The other day I was in bed scrolling through my Facebook, bothered by the lagging of the page, when I saw a post that was far too relatable. It read “crazy how we can transmit data from Mars but Wi-Fi still can’t reach people’s bedrooms”. Upon reading this, I began to explore new technological developments relating to Wi-Fi. I stumbled upon the development of a new type of Wi-Fi that could virtually solve that problem of unreliable internet access. This new Wi-Fi development is called Wi-Fi 6.
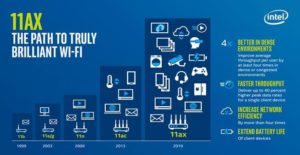
What is Wi-Fi 6?
Wi-Fi 6 is the newest generation in standard Wi-Fi technology. It is also known as “AX WiFi” or “802. 11ax WiFi.” It still fulfills the original function of Wi-Fi as it connects devices to the internet, however, it does so in a way that is faster, more efficient, and overall better for our growing society than the current 802. 11ac WiFi.
What is the goal?
While Wi-Fi 6 may come with greater speeds, that is not its overall goal. Rather, its purpose is to allow a larger number of devices to have improved network access. This would be especially beneficial in settings where there are mass amounts of devices connected to Wi-Fi at one time. These places including offices, universities, schools, companies, along with many more highly connected areas. Wi-Fi can only connect with a specific number of devices at once. When there are more devices than the network is capable of handling, there are issues with overall speed and connectivity. The new technologies of Wi-Fi 6 would help mitigate the problems associated with placing large amounts of Wi-Fi connected devices on a single network.
Longer battery life for devices
This new Wi-Fi allows for the connection of more devices, as well as improving the battery life of devices. It does this through a new “target wake time” (TWT) feature that allows the router to detect when devices are not being used. By doing this, it can halt the transmission of Wi-Fi, conserving power in devices, therefore improving overall battery life.
What technology will allow this to happen?
Two key technologies are responsible for accomplishing the goals of WiFi 6. These are MU-MIMO and OFDMA.
MU-MIMO stands for “multi-user, multiple input, multiple output”. This is already present in current routers, but Wi-Fi 6 upgrades it.
This technology allows routers to communicate with multiple devices at once. Current routers can simultaneously connect with up to four devices. Wi-Fi 6 would double this by allowing routers to connect with up to eight devices.
OFDMA stands for “orthogonal frequency division multiple access”. This technology allows one transmission to deliver data to multiple devices at once. Improving each transmission from the router to the device.
Should I go get a Wi-Fi 6 Router?
Although this new technology is exciting, it is not plausible for members of the general public to rush out and get these new routers. This is because your devices need to be compatible with WiFi 6 technology. The new routers are a bit costly. The implementation of Wi-Fi 6 in our society will be gradual. It will prove to be invaluable with the growing amount of devices in our society. As new phones, laptops, and other devices are released, most of them will likely be equipped with Wi-Fi 6 compatibility. As these new devices emerge, so will the presence of Wi-Fi 6 routers.
Want to know more about Wi-Fi 6 or wireless networking? Our network engineers can assist you with any questions you may have. Contact us today.
Technology in Sports
The presence of technology in sports has been around for a number of years. It continues to grow and evolve, contributing to a better experience for all participants. Technological advancements may be geared toward officials, coaches, fans, or athletes themselves. It is changing the way they prepare for battle, recover from injury, ensure accuracy, and how they improve upon the viewing experience/engagement.
To narrow our focus, I will dive deeper into the benefits of technology, specifically to coaches and athletes.
Coaches
From my experience, you can guarantee a coach to say one of the following, close to a million times in a career.
“It is what it is.”
“Stats don’t lie.”
“Preparation is key to winning.”
“Understanding your opponent is critical to our success.”
So much of a coach’s job falls into preparing their team for competition.
Data Analytics
Data Analytics give coaches the ability to know their teams, AND their opponents intimately. What are our tendencies? What are our opponent’s tendencies? Weaknesses? Strengths? All of these things can be monitored, recorded, and reviewed using data analytics. Once a coach knows what he/she is working with, they can allocate time and preparation appropriately.
Video Technology
Video Technology is extremely important to a coach’s ability to do their job successfully. At a certain level, the ability to capture and dissect a player’s form, decision-making, and over-all performance can make all the difference in winning and losing. “Why are they getting uncontested shots off from the elbow every possession?”
From reviewing video, maybe you learn that your post player is late to recover from help-side defense. These questions rely heavily on video technology for answers. “Why is Bob missing left every time?” Maybe you learn that his right foot is too far in front of his left, therefore causing disruption in the way he is squared to the basket. Video technology provides the “why” behind so many of a coach’s questions.
Athletes
One could argue the most important person in sports is the athlete. After all, they are the ones putting on the performance. How technology integrates with athletes is limitless. From optimizing preparation & recovery, to avoiding injury, to rehabilitating & navigating injury and more.
Pristine Physical Condition
A player’s health and well-being are crucial pieces to a long-lasting career. Having information at one’s fingertips allows athletes to achieve optimal conditioning. It also helps to develop a better and deeper understanding of how to maximize their performance and strengths.
Wearable technology has been around for a few decades, but limitations are continually pushed. While growth and innovation lead the industry toward new trends and ways in which athletes can track themselves. An example of wearable technology is a device to track steps and measure fitness. Of course, athletes often have the ability to use wearable technology in much higher-level applications.
Certain wearable technology provides information specific to muscular stress. This allows trainers to precisely measure an athlete’s performance. Training staff for teams in the MLS often use wearables. They monitor muscular output during training sessions while athletes are recovering from injury. This allows trainers to identify problems in workouts and correct them quickly. This translates to pushing hard, but not too hard. This is the KEY to recovering quickly and safely from injury.
Mental Improvement
Athletes of all realms are turning to virtual reality solutions to improve their mental game. This is arguably just as, if not more, important than the physical. For example, several NFL and college football teams use virtual reality tools to provide additional training for players outside of scheduled, on-field sessions.
Most positions at the collegiate and professional levels depend on split-second, accurate, decision-making skills. These skills are honed through thousands of repetitions in practice. Virtual Reality brings the playing field indoors. It multiples the repetitive input that cultivates the ability to make these split-second decisions.
What benefits will technology bring sports in the future? The playbook is wide open.
Want to know how Zunesis’ team can help your team get to the next level? Contact us today.
What? You still aren’t backing up your Office 365 Tenant?
Office 365 has become one of the most popular cloud-based productivity platforms. According to a recent study performed by Barracuda, “Market Analysis: Closing Backup Recovery Gaps”, more than 60% of IT professionals are using it to drive business success in some fashion. Email is the most popular (78%), followed by OneDrive (60%), SharePoint (50%), Teams (36%), and OneNote (35%).
Office 365 Security
Microsoft has done a good job in creating “Best Practices” for Office 365 Tenant Security. On January 6, 2020, they released the “Top 10 ways to secure Office 365 and Microsoft 365 Business Plans.” Its aim is to help secure organizations achieve the goals described in the Harvard Kennedy School Cybersecurity Campaign Handbook.
Microsoft recommends the following be applied to your Office 365 environment:
- Setup multi-factor authentication
- This is the easiest and most effective way to increase the security of your organization. Add a 2-step verification to all accounts. In addition to the password, there is a second component. This is usually a mobile device, which provides a code received from Office 365.
- Train your users
- Establish a strong culture of security awareness within the organization. This includes training users to identify phishing attacks. For example, don’t open the attachment just because someone you know sent it to you.
- Use separate/dedicated admin accounts
- Admin accounts are valuable targets for hackers. Admins should have a separate account for regular, non-administrative use.
- Raise the level of protection against malware in email
- Blocking of attachments with file types that are commonly used for malware.
- Protect against ransomware
- Warn users of messages originating external to the organization. Blocking of file extensions that are commonly used for ransomware. Warn users who receive attachments that include macros.
- Stop auto-forwarding for email
- Hackers who gain access to a user’s mailbox can exfiltrate mail by configuring the mailbox to automatically forward email.
- Use Office 365 Message Encryption
- Organizations can send and receive encrypted email messages between people inside and outside the organization.
- Protect your email from phishing attacks
- Configure anti-phishing protection, ATP (Advanced Threat Protection). This can help protect from malicious impersonation-based phishing attacks.
- Protect against malicious attachments and files with ATP (Advanced Threat Protection) Safe Attachments
- Helps determine whether an attachment is safe or malicious.
- Protect against phishing attacks with ATP (Advanced Threat Protection) Safe Links
- Hackers sometimes hide malicious websites in links in email or other files. Safe Links can help protect by providing time-of-click verification of web addresses (URLs) in email messages and Office documents.
Where’s Backup
 One glaring omission, not purposely according to Microsoft, is backup and retention of Microsoft 365 data. Microsoft does not hide the fact that they do not backup or provide long-term retention of Microsoft 365 data.
One glaring omission, not purposely according to Microsoft, is backup and retention of Microsoft 365 data. Microsoft does not hide the fact that they do not backup or provide long-term retention of Microsoft 365 data.
Wait……. What?
That’s right, Microsoft does not provide backup or long-term retention of Microsoft 365 data.
Let that sink in.
Microsoft does not provide backup or long-term retention of Microsoft 365 data.
An estimated 40%, that’s right 40%, of Microsoft 365 organizations aren’t using any third-party backup tools to protect their mission-critical data. Mostly due to a major misconception that Microsoft is backing up their data for them.
40% of Microsoft 365 Organizations
are not using third-party backup tools to protect
their mission critical data
Microsoft uses the term, shared responsibility model:
- They have physical security in their data centers.
- They offer data storage replication and redundancy.
- Their SLAs include guarantees of uptime and privacy controls.
- They will protect you from natural disasters that affect their data centers, hardware or software failures on their part, power outages, operating system errors, etc.
- You are responsible to protect your data from human error (due to malicious activity or innocuous accidents), misconfigured workflows, hackers, and viruses. Backing up your users and data is truly your responsibility. If you are not proactive about that, any help you get from Microsoft in times of crisis is minimal at best.
In other words, while Microsoft provides a resilient SaaS infrastructure to ensure availability, it does not protect data for historical restoration for long. Its SLAs don’t protect against user error, malicious intent or other data-destroying activity. In fact, deleted emails are not backed up in the traditional sense. They are kept in the Recycle Bin for a maximum of 93 days before they’re deleted forever. If a user deletes an email, and the retention period is reached, that email is gone forever. If a user deletes their whole mailbox, the admin doesn’t realize, and the retention period is reached, the whole mailbox is gone.
On SharePoint and OneDrive, deleted information is retained for a maximum of 14 days by Microsoft. Individuals must open a support ticket to retrieve it. SharePoint and OneDrive are unable to retrieve single items or files. They must restore an entire instance. It’s unlikely that such short retention policies will meet most compliance requirements.
Don’t Make a Costly Mistake
Many assume that Microsoft will support their backup requirements for Office 365 data. This could be a costly mistake. If they suffer a serious incident, they could find that crucial data has been deleted permanently. There are plenty of advanced, cost-effective third-party backup and recovery solutions for Office 365. IT Managers should revisit their backup strategies to ensure there are no gaps in coverage, especially in cloud-based applications, such as Office 365.
Need assistance navigating Microsoft products and backup solutions, contact Zunesis.
What’s on Your Mind? 2020 IT Needs
It’s 2020, the holidays are over and you’re back to managing your organization’s IT needs in support of their core initiatives. So, what’s on your mind? For many of our Clients, this can be summed up by three questions:
Are we adequately protected against Ransomware and can we recover from an attack?
Ransomware is a reality for individuals and businesses alike; no person or entity is immune. To someone responsible for protecting an entire organization from a Ransomware attack, the specter is ever-present. One that requires 24/7 vigilance. But these same individuals are keenly aware of that. Despite all their efforts to keep the attack from happening, they may be called upon to recover from an attack. We hear about this topic so much from our Clients that there are two BLOGS on the Zunesis website focusing on it exclusively. I would encourage you to read both Posts.
Mitigating the risks associated with Ransomware attacks requires a diligent adherence to a set of practices that include (but are not limited to):
- Keeping virus protection software up to date to keep up with the changing profiles of Ransomware attacks.
- Staying current with firmware patches on all devices (firewalls, switches, routers, serves, storage, etc.) to make sure your devices have the most recent protections.
- Staying current on Operating System updates and patches to plug security holes as they are identified.
- Managing usernames and passwords and segmenting authentication domains to reduce spread of an attack.
- Locking down non-essential ports to reduce points of entry.
- Segmenting LANs to minimize spread of an attack.
- Training of end-users to help them understand what to look for in emails and other external entry points. End-users are the most common entry point for attacks and the need for constant training cannot be over-emphasized.
If you are compromised, rather than paying a ransom, you’ll want to provide your organization with their best chance for recovery of your data. To accomplish this, you’ll need to spend time reviewing your backup/recovery and disaster recovery plans.
When reviewing your plans look for how they address the following:
- Are the frequency and retention policies designed to give you acceptable RPO and enough granularity to restore data that has not been compromised?
- Do you test your data for potential compromise?
- When looking at your backups, are they isolated from the rest of the network? Is there a possibility of being a target of attack (corruption or deletion)?
- Do you have multiple copies of your backups, on different media, and offsite?
- Does your backup/recovery software have built-in checks for warning of possible compromise?
- Do you have a standard practice of testing recovery of data?
While not exhaustive, the points outlined above, emphasize the multi-faceted approach an Organization needs to take in order to give themselves the best chance of avoiding the consequences of a Ransomware Attack. As I stated earlier in this post, Ransomware is top of mind for all our Clients and we will likely spend a lot of time working with them on this in 2020.
How will we get all our projects accomplished in 2020 and still manage the day-to-day tasks?
The challenge of not having enough resources and time have been a persistent issue in IT. I’ve been working in the industry for over 35 years and it seems there has never been enough money, time, or people to execute on the strategies developed to evolve and maintain the IT needs of an organization. In 2020 that is certainly not going to change.
The fact is, IT will always compete for the resources of the Organization because, for most organizations, their Mission Statement has nothing to do with building a world-class IT infrastructure. However, organizations across industries are more reliant than ever before on technology to carry out their primary Mission. For this reason, there will be an increasing array of projects that ultimately will need to be carried out by IT; the challenge of efficient resource utilization is not going to abate any time soon.
Is our infrastructure ready to support the needs of the Organization in a world where Digital Transformation is a constant, iterative process?
In the next decade, we will no doubt continue to see the evolution of how and where IT resources are utilized. After all, Digital Transformation is a journey, not a destination. More organizations are moving toward becoming Data-Driven, (leveraging Artificial Intelligence and Data Analytics to glean customer insights and make better decisions).
With this move, we will see the proliferation of Edge Computing devices, leveraging of IoT, and Machine Learning. These technologies will push us to adopt different strategies for on-premise and Cloud-based Compute, Network and Storage resources. For some IT organizations this will be a continuation of what they’ve already begun and for others it may mean a complete revamp of their existing infrastructure.
In the midst of protecting your organization from the bad actors, executing on new projects and maintaining the day-to-day tasks that are part of every IT organization, you and your team need to stay up with a constantly evolving industry that presents you with a myriad of options for continuing your Digital Transformation Journey. You can’t ignore the advances in technology, nor the relevance they might have for your organization, but finding the time to understand them and assess their value won’t be easy.
Our Available Services
 Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Whether you just want to sit down and discuss what’s on your mind, or you have already identified an area we can jump in and help, we are ready to engage. Just to give you an idea of what we have to offer, I’ve included a summary of some of the practices we have developed over 15 years to help our Clients achieve their goals.
NOTE: For any service we provide (one-time or ongoing), there is a standard process and set of deliverables we use as a starting template. From there, we will work with you to customize the service based on your specific needs. If there is one thing we know for certain, you have unique circumstances. We want to make sure our services conform to your specific needs.
Here are a few of our standard offerings:
IT Infrastructure Assessment – The objective for this assessment is to provide an analysis of where your infrastructure is today, where you want to see it in the future, and what will be required to bridge the gap.
Typical Tasks and Deliverables include:
- Discovery of Compute, Network, and Storage environment:
- Inventory/document configuration of on-premise equipment.
- Inventory/document applications (on-premise and cloud-based).
- Document hyper-visor and OS configurations.
- Document the types of data stored on-premise and, in the cloud.
- Review Backup/Recovery Infrastructure and policies.
- Review Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
- Produce a roadmap to go from where you are to where you want to be.
BC/DR Assessment – The objective of this assessment is to provide an analysis of your current Backup Recovery and Disaster Recovery architecture and processes. Because Ransomware is such a threat, we will conduct this assessment with a sub-focus on recovery from Ransomware attacks.
Typical Tasks and Deliverables here include:
- Discovery:
- Inventory/document configuration of backup environment.
- Inventory/document configuration of disaster recovery environment.
- Provide documentation on the types of data stored on-premise and in the cloud.
- Document SLA’s associated with applications and data.
- Log your Backup/Recovery policies.
- List details of Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
Recurring Data Center Advisory Service (RDCAS) – The objective of this service is to provide ongoing management of our Clients HPE environment. We monitor their device firmware and configuration. This helps them maintain best practices per HPE documentation. This service is provided over the course of a 12 Month period.
Typical Tasks and Deliverables include:
- Perform an initial inventory of all HPE devices, documenting firmware, configuration, and alerts.
- Monitor Critical Alerts published by HPE throughout the life of the service. Report these to the Client with recommendations for action.
- Monitor all alerts from HPE and report non-critical alerts in a quarterly report.
- Monitor release of new firmware and report to Client on quarterly basis (unless firmware is deemed critical).
- Offer assistance in deployment of firmware if needed.
- Assist in resolution of configuration if it doesn’t meet best practice per HPE documentation.
- Provide assistance in resolution of HPE support tickets as a Client advocate.
- Provide Quarterly environment reviews with Client.
Again, these are just examples of the ways we have helped our Clients address their challenges over the last 15 years. We have a team of technology professionals that are ready to assist you with all your infrastructure needs.
Have a great 2020. We look forward to hearing from you.
What’s on Your Mind? 2020 IT Needs
It’s 2020, the holidays are over and you’re back to managing your organization’s IT needs in support of their core initiatives. So, what’s on your mind? For many of our Clients, this can be summed up by three questions:
Are we adequately protected against Ransomware and can we recover from an attack?
Ransomware is a reality for individuals and businesses alike; no person or entity is immune. To someone responsible for protecting an entire organization from a Ransomware attack, the specter is ever-present. One that requires 24/7 vigilance. But these same individuals are keenly aware of that. Despite all their efforts to keep the attack from happening, they may be called upon to recover from an attack. We hear about this topic so much from our Clients that there are two BLOGS on the Zunesis website focusing on it exclusively. I would encourage you to read both Posts.
Mitigating the risks associated with Ransomware attacks requires a diligent adherence to a set of practices that include (but are not limited to):
- Keeping virus protection software up to date to keep up with the changing profiles of Ransomware attacks.
- Staying current with firmware patches on all devices (firewalls, switches, routers, serves, storage, etc.) to make sure your devices have the most recent protections.
- Staying current on Operating System updates and patches to plug security holes as they are identified.
- Managing usernames and passwords and segmenting authentication domains to reduce spread of an attack.
- Locking down non-essential ports to reduce points of entry.
- Segmenting LANs to minimize spread of an attack.
- Training of end-users to help them understand what to look for in emails and other external entry points. End-users are the most common entry point for attacks and the need for constant training cannot be over-emphasized.
If you are compromised, rather than paying a ransom, you’ll want to provide your organization with their best chance for recovery of your data. To accomplish this, you’ll need to spend time reviewing your backup/recovery and disaster recovery plans.
When reviewing your plans look for how they address the following:
- Are the frequency and retention policies designed to give you acceptable RPO and enough granularity to restore data that has not been compromised?
- Do you test your data for potential compromise?
- When looking at your backups, are they isolated from the rest of the network? Is there a possibility of being a target of attack (corruption or deletion)?
- Do you have multiple copies of your backups, on different media, and offsite?
- Does your backup/recovery software have built-in checks for warning of possible compromise?
- Do you have a standard practice of testing recovery of data?
While not exhaustive, the points outlined above, emphasize the multi-faceted approach an Organization needs to take in order to give themselves the best chance of avoiding the consequences of a Ransomware Attack. As I stated earlier in this post, Ransomware is top of mind for all our Clients and we will likely spend a lot of time working with them on this in 2020.
How will we get all our projects accomplished in 2020 and still manage the day-to-day tasks?
The challenge of not having enough resources and time have been a persistent issue in IT. I’ve been working in the industry for over 35 years and it seems there has never been enough money, time, or people to execute on the strategies developed to evolve and maintain the IT needs of an organization. In 2020 that is certainly not going to change.
The fact is, IT will always compete for the resources of the Organization because, for most organizations, their Mission Statement has nothing to do with building a world-class IT infrastructure. However, organizations across industries are more reliant than ever before on technology to carry out their primary Mission. For this reason, there will be an increasing array of projects that ultimately will need to be carried out by IT; the challenge of efficient resource utilization is not going to abate any time soon.
Is our infrastructure ready to support the needs of the Organization in a world where Digital Transformation is a constant, iterative process?
In the next decade, we will no doubt continue to see the evolution of how and where IT resources are utilized. After all, Digital Transformation is a journey, not a destination. More organizations are moving toward becoming Data-Driven, (leveraging Artificial Intelligence and Data Analytics to glean customer insights and make better decisions).
With this move, we will see the proliferation of Edge Computing devices, leveraging of IoT, and Machine Learning. These technologies will push us to adopt different strategies for on-premise and Cloud-based Compute, Network and Storage resources. For some IT organizations this will be a continuation of what they’ve already begun and for others it may mean a complete revamp of their existing infrastructure.
In the midst of protecting your organization from the bad actors, executing on new projects and maintaining the day-to-day tasks that are part of every IT organization, you and your team need to stay up with a constantly evolving industry that presents you with a myriad of options for continuing your Digital Transformation Journey. You can’t ignore the advances in technology, nor the relevance they might have for your organization, but finding the time to understand them and assess their value won’t be easy.
Our Available Services
 Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Whether you just want to sit down and discuss what’s on your mind, or you have already identified an area we can jump in and help, we are ready to engage. Just to give you an idea of what we have to offer, I’ve included a summary of some of the practices we have developed over 15 years to help our Clients achieve their goals.
NOTE: For any service we provide (one-time or ongoing), there is a standard process and set of deliverables we use as a starting template. From there, we will work with you to customize the service based on your specific needs. If there is one thing we know for certain, you have unique circumstances. We want to make sure our services conform to your specific needs.
Here are a few of our standard offerings:
IT Infrastructure Assessment – The objective for this assessment is to provide an analysis of where your infrastructure is today, where you want to see it in the future, and what will be required to bridge the gap.
Typical Tasks and Deliverables include:
- Discovery of Compute, Network, and Storage environment:
- Inventory/document configuration of on-premise equipment.
- Inventory/document applications (on-premise and cloud-based).
- Document hyper-visor and OS configurations.
- Document the types of data stored on-premise and, in the cloud.
- Review Backup/Recovery Infrastructure and policies.
- Review Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
- Produce a roadmap to go from where you are to where you want to be.
BC/DR Assessment – The objective of this assessment is to provide an analysis of your current Backup Recovery and Disaster Recovery architecture and processes. Because Ransomware is such a threat, we will conduct this assessment with a sub-focus on recovery from Ransomware attacks.
Typical Tasks and Deliverables here include:
- Discovery:
- Inventory/document configuration of backup environment.
- Inventory/document configuration of disaster recovery environment.
- Provide documentation on the types of data stored on-premise and in the cloud.
- Document SLA’s associated with applications and data.
- Log your Backup/Recovery policies.
- List details of Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
Recurring Data Center Advisory Service (RDCAS) – The objective of this service is to provide ongoing management of our Clients HPE environment. We monitor their device firmware and configuration. This helps them maintain best practices per HPE documentation. This service is provided over the course of a 12 Month period.
Typical Tasks and Deliverables include:
- Perform an initial inventory of all HPE devices, documenting firmware, configuration, and alerts.
- Monitor Critical Alerts published by HPE throughout the life of the service. Report these to the Client with recommendations for action.
- Monitor all alerts from HPE and report non-critical alerts in a quarterly report.
- Monitor release of new firmware and report to Client on quarterly basis (unless firmware is deemed critical).
- Offer assistance in deployment of firmware if needed.
- Assist in resolution of configuration if it doesn’t meet best practice per HPE documentation.
- Provide assistance in resolution of HPE support tickets as a Client advocate.
- Provide Quarterly environment reviews with Client.
Again, these are just examples of the ways we have helped our Clients address their challenges over the last 15 years. We have a team of technology professionals that are ready to assist you with all your infrastructure needs.
Have a great 2020. We look forward to hearing from you.
Hello 2020! Time for Improvement
2020 is here. I don’t know whether to cry or celebrate because the older I get, it appears the years go by faster and faster.
2019 was a complete blur. If that’s an indicator for 2020, it certainly will feel like the endless ‘dirt nap’ is somewhere on the horizon. Life is short, and we must embrace it as it happens. We need to continuously try to improve our quality of life.
Customer First
 I try to take that philosophy and apply it to our IT Solutions’ Team. We implement a Customer FIRST mentality which is:
I try to take that philosophy and apply it to our IT Solutions’ Team. We implement a Customer FIRST mentality which is:
F: Flexible
I: Invested
R: Responsive
S: Strategic
T: Trusted
Zunesis’ Wins
While those are all very respectable words, I wanted to highlight some of our wins towards a Customer FIRST approach:
Daily summaries on work completed for a client – When we work with our clients, we want to assure them we are in the process or have completed the work we have done for them. At the end of the day, we will provide a complete write-up of the work performed on that day. This allows our clients to trust in our capabilities and be current where the project stands.
Constant communication with client – Similar to the above, sometimes it’s important to gently ‘nudge’ the client. We may need an important piece of information from them for us to complete our milestone(s) or the overall objective. It also shows we’re organized and invested in exceeding client expectations.
Quick turnaround when clients send an email – Being responsive goes a long way. This is especially true if there’s an escalation. Problem resolution for an Infrastructure is extremely important. It can either save an organization or if not responded to in a timely manner, can cost an organization thousands to even millions of dollars.
Dedication to Detail – Do it right the first time. Budget the work accordingly (based on what has been learned with similar historical projects). Spell it out on a Kickoff Call with the client. Assign & schedule the correct resources. Document (and document some more for reference purposes). Continuously keep the client updated. This type of process will reduce the amount of rework, recognize scope and scope ‘creep’. It allows for additional opportunities with a client based on our reputation for being so thorough.
Internal brainstorming – Sometimes it’s possible to get stumped on one or more of the project’s process, attributes, resources, etc. Therefore, it’s so important that an engineering team meeting occurs. A uniformed type of cadence will be developed to discuss project status and introduce opportunities for solutions. We use these internal brainstorming sessions to think outside the box. There’s more than one way to par/birdie a hole on the golf course!
Opportunities
Now, some areas of opportunities for continuous wins:
Continue to implement our approach listed above – Each action item becomes more and more efficient and beneficial to the client as the practices above increase with repetition.
Keep internal stakeholders current – Your Project Manager can be the glue to the entire project. This is usually done without a hitch. It can be embarrassing to contact the client about an issue that’s already been resolved because the necessary stakeholders weren’t on all the applicable correspondences.
Identify areas of opportunity for your client to succeed – While knee-deep in a client’s infrastructure, there’s a distinct possibility our engineers may uncover a proverbial ticking time bomb. This could delay production or operations for your client far sooner than that Storage upgrade.
Infrastructure Assessments – This is almost in tangent with client success. Equipment may be running out of support from the manufacturer. This is why it’s so important for an organization to have a firm grip on their overall environment. This is just one example of a continued trusted partnership with a client.
Life is short. Implementing these type attributes and actions will allow your organization to spend less time in a datacenter. It will allow you to spend more time with the people and activities you enjoy the most.
Zunesis Solution Services Team
 As Gene Hackman says in Hoosiers, “This is your Team!”
As Gene Hackman says in Hoosiers, “This is your Team!”
James Hughes – Vice President of Engineering and Services / Engineer
Michael Gosselin – Chief Technology Officer / Engineer
Garrett Law – Networking / Engineer
Adam Gosselin – Network Administrator / Engineer
Joe Tressler – Microsoft / Engineer
James Burke – Networking, Compute / Engineer
Pete Knoblock – Project Management
Contact Zunesis to see how we can help improve your organization’s IT Solutions for 2020.




