Securing or Hardening
Securing or Hardening aims to protect and secure your IT infrastructure against cyberattacks by reducing the attack surface. The attack surface is all the different points where an attacker can to attempt to gain access or damage the equipment. This blog is focused on securing Servers and storage.
The goal of server hardening is to remove all unnecessary components and access in order to maximize security. This is easiest when a server performs a single function. For example, a web server needs to be visible to the internet whereas a database server needs to be more protected. It will often be visible only to the web servers or application servers and not directly connected to the internet.
If a single server is providing multiple functions, there may be a conflict of security requirements. It is best practice not to mix application functions on the same server.
Implementing Hardening Policies
The information below provides a starting point for implementing hardening policies. Some of these only apply to the servers, but others apply to all devices on the network (Servers, Storage, Networking).
All Devices:
- Change default credentials and remove (or disable) default accounts – before connecting the server to the network.
- Disable guest accounts, setup accounts and vendor accounts (Vendor accounts can be enabled when necessary).
- Install security patches and firmware updates on a scheduled basis. My recommendation is to review devices firmware, virtualization layer software, and operating systems a minimum of every 6 months. If possible, review them every quarter.
- If possible, sign up for service update notifications from all vendors. You will be notified of critical updates. Depending on the update, Critical Security updates may require immediate implementation.
- Develop a patch/firmware management process that includes what gets updated, when it gets updated, outage window required, can it be automated, process for patching/firmware upgrade, etc. Some devices may be updated quarterly, others monthly.
- Accurate time keeping is essential for some security protocols to work effectively. Configure NTP servers to ensure all servers, storage and network devices share the same timestamp. It is much harder to investigate security or operational issues if the logs on each device are not synchronized.
- Ensure all devices are located in a physically secured location and restricted to approved staff only. Review and disable access for anyone that has left or changed roles.
- Review user and administrator level access to all devices. Ensure all default userids and passwords have been changed. Remove all users that are not on the approved list. If possible, use roles-based access using Active Directory or the equivalent.
- For connection to all devices, use Secure Shell Protocol (or SSH) when possible. This enables you to make a secure connection to your network services over an unsecured network. Avoid using FTP, Telnet and rsh commands. Use a secured protocol.
Servers:
- Turn off services that are not required – this includes scripts, drivers, features, subsystems, file systems, and unnecessary web services. Remove all unnecessary software.
- On Windows systems only activate the Roles and Features required for that host to function correctly.
- On Linux systems remove packages that are not required and disable daemons that are not required.
- Remote Access (Windows RDP) is one of the most attacked subsystems on the internet – ideally only make it available within a VPN and not published directly to the internet. For Linux systems, remote access is usually using SSH. Configure SSH to whitelist permitted IP addresses that can connect and disable remote login for root.
- Configure operating system and application logging so that logs are captured and preserved. Consider an SIEM Solution to centralize and manage the event logs from across your network.
- Review Administrator Access to host operating systems. Administrator accounts should only be used when required by approved personnel.
- Set password settings to require “Strong and Unique” passwords. Force password changes periodically according to internal security practices (usually 30 to 90 days).
- Configure account lockout policies. Lockout user accounts after failed attempts.
- Consider using Multi-Factor Authentication (MFA) if feasible to improve the level of security.
- Review backup policies to ensure all servers are being backed up correctly according to company retention policies. Periodically test the backup to be sure recovery is possible.
- Review monitoring requirements and be aware of any activity on each system.
- Set up custom admin accounts. They can be an Active Directory (AD) account or a local account in the administrators group.
- Limit security context on accounts used for running services. By default, these are Network Service, Local System, or Local Service accounts. For sensitive application and user services, set up accounts for each service and limit privileges to the minimum required for each service. This limits the ability for privilege escalation and lateral movement.
- For Linux systems, use Secure Shell Protocol (or SSH) when possible. This enables you to make a secure connection to your network services over an unsecured network. Use a secured protocol.
- Enable UEFI Secure Boot will further ensure only trusted binaries are loaded during boot.
- If not in use, disable the IPv6 protocol to decrease the attack surface.
- Keep partitions separated can help decrease the radius of any attack. Separate the boot partition from the user data and application data will help protect your data.
Contact Zunesis today if you would like more information on hardening your infrastructure.
AMD EPYC Processors
I have been getting a lot of questions recently about AMD and if it should be used in the data center. The short answer is YES. Since AMD announced the EPYC processors, they have been gaining market share in the data center. Hewlett Packard Enterprise recently announced the industry’s broadest portfolio of AMD EPYC™ processor-based solutions to power everything from the edge to exascale supercomputers. They have been breaking performance records running AMD on the HPE Cray Supercomputers.
AMD EPYC Series Processors help propel your modern data center workloads with leadership performance and advanced security features. AMD has announced the 3rd generation of the EPYC processor. It sets the performance bar to new heights. Built on the Zen 3 core and the AMD Infinity Architecture, the AMD EPYC 7003 series provides the best performance, highest I/O, and integrated security. The video below shows the announcement for the new AMD EPYC generation 3 processors.
Hewett Packard Enterprise AMD EPYC Processor Portfolio
The current Hewlett Packard Enterprise product portfolio is built on the AMD EPYC generation 2 processor which features the 7002 series processors. The 7002 is based on Zen 2 core, which delivers optimized performance-per-watt, large L3 cache for low latency access to data. These processors support up to 64 cores per socket, 128 threads, 4TB of DDR4 memory capacity across 8 memory channels, and 128 lanes of PCIe® 4.0 connectivity to reduce bottlenecks.
Based on the AMD Infinity architecture, the 2nd Gen AMD EPYC Processors are the first server processors featuring a 7nm hybrid multi-die design and PCIe Gen4 I/O. The AMD EPYC Family continues to offer the most I/O and memory bandwidth in its class.
Security Features
AMD EPYC processors boast a set of advanced security features, called AMD Infinity Guard. This includes the AMD secure processor, Secure Memory Encryption (SME), and Secure Encrypted Virtualization (SEV). These features help minimize potential attack surfaces as software is booted, executed, and processes your critical data.
With Secure Encrypted Virtualization (SEV), AMD EPYC processors help safeguard privacy and integrity by encrypting each virtual machine. This aids in protecting your data’s confidentiality even if a malicious virtual machine finds a way into your virtual machine’s memory or a compromised hypervisor reaches into a guest virtual machine.
The HPE Server portfolio ranges from the low-end DL325 Gen10 Plus 1U server up to the HPE Cray EX supercomputer. There are 1 socket and 2 socket general-purpose server options, scalable building block options, high-performance computing options, and options built for AI and Deep Learning. Find out more about the HPE server product line with AMD EPYC processors here.
New Products
HPE will be announcing new products based on AMD EPYC Gen3 processors in mid-April 2021. More information will be available as it gets closer to the announcement date. According to the HPE Press release dated March 15, 2021, HPE has secured 19 world records in key areas for optimizing workload experiences. This includes achieving leadership positions in virtualization, energy efficiency, database analytic workloads, and Java applications. To date, HPE servers and systems using 2nd and 3rd Gen AMD EPYC processors combined to hold a total of 32 world records.
After the announcement, the full portfolio of HPE servers and systems supporting the new 3rd Gen AMD EPYC processor will include the following:
- HPE ProLiant DL325 Gen10 Plus v2 server
- HPE ProLiant DL385 Gen10 Plus v2 server
- HPE ProLiant DL345 Gen10 Plus server
- HPE ProLiant DL365 Gen10 Plus server
- HPE Apollo 2000 Gen10 Plus system with the HPE ProLiant XL225n Gen10 Plus server
- HPE Apollo 6500 Gen10 Plus system with the HPE ProLiant XL675d Gen10 Plus server
- HPE Apollo 6500 Gen10 Plus system with the HPE ProLiant XL645d Gen10 Plus server
- HPE Cray EX supercomputer EX425
- HPE Cray EX supercomputer EX235n
Availability
All new HPE Apollo systems with the 3rd Gen AMD EPYC processor will be available worldwide on April 6. All new HPE ProLiant servers with the 3rd Gen AMD EPYC processor will be available worldwide on April 19. Contact Zunesis, if you would like to learn more about these processors.
Blogs typically are not hard to write. The trick is to find something relevant for the readers and something that is passionate to you. Just take a look at some of the blogs my teammates here at Zunesis have written.
The year 2020 and how the Covid-19 pandemic are affecting our world, a topic which is dominating every news cycle, no matter the industry:
2021 – It’s Only a Date Change – Peter Knoblock
Going Back to Basics – Tom Savage
2021 Strikes Back – Caleb Clark
CARES Act Funding to Assist with Distance Learning – Sara Wessells
Another Zunesis blogger, a fitness enthusiast, compared IT Health Checks and Assessments to doing Yoga.
Yoga + IT Health = Nirvana – Stacy Lara
These blogs were easy for the authors to write because they are passionate about their topics, our world, the industry we serve, and the customers we serve.
AD Health Checks
Over four years ago in May 2016, I wrote a blog titled: Why You Need to Check the Health of Your Active Directory.
First, I cannot believe that was four years ago, and second, it is still very relevant today. In fact, I would say more relevant, enough to expand the AD Health Checks to the entire server infrastructure.
In that blog, I compared Active Directory to the central nervous system of the human body. How, just as you see a doctor for regular checkups, AD also needs these types of checkups. If AD is the central nervous system, then the servers which support the infrastructure are the major organs. Just like the AD Health Check, the servers must be checked periodically.
Screen for Diseases
1. Verify backup solution: Be sure your backups are working. Daily reports need to be reviewed for completion and to identify issues. Perform test recoveries to be sure the backup solution is working at 100%. Don’t have a backup or unsure about your current solution? Zunesis has a blog for that:
Are You Sure You Can Recover Your Backups? – James Hughes
Protecting your Data with Veeam Backup – Adam Gosselin
2. Monitor Disk Usage: Servers generate a lot of data which can add up over time. Make sure you are getting rid of old log files. If they are needed, then archive them to permanent storage. Remove old applications that can leave significant security holes. Review the removal as some uninstallers can leave old files. A smaller data footprint means faster recovery.
3. Monitor system alarms for hardware: Check for any type of hardware warnings, errors, or failures. Warnings tend to lead to errors, which can lead to failures.
4. Monitor server resource utilization: Monitor disk, CPU, RAM, network utilization, and log files. Check for OS or Application issues.
5. Updates, updates, updates: Check for Operating System updates. Check for Application updates. Check for Hardware (Firmware) updates. Hackers are very quick and can develop variants within hours of an issue being disclosed. Rapid response is key.
6. Review privileged user accounts: Validate for accuracy and check account permissions to make sure they are appropriate for each user.
7. Review Password Security: User passwords should be changed every 45-60 days. Service Account passwords should be changed annually.
Future Health Precautions
Assess Risk of Future Medical Problems
- Review Microsoft Server Roadmap for planning migrations.
Encourage a Healthy Lifestyle
- Review and discuss current administrative practices surrounding the Servers.
- Review and discuss and recommend monitoring strategies around the Servers.
- Review and discuss and recommend auditing strategies of the Servers.
Maintain a Relationship with Doctors in Case of an Illness
- Good to have a relationship with an infrastructure provider, like Zunesis, when issues arise and advanced assistance is needed.
- Good to have an independent third-party, like Zunesis, doing the health checks. You aren’t allowed to prescribe your own medication, are you?
These should be included in a larger Infrastructure Monitoring Program with documented Policies and Procedures. The checks and the levels may vary depending on the organization.
Just like the human body, proper monitoring and care can assist in keeping your Servers healthy. Your Servers can only benefit from these periodic “doctor” visits. The Zunesis Infrastructure Health Check will assess your current Server Infrastructure and deliver a report providing a third-party review, validation, and recommendations for improvement. Contact Zunesis today to schedule a health check for your organization.
REST for the Weary – RESTful APIs
As the expression goes, “no rest for the weary.” A lot of us in the IT industry can relate to that statement. We are often needing to work long hours with heavy workloads.
Why is it then, that at least in my observation, many systems and network engineers still have not jumped on the automation train? We’re so busy being busy, that we don’t take the time to save time. Some of us still think RESTful APIs are something that only “devs” use. Luckily for our sanity, many of us are picking up this much needed skill.
If you haven’t played with RESTful APIs yet, and are in IT operations, I highly encourage you to check out RESTful APIs and get some lab time. By sharing some personal experience, I’d like to argue that there really can be “REST for the weary.”(Pun intended)
A slightly better way
I remember before RESTful APIs were something that more vendors were supporting. I had to do write Expect scripts in Linux to do my automation. Really, this was just screen scraping terminal output and brute forcing automation. It was messy at best, especially trying to automate devices that weren’t made for automation.
This wasn’t a whole lot of fun, but it was worth the pain involved since it still saved mountains of time. There was quite a bit of pain with some vendors. They needed weird keystroke combinations before it would allow CLI access even after SSH’ing in. Implementing “CTRL+Y” through an SSH session via script was way more of a headache than you’d think it should be.
Complaining aside, spending time writing Expect scripts was certainly MUCH easier than doing things manually. As an example, in a large environment I previously worked in, my co-workers spent time manually SSH’ing to literally hundreds of switch stacks. They had to run some commands and capture output to save.
I was asked on a regular basis by management to get MAC address/switchport/dot1x info, and other data which could be queried for historical data in a database. This was in preparation for a forklift upgrade on the network. The use case was to get a history of devices, interface information, and all other relevant historical data. Pulling MACs from the cores via uplinks wouldn’t give necessary detail.
This wasn’t an option. We had to go to the switches as a source of truth. The idea was also to compare to data from other sources (the IP-PBX system was one example) in preparation for the upgrade. They wanted to make sure network cut-overs were un-noticed by end users, aside from the downtime to swap equipment of course. I spent quite a bit of time writing and tuning Expect scripts, but still much less than doing things the old fashioned way.
The actual better way
Fast forward to my next job managing literally thousands of server nodes in a high uptime environment. I started getting asked to do things like update BIOS settings ON EVERY SERVER. To make things worse, as software engineering changed their code, they’d ask me to change BIOS settings multiple times. There was no way I was going to iLO into every one of those servers, reboot, wait, press F9 to access system utilities, select BIOS/Platform configuration(RBSU)… etc. Thankfully, I didn’t have to draw a line in the sand and explain that I was unwilling to do this.
After some research, I learned that HPE makes a RESTful API available on their Gen9 and Gen10 servers. Lucky for me, we were using Gen9 servers at the time.
Managing BIOS settings isn’t the only thing you can do by the way. You could probably integrate this into your monitoring system if it allows, for non responsive devices as an example. We’ve all seen servers where the lights are on but nobody is home. They seem dead, but respond to pings…intermittently and with high latency. You could use your monitoring system to poll services, and metrics like CPU and RAM utilization. Then, reboot the server via iLO RESTful API, if it is really locked up. No more waiting for a human to notice alerts, escalate if needed, then reboot the server manually.
One Interface for Integrated Control
HPE Integrated Lights Out (iLO) server management provides intelligent remote control automation through scripting or an API. Gain even more capabilities that go beyond scripting by leveraging one API to manage your complete lifecycle of HPE Gen9 and Gen10 servers—iLO RESTful API.
A single API interface integrates server management components and full compute power. Use it with HPE iLO 4 and iLO 5 to perform remote server provisioning, configuration, inventory and monitoring to industry standards through Redfish API conformance.
This was a game changer. I was able to prepare some standard JSON files with standardized BIOS settings. Then, write a script utilizing HPE’s RESTful API, and push settings described in the JSON file to every server (or subset of servers for testing) with ease.
Some settings still required a reboot to take effect. This was easily handled by scheduled reboots during a maintenance window. I also didn’t need to patch together a solution to script iLO changes with the software equivalent of duct tape and bubble gum, but instead utilized a RESTful API. Something that would have taken FOREVER, was accomplished with ease using something very well documented by HPE.
Give it a try!
Ready to give RESTful APIs a chance on your HPE servers and Aruba networking? Check out these resources:
Not using RESTful API capable servers or networking? The seasoned professionals at Zunesis can assess your environment, and recommend an appropriate refresh path utilizing the latest Aruba networking equipment and Gen10 HPE servers.
Windows 7 OS Enters Final Year of Free Support
Windows 7’s five years of extended support will expire on January 14, 2020. After this date, security fixes will no longer be freely available for the operating system that’s still widely used. If you still use Windows 7, it may be time to consider an upgrade.
“Changes and upgrades in technology are inevitable,” said Brad Anderson, corporate vice president for Microsoft 365, in a blog. “And there’s never been a better time to start putting in motion the things you need to do to shift your organization to a modern desktop with Microsoft 365.” Microsoft will continue to provide security updates for Windows 7 to business customers that pay for support, according to ZDNet, but not individual users.
Windows 10
Windows 7 was released in 2009 and is still one of the most widely used desktop operating systems. Windows 10 finally overtook Windows 7 in the desktop market at the end of last year, according to ZDNet. Data analysis reports for December 2018 showed that 39.2 percent of the machines they collect data from used Windows 10, while 36.9 percent used Windows 7, according to ZDNet.
What Does End of Support Mean?
The end of free support does not mean the end of support entirely. Microsoft has long offered paid support options for its operating systems beyond their normal lifetime, and Windows 7 is no different. What is different is the way that paid support will be offered. For previous versions of Windows, companies had to enter into a support contract of some kind to continue to receive patches. For Windows 7, however, the extra patches will simply be an optional extra that can be added to an existing volume license subscription. No separate support contract will be needed on a per-device basis. These Extended Security Updates (ESU) will be available for three years after the 2020 cut-off, with prices escalating each year.
Alternative Option
According to Microsoft Technologist Peter Bright, as an alternative, Microsoft is offering all three years of ESUs to customers of the new Windows Virtual Desktop (WVD) service at no extra cost. This service offers cloud-hosted virtual machines running Windows 7 plus whatever applications are needed, and those virtual machines will continue to be patched into 2023. WVD uses existing Windows Enterprise E3 licenses, and it runs on the full range of Azure virtual machines, with no additional costs incurred. This includes, for example, GPU-equipped VMs, meaning that WVD should be usable for a wide range of workloads.
Office 365 will continue to be supported on Windows 7, but only with the ESUs applied. Similar policies exist for Windows Server 2008 and Windows Server 2008 R2. These also drop out of free support in one year. For on-premises deployments, customers will be able to buy the Extended Security Updates, but workloads in Azure will receive all three years of fixes for free.
Here are a few reasons why Windows 10 is superior to Windows 7:
- Multitasking – It is much easier to juggle multiple open windows when you’re working. Features include offering both half-monitor and quarter-monitor sizes when you drag a window to one part of the Desktop. Other open windows are able to fill any open space automatically. One can view a much clearer thumbnail overview of your open windows and supports multiple Desktops. This makes working with full-screen windows much easier when you don’t have multiple monitors
- Always up to date – It’s no longer possible to forget to run Windows Update. You will be less likely to miss a critical operating system patch that fixes a serious security problem. By forcing all users to stay up to date, everyone’s online safety is improved. It reduces the risk of a PC being compromised by a hacker and becoming part of a botnet that could be used to attack your PC.
- Security – The safety of your PC is improved. With alternatives to a simple password, such as using a familiar picture, it makes it much harder for anyone to sign into your PC without your permission.The new PIN system also means you can protect your Microsoft account with a long, strong and very secure password, but still use a simple PIN code to sign into your PC — and it only works on your PC.
- New Windows Features – Digital assistant Cortana is gradually improving with every update, while the Action Centre is a neat and tidy place to keep all your notifications.
- Faster – Performance tests have shown that this version is faster across the board than earlier versions of Windows. It boots, goes to sleep and wakes from sleep marginally faster than it would on a PC of the same specification. This means less waiting around when you want to do something. Application performance is more of a mixed bag. Tests show it to be faster than Windows 7 with some apps and slower with others. Bear in mind that Microsoft will update Windows 10 regularly. Windows 7 is now essentially frozen in its current state after ‘mainstream’ support ended in January 2015.
Contact Zunesis if your organization is interested in moving from Windows 7 to Windows 10. We can provide support and expertise during the transition.
Windows 7 OS Enters Final Year of Free Support
Windows 7’s five years of extended support will expire on January 14, 2020. After this date, security fixes will no longer be freely available for the operating system that’s still widely used. If you still use Windows 7, it may be time to consider an upgrade.
“Changes and upgrades in technology are inevitable,” said Brad Anderson, corporate vice president for Microsoft 365, in a blog. “And there’s never been a better time to start putting in motion the things you need to do to shift your organization to a modern desktop with Microsoft 365.” Microsoft will continue to provide security updates for Windows 7 to business customers that pay for support, according to ZDNet, but not individual users.
Windows 10
Windows 7 was released in 2009 and is still one of the most widely used desktop operating systems. Windows 10 finally overtook Windows 7 in the desktop market at the end of last year, according to ZDNet. Data analysis reports for December 2018 showed that 39.2 percent of the machines they collect data from used Windows 10, while 36.9 percent used Windows 7, according to ZDNet.
What Does End of Support Mean?
The end of free support does not mean the end of support entirely. Microsoft has long offered paid support options for its operating systems beyond their normal lifetime, and Windows 7 is no different. What is different is the way that paid support will be offered. For previous versions of Windows, companies had to enter into a support contract of some kind to continue to receive patches. For Windows 7, however, the extra patches will simply be an optional extra that can be added to an existing volume license subscription. No separate support contract will be needed on a per-device basis. These Extended Security Updates (ESU) will be available for three years after the 2020 cut-off, with prices escalating each year.
Alternative Option
According to Microsoft Technologist Peter Bright, as an alternative, Microsoft is offering all three years of ESUs to customers of the new Windows Virtual Desktop (WVD) service at no extra cost. This service offers cloud-hosted virtual machines running Windows 7 plus whatever applications are needed, and those virtual machines will continue to be patched into 2023. WVD uses existing Windows Enterprise E3 licenses, and it runs on the full range of Azure virtual machines, with no additional costs incurred. This includes, for example, GPU-equipped VMs, meaning that WVD should be usable for a wide range of workloads.
Office 365 will continue to be supported on Windows 7, but only with the ESUs applied. Similar policies exist for Windows Server 2008 and Windows Server 2008 R2. These also drop out of free support in one year. For on-premises deployments, customers will be able to buy the Extended Security Updates, but workloads in Azure will receive all three years of fixes for free.
Here are a few reasons why Windows 10 is superior to Windows 7:
- Multitasking – It is much easier to juggle multiple open windows when you’re working. Features include offering both half-monitor and quarter-monitor sizes when you drag a window to one part of the Desktop. Other open windows are able to fill any open space automatically. One can view a much clearer thumbnail overview of your open windows and supports multiple Desktops. This makes working with full-screen windows much easier when you don’t have multiple monitors
- Always up to date – It’s no longer possible to forget to run Windows Update. You will be less likely to miss a critical operating system patch that fixes a serious security problem. By forcing all users to stay up to date, everyone’s online safety is improved. It reduces the risk of a PC being compromised by a hacker and becoming part of a botnet that could be used to attack your PC.
- Security – The safety of your PC is improved. With alternatives to a simple password, such as using a familiar picture, it makes it much harder for anyone to sign into your PC without your permission.The new PIN system also means you can protect your Microsoft account with a long, strong and very secure password, but still use a simple PIN code to sign into your PC — and it only works on your PC.
- New Windows Features – Digital assistant Cortana is gradually improving with every update, while the Action Centre is a neat and tidy place to keep all your notifications.
- Faster – Performance tests have shown that this version is faster across the board than earlier versions of Windows. It boots, goes to sleep and wakes from sleep marginally faster than it would on a PC of the same specification. This means less waiting around when you want to do something. Application performance is more of a mixed bag. Tests show it to be faster than Windows 7 with some apps and slower with others. Bear in mind that Microsoft will update Windows 10 regularly. Windows 7 is now essentially frozen in its current state after ‘mainstream’ support ended in January 2015.
Contact Zunesis if your organization is interested in moving from Windows 7 to Windows 10. We can provide support and expertise during the transition.
In Search of the Holy Grail (and avoiding the killer rabbit)
In this post, I’m going to be writing about a solution from HPE to help improve the management of IT Infrastructure. First, I want to say that I have come to understand the term “IT Infrastructure” can be used very broadly, depending on the perspective of the Speaker or Writer and their audience. So, before I get started, let me define what the term means for me.
When I talk about IT Infrastructure components, I am referring to the hardware and software that provide the foundation for Applications supporting the line of business. The Business Applications will include email, document management, ERP and CRM Systems, etc. The foundational components that support these applications include Compute, Storage, and Networking hardware as well as Operating Systems and Hypervisors. In my mind, these foundational pieces are the IT Infrastructure.
Managing Can be a Challenge
Management of IT Infrastructure has long been a challenge for Systems Administrators. Once we moved past the mainframe dominated environment, to a distributed architecture, the number of devices and operating environments (operating systems and hypervisors) grew very quickly. Each component of an IT Infrastructure requires configuration, management, and monitoring (for alerts, performance, capacity, etc.) Of course, each device and operating environment comes with their own management and monitoring tools, but, because of the disparate toolset, the burden of correlating the information from each of these sources falls on the shoulders of Systems Administrators. This task of monitoring and correlating data from our IT Infrastructure can be incredibly time consuming. And, because our days are often filled with the unexpected, it is difficult to be consistent in our execution of the monitoring/correlation tasks.
To help ease this burden, the industry has seen the introduction of many applications over the years, designed to aggregate alerts and performance metrics. These tools certainly help, but they can often fall short.
What do we do with the information they are presenting to us?
How do we make sense of the data?
Can these tools help us understand trends in utilization, predict resource short-falls, proactively warn of component failures?
And, can they provide any correlation in the context of analytics data collected from thousands of similar environments from around the world?
That would be the Holy Grail of IT Management. Wouldn’t it?

Okay, a mid-post pause. My reference to the Holy Grail (and the killer rabbit) is from the movie, Monty Python and the Holy Grail. I only used it here because some of my Zunesis Colleagues have written posts using various movie references and I felt the need to respond with my own. I’m older than many of my colleagues so my reference may be a little more dated. However, I think the movie is iconic and will still be familiar to most.
Okay, now back to the discussion of IT Management and the challenges we face. To borrow a phrase from Monty Python, “…and now, for something completely different…”.
HPE InfoSight
In April of 2017, HPE completed the acquisition of Nimble Storage. This acquisition introduced a great storage solution into the HPE Storage family, but, one of the biggest drivers for this acquisition was InfoSight Predictive Analytics. At the time, InfoSight collected data from thousands of sensors across all deployed Nimble arrays globally. This data was fed into an analytics engine allowing global visibility and learning to provide predictive problem resolution back to each Nimble user. The analytics allowed many problems to be resolved, non-disruptively, sometimes before the end-user knew it was a problem.
So, in addition to providing localized alerting, phone-home support, performance data, resource trending, System Administrators now had a tool that could act on their behalf and provide correlations that wouldn’t be possible without the global context.
At the time of the acquisition, HPE committed to leveraging InfoSight for other HPE solutions over time. They have been honoring that commitment ever since. Very quickly they included InfoSight support for 3PAR StorServ, StoreOnce, and RMC. These were in addition to the existing support for Nimble Arrays and VMware.
As of January 7th of 2019, HPE officially included support for Gen 10, 9, and 8 ProLiant Servers, Synergy, and the Apollo Server families. This recent announcement means that many key components of the IT Infrastructure are now part of the InfoSight Predictive Analytics environment.
For HPE storage solutions, HPE InfoSight Predictive Analytics answers questions like:
- How has my data usage trended?
- When am I going to run out of capacity?
- What if I ran these apps… on the same array?
For the newly announced HPE Server environment HPE will provide:
- Predictive analytics to predict and prevent problems
- data analytics for server security
- predictive data analytics for parts failure
- Global learning that provides wellness and performance dashboards for your global inventory of servers
- global inventory of servers
- A recommendation engine to eliminate performance bottlenecks on servers
For VMware environments, InfoSight Cross-stack Analytics identifies:
- Noisy Neighbor
- Inactive VMs
- Latency Attribution – identify root cause across host, storage, or SAN
- Top Performing VMs – Visibility into Top 10 VMs by IOPS and Latency
Benefits of InfoSight
Based on an ESG Report titled, “Assessing the Financial Impact of HPE InfoSight Predictive Analytics”, published in September 2017, InfoSight provided the following benefits based on a survey of nearly 500 users:
- 79% lower IT operational expenses.
- 73% fewer trouble tickets in the environment.
- 85% less time spent resolving storage-related trouble tickets.
- 69% faster time to resolution for events that necessitate level 3 support.
- The ability to manage and troubleshoot the entire infrastructure environment from a single, intelligent platform.
HPE InfoSight is an application of AI that is here today and will continue to grow in the IT Infrastructure components it supports as well as the benefits it provides. If you have an HPE environment today, you’ll want to find out if HPE InfoSight can be leveraged to help you better manage your IT Infrastructure.
Introducing ProLiant Gen10
The industry-leading success of HPE ProLiant stems in part from their ongoing commitment to providing a complete industry-standard server infrastructure that delivers innovation, quality, security and proven performance.
HPE ProLiant Gen10 is available in these families (outside of BladeSystem, Synergy, and Apollo platforms…but that’s a whole other discussion!):
- HPE ProLiant MicroServer

- HPE ProLiant Rack family – DL360, DL380, DL560 and DL580 servers – we will dive deeper into this family below as these are by far the most popular server sold.
- HPE ProLiant Tower family – ML110 and ML350 servers
HPE ProLiant Gen10 Rack Servers
The new HPE Gen10 rack servers are “The World’s Most Secure Industry Standard Servers”. This bold claim is founded on a unique silicon root of trust technology along with a myriad of other differentiating security technologies that only HPE offers.
The DL family of servers are the most flexible, reliable, and performance-optimized ProLiant rack servers. As HPE continues to provide industry-leading compute innovations, the ProLiant Gen10 rack portfolio, with flexible choices and versatile design, along with improved energy efficiencies, ultimately lowers TCO.
Integrated with a simplified, but comprehensive management suite and industry-leading support, the ProLiant Gen10 rack portfolio delivers a more reliable, fast, and secure infrastructure solution. It also helps increase IT staff productivity, and accelerates service delivery.
In addition, the rack portfolio is performance-optimized for multi-application workloads to significantly increase the speed of IT operations and enable IT to respond to business needs of any size, faster.
The HPE ProLiant Gen10 rack portfolio provides:
- Up to 27x faster checkpoint operations enabling significantly faster business operations and 20x reduction in database restart time preserving maximum uptime.
- Up to a 70 percent performance gain and 27 percent increase in cores
- Firmware anchored directly into the Silicon (Root of Trust), providing protection through the entire supply chain.
- 66 percent greater memory bandwidth increasing application performance for memory-intensive applications
Differentiating Innovations
Software-defined compute and converged infrastructure to run diverse workloads and applications across traditional and multi-cloud environments:
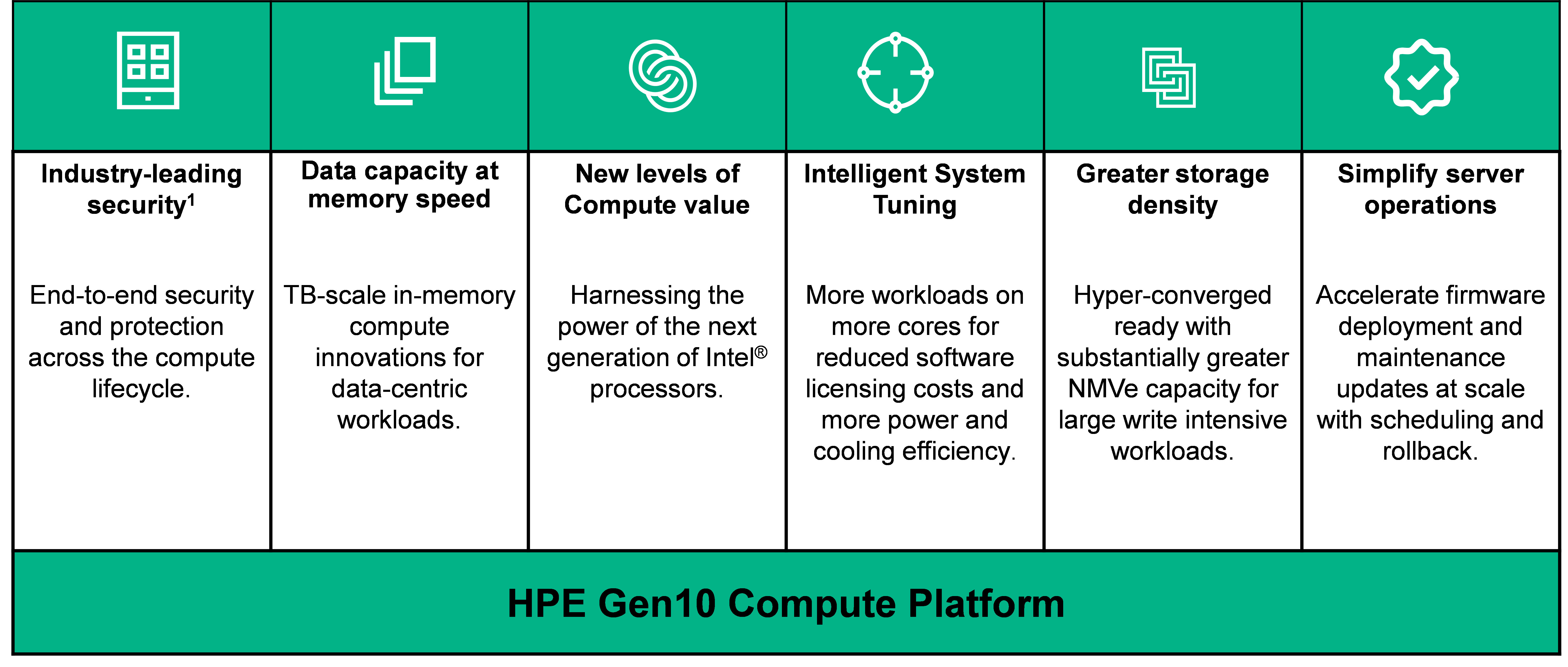
The bold claim that the ProLiant Gen 10 platform “The World’s Most Secure Industry Standard Servers” is founded on a unique silicon root of trust technology along with several other differentiating security technologies that HPE offers:
- Silicon root of trust—creates a digital fingerprint in the silicon and ensures the server will never boot with compromised firmware.
- Firmware threat detection—know on a daily basis whether firmware has been compromised. In the event of a breach, you can automatically recover to a known trusted state and quickly get the sever operational again.
- Server data security—implementing the highest level of security algorithms, known as CNSA-suite, you can keep your most confidential information within your server protected.
- Runtime Firmware Validation—Millions of lines of firmware code run before server operating system boots and with Runtime Firmware Validation, enabled by iLO Advanced Premium Security Edition, the server firmware is checked every 24 hours verifying validity and credibility of essential system firmware.
- Intel® Xeon® Processor Scalable Family—Next generation industry standard CPUs with faster processing, higher speed memory access, enhanced software-defined management and security.
- HPE Scalable Persistent Memory Non-Volatile DIMM (NVDIMM)—In-memory compute performance, accelerating applications for fast caching and storage, reduce transaction costs for latency-sensitive workloads, and deploy bigger, more affordable datasets to gain new insights from large memory pools.
- Intelligent System Tuning—Automate application performance tuning with core boosting and jitter smoothing technology. This new set of server tuning technologies enable you to dynamically configure server resources to match specific workloads for a more intelligent server environment.
- Hyper-Converged Ready Storage Density—Substantially greater NVMe capacity for large write intensive workloads needing advanced caching/tiering.
As an HPE Platinum Data Center partner, Zunesis can work with your organization to analyze your current environment. Whether you currently have ProLiant or other OEM x86 servers, we can develop a plan for migration to the ProLiant Gen 10 platform.
Zunesis can also provide installation, workload migration, and knowledge transfer services to make your migration as seamless as possible. We will provide a complete solution that is “Ready to Go”!
If your servers are more than 3 years old (for example, ProLiant Gen 8 or older), your organization will benefit from working with Zunesis and HPE on a Customer Connect discussion on a potential migration to Gen 10 architecture.
For details about HPE ProLiant Gen 10 servers, Zunesis Customer Connect Services, or more…contact your Zunesis Account Manager.

