Data Protection
In the age of ransomware and digital transformation, your company’s data is even more critical than ever to keep your business running. While avoiding data loss is the main priority of backups, it can often be hard to balance that with the cost of those backups. On top of all that, data is harder to manage and control than ever due to multi-cloud infrastructure and workers more often working remotely.
So how do you deal with all of that and still have a trusted backup in case the worst should happen? You need a single, robust solution for data management that can protect your data through all phases of its lifecycle.
Veeam has been a leading player in the backup space for a while now. It has really stepped up when it comes to addressing new challenges in data protection. It has a host of different products, enterprise to consumer, that make it easy for businesses big and small to tackle the issue. They continue to innovate and keep your data secure while remaining flexible enough to fit into any environment. This year is no different with the release of Veeam version 11.
So what is new in the newest version of Veeam?
Continuous Data Protection, or CDP
It integrates with VMware environments to eliminate downtime and minimize data loss with a host of new features. CDP will eliminate the need for VM snapshots with I/O level tracking, and reduce the bandwidth needed for replication. It works on any OS or application as long as they are running in a vSphere VM. CDP will also schedule your jobs for you, just define the required RPO and CDP will take care of it. Depending on the amount of data, CDP can also offload data processing from your hosts to proxies. It calculates the required bandwidth to eliminate guesswork.
Hardened Repositories
This keeps your backups safe from malware and hackers with immutable backups. Single-use credentials are never stored in the configuration database eliminating any possibility of those credentials being extracted from a compromised backup server.
Expanded Object Storage Support
This feature reduces the cost of long-term archives. Veeam now integrates with Amazon S3 Glacier and Azure blob archive storage which are best for very long-term storage. These repositories can be made immutable, and are policy-based, so no management required.
Expanded Instant Recovery
It makes even more of your workloads instantly available. Instant recovery has been a feature of Veeam for a while, but now it has been expanded to include SQL and Oracle databases. Regardless of size, databases are made available to production applications and clients in minutes. You can then finalize those recoveries either manually, or by scheduling them to switch as soon as synchronization catches up, or even scheduling the switch during maintenance hours.
More Improvements
Veeam has made many more improvements with Version 11, enhancing many aspects of the program. GFS and Archive backups have added functionality. Powershell is now more powerful. Backup speeds have increased. Compliance with WORM backups has been added. As well, the GUI has seen some improvements. All of these features are included with normal licenses, you don’t need to pay extra for any of this stuff.
I am barely even scratching the surface on what is in the new version. I am most excited about the steps Veeam is taking to make their product more resilient against viruses and ransomware. Ransomware attacks have ramped up over the last few years. Keeping good copies of data in case of such an attack has been a struggle. Companies like Veeam have been in an arms race against hackers. Things like immutable backups are a huge leg up in the fight. Maybe someday, we won’t have to worry about that stuff, but for now, at least we have Veeam.
Contact Zunesis to find out more about Veeam V11.
Every 11 seconds, a network is attacked by ransomware. Each successful attempt costs a company $80,000 on average. This adds up to over $20 billion each year. This number continues to grow each year. Cyber security is quickly becoming one of the most important investments for companies large and small.
These investments come in many forms; training, antivirus programs, spam filters, and backups to name a few. Once your data is compromised though, there is really only one thing you can do. You need to do a restore from a backup.
So, how does Veeam backup help protect data against ransomware?
Immutable backups
Immutable backups are copies of your data that cannot be changed. Veeam offers immutability in the capacity tier of their Scale-out Backup Repository (SOBR). It leverages a native function of object storage that prevents blocks of data from being changed for a set amount of time. Not even a malicious admin with full access to backups can change this data, let alone ransomware.
Air-Gapping
A related concept is air-gapping your backup repository. This basically means backups are unreachable or offline after the backup is taken. A common way of doing this is tape backups. Once the tape is written, it is physically removed from the network. It is stored in a secure location, inaccessible until the tape is moved back onto the network.
Another feature offered by Veeam that is similar is rotated media. This allows to swap hard drives for the backup chains so that one or more hard drives with backup data are offline or air gapped at all times. This protects that set of data from attacks.
Veeam ONE
Detecting ransomware in its initial stages can be difficult. Veeam ONE provides the ability to monitor your environment closely and be aware of any suspicious or abnormal activity. By analyzing CPU usage, datastore write rate, and network transmit rate, Veeam ONE can help identify higher than normal activity on a particular machine, trigger an alarm, and immediately notify you to inspect the machine.
Veeam SureBackup
SureBackup is a feature of Veeam that allows you to create a sandbox to test your backups before restoring them to production. It can run virus and malware scans on backup sets, automatically or manually. It ensures your data is not infected without the need to restore the data somewhere first.
Secure Restore
A related feature is Secure Restore, which scans your data as it is being restored. This gives you access to the latest virus definitions which helps safeguard against viruses that were previously unknown at the time of the backup.
Veeam DataLabs
Unsure of a workload, or suspect it may be infected? DataLabs gives you the ability to restore the data to a fully secured and isolated environment to test. A fully isolated sandbox lets you run any tests you want without impacting production systems, so you can make sure your workloads are uninfected before you restore them.
Ransomware protection alliance
Veeam is part of a group of leading hardware and software companies, like HPE, Cisco, and AWS, that work together to make sure their products integrate using the highest security standards possible. They bring together the most powerful recovery solutions to combat ransomware.
Veeam backup and recovery is a powerful tool in the fight against ransomware. It is completely dependent on how it is implemented and used. You should always secure your backup server, follow the 3-2-1 rule, implement Veeam’s features for ransomware detection, protect your network, and test your backups. A good backup strategy is just another piece in the puzzle in the fight against ransomware.
Contact Zunesis to find out more about Veeam backup and recovery solutions for your organization.
Access to your Business-Critical Data and Applications
There are many facets to a thoughtful plan for maintaining highly available access to your business-critical Data and Applications. The consideration starts with the location of your hardware infrastructure components (Compute, Networking, Storage). Does the facility provide security, cooling, reliable and redundant power, etc.? Are your hosts, storage and network equipment designed with redundancy, i.e, Power Supplies, Fans, Drives, etc.? Does your design include Clustering, Replication, perhaps a Disaster Recovery site? All of these are part of a complete plan.
But, even the most highly available hardware infrastructure is not much use without the Data and Applications it is configured to support. For protection of data and applications, we must have a Backup/Recovery process in place. Often, with Backup/Recovery implementations, the biggest effort is with the initial setup. This is where the software is installed, backup targets are configured, and backup jobs are defined. After that, the jobs get monitored periodically. If the job status is green, then nothing more is done until a file or Virtual Machine (VM) needs to be recovered.
Testing is Important
While taking time to plan the jobs and maintain consistent monitoring of them is critical, testing the Recovery of the Data and Applications being protected is equally important. All of us would likely agree we need to validate our Backup data. However, this is a step that is often pushed to the side because of competing priorities in every IT environment. For many IT environments, Backup/Recovery becomes a “set it and forget it” activity. The focus is mainly on the Backup process.
So, perhaps the answer to ensuring we validate the recoverability of what we are backing up is to automate the validation process. At Zunesis, we partner with Veeam to help our clients protect their Data and Applications with Veeam Backup and Replication (Veeam B&R). If you aren’t familiar with Veeam, let me provide a brief summary.
Veeam Backup and Replication
Veeam B&R is a Backup/Recovery application for protecting any workload, including virtual machines, physical servers, Oracle, Microsoft SQL, Exchange, Active Directory, Microsoft SharePoint, NAS, and Cloud. These don’t represent everything that Veeam B&R can protect, but this list should make it clear that Veeam will likely be able to protect any workload in your environment. Furthermore, Veeam has built-in Replication, WAN Acceleration, Integration with many storage arrays, Encryption, Deduplication, Compression, and more.
Veeam SureBackup
But the one feature I want to highlight here is Veeam SureBackup. Perhaps you use Veeam and have seen the SureBackup option in the management console but never really explored its capabilities. To summarize, SureBackup is the Veeam technology that lets you test VM backups and validate that you can recover data from them. With SureBackup, you can verify any restore point of any VM protected by Veeam B&R. Using SureBackup, Veeam B&R can boot the VM from the Backup in an isolated environment, scan VM’s for malware, run tests against the VM, power the VM off and create a report on the recovery verification results. The report can then be automatically emailed to you for review.
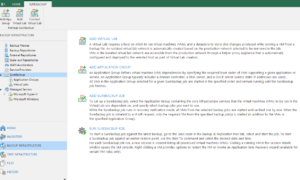
As referenced below, SureBackup is a feature you would see whenever you are viewing the Veeam B&R Management Console. And like most of the Veeam features, you are guided through its setup using a step-by-step process in the Management Console. The screenshot shown below lists the major steps (in order) for setting up the SureBackup environment.
While it is beyond the scope of this post to walk you through the entire setup, I would like to provide you a summary of the setup using the steps outlined in the screenshot above. Through this Summary, I hope to convey the power of the Veeam SureBackup feature.
It is important to remember that the SureBackup feature utilizes VM’s that are protected by scheduled Veeam Backup Jobs.
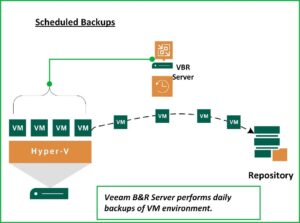
Once you have the Backup Jobs defined, you can setup the SureBackup environment to validate that what you’re backing up can be restored when the need arises. So, let’s take a look at the major steps required to implement SureBackup.
ADD VIRTUAL LAB
The first step in building a SureBackup environment is to Create a Virtual Lab. The virtual lab is an isolated virtual environment in which the backed up Virtual Machines are started and tested. You can create multiple Virtual Labs depending on your needs. During the creation of the Virtual Lab, Veeam B&R will deploy a Linux Appliance that will fence off your Production environment from the Virtual Machines being tested.
The Appliance will act as Gateway, provide DHCP, and Routing to the isolated environment while facilitating access from the Production environment if needed. To accomplish this, the Appliance has network access to both the Production environment and to the Virtual Lab. With the Appliance in place, VM’s can be restored to the virtual lab using the same IP Addressing as they have in the Production environment from which they were Backed up. The Appliance will keep any conflicts from arising between the two parallel environments.
ADD APPLICATION GROUP
With the Appliance in place, it’s time to create the Application Groups. An Application Group includes the VM’s you want to validate along with any VM’s they may be dependent upon. For instance, if you want to test a SQL Database Server, you will probably want to have a Domain Controller and DNS Server available and perhaps the Application Server. So, the Application Group is the place where you define a working environment for the workloads you want to validate.
ADD SUREBACKUP JOB
With the Virtual Lab(s) and Application Group(s) Defined, it’s time to create the actual SureBackup Job that will build the environment on-demand or based on a schedule. In this step you will specify the Virtual Lab you’ll be using and the Application Group you’ll be including in that Virtual Lab. Then, you can select from the Backup jobs you already have running to specify the VM’s you’ll want to validate.
As part of the Job creation you can configure what you want to test/validate for each VM. Examples of validation criteria include testing the disk content for corruption, scanning VM’s for malware, and performing PING tests. During the setup you are able to select predefined test scripts or include custom scripts to use for testing. Once all the components have been defined, you can schedule when you want the jobs to run (Daily, Weekly, Monthly). You will also decide to whom the Job results should be sent.
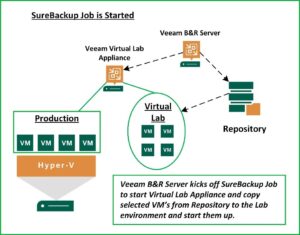
Benefits Worth the Effort
So, as you can see, the SureBackup environment will take a little time and planning to build and test. The benefits are well worth the effort.
It provides an automated method of validating Backups. Its design allows for the Virtual Lab to be created on-demand. This is an environment where one can test server and software updates, perform security testing, and conduct DevOps and Analytics. This is all done without impacting your Production environment. Veeam calls this capability the On-Demand Sandbox.
If you already use Veeam B&R, but haven’t tried the SureBackup option yet, I hope this post has encouraged you to give it a try. If you do not currently use Veeam, I hope your interest is peaked and you want to learn more. In either case, Zunesis has Solution Architects who can help you. We have Veeam B&R deployed in our lab so you can explore for yourself the SureBackup functionality. You can get a better understanding of this important piece of a thoughtful plan to maintain highly available access to your business-critical Data and Applications.
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.
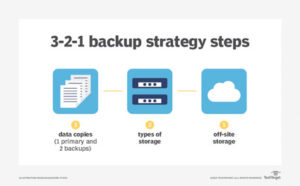
The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.

The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
Veeam Backup and Replication
As the CEO of Zunesis, I am fond of saying “get beyond talking and PowerPoint slides and find some way to take action”. Everyone can talk a good game, but far fewer can actual design and implement successful IT solutions on-time and within budget. I feel like customers are tired of watching our lips flap and instead want IT Solution Providers to show them actual tangible value. It seems that all customers are from Missouri these days “the show me state”.
In 2015, Zunesis made the decision to invest heavily in a Technology Lab so we could show our clients and prospects actual infrastructure solutions, software solutions and management platforms. The ability to show technology working, instead of just talking about it, has been a big benefit to our clients. Building out a professional technology lab has been expensive, but the rewards stretch beyond just show and tell. The Lab has also proven beneficial to our Solution Architects who constantly use the Zunesis Lab to hone their skills on newer technology and test specific upgrade paths for software. The IT world is always changing and we want to make sure that we have tested specific technology and integration paths before we recommend them and before we go on site for an implementation.

Zunesis – Technology Lab featuring Nimble Storage

Zunesis Technology Lab
Zunesis has been a Platinum Partner with Hewlett Packard Enterprise (HPE) for 13+ years. As a result, most of the technology in our lab is HPE. Today we have 3 different 3Par Storage Arrays, a Nimble Array, a C7000 Chassis that includes a variety of HPE Servers (Generation 7, 8 and 9) and OneView for overall systems management. The Lab has several Brocade Fibre Channel Switches and Moonshot servers. Within the Lab, we run VMware and Veeam software and have connections to the Microsoft Cloud – Azure. In the coming months, we will be installing new technology in the Lab including:
- Simplivity 2 node
- HPE Gen10 servers
- Aruba switches top of rack
- Extreme network top of rack switches
In the not too distant future, we will replace the C7000 Chassis with an HPE Synergy frame.
Our plans are to continue to invest in our Lab so we can show clients and prospects the actual technology, instead of just talking about it. Furthermore, the Lab is another way we can invest in the on-going technical training and proficiency of our Solution Architects at Zunesis. If you would ever like to stop by for a technology demonstration or just to talk about what you are trying to accomplish in your business, Contact us and would be happy to have you come by for a visit.

