Security- Top Priority in Today’s World
Security is a hot button in today’s world. Now that the number of remote workers has gone up significantly due to the health crisis, the rise of ransomware attacks has followed closely behind. Remote work environments increase the number of targets for hackers. Phishing attempts are up more than 600% in the last 6 months, exploiting new vulnerabilities in the workforce.
Multiple devices in multiple locations create new opportunities for cyberattacks. With a remote workforce, the chance for unexpected risks increases dramatically. One of those reasons being, employees use “work-arounds” and personal devices when accessing or sharing private data and documents.
There are many avenues to take when considering a heightened and more secure environment. Often, the enterprise infrastructure is not top of mind. Many solutions are available to tighten up an enterprise infrastructure to ensure a more secure environment. These projects are just as imperative when it comes to protecting your company as others.
A number of Zunesis clients have shifted focus from other high priority projects to firewall implementations. This is in an attempt to mitigate the increased security risks.
Firewall
A firewall is a network security system that monitors and controls incoming and outgoing network-traffic. It is based on predetermined security rules. It typically establishes a barrier between a trusted internal network and untrusted external network, such as the Internet.
Depending on the enterprise, a firewall solution can look very different from one company to the next. All entities should be aware of their needs and choose accordingly.
Identifying and deploying a firewall solution specific to the needs of your company is a great place to start. How else can we tighten up an enterprise infrastructure to aid in the security of company information during these cyber wars?
Zunesis Services – Risk Mitigation
Zunesis has assessments available to aid in the risk mitigation of your organization.
Firewall/Network Assessment
Often times, organizations understand the importance of a firewall, and may have even purchased a firewall solution. But, organizations frequently fail to configure said solution correctly or are not using it to its full capability. Zunesis has created an assessment to help your organization with your network security firewall needs.
The Zunesis Firewall Assessment will discover the overall utilization of an organization’s current firewall and their adherence to industry’s best standards. Components of change management and administrative access to the firewall(s) will be examined. Additional focus is made to examine the strength of the existing firewall access control lists (ACLs). Recommendations will be made on how to streamline the firewall rules or leverage additional features to make them more secure.
Ransomware Readiness and Recovery Assessment:
There will be an estimated $6 trillion in damages to business by 2021 from ransomware. The advantage of being prepared, is that you can manage problems quickly and more efficiently by already having a solution ready when a problem ensues. The importance of preparation is that it is a time saver – and time is money!
Intelligent Data Protection is a comprehensive approach to data protection and copy data management. It focuses on how an organization protects and uses its data (now and in the future). Is your organization prepared? What is your backup policy? What is your Disaster Recovery plan?
Zunesis has developed an assessment that documents the readiness of an organization to recover data that may have been impacted by a Ransomware attack. Through review and analysis, a Zunesis engineer will provide observations and recommendations to better prepare your organization for future data attacks.
Recurring Data Center Assessment Services:
If limited resources within your company’s IT department is problematic, maintenance details are often the first thing to slip through the cracks. It is important to stay on top of firmware updates, device OS updates and other customer advisories.
Through RDCAS, we ensure that the most current software and firmware updates are installed across your environment. We work closely with your organization to determine the frequency of your infrastructure review.
The review is limited to the following HPE infrastructure devices including: blades and rack mount servers, HPE Storage, HPE Fibre Channel Switches, HPE Synergy Frame and HPE SimpliVity Hyper-converged platform.
What does the future hold for security innovation and advancements?
The future for security in today’s organizations will still remain a high priority. Here are a few predictions from IT experts.
- Artificial Intelligence (AI) will be a core component of cybersecurity systems
- Cyber warfare threats will be a focus
- The number of hackers will rise
- Developing cybersecurity talent becomes essential
- Legacy technology will continue to be an issue
Zunesis’ commitment is to help moderate problems and issues that arise within the industry. Our goal is to make the lives of our clients better. With risks and threats to businesses on the rise, Zunesis is dedicated to helping our clients prepare for the worst, plan for the best, and manage the present.
Access to your Business-Critical Data and Applications
There are many facets to a thoughtful plan for maintaining highly available access to your business-critical Data and Applications. The consideration starts with the location of your hardware infrastructure components (Compute, Networking, Storage). Does the facility provide security, cooling, reliable and redundant power, etc.? Are your hosts, storage and network equipment designed with redundancy, i.e, Power Supplies, Fans, Drives, etc.? Does your design include Clustering, Replication, perhaps a Disaster Recovery site? All of these are part of a complete plan.
But, even the most highly available hardware infrastructure is not much use without the Data and Applications it is configured to support. For protection of data and applications, we must have a Backup/Recovery process in place. Often, with Backup/Recovery implementations, the biggest effort is with the initial setup. This is where the software is installed, backup targets are configured, and backup jobs are defined. After that, the jobs get monitored periodically. If the job status is green, then nothing more is done until a file or Virtual Machine (VM) needs to be recovered.
Testing is Important
While taking time to plan the jobs and maintain consistent monitoring of them is critical, testing the Recovery of the Data and Applications being protected is equally important. All of us would likely agree we need to validate our Backup data. However, this is a step that is often pushed to the side because of competing priorities in every IT environment. For many IT environments, Backup/Recovery becomes a “set it and forget it” activity. The focus is mainly on the Backup process.
So, perhaps the answer to ensuring we validate the recoverability of what we are backing up is to automate the validation process. At Zunesis, we partner with Veeam to help our clients protect their Data and Applications with Veeam Backup and Replication (Veeam B&R). If you aren’t familiar with Veeam, let me provide a brief summary.
Veeam Backup and Replication
Veeam B&R is a Backup/Recovery application for protecting any workload, including virtual machines, physical servers, Oracle, Microsoft SQL, Exchange, Active Directory, Microsoft SharePoint, NAS, and Cloud. These don’t represent everything that Veeam B&R can protect, but this list should make it clear that Veeam will likely be able to protect any workload in your environment. Furthermore, Veeam has built-in Replication, WAN Acceleration, Integration with many storage arrays, Encryption, Deduplication, Compression, and more.
Veeam SureBackup
But the one feature I want to highlight here is Veeam SureBackup. Perhaps you use Veeam and have seen the SureBackup option in the management console but never really explored its capabilities. To summarize, SureBackup is the Veeam technology that lets you test VM backups and validate that you can recover data from them. With SureBackup, you can verify any restore point of any VM protected by Veeam B&R. Using SureBackup, Veeam B&R can boot the VM from the Backup in an isolated environment, scan VM’s for malware, run tests against the VM, power the VM off and create a report on the recovery verification results. The report can then be automatically emailed to you for review.
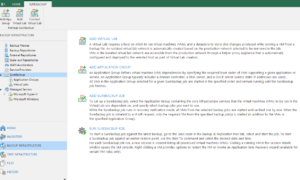
As referenced below, SureBackup is a feature you would see whenever you are viewing the Veeam B&R Management Console. And like most of the Veeam features, you are guided through its setup using a step-by-step process in the Management Console. The screenshot shown below lists the major steps (in order) for setting up the SureBackup environment.
While it is beyond the scope of this post to walk you through the entire setup, I would like to provide you a summary of the setup using the steps outlined in the screenshot above. Through this Summary, I hope to convey the power of the Veeam SureBackup feature.
It is important to remember that the SureBackup feature utilizes VM’s that are protected by scheduled Veeam Backup Jobs.
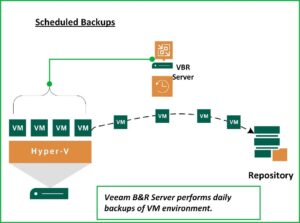
Once you have the Backup Jobs defined, you can setup the SureBackup environment to validate that what you’re backing up can be restored when the need arises. So, let’s take a look at the major steps required to implement SureBackup.
ADD VIRTUAL LAB
The first step in building a SureBackup environment is to Create a Virtual Lab. The virtual lab is an isolated virtual environment in which the backed up Virtual Machines are started and tested. You can create multiple Virtual Labs depending on your needs. During the creation of the Virtual Lab, Veeam B&R will deploy a Linux Appliance that will fence off your Production environment from the Virtual Machines being tested.
The Appliance will act as Gateway, provide DHCP, and Routing to the isolated environment while facilitating access from the Production environment if needed. To accomplish this, the Appliance has network access to both the Production environment and to the Virtual Lab. With the Appliance in place, VM’s can be restored to the virtual lab using the same IP Addressing as they have in the Production environment from which they were Backed up. The Appliance will keep any conflicts from arising between the two parallel environments.
ADD APPLICATION GROUP
With the Appliance in place, it’s time to create the Application Groups. An Application Group includes the VM’s you want to validate along with any VM’s they may be dependent upon. For instance, if you want to test a SQL Database Server, you will probably want to have a Domain Controller and DNS Server available and perhaps the Application Server. So, the Application Group is the place where you define a working environment for the workloads you want to validate.
ADD SUREBACKUP JOB
With the Virtual Lab(s) and Application Group(s) Defined, it’s time to create the actual SureBackup Job that will build the environment on-demand or based on a schedule. In this step you will specify the Virtual Lab you’ll be using and the Application Group you’ll be including in that Virtual Lab. Then, you can select from the Backup jobs you already have running to specify the VM’s you’ll want to validate.
As part of the Job creation you can configure what you want to test/validate for each VM. Examples of validation criteria include testing the disk content for corruption, scanning VM’s for malware, and performing PING tests. During the setup you are able to select predefined test scripts or include custom scripts to use for testing. Once all the components have been defined, you can schedule when you want the jobs to run (Daily, Weekly, Monthly). You will also decide to whom the Job results should be sent.
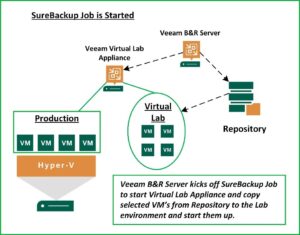
Benefits Worth the Effort
So, as you can see, the SureBackup environment will take a little time and planning to build and test. The benefits are well worth the effort.
It provides an automated method of validating Backups. Its design allows for the Virtual Lab to be created on-demand. This is an environment where one can test server and software updates, perform security testing, and conduct DevOps and Analytics. This is all done without impacting your Production environment. Veeam calls this capability the On-Demand Sandbox.
If you already use Veeam B&R, but haven’t tried the SureBackup option yet, I hope this post has encouraged you to give it a try. If you do not currently use Veeam, I hope your interest is peaked and you want to learn more. In either case, Zunesis has Solution Architects who can help you. We have Veeam B&R deployed in our lab so you can explore for yourself the SureBackup functionality. You can get a better understanding of this important piece of a thoughtful plan to maintain highly available access to your business-critical Data and Applications.
Healthcare and Education
The world is experiencing hardships across different industries. Two industries that are top of mind for everyone right now are education and healthcare. Both industries have immediate needs. Classes need to be available for children of all ages including higher education. Healthcare institutions need to stay operational.
Beyond the classroom, this also impacts parents. They want the assurance that their children can receive a valid education (from home or in the classroom). They need to have access to the right tools to make this work. For full-time workers, they need to balance work and education for their child(ren).
Quick access to a healthcare provider (telehealth or otherwise) is a desire for all. Healthcare professionals need to keep things running efficiently wherever they are practicing.
Funding Available
Many organizations in education and healthcare are in need of various solutions to help accommodate these unusual times. The biggest issue is that many may not have the budget available.
There is Federal funding available. Many have acted on this and have already received their allotted amount. There’s also the possibility that many (including institutions) aren’t knowledgeable about who and what qualifies for the CARES Act.
CARES Act
On March 27th, the CARES Act was signed into law. The United States Treasury set aside $150 billion. Through the Coronavirus Relief Fund, the CARES Act provides for payments to State, Local, and Tribal governments navigating the impact of the COVID-19 outbreak.
The CARES Act requires that the payments from the Coronavirus Relief Fund only be used to cover expenses that—
- are necessary expenditures incurred due to the public health emergency with respect to the Coronavirus Disease 2019 (COVID–19);
- were not accounted for in the budget most recently approved as of March 27, 2020 (the date of enactment of the CARES Act) for the State or government; and
- were incurred during the period that begins on March 1, 2020 and ends on December 30, 2020.
This funding can include Technology infrastructure maintenance, laptops for children for in-home education, telehealth and improved bandwidth capacity. There is a significant demand for institutions to keep up with the necessary technology and bandwidth as remote working and schooling continue.
Examples of How the Funding Can Be Used
This funding covers K-12, higher education, Telehealth and Healthcare providers at the state and local levels. Many organizations may ask how can this funding be used.
In healthcare, there is the need for never-ending storage for electronic versions of X-rays. These are typically very large files and will take up a significant amount of space in one’s current storage environment. This is one example in healthcare where funding is needed.
Another case is schools who store online educational software, student’s online reports, projects, etc. More and more file space is a need. Data centers will need to expand and costs for storage will increase. These type of funds can help education and healthcare institutions expand their storage to accommodate the forthcoming Terabyte avalanche. There are cases where these funds could pay for the entire storage upgrade.
Providing children with the necessary equipment to learn as much at home as they are in the classroom is expensive. However, like the potential storage costs being covered under the CARES Act, State or local funding, the same could be said for laptops. Below is an example of funding available from a fund titled, “Elementary and Secondary School Emergency Relief Fund (ESSER).”

Items to Be Aware Of
However, much like annual budgets prior to COVID-19, if funds are not used, then the next round results in a smaller financial injection. There are also local and state funds available for educators and healthcare providers. These have their own deadlines for application and expenditures. Below is a timeline of the Elementary and Secondary School Emergency Relief Fund (ESSER) ($13.2 billion). This is just an example of what to be aware of when researching and applying for funds. There’s a ‘shot clock’ for obtaining these funds.
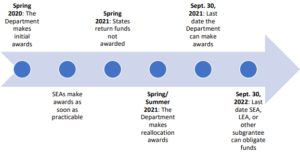
Recipients of the CARES Act, State and local funding must all meet the requirements. At Zunesis, we can help identify funds and grants which would be applicable to an education or healthcare institution. We have done this for several of our SLED and Healthcare customers. It can be overwhelming, but we’re very good at identifying these opportunities.
Being an IT Solutions provider, we can identify the optimal infrastructure for your Education or Healthcare organization. And once the funding is available, we will make the applicable hardware order, track it, install it and provide documentation for reference.
We are all in this fight together. Let’s work together to help one another out during these times of need.
Microsoft Product Life cycle
A typical Microsoft product life cycle lasts 10 years from the date of the product’s initial release. The end of this life cycle is known as the product’s end of support. This means Microsoft will no longer provide updates or support of any kind.
End of support can result in vulnerabilities that impact your infrastructure and data.
End of Support
Mainstream support for Exchange Server 2010 ended in January 2015. Per standard practice, Microsoft’s extended support ends five years after mainstream. The original end of support date was in line with the end of support for Windows 7 and Windows 2008 server. This occurred on January 14, 2020. However, to allow businesses time to complete their migrations, it was extended to October 13, 2020.
Mainstream support for Office Suite 2010 is also ending on October 13, 2020. This leaves approximately 3 months to find the right path for your organization and implement the migrations.
End of Support Implications
- So Long Security Updates – Critical components like bug fixes and security patches that protect users and data will discontinue. Without these updates, the risk of ransomware or malicious attempts to access information rises.
- No More Support – The first thing Microsoft support will tell you when you attempt to open a new case is, sorry, that version is no longer supported. We cannot help.
- Goodbye Support Documentation Updates – While existing articles will still be available, new best practices and guidance will no longer continue to be published for those versions.
- Hello Compliance Issues – Running outdated or unsupported products can be an immediate ticket out of compliance. If your industry or regional standards are dependent on regulations, you may be introducing a legal problem if you stay put.
- No More Bug Fixes – With the discontinuation of bug fixing, you can expect to see the introduction of stability and usability issues.
- Accept Risks with Unsupported Versions – There are risks of downtime and productivity loss from server failure. It could end up costing you money in addition to headaches.
What will happen on October 14, 2020?
If you are on these versions of Microsoft software, they will continue to run. However, there will be some very good reasons to be concerned when staying on these platforms:
- Compatibility – Assuming you’re Exchange Server 2010 is running on a compatible Microsoft Windows Server OS, updates to the OS may not be compatible with Exchange Server 2010. Making it very possible that an OS update could cause Exchange Server to cease to function. So, you will be limited to what updates you can install from the OS perspective.
- Security – Vulnerabilities are discovered and released daily. After October 13, Microsoft will not release security patches to address the new vulnerabilities for Exchange Server 2010 and Office Suite 2010. This means a new vulnerability may or may not work in Exchange Server 2010 or Office Suite 2010. Microsoft will not care. Be sure that the cybercriminals will be testing out the new vulnerabilities on the older versions.
- Compliance – New government regulations around protecting data are getting specific around what kinds of IT controls need to be in place. For example, PCI requirements state “Ensure that all system components and software are protected from known vulnerabilities by having the latest vendor-supplied security patches installed. Deploy critical patches within a month of release.”
Options – Exchange Server 2010
- Migrate to Exchange Online (Office 365) – This is the preferred path by most organizations. By upgrading to Office 365, you have the latest version of Exchange in addition to all the functionality, collaboration, and applications without maintaining on-premises hardware.Microsoft provides one of three types of migration scenarios:
1. Cutover: (for smaller orgs) Where everything is migrated and on-prem services are shut down.
2. Minimal Hybrid: Similar to cutover, but when you have so many mailboxes you need a bit of time but without any of the hybrid environment features.
3. Full Hybrid: Where you have lots of mailboxes and need to be hybrid for an extended period of time while you migrate. This is also clearly the preferred option from Microsoft’s end.
From feature enhancements to recent announcements of price hikes for on-prem software, Microsoft continues to push organizations off-premises and into the cloud suite. Support is available for all of Microsoft’s cloud offerings.
- Remain On-Premises and Migrate to a Supported Version of Exchange – Moving email to the cloud may not be possible for business reasons. By migrating to a newer instance of Exchange, your organization has protection against the implications of an out-of-date server. Microsoft has 3 versions of Exchange Server remaining under support after October 13, Exchange Server 2013, 2016, and 2019. All are viable choices to remain on-prem (Exchange Server 2013 is slated for end of support 4/2023). Microsoft recommends at least Exchange 2016 as 2013 has limited functionality compared to Office 365. Keep in mind, there is no upgrade path for Exchange Server. A new Exchange environment will need to be stood up. Then a migration occurs to move the mailboxes and data. Support is not available with Microsoft’s on-prem offerings.
Whichever option one chooses, the plan should be simple and effective.
- Decide on a path – Determine whether to update to a newer version of Exchange Server or move to Office 365 (or another platform if desired).
- Assess Mailbox Usage – How many mailboxes and how much space are they taking up?
- Determine Migration Strategy – whether on-prem or cloud.
- Assess Archive Options – will archiving help depending on length of time email has been around and the amount of space.
- Archive – archive any data fit for archiving
- Migrate – whether on-prem or cloud.
Options – Office Suite 2010
Microsoft has also been making a push to Office 365 here as well. There are fewer feature updates and enhancements for Office Suite 2019. A recent 10 percent price hike has occurred. It has a shorter extended support life than prior versions of Office Suite.
Both versions of Office Suite 2019 (Cloud or On-Prem) require Windows 10.
Migrate to Office 365
- Subscription based service with a license tied to a subscription few based on the amount of users
- Upgrade options with a variety of available plans to tailor usage to user needs.
- Regular feature updates to keep current with Office features, tools, and bug fixes alongside security updates to keep protection up to date and safe from hackers.
- Built in cloud storage capabilities with Microsoft OneDrive.
- Support window that will exist as long as the Office Suite does.
Remain On-Premises and upgrade to Office Suite 2019
- One-time purchase sold on a per computer perpetual license.
- No upgrade options for future releases.
- No feature updates from initial release.
- Security updates to keep protection up to date and safe from hacking.
- Five-year support window that ends in 2025.
Conclusion
Office Exchange Server 2010 and Office Suite 2010 end of life is an inevitability all users must face. With a little less than 3 months remaining, now is the perfect time to figure out which of Microsoft’s options are best. Then, start the groundwork for migration. Deciding whether Office 365 is right for your organization will depend greatly on your needs. Whatever your requirements, making an informed decision will ensure an ease of transition and applications that are optimal for use.
Contact Zunesis for an assessment on what Microsoft option is best for your organization.




