Santa made a list and he checked it twice. Let’s find out who’s naughty and who’s nice!
Naughty List
Who is on the naughty list this year?
-
- Ransomware Attackers
- Bad Password Creators
- Uncommitted Remote Workers
Wondering why Ransomware Attackers take the number one spot on this year’s naughty list?
Ransomware is malicious software that poses a threat usually by denying you access to your data. The attacker demands a ransom from the victim, with the promise to restore access to their data upon payment (which rarely happens even if the victim pays the ransom).
In 2021, the estimate is that a ransomware attack will take place every 11 seconds. The total damage could reach $20 billion. To break that out, in 2019 the average cost per ransomware attack was $133,000. Imagine a 90% chance of someone holding a $133,000 ransom over you. This is happening all too often, and it is happening in the world of technology. No, thank you…. “SANTA”! (tattletale voice).
Though not in the same league as a ransomware attacker, bad password creators and uncommitted remote workers take second and third place on Santa’s list of naughtiness.
Passwords
Passwords provide the first line of defense against unauthorized access to your computer and personal (and your company’s) information. The stronger your password, the more protected your computer will be from the hackers and malicious attackers mentioned above. One of the most common ways that hackers break into computers is by guessing passwords.
Simple and commonly used passwords enable intruders to easily gain access and control of a computing device. If you want to be considered the ‘good’ worker that you are and to receive ALL of the toys and treats that you deserve this year, it is imperative you put thought into creating a unique and somewhat complex password. This not only protects you from having your personal information compromised, but your company will thank you too!
Casual Remote Workers
Casual remote workers, or in other words, remote workers who do not take company policies and procedures seriously, are the last of the naughties. With so many people now working from home, assailants have more opportunity to pull off an attack. There is a myriad of ways in which a remote worker can lessen the chances of a company being compromised; the below is a good place to start:
1. Brute force attack through the VPN
In a brute force attack, a hacker uses a rapid trial and error approach to guess the correct password, PIN, or encryption keys. It doesn’t require a lot of intellect or complex algorithms – it’s merely a guessing game. (Refer back to #2 on the list – create unique passwords!)
2.Command and Control via Phishing
Phishing is the fraudulent attempt to obtain sensitive information or data, such as usernames, passwords and credit card details, by disguising oneself as a trustworthy entity in an electronic communication. (Take the time to really think about what you are being asked. Work with your IT team to learn how to identify a phishing email)
3.Bypass of Multi-Factor Authentication
Multi-factor authentication is an electronic authentication method in which a computer user is granted access to a website or application only after successfully presenting two or more pieces of evidence to an authentication mechanism. (When you are asked if you would like to set up multifactor authentication, the answer is always yes 😊)
Nice List
Who is on the nice list this year?
- SysAdmins/IT Departments
- IT leadership for navigating 2020
- Leaders who allocated budget to team members over products
SysAdmins
In a simple definition, System Administrators fix computer server problems; they organize, install, and support an organization’s computer systems. This includes local area networks (LANs), wide area networks (WANs), network segments, intranets, and other data communication systems.
In a more accurate description of SysAdmins and your IT Department; they are super(wo)men! These individuals have always been deserving of appreciation from the surrounding departments and people in their lives, but 2020 has challenged the company’s IT departments to deliver even more, even faster. Expectations are that they continue making your company’s communication working seamlessly. In today’s world, they work tirelessly to ensure remote workers are set up to be efficient. They work hard to implement, teach, and manage policies and best practices for remote workers. Not only is your IT department on the nice list this year, but they also get to eat the cookie dough from the Christmas Cookie bowl too! Score!
IT Leadership
IT leadership is another group that made the nice list. When no one knows what is going on (and I do mean no one), people look to leadership for guidance and direction. The difficulties of leading a group of people and an organization have their own challenges in a “normal” year but when you’re working from a recipe that encompasses budget cuts, the need for innovation, navigating new working situations, and the increased pressure of diminishing cyberattacks, a “successful” outcome can be hard to measure.
The following challenges were top on the list for IT leadership this year:
- Cybersecurity
- Digital transformation
- Cloud computing
- Hiring
- Budget
Increased pressure to perform with drastically lower budgets has forced IT leaders to identify their very top priorities in order to allocate budgets appropriately. Nothing new here, leaders have done this since the beginning of time, but when you think your budget is one thing and it QUICKLY becomes another, this balancing act isn’t nearly as easy as it seems. To the leaders who opted to take care of their employees over buying the latest and greatest; thank you!! Your team noticed and MOST IMPORTANTLY, Santa noticed! You know what they say, “he knows if you’ve been bad or good so be good for goodness sake!!”
Happy Holidays to you and yours!
What VPN services are a Good Fit for you?
I am certain that many people are familiar with the concept of a VPN or virtual private network. They are used to gain access to a corporate network while traveling or at home. I would assert though that few are familiar with the growing market of personal VPN providers who target non-commercial entities and individuals.
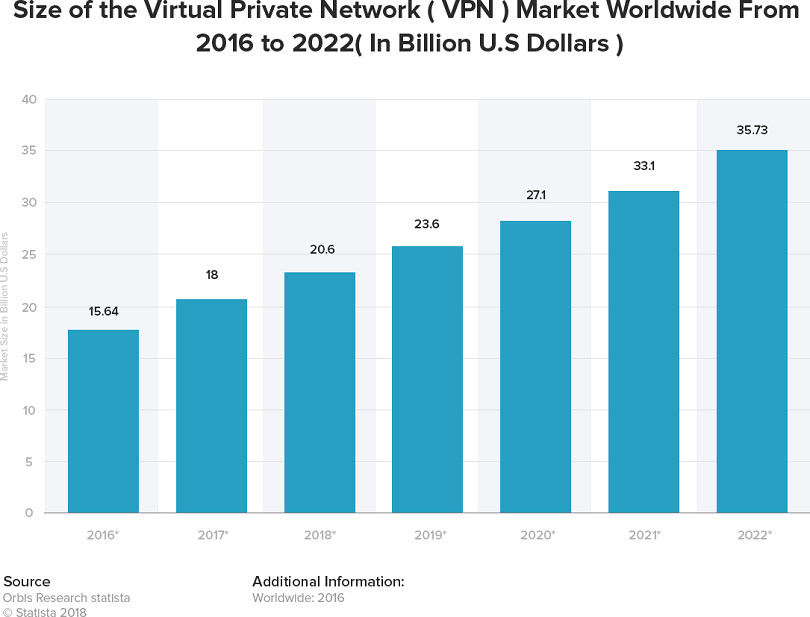
According to Orbis research Statista:
This market has grown eight billion dollars in the past five years
and is expected to grow another twelve billion in the next three years.
This emerging market has many players. Understanding which to use can be quite confusing to someone who is not well informed on the topic.
We will explore the concepts of how they differ from the often-provided corporate VPN’s. As well as discuss how to use them to protect your private information aside from how the company protects itself.
Corporate vs. Personal VPN
Most business travelers do utilize corporate VPN connections to gain access to company files and services. When the traffic is not destined to the business networks, the traffic is not tunneled back to the home office. This configuration is called split tunneling.
It is a very common configuration. Network engineers configure this so that users will not saturate the VPN concentrators with YouTube, Netflix and other non-business-related traffic. Additionally, as business travelers it is incumbent on us to use company assets such as bandwidth in a manner which is in line with our companies’ policies.
How do the personal VPN services work?
Most if not all personal VPNs use a client-based software to encapsulate and encrypt the traffic. This makes it very hard to unscramble if someone is capturing data from an open network.
The other mechanism used is to proxy the traffic to a third party where it is then sent to the eventual destination. The proxy or redirect mechanism ensures that the transmitted information doesn’t contain the public IP of the coffee shop or public network but the source IP address of the proxy service. This is important when connecting to financial institutions that monitor the public IP address that you normally connect from.
If for some reason another person attempts to connect to your bank account through the bank’s web portal, the bank would notice that it is not the normal public IP address that you would typically connect from and disallow the login attempt.
Who are they for?
Firstly, who should use a personal VPN? The answer is anyone who regularly uses free and open Wi-Fi at public places. Anytime you connect to the coffee shop Wi-Fi or to a hotels guest network connection, you are often at risk of someone intercepting the unencrypted traffic you are sending and receiving. This vulnerability has existed for many years and is called a, “man in the middle attack”.
This sort of intrusion used to be carried out by very skilled hackers but these days the attack is very well documented. Toolkits to exploit these common scenarios are being used by very unskilled characters.
Personal VPNs circumvent the vulnerabilities of open networks by using encapsulation and traffic proxying so that the connection is more secure and free from prying eyes.
Good rules to live by regarding when you should use a VPN include:
- Are you logging in to a private or personal account of any kind?
- Are you transmitting information that is proprietary?
- Is there personal or customer information being transmitted?
- Is banking or financial information being received?
If any of these conditions exist, I would recommend using a personal VPN to protect yourself. The many protective and anonymizing mechanisms that the VPNs employ would allow you to safely transmit and receive any data without the risk of intrusion.
Current major players in this market
I will not make any direct recommendation since at Zunesis do not sell these products directly. We can help with the implementation of them if requested. I would recommend that you find a solution that does satisfy the conditions I have covered.
This article from PCMag.com gives a great overview of how VPNs work and how each VPN company compared to the others.
How can Zunesis help?
At Zunesis, our expertise and offerings focus on corporate VPNs and other firewall services. We find it equally important that our clients and partners understand the risks involved when not utilizing some protective measures when they connect to open public Wi-Fi systems.
We have all heard of the unlucky Hollywood stars who have had their personal accounts targeted or hacked at great expense to themselves. Reputations are very important in business and in private life. Remember that the weakest link is not the traffic we monitor, it is the traffic we do not.

