Ransomware
Ransomware is a form of Malware that, once activated, can deny access to files on smartphones, personal computers, and servers. In some forms, a Ransomware attack will go beyond denial of service; and the Cyber Criminals will threaten to publish your data. As the name suggests, Ransomware offers to unlock your files if you pay a ransom. While modern day Ransomware attacks can be traced back to 2005, the history of Ransomware goes back as far as 1989. The pace of these attacks doesn’t appear to be slowing down. In 2016, many sources had payouts approaching $1 billion by the end of the year.
 As you might imagine, having been around for such a long time, Cyber Criminals have developed several ways to launch Ransomware attacks. Within the data center, our first goal is to keep these attacks out of our systems and away from our production data. IT Professionals protect their production environments by using firewalls, anti-virus software, proper authentication practices, and end-user education, among other measures.
As you might imagine, having been around for such a long time, Cyber Criminals have developed several ways to launch Ransomware attacks. Within the data center, our first goal is to keep these attacks out of our systems and away from our production data. IT Professionals protect their production environments by using firewalls, anti-virus software, proper authentication practices, and end-user education, among other measures.
Despite these efforts, there is always the possibility that an attack is successful and systems are compromised. In the event our corporate files do become impacted by a Ransomware event, we must be able to rely on our data backups to restore systems and not be forced to pay a ransom. However, this begs an important question:
How can we be sure that our backups are protected?
This is a question that is being asked more frequently by our clients.
First, we need to acknowledge that backups are not free from the risk of being attacked by Ransomware. However, there are steps that can be taken to reduce the risk of exposure, even if the Malware has found its way into the Production infrastructure. These steps fall generally into three categories: Security, Replication, and Isolation.
Security
- Provide a dedicated host for the backup application.
- Disable network interfaces not in use on the hosts involved in performing backups.
- Restrict the number of user accounts with access to the backup application and the host onto which it is installed.
- Disable access to communications ports and protocols not needed for the backup operation (i.e., HTTP, FTP, Telnet, etc.).
- Disable accounts not used for operation of the backup process.
- Disable services not used for operation of the backup process.
- Utilize best practices for user credentials (password complexity, aging, etc.).
- Keep Security Patches up to date on the host and the backup application itself.
Replication
 Maintain at least three (3) copies of the backup files on at least two (2) different types of media and keep at least one (1) of those copies offsite. (3-2-1 Rule)
Maintain at least three (3) copies of the backup files on at least two (2) different types of media and keep at least one (1) of those copies offsite. (3-2-1 Rule)- Consider keeping a copy of your backup on tape or on spinning disk that is not connected to the network unless backups are running. The point here is to maintain an offline copy.
- If replicating between backup appliances, consider building a delay into replication to keep from immediately replicating files infected with the Ransomware. This tactic may allow you time to discover the proliferation of an attack and keep it from spreading to your replication target.
- Utilize hardware based snapshots on Production storage arrays and backup appliances (these are not usually presented to a file system and are therefore not subject to attack).
- Maintain multiple restore points using snapshots and the backup software.
Isolation
- Maintain separate hosts for the backup infrastructure.
- Utilize offline backup media (tape or disconnected disk targets).
- Utilize hardware based snapshots.
- Utilize Cloud connected backup targets.
The steps listed above are intended to provide guidelines for protecting your backup data from Ransomware. Execution of these steps is dependent on your own infrastructure, the type of backup targets you employ, the backup software you use, etc.
There are many resources available that delve into this topic in greater detail. The intent of this post is simply to make sure you are including backups in your strategy to protect the enterprise against Ransomware attacks. And, of course, Zunesis is ready to help you design a strategy that fits your needs and is right for your environment.
Though not a new phenomenon, ransomware has made some serious headlines this week.
With the recent wave of Ransomware attacks, it is becoming increasingly important for organizations to protect themselves and their sensitive data.
There are different types of ransomware. They can target any PC users – whether it’s a home computer, endpoints in an enterprise network, or servers used by a government agency or healthcare provider.
Ransomware can:
- Prevent you from accessing Windows,
- Encrypt files so you can’t use them,
- Stop certain apps from running (like your web browser).
Ransomware will demand that you pay money (a “ransom”) to get access to your PC or files. However, there is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.
Microsoft provides a complete portfolio of Cloud services to protect your data from these types of attacks. One of our specialties is helping customers transition from on premise to either hybrid or full cloud environments. Often, customers just do not know where to start. We have a complimentary assessment that can establish the basics called a “Cloud Migration Health Check,” by which we can provide you with a report outlining current on premises investments compared to what those same investments would cost in the cloud, highlighting cost savings in the process.
In light of this week’s events, (WannaCry), would it be worth a few minutes of your time to review your current environment and projects to see if Microsoft Cloud and Microsoft Office 365 & Azure would be a good fit for your organization?
Please contact us to learn more on how Microsoft dedicated Office 365 and Azure: Storage, Backup, and Disaster Recovery solutions can help optimize and protect your IT investments.
Studies show that employees are increasingly using their personal devices for more than personal use.
- 66% of employees use personal devices for work purposes.
- 52% of information workers across 17 countries report using three or more devices for work.
- 90% of enterprises will have two or more mobile operating systems to support in 2017.
- 80% of employees admit to using non-approved SaaS applications in their jobs.
So, how do we keep all of these devices secure when they’re working with corporate information?
When you combine Office 365 with the Enterprise Mobility Suite, you give employees the freedom to work securely from virtually anywhere, on any device, with the gold standard of productivity tools: O365.
- Enhance employee productivity in the office or on the road with reliable access to mobile apps, tools, and data.
- Keep sensitive data protected without the need for complex security configurations.
- Seamlessly manage employee devices, apps, and data through one simple IT admin portal.
- Give remote workers access to the familiar Office apps and productivity tools they love.
Maximize productivity with the combined benefits of Microsoft Enterprise Mobility Suite + Office 365
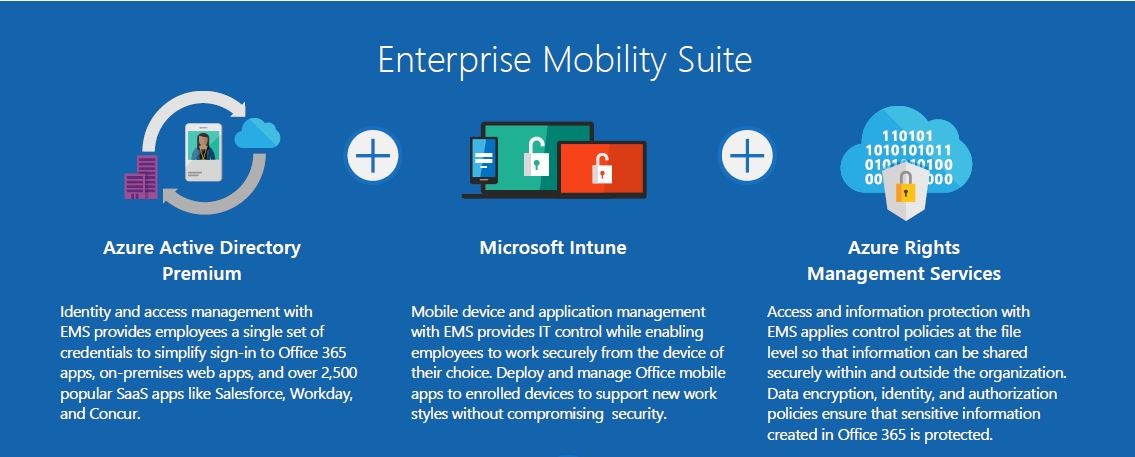
 The Enterprise Mobility Suite (EMS) is the only comprehensive cloud solution that can manage identities, devices, apps, and data. EMS includes three products: Microsoft Azure Active Directory Premium, Microsoft Intune, and Microsoft Azure Rights Management Services.
The Enterprise Mobility Suite (EMS) is the only comprehensive cloud solution that can manage identities, devices, apps, and data. EMS includes three products: Microsoft Azure Active Directory Premium, Microsoft Intune, and Microsoft Azure Rights Management Services.
Office 365 is a cloud-based service that provides users with access to industry-standard Office productivity apps like Word, PowerPoint, Excel, Publisher, and Outlook from any location with a secure internet connection. Office 365 is designed for employees who want the flexibility to take their work with them, wherever they go, without sacrificing the user experience.
Together, the EMS + Office 365 suite offers a complete managed mobile productivity solution that enables your users with the gold standard of productivity and deeply integrated protection for company data.
Synchronized identity management
Improve employee productivity with single sign-on to Office mobile apps, over 2,500 popular SaaS apps, and on-premises web apps. Enable self-service options to allow users to manage groups, passwords, devices, and apps, reducing the need for IT troubleshooting assistance. Now your employees have access to the information, tools, and intuitive Office 365 apps they need, whenever they need it.
Mobile app and device management
Empower BYOD with secure device management that ensures even personal devices are protected and compliant. Deploy the Office mobile apps so that every enrolled device becomes a powerful work tool. Now your employees can work with the Office 365 apps they know, from the devices they love.
Help protect sensitive information
Protect corporate data by allowing more secure access to company resources and enable safe sharing of sensitive information inside and outside of your organization. Easily apply encryption policies at the file level that follow the file within your organization and outside of your organization. Now your data is protected anywhere—even on the go.
Key Business Benefits of Enterprise Mobility Suite + Microsoft Office 365
- Give employees the best productivity experience wherever they happen to be working.
- Unburden your IT department by eliminating typical incompatibility and user experience issues with a simplified user management system.
- Increase business agility by sharing data securely with intended recipients, and completely on your own terms.
Composable
Have you heard the term “composable infrastructure” and aren’t really sure what it is? You’re not alone. There’s a lot of confusion out there about infrastructures of all types, from converged to hyper converged and now composable, so we understand the confusion. First, let’s talk about three types of infrastructures to give you a bit more background:
- Converged Infrastructure. This is a hardware-focused, static (aka it doesn’t change) infrastructure that supports both private and cloud environments.
- Hyper Converged Infrastructure (HCI). In an HCI environment, the infrastructure is software-defined instead of hardware-focused like a converged infrastructure. All of the various technologies (compute, storage, networking, and virtualization) are integrated together into a hardware box from a single vendor.
- Composable Infrastructure. Here, nothing is static. It consists of compute, fabric, and storage modules that you can access and use as you need them.
The main differentiator for a composable infrastructure, specifically one from Hewlett Packard Enterprise, is that it’s completely programmable and software-defined. This means that you can access your composable infrastructure to configure and reconfigure all of the resources—compute, fabric, and storage—for whatever your particular workflow needs are at that moment. Composable infrastructure is hallmarked by these three differentiators:
- Fluid Pool of Resources. Your compute, storage, and fabric resources are pooled together and provisioned to use at will.
- Software-Defined Intelligence. This is where you define the resources you need and manage the resource lifecycle.
- Unified API. The HPE OneView is a programmable interface that you use to set everything up through just one line of code.
Synergy
For composable infrastructure, we work with HPE Synergy. Maybe you’ve heard of that, too, and aren’t sure what it’s all about? Let’s dig in.
Consider this: You need to test something, and in order to do that, you need resources. So, to deploy those necessary resources, you would go to the Synergy template and request the exact resources you need in the form of an infrastructure. Synergy then quickly gets to work to compose the exact infrastructure you need from the pool of resources. When you’re done with what you’re working on, you then go back into Synergy and release those resources back into the pool for others to use.
Now that you know more about it, contact us to learn how we can help you make the move to composable infrastructure.




