft 365 data.
Let that sink in.
Microsoft does not provide backup or long-term retention of Microsoft 365 data.
An estimated 40%, that’s right 40%, of Microsoft 365 organizations aren’t using any third-party backup tools to protect their mission-critical data. Mostly due to a major misconception that Microsoft is backing up their data for them.
40% of Microsoft 365 Organizations
are not using third-party backup tools to protect
their mission critical data
Microsoft uses the term, shared responsibility model:
- They have physical security in their data centers.
- They offer data storage replication and redundancy.
- Their SLAs include guarantees of uptime and privacy controls.
- They will protect you from natural disasters that affect their data centers, hardware or software failures on their part, power outages, operating system errors, etc.
- You are responsible to protect your data from human error (due to malicious activity or innocuous accidents), misconfigured workflows, hackers, and viruses. Backing up your users and data is truly your responsibility. If you are not proactive about that, any help you get from Microsoft in times of crisis is minimal at best.
In other words, while Microsoft provides a resilient SaaS infrastructure to ensure availability, it does not protect data for historical restoration for long. Its SLAs don’t protect against user error, malicious intent or other data-destroying activity. In fact, deleted emails are not backed up in the traditional sense. They are kept in the Recycle Bin for a maximum of 93 days before they’re deleted forever. If a user deletes an email, and the retention period is reached, that email is gone forever. If a user deletes their whole mailbox, the admin doesn’t realize, and the retention period is reached, the whole mailbox is gone.
On SharePoint and OneDrive, deleted information is retained for a maximum of 14 days by Microsoft. Individuals must open a support ticket to retrieve it. SharePoint and OneDrive are unable to retrieve single items or files. They must restore an entire instance. It’s unlikely that such short retention policies will meet most compliance requirements.
Don’t Make a Costly Mistake
Many assume that Microsoft will support their backup requirements for Office 365 data. This could be a costly mistake. If they suffer a serious incident, they could find that crucial data has been deleted permanently. There are plenty of advanced, cost-effective third-party backup and recovery solutions for Office 365. IT Managers should revisit their backup strategies to ensure there are no gaps in coverage, especially in cloud-based applications, such as Office 365.
Need assistance navigating Microsoft products and backup solutions, contact Zunesis.

