 As the founder and CEO of a Colorado-based HPE Platinum Partner (Zunesis), I have been working hand-in-hand with Hewlett Packard for more than 15 years. During that time, I have seen many technology products come and go. In the past year, I have had a chance to understand the value of HPE’s most recent acquistion – SimpliVity and this solution has really caught my eye as unique and compelling.
As the founder and CEO of a Colorado-based HPE Platinum Partner (Zunesis), I have been working hand-in-hand with Hewlett Packard for more than 15 years. During that time, I have seen many technology products come and go. In the past year, I have had a chance to understand the value of HPE’s most recent acquistion – SimpliVity and this solution has really caught my eye as unique and compelling.
SimpliVity is a next generation hyperconverged solution that takes advantage of the hyperconverged strategy while also providing new and improved solutions to the limitations that have existed in other hyperconverged solutions. First, let’s talk about business value and benefits. According to unbiased research firms like Forrester, IDC, and ESG, SimpliVity provides the following business value:
- 73% Total Cost of Ownership (TCO) savings compared to traditional IT infrastructure
- 10:1 device reduction
- Up to 49% TCO cost savings when compared to AWS
- 81% increase in time spent on new projects
- Rapid scaling to 1,000 Virtual Machines with peak and predictable performance
- One hour to provision an 8-node cluster
- 57% of customers reduced RTOs from days/hours to minutes
- 70% improvement in backup/recovery and Disaster Recovery (DR)
- Nearly half of customers retired existing 3rd party backups and replication solutions
HPE SimpliVity HyperGuarantee
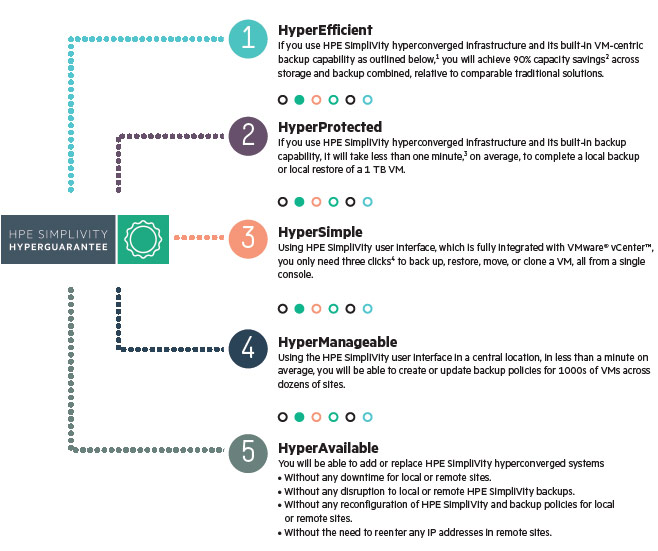
We are seeing enterprise clients deploy SimpliVity because of the way it protects data and provides built in disaster recovery. Enterprise clients with larger mission critical workloads find that SimpliVity is unique in the way it provides a robust and reliable infrastructure framework. SimpliVity provides a hyper-converged solution that is purpose-built for workloads that cannot afford to go down. Take a look at the next generation of Hyper-Converged technology in SimpliVity. Give Zunesis a call and let us spend time explaining how SimpliVity works and the value it can provide your business.
Why HPE SimpliVity and Zunesis? Read More
Wouldn’t it be nice to know how your customers really feel about the product/service you are providing them? Do you wonder if they are recommending you to other people or are they bashing you on Twitter to thousands? How many complaints have gone unanswered? Why didn’t your radio commercial bring in new business? How come your competitor’s Facebook (call-to-action) post brought in 50 new customers last week? And why didn’t anyone tell you that a waiter (at your restaurant) was unfriendly, your facilities were dirty and nobody responded to a customer’s complaint?
Not knowing the answers to these questions can expedite the trip to Chapter 7 or 13. Many business owners think they know how to market their business, but they are fooling themselves. If every business owner knew how to market their business, there would be no tangible phone books,no direct mail and certainly a lot less of the street corner sign flippers. Areas of focus in 2017 and beyond should be knowing what consumers are saying about your brand in real-time.
Could you imagine if your customers were saying this about your product or service on Facebook and your organization didn’t know about it?

But first, a chronology ……
Old School
Traditional methods of Listening are not in the present and are almost too late once the brand receives the information. Traditional methods included mailing out a survey in the actual mail (this could take months depending on how long it took to get a valid sample). Then hoping to get a 5-10% response rate and a valid sample (usually 5% +/- margin of error). Several steps had to take place before finally getting the data ready for a deliverable. Such steps included, hand coding the surveys once the data was received, running a statistical analysis, handing off reams of data to the analyst, cross-tabulating, putting those numbers into workable English and ultimately presenting the data in a way which makes sense to mid-management or C-Suite individuals.

Alexander Bell
We then graduated into telephone surveys using call centers and IVR(interactive voice response) systems based on POS (point of service) information (let’s not forget how long that took to implement and become active). Survey fields could also take months to receive the necessary amount of data to conduct statistically valid analysis. Questions were similar to tangible surveys. The key point was the amount of time it took from consumer input to brand action.

Al Gore – Internet
Online surveys were the next wave of market research technological advances. Again, the wait time to get enough information was not real time. Sure, there’s always going to be the 800 number, contact us forms via the brand’s contact us webpage, long-form writing, etc.; but again, it’s just not quick enough to act upon.

But if a brand really wants to be current with its former, existing and potential customers, it needs to be socially aware of what is being said about them in real-time. Speed to action is vital to extend a consumer’s loyalty, impress, excite and any other variation which leads to a monetized transaction and a likelihood to recommend and return.

So What is Social Media Listening?
Twenty years ago, this industry didn’t exist. Now, it’s an absolute requisite for a company to succeed in market-share expansion, crisis monitoring, customer service, sales, strategy, public relations, marketing and beyond.
Social Media Listening is simply defined as the following:
“Observing, interpreting and acting upon active conversation in real time. Any time a former, existing or potential consumer mentions your brand’s name on publicly available social media channels; there’s always someone observing, interpreting and acting upon that person’s quote.”

Dynamic
Social Media is about as dynamic as it gets. Facebook, Twitter, Instagram, LinkedIn, etc. continue to change their algorithms to increase usage which in turn provides more money into these Tech Giants. All the while, Social Media firms continue to comprehend the dynamics so they too, can increase their client- base; which in turn, that client base can go advertise on those giant social sites. It’s all cyclical, but the orbit is never the same.
Another item to consider when reading this, and it’s the same for any vertical; consumer sentiment can change within seconds. A brand’s image can be positively engaged in one minute and in the next minute, its stock price has plummeted by 5% or more. And there are plenty of examples out there which reflect this:
- Angry/Offensive tweet from C-Suite or Celebrity
- Product recall
- Health Concerns
- Political Views
- Accusations
- Imagery
These are just a few areas where organizations need to be ready in case a forced or unforced error comes across the Public Relation’s Monitor.
Sentiment is happening in real-time and organizations need to have the ability to understand where it’s coming from, how it happened, why it happened and what to do next. Not to mention, consumers demand a response in 30 seconds or less.
GenX, Millennials, Boomers ……
The lovers of Direct Mail are wasting their money. When you live in an apartment complex at the age of 25, do you want an ad about a Garage Door Company? How about a Plumber? Air Conditioning? Yet, on an individual’s Facebook Page, there’s targeted advertising based on that individual’s demographic and a few other “clandestine” (yet legal) metrics.
If there’s a topic on Facebook, Twitter, Instagram, etc. which falls into your industry, wouldn’t you want to know who’s talking about it, how old, is it Global, is it National, what gender?

Welcome to the Jungle
It’s the 21st Century folks. If you are relying upon 20th century tactics, you are missing the train. Social Listening is becoming more and more dynamic in terms of data availability. We’re unearthing metrics which are not available to just any organization. It’s paramount for an organization to take its temperature, implement a recourse if need-be and track the success of that campaign all within 60 seconds. If you don’t, your competitors will and they will GLADLY take your customers with them.
Over $500 Million Pledged to Computer Science Education
A recent article from staff reporter, Emily Tate at the Scoop News Group, announced that Computer Science has picked up a concerted cross-sector support with the Trump administration and a slew of private sector companies collectively committing more than half a billion dollars to K-12 and post-secondary STEM programs.
President Donald Trump signed a memorandum directing Education Secretary Betsy DeVos to prioritize high-quality STEM education- and in particular, computer science- within her department. She was instructed to spend at least $200 million per year in existing grant funds on that priority.
The directive, which also asks DeVos to explore other ways the administration can support computer science education, will not establish a new grant program or draw from new funds. Instead, STEM initiatives will warrant extra consideration as the Education Department chooses where to allocate existing grant money.
In announcing the directive, the White House emphasized the growing role of technology in the economy, saying that “Technical knowledge and skills are more important than ever.”
More than half of American schools – about 60 percent – do not offer computer science courses today, according to Code.org, but the demand for trained computer programmers and computer science graduates continues to climb. Seventy-one percent of all new jobs in STEM are in computing, yet only 8 percent of STEM graduates have computer science backgrounds.
“Greater access to STEM and computer science programs will ensure that our children can develop the skills they need to compete and to win in the workforce of tomorrow. ”
– President Trump
Following the president’s lead, nearly a dozen private-sector companies together pledged more than $300 million to K-12 computer science programs at an event in Detroit with Ivanka Trump, who released a video on Twitter extolling the White House’s effort and calling it “enormously important.”
Amazon, Facebook, Google, Microsoft and Salesforce each earmarked $50 million. Lockheed Martin, whose CEO was in Detroit for the event, pledged $25 million. Accenture, General Motors and Pluralsight offered $10 million or more each. Other businesses, individual and foundations dedicated funds as well.
“This money prioritizes and shines a light on computer science as a need,” said Dave Frye, Associate Director of the Friday Institute, an education resource center based out of North Carolina State University’s College of Education. “Even within STEM, computer science needs some attention. It doesn’t have the presence in schools other than STEM curricula have.”
Other organizations, including the Consortium for School Networking (CoSN), applauded Trump’s directive but questioned why the administration didn’t show that same support for STEM in its suggested budget, which proposed cutting $9 billion from the education department and would have affected key educational technology programs. “CoSN appreciates the Administration’s focus on STEM education and computer science. We hope the directive now signals a serious commitment from the Administration to educational technology investments, and in particular, the Student Support and Academic Enrichment grant program,” Keith Krueger, CEO of CoSN, said in statement. “Full funding of the program would help equip all students and schools with the resources they need to excel in modern learning settings.”
The Threats are Many and so are the Protection Methods
In a modern society, the need for cyber security touches a surprisingly large portion of our day-to-day lives. Because of the Internet of Things (IoT), we can scarcely climb out of bed each morning before we use a device that is connected to the internet in some way. Whether it’s our smart phones, Alexa, Siri, tablets, laptops, television or even our automobiles, we are potentially putting personal data out on the internet before we’ve even had our first cup of coffee (or even as we order our coffee for pickup as we head into work). We pay our bills online, we use our phones to deposit checks and we even have wi-fi enabled automobiles.
As individuals, we are responsible for looking out for our own security. As IT Professionals, we are responsible for protecting the data our company produces and collects. In many cases, the data we are protecting in our professional role is personal data, possibly our own. But, the recent Equifax breach is a harsh reminder that, even companies we associate with security are vulnerable. If there is any lesson we can take away from our personal experiences, and the stories behind the headlines, it’s that there is not single solution that will protect us from the threat of our data ending up at the mercy of people with bad intentions. Those of you reading this post are intimately familiar with the steps needed to protect company data. From the network to the desktop, and all points in between, there are many layers to a data protection strategy. One such layer is the Data Backup solutions we use.
Backup, the Original Data Protection
Decades ago, during simpler times, data protection meant being diligent about performing regular backups of data in case a file was accidentally deleted, corrupted or the hard drive crashed. Back in that simpler time, the media to which businesses directed those backups was almost always Tape, lots of tape! This process typically included keeping a set of tapes onsite for immediate restore needs and sending a second set offsite in case of catastrophe and for longer term retention. However, over time, Tape has been increasingly replaced by disk-based backup targets (think HPE StoreOnce, Data Domain, ExaGrid).

Disk-based backup targets started out as a faster way to get data backed up. Tape was still used but typically as a secondary backup target and for longer term retention offsite. The need to go to an offsite backup for file recovery was rare and so tape became that insurance policy that was never going to be needed. As use of disk-based backups became more prevalent, the technology employed to store data evolved. Improvements in compression, deduplication, and replication improved the efficiency of storing larger amounts of data (in the petabytes) and replicating that data to offsite facilities. In fact, with the ability to replicate data from one disk-based target to another over distance, we have started to see Tape being replaced at offsite facilities as well.
Backups As Our Last Defense
While we originally used backup for recovery from accidentally deleted files, random corruption and the occasional disk crash, the world we live in today requires a broader definition for Data Backup. Today, we may need to leverage our backups to recover from a Cyberattack that has either corrupted our data or rendered it unusable as part of a Ransomware attack. Because these kinds of attacks target files on volumes that are persistently mounted to hosts, the vulnerability of disk-based backup targets has come under some scrutiny lately.
Of course, many question whether the risk to disk-based backup targets is very high. After all, backup environments are typically isolated from other, more accessible, areas of the IT infrastructure. Moreover, because of the potential for Cyberattacks on the disk-based backup targets, other processes have been documented and are being implemented to mitigate the risk further. We are starting to see some of these added protections built into the backup software we use and many manufacturers of the disk-based backup devices are providing their own best-practice processes.
Despite the fear of risk for disk-based solutions, we aren’t seeing a trend away from disk-based backup, but we are hearing reports that some companies are once again turning to Tape as their last form of defense against the type of Cyberattacks that would corrupt, delete or encrypt their data. And while disk-based technology has been evolving, tape technology has also continued to evolve. LTO7 technologies provide capacities as high as 15TB (compressed) per tape cartridge. In addition to high capacities and a low TCO, Tape offers encryption at-rest, can be kept offsite and most importantly offline.
So, as we implement safeguards to keep the bad guys out of our IT infrastructure, we need to remember that our plans should include multiple layers. We also need to prepare for the possibility that our best efforts will be thwarted and that our data will be compromised. So, as part of our protection against malicious behavior and risk to our data, we need to carefully plan our Backup processes by taking the layered approach as well.




