Assessments – A Necessary Evil
Assessments are a necessary evil for an IT Department. Egos are hurt, exposure of negligence and complacency are all deliverables of a thorough assessment. But we’re going to look at it in a different way.
An IT Department can be considered the Heroes of an organization because they realized an assessment(s) needed to be done. Preventing a catastrophic breakdown or failure of an organization’s infrastructure or by saving an organization millions of dollars, the IT Team can leverage the C-Suite for that pool table in the breakroom without much resistance.
Limited Bandwidth
We all wear many hats in an organization and can be considered the Jacks of all trades and Masters of none. An individual who’s heading up the IT Department may have a Networking core competency but have little or no knowledge of a Storage competency. And, there’s the chance an individual and only that individual makes up the entire IT Department. This can be the case for SMB companies. Enterprises have a few folks, but even their bandwidth is not what it should be.
Gaps in knowledge ranging from Networking, Compute, Storage, etc. can jeopardize an organizations’ infrastructure. This can cause significant trouble with product outputs. However, being proactive instead of being reactive can help minimize the opportunity for failure or loss to occur.
Available Assessments
Assessment is a very broad term. There can be levels and micro-levels of assessments within an IT Infrastructure.
Here’s a very high-level summary of the types of assessments that are available via Zunesis at the click of the ‘SEND’ button on a product / service inquiry form:
1. IT Infrastructure Assessment – Experts will assess the current IT infrastructure and deliver a report detailing observations regarding hardware, software, and the business processes impacted by the organization’s IT environment. Recommendations and potential solutions should also be part of the final deliverable.
2. Data Management Assessment – Data Management Assessment Service can be used to focus separately on Production Data, Archive Data, Backup/Recovery, or it can encompass all three. Part of the perks of having this information would be to document current data management practices as well as short-term and long-term objectives.
3. Recurring Data Center Assessment & Advisory Service – This is a review of the IT Infrastructure Assessment, but it would occur on a quarterly, bi-annually, or yearly cadence. Benefits include lower support and maintenance costs, greater control over the existing environment and other attributes which lead to high performance without breaking the bank.
4. VMware Assessment Services – Deliverables include documentation on current environment, observations about current VMware use and short-term recommendations and areas of opportunity. This information will provide a clearer picture of the environment’s long-term strategy and cost efficiency.
5. Wireless Site Survey – This assessment should be done by all organizations (i.e., Government agencies, Education, office buildings, etc.). A Network Engineer will import floor plans into a tool and draw walls on the map to give them an idea of what their coverage area will look like. Or if already installed, the site survey will validate a recent wireless network installation.
6. Ransomware Recovery Preparedness & Risk Assessment – There’s no need to elaborate on this assessment. To be blunt, if an organization doesn’t feel this is necessary, then they better be prepared to lose all their data and pay a fortune to get it back. And, there’s a chance an organization may never get their lost data back. People will lose jobs over this if this assessment is not done and done soon.
7. Firewall Assessment – This provides the overall utilization of an organization’s current firewall and their adherence to industry’s best standards through a Network Vulnerability Assessment. Recommendations, best practices, snapshot of existing firewall layout, potential of what the layout can be in the long-term are just some of the attributes a company can glean from this assessment.
Potential Problem Analysis
Now that these assessments have been identified and the importance of each, organizations need to think operationally, tactically and strategically about the consequences and costs of not undergoing these assessments. Potential Problem Analysis consists of identifying the problem before it actually occurs. This type of thinking is true in any infrastructure environment and should be implemented immediately. Band Aide’s and Duct Tape can only go so far.
Again, being proactive rather than reactive, an organization can prevent significant down-times, reduce costs by protecting current hardware, avoid ransomware, avoid closure, save jobs and many other elements which will lead to continued operation time and an increased/valid sense of security.
Santa made a list and he checked it twice. Let’s find out who’s naughty and who’s nice!
Naughty List
Who is on the naughty list this year?
-
- Ransomware Attackers
- Bad Password Creators
- Uncommitted Remote Workers
Wondering why Ransomware Attackers take the number one spot on this year’s naughty list?
Ransomware is malicious software that poses a threat usually by denying you access to your data. The attacker demands a ransom from the victim, with the promise to restore access to their data upon payment (which rarely happens even if the victim pays the ransom).
In 2021, the estimate is that a ransomware attack will take place every 11 seconds. The total damage could reach $20 billion. To break that out, in 2019 the average cost per ransomware attack was $133,000. Imagine a 90% chance of someone holding a $133,000 ransom over you. This is happening all too often, and it is happening in the world of technology. No, thank you…. “SANTA”! (tattletale voice).
Though not in the same league as a ransomware attacker, bad password creators and uncommitted remote workers take second and third place on Santa’s list of naughtiness.
Passwords
Passwords provide the first line of defense against unauthorized access to your computer and personal (and your company’s) information. The stronger your password, the more protected your computer will be from the hackers and malicious attackers mentioned above. One of the most common ways that hackers break into computers is by guessing passwords.
Simple and commonly used passwords enable intruders to easily gain access and control of a computing device. If you want to be considered the ‘good’ worker that you are and to receive ALL of the toys and treats that you deserve this year, it is imperative you put thought into creating a unique and somewhat complex password. This not only protects you from having your personal information compromised, but your company will thank you too!
Casual Remote Workers
Casual remote workers, or in other words, remote workers who do not take company policies and procedures seriously, are the last of the naughties. With so many people now working from home, assailants have more opportunity to pull off an attack. There is a myriad of ways in which a remote worker can lessen the chances of a company being compromised; the below is a good place to start:
1. Brute force attack through the VPN
In a brute force attack, a hacker uses a rapid trial and error approach to guess the correct password, PIN, or encryption keys. It doesn’t require a lot of intellect or complex algorithms – it’s merely a guessing game. (Refer back to #2 on the list – create unique passwords!)
2.Command and Control via Phishing
Phishing is the fraudulent attempt to obtain sensitive information or data, such as usernames, passwords and credit card details, by disguising oneself as a trustworthy entity in an electronic communication. (Take the time to really think about what you are being asked. Work with your IT team to learn how to identify a phishing email)
3.Bypass of Multi-Factor Authentication
Multi-factor authentication is an electronic authentication method in which a computer user is granted access to a website or application only after successfully presenting two or more pieces of evidence to an authentication mechanism. (When you are asked if you would like to set up multifactor authentication, the answer is always yes 😊)
Nice List
Who is on the nice list this year?
- SysAdmins/IT Departments
- IT leadership for navigating 2020
- Leaders who allocated budget to team members over products
SysAdmins
In a simple definition, System Administrators fix computer server problems; they organize, install, and support an organization’s computer systems. This includes local area networks (LANs), wide area networks (WANs), network segments, intranets, and other data communication systems.
In a more accurate description of SysAdmins and your IT Department; they are super(wo)men! These individuals have always been deserving of appreciation from the surrounding departments and people in their lives, but 2020 has challenged the company’s IT departments to deliver even more, even faster. Expectations are that they continue making your company’s communication working seamlessly. In today’s world, they work tirelessly to ensure remote workers are set up to be efficient. They work hard to implement, teach, and manage policies and best practices for remote workers. Not only is your IT department on the nice list this year, but they also get to eat the cookie dough from the Christmas Cookie bowl too! Score!
IT Leadership
IT leadership is another group that made the nice list. When no one knows what is going on (and I do mean no one), people look to leadership for guidance and direction. The difficulties of leading a group of people and an organization have their own challenges in a “normal” year but when you’re working from a recipe that encompasses budget cuts, the need for innovation, navigating new working situations, and the increased pressure of diminishing cyberattacks, a “successful” outcome can be hard to measure.
The following challenges were top on the list for IT leadership this year:
- Cybersecurity
- Digital transformation
- Cloud computing
- Hiring
- Budget
Increased pressure to perform with drastically lower budgets has forced IT leaders to identify their very top priorities in order to allocate budgets appropriately. Nothing new here, leaders have done this since the beginning of time, but when you think your budget is one thing and it QUICKLY becomes another, this balancing act isn’t nearly as easy as it seems. To the leaders who opted to take care of their employees over buying the latest and greatest; thank you!! Your team noticed and MOST IMPORTANTLY, Santa noticed! You know what they say, “he knows if you’ve been bad or good so be good for goodness sake!!”
Happy Holidays to you and yours!
As we approach day [xyz] of the plague, I was ready to write another blog post about COVID-19 and technology. It seems that all we can think about lately is the virus. Working from home with three kids under 10 years old certainly has been “fun” for me. I’ll definitely be glad once this thing is gone.
Ransomware Uptick
Instead, I’d like to take some time to talk about ransomware. Another currently rampant plague of the digital variety. Among malware, ransomware is some of the absolute worst of the worst. It certainly has it’s own place in H-E double hockey sticks.
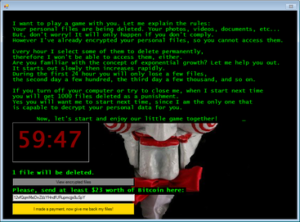
At a time where people and businesses are already suffering, we are seeing an uptick in ransomware attacks. Encryption of your files occurs, and cyber criminals demand a ransom in order to decrypt them. Often times, organizations use military grade encryption. So, the only way to decrypt the files is to pay the ransom.
Since only the criminals have the required decryption keys, it would be nearly impossible to decrypt even with your handy dandy cereal box decoder ring. Unfortunately, paying the ransom is a risky proposition. There is no guarantee that your files will be decrypted. This also validates the cyber criminal business model and encourages bad actors.
Ransomware spreads like fire, and burns the building to the ground if you don’t prepare.
How to deal with ransomware
BACKUP
First of all, you REALLY should have good backups. This doesn’t prevent the ransomware attack, but it certainly prevents you from needing to either a)open up your wallet or b)lose important data.
You might be surprised how many of us don’t follow rule #1 for data. Backups should be available locally, as well as off-site/cloud. You should also make sure that you can restore multiple points in time. This is in case your more recent backups contain ransomware. This isn’t just best practice for ransomware, it is just good practice in general.
Whether it comes in the form of ransomware, hard drive failure, data corruption, or space aliens shooting lasers at your PC, you really should have a plan for your data. How much is your data worth to you? For the ransomware event, skip the heartburn and restore from backup prior to an attack.
Prevent ransomware with good personal cyber hygiene
Be proactive with cyber security. Here are some suggestions:
- Rule #1 – Take regular backups
- Rule #2 – Take regular backups
- Rule #3 – Make sure your backups are good, and validate that you can restore from them.
- THINK BEFORE YOU CLICK
- Make sure that you are using reputable antivirus and malware protection to stop most threats.
- Stop believing that your AV/Malware prevention suite will stop 100% of attacks, zero day exploits will keep coming.
- Do not open files from people that you do not know, or click on random email links from your “bank” asking you to “update” your information.
- Have a good firewall, network segmentation, SPAM filter, etc.
- Don’t re-use the same few passwords for EVERYTHING. Do not use the same password with 1,2,3,etc., to get around password complexity requirements not allowing you to re-use your password.
- Use multi factor authentication where possible.
- Make sure that you are updating your operating system regularly.
- Security patches don’t work if you don’t install them.
What to do if you get hit with Ransomware
Hopefully this will always be theoretical, and you never get hit. First of all, you definitely want to isolate the machine. This stuff will scan your ARP tables, your registry, and a variety of other sources to look for other hosts to infect. I’d say immediately power off, enter the nuclear codes, and kill it with fire. In other words, wipe/erase the machine. You can then move forward with rebuilding the OS and restoring your data once you’ve got a blank canvas. Just because your security scan came up clean does not 100% guarantee a malware free result.
Next, if there are other machines on the network, quarantine and examine them. Ransomware will proactively work to infect everything else it can on the network. If other machines are impacted, they should also be nuked and rebuilt. This includes your business critical servers. Actually, this is especially critical for business critical systems. These systems house critical data, and are often a central point of access(points of infection) by many users. YES, THIS IS PAINFUL. However, if you have good backups to restore from, it isn’t nearly as big of a deal.
Are you prepared?
Much like the human pandemic that we are all too familiar with, hopefully you are “distancing” yourself from the digital pandemic. The best way to beat a ransomware attack is prevention, not reaction after the fact when it’s too late. If you need help preparing, or even just a second set of eyes to review your existing strategy, please contact us for an assessment. We are here to help.
What? You still aren’t backing up your Office 365 Tenant?
Office 365 has become one of the most popular cloud-based productivity platforms. According to a recent study performed by Barracuda, “Market Analysis: Closing Backup Recovery Gaps”, more than 60% of IT professionals are using it to drive business success in some fashion. Email is the most popular (78%), followed by OneDrive (60%), SharePoint (50%), Teams (36%), and OneNote (35%).
Office 365 Security
Microsoft has done a good job in creating “Best Practices” for Office 365 Tenant Security. On January 6, 2020, they released the “Top 10 ways to secure Office 365 and Microsoft 365 Business Plans.” Its aim is to help secure organizations achieve the goals described in the Harvard Kennedy School Cybersecurity Campaign Handbook.
Microsoft recommends the following be applied to your Office 365 environment:
- Setup multi-factor authentication
- This is the easiest and most effective way to increase the security of your organization. Add a 2-step verification to all accounts. In addition to the password, there is a second component. This is usually a mobile device, which provides a code received from Office 365.
- Train your users
- Establish a strong culture of security awareness within the organization. This includes training users to identify phishing attacks. For example, don’t open the attachment just because someone you know sent it to you.
- Use separate/dedicated admin accounts
- Admin accounts are valuable targets for hackers. Admins should have a separate account for regular, non-administrative use.
- Raise the level of protection against malware in email
- Blocking of attachments with file types that are commonly used for malware.
- Protect against ransomware
- Warn users of messages originating external to the organization. Blocking of file extensions that are commonly used for ransomware. Warn users who receive attachments that include macros.
- Stop auto-forwarding for email
- Hackers who gain access to a user’s mailbox can exfiltrate mail by configuring the mailbox to automatically forward email.
- Use Office 365 Message Encryption
- Organizations can send and receive encrypted email messages between people inside and outside the organization.
- Protect your email from phishing attacks
- Configure anti-phishing protection, ATP (Advanced Threat Protection). This can help protect from malicious impersonation-based phishing attacks.
- Protect against malicious attachments and files with ATP (Advanced Threat Protection) Safe Attachments
- Helps determine whether an attachment is safe or malicious.
- Protect against phishing attacks with ATP (Advanced Threat Protection) Safe Links
- Hackers sometimes hide malicious websites in links in email or other files. Safe Links can help protect by providing time-of-click verification of web addresses (URLs) in email messages and Office documents.
Where’s Backup
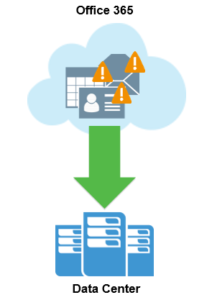 One glaring omission, not purposely according to Microsoft, is backup and retention of Microsoft 365 data. Microsoft does not hide the fact that they do not backup or provide long-term retention of Microsoft 365 data.
One glaring omission, not purposely according to Microsoft, is backup and retention of Microsoft 365 data. Microsoft does not hide the fact that they do not backup or provide long-term retention of Microsoft 365 data.
Wait……. What?
That’s right, Microsoft does not provide backup or long-term retention of Microsoft 365 data.
Let that sink in.
Microsoft does not provide backup or long-term retention of Microsoft 365 data.
An estimated 40%, that’s right 40%, of Microsoft 365 organizations aren’t using any third-party backup tools to protect their mission-critical data. Mostly due to a major misconception that Microsoft is backing up their data for them.
40% of Microsoft 365 Organizations
are not using third-party backup tools to protect
their mission critical data
Microsoft uses the term, shared responsibility model:
- They have physical security in their data centers.
- They offer data storage replication and redundancy.
- Their SLAs include guarantees of uptime and privacy controls.
- They will protect you from natural disasters that affect their data centers, hardware or software failures on their part, power outages, operating system errors, etc.
- You are responsible to protect your data from human error (due to malicious activity or innocuous accidents), misconfigured workflows, hackers, and viruses. Backing up your users and data is truly your responsibility. If you are not proactive about that, any help you get from Microsoft in times of crisis is minimal at best.
In other words, while Microsoft provides a resilient SaaS infrastructure to ensure availability, it does not protect data for historical restoration for long. Its SLAs don’t protect against user error, malicious intent or other data-destroying activity. In fact, deleted emails are not backed up in the traditional sense. They are kept in the Recycle Bin for a maximum of 93 days before they’re deleted forever. If a user deletes an email, and the retention period is reached, that email is gone forever. If a user deletes their whole mailbox, the admin doesn’t realize, and the retention period is reached, the whole mailbox is gone.
On SharePoint and OneDrive, deleted information is retained for a maximum of 14 days by Microsoft. Individuals must open a support ticket to retrieve it. SharePoint and OneDrive are unable to retrieve single items or files. They must restore an entire instance. It’s unlikely that such short retention policies will meet most compliance requirements.
Don’t Make a Costly Mistake
Many assume that Microsoft will support their backup requirements for Office 365 data. This could be a costly mistake. If they suffer a serious incident, they could find that crucial data has been deleted permanently. There are plenty of advanced, cost-effective third-party backup and recovery solutions for Office 365. IT Managers should revisit their backup strategies to ensure there are no gaps in coverage, especially in cloud-based applications, such as Office 365.
Need assistance navigating Microsoft products and backup solutions, contact Zunesis.
What’s on Your Mind? 2020 IT Needs
It’s 2020, the holidays are over and you’re back to managing your organization’s IT needs in support of their core initiatives. So, what’s on your mind? For many of our Clients, this can be summed up by three questions:
Are we adequately protected against Ransomware and can we recover from an attack?
Ransomware is a reality for individuals and businesses alike; no person or entity is immune. To someone responsible for protecting an entire organization from a Ransomware attack, the specter is ever-present. One that requires 24/7 vigilance. But these same individuals are keenly aware of that. Despite all their efforts to keep the attack from happening, they may be called upon to recover from an attack. We hear about this topic so much from our Clients that there are two BLOGS on the Zunesis website focusing on it exclusively. I would encourage you to read both Posts.
Mitigating the risks associated with Ransomware attacks requires a diligent adherence to a set of practices that include (but are not limited to):
- Keeping virus protection software up to date to keep up with the changing profiles of Ransomware attacks.
- Staying current with firmware patches on all devices (firewalls, switches, routers, serves, storage, etc.) to make sure your devices have the most recent protections.
- Staying current on Operating System updates and patches to plug security holes as they are identified.
- Managing usernames and passwords and segmenting authentication domains to reduce spread of an attack.
- Locking down non-essential ports to reduce points of entry.
- Segmenting LANs to minimize spread of an attack.
- Training of end-users to help them understand what to look for in emails and other external entry points. End-users are the most common entry point for attacks and the need for constant training cannot be over-emphasized.
If you are compromised, rather than paying a ransom, you’ll want to provide your organization with their best chance for recovery of your data. To accomplish this, you’ll need to spend time reviewing your backup/recovery and disaster recovery plans.
When reviewing your plans look for how they address the following:
- Are the frequency and retention policies designed to give you acceptable RPO and enough granularity to restore data that has not been compromised?
- Do you test your data for potential compromise?
- When looking at your backups, are they isolated from the rest of the network? Is there a possibility of being a target of attack (corruption or deletion)?
- Do you have multiple copies of your backups, on different media, and offsite?
- Does your backup/recovery software have built-in checks for warning of possible compromise?
- Do you have a standard practice of testing recovery of data?
While not exhaustive, the points outlined above, emphasize the multi-faceted approach an Organization needs to take in order to give themselves the best chance of avoiding the consequences of a Ransomware Attack. As I stated earlier in this post, Ransomware is top of mind for all our Clients and we will likely spend a lot of time working with them on this in 2020.
How will we get all our projects accomplished in 2020 and still manage the day-to-day tasks?
The challenge of not having enough resources and time have been a persistent issue in IT. I’ve been working in the industry for over 35 years and it seems there has never been enough money, time, or people to execute on the strategies developed to evolve and maintain the IT needs of an organization. In 2020 that is certainly not going to change.
The fact is, IT will always compete for the resources of the Organization because, for most organizations, their Mission Statement has nothing to do with building a world-class IT infrastructure. However, organizations across industries are more reliant than ever before on technology to carry out their primary Mission. For this reason, there will be an increasing array of projects that ultimately will need to be carried out by IT; the challenge of efficient resource utilization is not going to abate any time soon.
Is our infrastructure ready to support the needs of the Organization in a world where Digital Transformation is a constant, iterative process?
In the next decade, we will no doubt continue to see the evolution of how and where IT resources are utilized. After all, Digital Transformation is a journey, not a destination. More organizations are moving toward becoming Data-Driven, (leveraging Artificial Intelligence and Data Analytics to glean customer insights and make better decisions).
With this move, we will see the proliferation of Edge Computing devices, leveraging of IoT, and Machine Learning. These technologies will push us to adopt different strategies for on-premise and Cloud-based Compute, Network and Storage resources. For some IT organizations this will be a continuation of what they’ve already begun and for others it may mean a complete revamp of their existing infrastructure.
In the midst of protecting your organization from the bad actors, executing on new projects and maintaining the day-to-day tasks that are part of every IT organization, you and your team need to stay up with a constantly evolving industry that presents you with a myriad of options for continuing your Digital Transformation Journey. You can’t ignore the advances in technology, nor the relevance they might have for your organization, but finding the time to understand them and assess their value won’t be easy.
Our Available Services
 Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Whether you just want to sit down and discuss what’s on your mind, or you have already identified an area we can jump in and help, we are ready to engage. Just to give you an idea of what we have to offer, I’ve included a summary of some of the practices we have developed over 15 years to help our Clients achieve their goals.
NOTE: For any service we provide (one-time or ongoing), there is a standard process and set of deliverables we use as a starting template. From there, we will work with you to customize the service based on your specific needs. If there is one thing we know for certain, you have unique circumstances. We want to make sure our services conform to your specific needs.
Here are a few of our standard offerings:
IT Infrastructure Assessment – The objective for this assessment is to provide an analysis of where your infrastructure is today, where you want to see it in the future, and what will be required to bridge the gap.
Typical Tasks and Deliverables include:
- Discovery of Compute, Network, and Storage environment:
- Inventory/document configuration of on-premise equipment.
- Inventory/document applications (on-premise and cloud-based).
- Document hyper-visor and OS configurations.
- Document the types of data stored on-premise and, in the cloud.
- Review Backup/Recovery Infrastructure and policies.
- Review Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
- Produce a roadmap to go from where you are to where you want to be.
BC/DR Assessment – The objective of this assessment is to provide an analysis of your current Backup Recovery and Disaster Recovery architecture and processes. Because Ransomware is such a threat, we will conduct this assessment with a sub-focus on recovery from Ransomware attacks.
Typical Tasks and Deliverables here include:
- Discovery:
- Inventory/document configuration of backup environment.
- Inventory/document configuration of disaster recovery environment.
- Provide documentation on the types of data stored on-premise and in the cloud.
- Document SLA’s associated with applications and data.
- Log your Backup/Recovery policies.
- List details of Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
Recurring Data Center Advisory Service (RDCAS) – The objective of this service is to provide ongoing management of our Clients HPE environment. We monitor their device firmware and configuration. This helps them maintain best practices per HPE documentation. This service is provided over the course of a 12 Month period.
Typical Tasks and Deliverables include:
- Perform an initial inventory of all HPE devices, documenting firmware, configuration, and alerts.
- Monitor Critical Alerts published by HPE throughout the life of the service. Report these to the Client with recommendations for action.
- Monitor all alerts from HPE and report non-critical alerts in a quarterly report.
- Monitor release of new firmware and report to Client on quarterly basis (unless firmware is deemed critical).
- Offer assistance in deployment of firmware if needed.
- Assist in resolution of configuration if it doesn’t meet best practice per HPE documentation.
- Provide assistance in resolution of HPE support tickets as a Client advocate.
- Provide Quarterly environment reviews with Client.
Again, these are just examples of the ways we have helped our Clients address their challenges over the last 15 years. We have a team of technology professionals that are ready to assist you with all your infrastructure needs.
Have a great 2020. We look forward to hearing from you.
What’s on Your Mind? 2020 IT Needs
It’s 2020, the holidays are over and you’re back to managing your organization’s IT needs in support of their core initiatives. So, what’s on your mind? For many of our Clients, this can be summed up by three questions:
Are we adequately protected against Ransomware and can we recover from an attack?
Ransomware is a reality for individuals and businesses alike; no person or entity is immune. To someone responsible for protecting an entire organization from a Ransomware attack, the specter is ever-present. One that requires 24/7 vigilance. But these same individuals are keenly aware of that. Despite all their efforts to keep the attack from happening, they may be called upon to recover from an attack. We hear about this topic so much from our Clients that there are two BLOGS on the Zunesis website focusing on it exclusively. I would encourage you to read both Posts.
Mitigating the risks associated with Ransomware attacks requires a diligent adherence to a set of practices that include (but are not limited to):
- Keeping virus protection software up to date to keep up with the changing profiles of Ransomware attacks.
- Staying current with firmware patches on all devices (firewalls, switches, routers, serves, storage, etc.) to make sure your devices have the most recent protections.
- Staying current on Operating System updates and patches to plug security holes as they are identified.
- Managing usernames and passwords and segmenting authentication domains to reduce spread of an attack.
- Locking down non-essential ports to reduce points of entry.
- Segmenting LANs to minimize spread of an attack.
- Training of end-users to help them understand what to look for in emails and other external entry points. End-users are the most common entry point for attacks and the need for constant training cannot be over-emphasized.
If you are compromised, rather than paying a ransom, you’ll want to provide your organization with their best chance for recovery of your data. To accomplish this, you’ll need to spend time reviewing your backup/recovery and disaster recovery plans.
When reviewing your plans look for how they address the following:
- Are the frequency and retention policies designed to give you acceptable RPO and enough granularity to restore data that has not been compromised?
- Do you test your data for potential compromise?
- When looking at your backups, are they isolated from the rest of the network? Is there a possibility of being a target of attack (corruption or deletion)?
- Do you have multiple copies of your backups, on different media, and offsite?
- Does your backup/recovery software have built-in checks for warning of possible compromise?
- Do you have a standard practice of testing recovery of data?
While not exhaustive, the points outlined above, emphasize the multi-faceted approach an Organization needs to take in order to give themselves the best chance of avoiding the consequences of a Ransomware Attack. As I stated earlier in this post, Ransomware is top of mind for all our Clients and we will likely spend a lot of time working with them on this in 2020.
How will we get all our projects accomplished in 2020 and still manage the day-to-day tasks?
The challenge of not having enough resources and time have been a persistent issue in IT. I’ve been working in the industry for over 35 years and it seems there has never been enough money, time, or people to execute on the strategies developed to evolve and maintain the IT needs of an organization. In 2020 that is certainly not going to change.
The fact is, IT will always compete for the resources of the Organization because, for most organizations, their Mission Statement has nothing to do with building a world-class IT infrastructure. However, organizations across industries are more reliant than ever before on technology to carry out their primary Mission. For this reason, there will be an increasing array of projects that ultimately will need to be carried out by IT; the challenge of efficient resource utilization is not going to abate any time soon.
Is our infrastructure ready to support the needs of the Organization in a world where Digital Transformation is a constant, iterative process?
In the next decade, we will no doubt continue to see the evolution of how and where IT resources are utilized. After all, Digital Transformation is a journey, not a destination. More organizations are moving toward becoming Data-Driven, (leveraging Artificial Intelligence and Data Analytics to glean customer insights and make better decisions).
With this move, we will see the proliferation of Edge Computing devices, leveraging of IoT, and Machine Learning. These technologies will push us to adopt different strategies for on-premise and Cloud-based Compute, Network and Storage resources. For some IT organizations this will be a continuation of what they’ve already begun and for others it may mean a complete revamp of their existing infrastructure.
In the midst of protecting your organization from the bad actors, executing on new projects and maintaining the day-to-day tasks that are part of every IT organization, you and your team need to stay up with a constantly evolving industry that presents you with a myriad of options for continuing your Digital Transformation Journey. You can’t ignore the advances in technology, nor the relevance they might have for your organization, but finding the time to understand them and assess their value won’t be easy.
Our Available Services
 Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Whether you just want to sit down and discuss what’s on your mind, or you have already identified an area we can jump in and help, we are ready to engage. Just to give you an idea of what we have to offer, I’ve included a summary of some of the practices we have developed over 15 years to help our Clients achieve their goals.
NOTE: For any service we provide (one-time or ongoing), there is a standard process and set of deliverables we use as a starting template. From there, we will work with you to customize the service based on your specific needs. If there is one thing we know for certain, you have unique circumstances. We want to make sure our services conform to your specific needs.
Here are a few of our standard offerings:
IT Infrastructure Assessment – The objective for this assessment is to provide an analysis of where your infrastructure is today, where you want to see it in the future, and what will be required to bridge the gap.
Typical Tasks and Deliverables include:
- Discovery of Compute, Network, and Storage environment:
- Inventory/document configuration of on-premise equipment.
- Inventory/document applications (on-premise and cloud-based).
- Document hyper-visor and OS configurations.
- Document the types of data stored on-premise and, in the cloud.
- Review Backup/Recovery Infrastructure and policies.
- Review Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
- Produce a roadmap to go from where you are to where you want to be.
BC/DR Assessment – The objective of this assessment is to provide an analysis of your current Backup Recovery and Disaster Recovery architecture and processes. Because Ransomware is such a threat, we will conduct this assessment with a sub-focus on recovery from Ransomware attacks.
Typical Tasks and Deliverables here include:
- Discovery:
- Inventory/document configuration of backup environment.
- Inventory/document configuration of disaster recovery environment.
- Provide documentation on the types of data stored on-premise and in the cloud.
- Document SLA’s associated with applications and data.
- Log your Backup/Recovery policies.
- List details of Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
Recurring Data Center Advisory Service (RDCAS) – The objective of this service is to provide ongoing management of our Clients HPE environment. We monitor their device firmware and configuration. This helps them maintain best practices per HPE documentation. This service is provided over the course of a 12 Month period.
Typical Tasks and Deliverables include:
- Perform an initial inventory of all HPE devices, documenting firmware, configuration, and alerts.
- Monitor Critical Alerts published by HPE throughout the life of the service. Report these to the Client with recommendations for action.
- Monitor all alerts from HPE and report non-critical alerts in a quarterly report.
- Monitor release of new firmware and report to Client on quarterly basis (unless firmware is deemed critical).
- Offer assistance in deployment of firmware if needed.
- Assist in resolution of configuration if it doesn’t meet best practice per HPE documentation.
- Provide assistance in resolution of HPE support tickets as a Client advocate.
- Provide Quarterly environment reviews with Client.
Again, these are just examples of the ways we have helped our Clients address their challenges over the last 15 years. We have a team of technology professionals that are ready to assist you with all your infrastructure needs.
Have a great 2020. We look forward to hearing from you.
Ransomware
In May 2017, the National Health Service of England and Scotland was hit with the largest ransomware attack at that time. The attack affected an estimated 200,000 computers across 150 countries. The estimated economic loss ranges from hundreds of millions to four billion dollars. This attack, dubbed the WannaCry ransomware attack, catapulted network security to the top of many organization’s priority list. It brought to light the amount of damage that could be done by a malicious virus.
What is Ransomware?
Ransomware is a type of malicious software, or malware. It is designed to deny access to a computer system or its data until a ransom is paid. It is typically spread through phishing emails or by visiting an infected website. The virus works by encrypting all the data on the user’s hard drive. Then, it requests a payment, usually in the form of cryptocurrency, to be sent to the hackers. However, there is no guarantee the user will recover their files if they pay that ransom.
Ransomware can be devastating for users and organizations. Currently, we are seeing a lot of government agencies, education organizations, and healthcare organizations targeted by these attacks.
What precautions can you take?
In order to protect your user’s and organization’s data, there are a number of precautions you can take. Most of which are best practice even without the threat of ransomware.
First, keep all applications and operating systems up to date. Outdated apps and OS’s are the target of most attacks. This was the case in the WannaCry attack.
Second, train users to avoid phishing emails. These are emails designed to look legitimate at first glance but have links that redirect you to an infected site, or attachments that download the malware directly. Phishing emails and sites are also associated with social engineering attacks designed to steal credentials. It is always a good idea to train users to never click on links or open attachments in unsolicited emails.
Next, backup your data on a regular basis. Backing up your data is a good idea for a myriad of reasons. It can really save you in the case of a ransomware attack. Best practice would be to keep 3 copies of your backups, with one offline and another in a geologically separate location. These backups should also be regularly tested.
A great way to control what is installed on your organization’s computers is access control. Restricting privileges may not allow malware to be installed on a system without an administrator’s approval. This will limit the spread of the malware through a network.
Similarly, another useful tool for fighting malware is a spam filter on your emails. A strong spam filter will prevent most phishing emails from making it to users’ inboxes. It will authenticate inbound emails to prevent spoofing.
What to do when you’ve been infected by ransomware
The first thing anyone should do when infected by ransomware is to contact law enforcement immediately. You should report the infection to the FBI’s cyber task forces and internet crime complaint center.
Currently, the FBI does not recommend paying any ransom. While it could cost organizations large sums of money to be down for any length of time, there is no guarantee that paying the ransom will restore your data. There are numerous cases of this happening. Some victims who have paid the ransom have even been targeted again. Other victims have even been asked to pay more after the original ransom to get all their data back. Paying may inadvertently encourage this criminal business model. This makes it more prevalent in the future.
Once you have found out that you are infected, you should isolate any infected machines immediately. In addition, one should take any unaffected machines offline so they don’t get infected. Same goes for backups. They should be taken offline immediately to stop the ransomware from spreading into your backups.
From there, you should follow your organization’s incident response plan. Follow any instruction given to you by law enforcement.
There will never be any way that you can guarantee you won’t fall victim to one of these attacks. Malware is always evolving, just like security practices are. It will always be an arms race between hackers and security experts. Your best bet is to always follow best security practices, and to always have a plan to recover from any successful attacks.
Where to report Activity
FBI
Internet Crime Complaint Center
United States Secret Service
Contact Zunesis to have an assessment done on your current infrastructure. Ask us about helpful hints to help keep your data secure.
New Ransomware Focus
Ransomware has a new focus. Recent studies and surveys report that ransomware attacks have sky rocketed against government agencies, public healthcare providers and schools in the first nine months of 2019.
A report published by Emsisoft noted that at least 68 state, county and municipal entities have been affected by ransomware attacks this year. In addition, at least 62 ransomware attacks have involved School Districts. Healthcare providers reported 491 ransomware attacks.
This report also cited the following trends in 2019:
- Cybercriminals Target MSPs: Cybercriminals are increasingly targeting software used by MSPs and other third-party service providers. They simultaneously attack service providers and their customers.
- Ransoms Are Increasing: Cybercriminals want to maximize their profits, and as such, are increasing their ransom requests.
- Cyber Insurance Drives Ransom Payments: Organizations that leverage cyber insurance are more prone than others to pay cybercriminals’ ransoms.
- Cybercriminals Prioritize Email and Remote Desktop Protocol(RDP): Emails and RDP attachments represent the top choices for cybercriminals to launch ransomware attacks.
Credibility & Sophistication
Ironically, Ransomware cybercriminals consistently operate with integrity by following through on their commitment to decipher encrypted data once a ransom is paid. These criminals understand that for their crimes to continue to be profitable, they must follow through and make the data available to their victims after they have received payments.
Local Governments and School Districts find themselves in a tough situation. They often are forced to rapidly make arrangements for the ransom payment because their IT systems completely stop working.
To ensure that their damage is inflicted, cyber-criminals are making their attacks more sophisticated. Today’s ransomware attacks often include “time delayed fuses”. These attacks are designed to infect not only an organization’s primary data storage but also their replicated data sets and backups. When an organization attempts to recover from a ransomware attack using their backup data, they soon find that their backup data is also infected and encrypted. As countermeasures against ransomware become increasingly sophisticated, so do the attacks.
The Voice of America: Ransomware Focus
A report just published by IBM Security-Morning Consult showed the following:
- 79% of Americans are concerned about the threat of ransomware to cities across the US. While 68% are concerned about the threat of ransomware to their specific city. 75% are worried about threats to their personal data.
- 56% of Americans would disapprove of their local government using tax dollars to pay a ransomware hacker. When given an explicit choice, 63% of respondents would prefer to pay higher repair costs and not pay a ransom rather than using taxpayer dollars to pay for a ransom.
- More than 50% of Americans would not be willing to pay additional taxes to protect their city, county, or town from ransomware attacks. Among those who are unwilling to pay additional taxes for cyber-security, respondents are split 50/50 on whether they would support cutting funding from other local priorities for cyber-security.
- Nearly half (49%) of the respondents view the Federal Government as having the greatest responsibility to protect cities from ransomware attacks. 22% seeing it as a state-level responsibility. 28% view it as the responsibility of the local Government.
These statistics explain the complexity that our civic leaders face when addressing the threat of ransomware. Public policy will evolve over time and likely make substantial progress as knowledge is gained. Unfortunately, the threat to our local governments and public institutions is very real today.
A Step in the Right Direction
Organizations of all sizes can take a meaningful first step to reduce their risk to ransomware. They need to assess their data backup and data protection policies. Having the right processes and technology in place will substantially lessen the risk of ransomware.
Zunesis specializes in helping organizations evaluate and assess their backup and data protection policies. This includes retention policies and “air gaps”. This is one step in providing greater overall security for Government agencies, schools and healthcare providers. Often considered to be the important first step.
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.
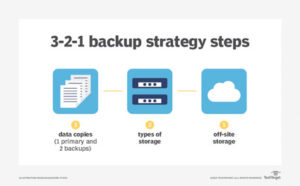
The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
Veeam Backup and Replication
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.

The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst

