 In April of 2015, Microsoft officially launched Skype for Business. Microsoft’s instant messaging and conferencing program has become more and more useful over the years, making it easier to do things like share documents, give presentations, and video chat.
In April of 2015, Microsoft officially launched Skype for Business. Microsoft’s instant messaging and conferencing program has become more and more useful over the years, making it easier to do things like share documents, give presentations, and video chat.
One benefit that more companies are using or looking into using is utilizing Skype to replace their business’ existing phone system. Zunesis moved their phone system to Skype last year and has only begun to use some of its functionalities.
How Does it Work?
Skype’s Cloud PBX system does almost everything a regular PBX system does, but it also integrates with Office 365, allowing you to do things like send voicemails as an email, eliminating the need to ever check voicemail again. It does everything a landline does, such as hold and transfer, but it also has many features landlines don’t have.
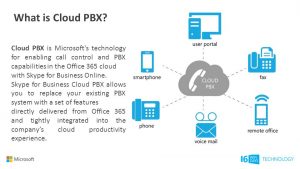
As part of the Office 356 suite, Skype centralizes all administration in the cloud. This simplifies all administrative tasks, and allows users to make and receive calls anywhere, as long as they have the Skype app running on their laptop or mobile device. No longer do employees need to be tethered to a desk phone during business hours, and in a world of increasing mobility, this is incredibly useful. You don’t even need to get new phone numbers to replace your current system, Skype allows you to port any phone numbers, allowing you to keep your business number. No need for new business cards, or any emails to customers telling them your phone number has changed.
Another perk of using Skype instead of a traditional phone line is the flexible subscriptions. You can add or subtract users as you go so you never have to pay for more than what you are using. You can set permissions by giving some users the ability to make international calls, while only allowing others to make domestic calls.
Skype integrates VOIP capabilities with instant messaging and conferencing, making it a great communications tool. One can send instant messages, screen share, or make calls all from the same place, using the same contacts. You can dial by name from any office 365 app, or use the traditional dialer in Skype, which is a welcome familiarity for many users. It also comes with 5 licenses per user, so you can make calls from any device.
Some other features include:
 Enterprise calendar call routing: where you can enable or disable call forwarding by using your exchange calendar business hours.
Enterprise calendar call routing: where you can enable or disable call forwarding by using your exchange calendar business hours.
Do-not-disturb routing and call blocking: If you don’t want to be disturbed while you work on a big project, you can easily block calls except from those that you specifically indicate are ok to come through to you.
Device Switching or Transfer a Call to Another Person in your Office: Move from a headset to speakerphone with just a few clicks. Easily transfer calls to other people.
Caller ID, Call Waiting, Call Delegation, Call History and Call Forwarding: All tools available through Skype.
Support: Microsoft offers 24/7 support, so you never have to worry about phone lines going down. Anyone already using Office 365 should definitely be looking to replace their current phone systems with Skype. It offers so much for so little, costing around $8/user, it could end up saving your business money.
Additional Resources on Deployment, Licensing and Features of Skype Business Phone System:
- Set up Calling Plans: This article has step-by-step instructions to get set up with your phone numbers or to transfer your existing phone numbers to Skype for Business.
- Plan your Phone System in Office 365 (Cloud PBX) solution: This TechNet article lays out all of your deployment options. It also has information about planning an entirely cloud-only solution.
- Skype for Business and Microsoft Teams add-on licensing: Learn which licenses you need to buy to get the Phone System in Office 365.
- Set up Phone System voicemail – Admin help
- Discover Skype for Business: Help the people in your company learn how to use Skype for Business features.
As of September 2017, Microsoft announced that Microsoft Teams will replace Skype for Business and will add more functionality. The transition will occur over the next three years and Zunesis will keep you updated as further announcements are made.
If you are interested in learning more about using Skype for Business for your phone system, contact Zunesis for more information on how we can set up your company with licenses.
Cloud computing has definitely impacted how most enterprise IT Departments are managing their overall IT architecture. Businesses are constantly reevaluating what infrastructure will work best for their environment. Is it private cloud, public cloud, or hybrid cloud? What are the differences between these types of clouds? All three options provide similar benefits, including cost-effectiveness, performance and reliability but ultimately which deployment method a business chooses is dependent upon their business needs.
Public Cloud
 Public cloud is a term for cloud computing services offered over the public Internet and available to anyone who wants to purchase them. This type of cloud typically offers the greatest level of efficiency in shared resources however they are typically more vulnerable than private clouds. Microsoft Azure is an example of a public cloud. All hardware, software, and other supporting infrastructure is owned and managed by the cloud provider. You share the same hardware, storage, and network devices with other organizations or “cloud tenants.” You access your services and manage your account using a web browser.
Public cloud is a term for cloud computing services offered over the public Internet and available to anyone who wants to purchase them. This type of cloud typically offers the greatest level of efficiency in shared resources however they are typically more vulnerable than private clouds. Microsoft Azure is an example of a public cloud. All hardware, software, and other supporting infrastructure is owned and managed by the cloud provider. You share the same hardware, storage, and network devices with other organizations or “cloud tenants.” You access your services and manage your account using a web browser.
A public cloud may be a good option when:
- Your workload for applications is used by lots of people, such as email
- You have SaaS (Software as a Service) applications from a vendor who has a well implemented security strategy
- You need incremental capacity (ability to add computer capacity for peak times)
- You are doing collaboration projects
- You are doing an ad-hoc software development project using a Platform as a Service (PaaS) offering cloud
- Testing and developing environments
Public cloud storage is for the most part cheaper than on-premises storage especially when you look into the upkeep and upgrades you may need with your hardware. Most cloud-storage services can accommodate periodic surges and typically have security protocols in place to protect your data including backup in a second location.
The biggest warning is to make sure that your business takes the extra time and due diligence to ensure you have security and governance issues well planned. This option may work best for small businesses since they typically do not have a lot of proprietary information that requires extra security.
Private Cloud
 A private cloud consists of computing resources used exclusively by one business or organization. It can be located physically at a business’ on-site datacenter or it can be hosted by a third-party service provider. The services and infrastructure are always maintained on a private network and the hardware and software are dedicated solely to the organization to allow your business to customize its resources to best fit your specific IT requirements. Private clouds are often used by government agencies, financial institutions and other mid to large size organizations where its critical to have control over their IT environment.
A private cloud consists of computing resources used exclusively by one business or organization. It can be located physically at a business’ on-site datacenter or it can be hosted by a third-party service provider. The services and infrastructure are always maintained on a private network and the hardware and software are dedicated solely to the organization to allow your business to customize its resources to best fit your specific IT requirements. Private clouds are often used by government agencies, financial institutions and other mid to large size organizations where its critical to have control over their IT environment.
Advantages include:
- Ability to customize the cloud environment to meet your specific business needs
- Improved security since your resources are not shared with others
- High Scalability
Here are some additional indicators that your application may be a good fit for the private cloud:
- Application has very predictable usage patterns and low storage costs
- You need high performance access to a file system. For example, a media company that creates or produces large videos
- An application that may be poorly written or infrequently used that may not be worth the effort of moving it to the public cloud
Hybrid Cloud
 A hybrid cloud is becoming a more popular choice for businesses of all sizes. In 2015, almost 90% of enterprises said they were looking to pursue a hybrid cloud solution. It is where both public and private cloud are utilized to host your data. In a hybrid cloud, both data and applications can move between private and public clouds for greater flexibility.
A hybrid cloud is becoming a more popular choice for businesses of all sizes. In 2015, almost 90% of enterprises said they were looking to pursue a hybrid cloud solution. It is where both public and private cloud are utilized to host your data. In a hybrid cloud, both data and applications can move between private and public clouds for greater flexibility.
Cloud bursting is also an option when using a hybrid cloud. Its when an application or resource runs in the private cloud until there is a spike in demand such as during the holiday season when online shopping is at its peak and then at that point, the organization can “burst through” to the public cloud to tap into additional computing resources.
Advantages of hybrid clouds:
- Control: you can maintain a private infrastructure for sensitive assets
- Flexibility: take advantage of additional resources in the public cloud when you need them
- Cost-effectiveness: You pay for extra computing power only when needed
- Ease: You can migrate to the cloud gradually and phase in workloads over time.
A hybrid environment is only as strong as the integrations that unite them. The team managing the infrastructure should always be running performance monitoring, regular testing, and data ingress and egress procedures to reveal possible areas of difficulty and when to further evolve the application.
When deciding what cloud platform works best for you, its best to analyze your business’ needs and what will work the best for your budget, security, and compliance. Zunesis account managers and solution architects are available to sit down with you for a discovery of what will work best for your organization. We have relationships with several great partners including Microsoft and HPE that can take your business to where you want to go in terms of cloud computing. Contact us today to find out more on how we can help.
Cloud computing has definitely impacted how most enterprise IT Departments are managing their overall IT architecture. Businesses are constantly reevaluating what infrastructure will work best for their environment. Is it private cloud, public cloud, or hybrid cloud? What are the differences between these types of clouds? All three options provide similar benefits, including cost-effectiveness, performance and reliability but ultimately which deployment method a business chooses is dependent upon their business needs.
Public Cloud
 Public cloud is a term for cloud computing services offered over the public Internet and available to anyone who wants to purchase them. This type of cloud typically offers the greatest level of efficiency in shared resources however they are typically more vulnerable than private clouds. Microsoft Azure is an example of a public cloud. All hardware, software, and other supporting infrastructure is owned and managed by the cloud provider. You share the same hardware, storage, and network devices with other organizations or “cloud tenants.” You access your services and manage your account using a web browser.
Public cloud is a term for cloud computing services offered over the public Internet and available to anyone who wants to purchase them. This type of cloud typically offers the greatest level of efficiency in shared resources however they are typically more vulnerable than private clouds. Microsoft Azure is an example of a public cloud. All hardware, software, and other supporting infrastructure is owned and managed by the cloud provider. You share the same hardware, storage, and network devices with other organizations or “cloud tenants.” You access your services and manage your account using a web browser.
A public cloud may be a good option when:
- Your workload for applications is used by lots of people, such as email
- You have SaaS (Software as a Service) applications from a vendor who has a well implemented security strategy
- You need incremental capacity (ability to add computer capacity for peak times)
- You are doing collaboration projects
- You are doing an ad-hoc software development project using a Platform as a Service (PaaS) offering cloud
- Testing and developing environments
Public cloud storage is for the most part cheaper than on-premises storage especially when you look into the upkeep and upgrades you may need with your hardware. Most cloud-storage services can accommodate periodic surges and typically have security protocols in place to protect your data including backup in a second location.
The biggest warning is to make sure that your business takes the extra time and due diligence to ensure you have security and governance issues well planned. This option may work best for small businesses since they typically do not have a lot of proprietary information that requires extra security.
Private Cloud
 A private cloud consists of computing resources used exclusively by one business or organization. It can be located physically at a business’ on-site datacenter or it can be hosted by a third-party service provider. The services and infrastructure are always maintained on a private network and the hardware and software are dedicated solely to the organization to allow your business to customize its resources to best fit your specific IT requirements. Private clouds are often used by government agencies, financial institutions and other mid to large size organizations where its critical to have control over their IT environment.
A private cloud consists of computing resources used exclusively by one business or organization. It can be located physically at a business’ on-site datacenter or it can be hosted by a third-party service provider. The services and infrastructure are always maintained on a private network and the hardware and software are dedicated solely to the organization to allow your business to customize its resources to best fit your specific IT requirements. Private clouds are often used by government agencies, financial institutions and other mid to large size organizations where its critical to have control over their IT environment.
Advantages include:
- Ability to customize the cloud environment to meet your specific business needs
- Improved security since your resources are not shared with others
- High Scalability
Here are some additional indicators that your application may be a good fit for the private cloud:
- Application has very predictable usage patterns and low storage costs
- You need high performance access to a file system. For example, a media company that creates or produces large videos
- An application that may be poorly written or infrequently used that may not be worth the effort of moving it to the public cloud
Hybrid Cloud
 A hybrid cloud is becoming a more popular choice for businesses of all sizes. In 2015, almost 90% of enterprises said they were looking to pursue a hybrid cloud solution. It is where both public and private cloud are utilized to host your data. In a hybrid cloud, both data and applications can move between private and public clouds for greater flexibility.
A hybrid cloud is becoming a more popular choice for businesses of all sizes. In 2015, almost 90% of enterprises said they were looking to pursue a hybrid cloud solution. It is where both public and private cloud are utilized to host your data. In a hybrid cloud, both data and applications can move between private and public clouds for greater flexibility.
Cloud bursting is also an option when using a hybrid cloud. Its when an application or resource runs in the private cloud until there is a spike in demand such as during the holiday season when online shopping is at its peak and then at that point, the organization can “burst through” to the public cloud to tap into additional computing resources.
Advantages of hybrid clouds:
- Control: you can maintain a private infrastructure for sensitive assets
- Flexibility: take advantage of additional resources in the public cloud when you need them
- Cost-effectiveness: You pay for extra computing power only when needed
- Ease: You can migrate to the cloud gradually and phase in workloads over time.
A hybrid environment is only as strong as the integrations that unite them. The team managing the infrastructure should always be running performance monitoring, regular testing, and data ingress and egress procedures to reveal possible areas of difficulty and when to further evolve the application.
When deciding what cloud platform works best for you, its best to analyze your business’ needs and what will work the best for your budget, security, and compliance. Zunesis account managers and solution architects are available to sit down with you for a discovery of what will work best for your organization. We have relationships with several great partners including Microsoft and HPE that can take your business to where you want to go in terms of cloud computing. Contact us today to find out more on how we can help.
What Is Azure Site Recovery?
Business outages are caused by natural events and operational failures. Organizations need a business continuity and disaster recovery (BCDR) strategy that keeps apps and data safe and available during both planned and unplanned downtime. It also needs to be able to recover those apps and data to normal working conditions as soon as possible. Azure Site Recovery meets these needs through the following avenues:
- Simple, automated protection and disaster recovery in the cloud
- Orchestrated disaster recovery as a service (DRaaS)
- Replication and disaster recovery to Azure
- Continuous health monitoring with Site Recovery
Why Site Recovery?
There are a host of reasons why Azure Site Recovery is an excellent option for BCDR, including recovery in the cloud, resiliency, testing, flexible failover, and continuous monitoring.
Disaster Recovery in the Cloud
 Replicate workloads running on VMs and physical servers to Azure, rather than to a secondary site. This eliminates the cost and complexity of maintaining a secondary data center. With Site Recovery, you have the ability to replicate any workload running on-premises, Hyper-V VMs, and Windows/Linux physical servers.
Replicate workloads running on VMs and physical servers to Azure, rather than to a secondary site. This eliminates the cost and complexity of maintaining a secondary data center. With Site Recovery, you have the ability to replicate any workload running on-premises, Hyper-V VMs, and Windows/Linux physical servers.
Resilience
Site Recovery orchestrates replication and failover, without intercepting application data. Replicated data is stored in Azure storage, with the resilience that provides. When failover occurs, Azure VMs are created based on the replicated data.
Testing Without Disruption
Azure Site Recovery allows you to easily run test failovers to support disaster recovery drills without affecting production environments.
Rich Recovery Plans with Flexible Failover and Recovery
Recovery plans allow modeling to customize failover and recovery of multi-tier applications spread over multiple VMs. Order groups within plans, and add scripts and manual actions. Recovery plans can be integrated with Azure automation runbooks. You can run planned failovers for expected outages with zero data loss, or be prepared for unplanned failovers with minimal data loss. Easily fail back to the primary site when it’s available again.
Continuous Health Monitoring
Site Recovery monitors the state of your protected instances continuously and remotely from Azure.
Interested in learning more about how Azure Site Recovery can improve (or even become) your “plan for a rainy day”? Please contact us today to learn more about this exciting solution!
What Is EMS for Office 365?
In this mobile-first, cloud-first era, questions around security dominate the conversations about moving to the cloud. EMS provides an identity-driven security solution that offers a holistic approach to security challenges by not only protecting the organization but also identifying breaches before they cause damage.
How Do You Know If EMS Might Be a Fit for Your Organization?
As with most solutions, EMS is built to solve real problems that organizations are facing in order to help them be more efficient, productive, and secure. Below are some issues that many IT organizations face, and EMS is specifically built to address these problems:
- How to help users who have too many passwords to keep track of them all
- How to secure data across mobile devices
- How to manage BYOD
- How to ensure sensitive data is protected, even on users’ mobile devices
- How to create and enforce proactive threat protection
 How Does EMS for Office 365 Address These Issues?
How Does EMS for Office 365 Address These Issues?
EMS is a rather robust solution. However, in a nutshell, below is a list of the ways in which EMS addresses the organizational concerns listed above.
Identity Management
- Single Sign-On (SSO)
- Cloud applications
- Azure supports SSO for over 2,500 SaaS application
- On-Prem applications
- Using Microsoft Identity Manager
- Cloud applications
- Multi-Factor Authentication
- Provide users an extra layer of security – force users to prove their identity using password in a combination with mobile phone (app/text/email)
- Advanced Reporting
- Track SSO utilization and identify anomalies
- Self-Service Password Reset
- With write-back capabilities
- Users can reset their own passwords, reducing Help Desk calls
Mobile Device Management (MDM)
- Microsoft Intune
- Manage all mobile devices in the mobile ecosystem
- Utilize Mobile Application Management (MAM) without requiring devices to be enrolled
- Manage corporate data on user owned device
- Utilize the same Office Applications used on-prem
Information Protection – Formerly Called Rights Management
- Classify, label, and protect data
- Apply persistent protection which travels with the data
- Enable safe sharing
Identify Driven Security
- Microsoft Threat Advanced Analytics
- Protection from advanced targeted attacks by applying user and entity behavior analytics
If you find yourself facing any of these issues in your IT organization, I strongly suggest looking into EMS from Microsoft. We would be happy to walk you through any questions you might have about the solution or talk about how it could improve your specific environment. Contact us today.
What Is EMS for Office 365?
In this mobile-first, cloud-first era, questions around security dominate the conversations about moving to the cloud. EMS provides an identity-driven security solution that offers a holistic approach to security challenges by not only protecting the organization but also identifying breaches before they cause damage.
How Do You Know If EMS Might Be a Fit for Your Organization?
As with most solutions, EMS is built to solve real problems that organizations are facing in order to help them be more efficient, productive, and secure. Below are some issues that many IT organizations face, and EMS is specifically built to address these problems:
- How to help users who have too many passwords to keep track of them all
- How to secure data across mobile devices
- How to manage BYOD
- How to ensure sensitive data is protected, even on users’ mobile devices
- How to create and enforce proactive threat protection
 How Does EMS for Office 365 Address These Issues?
How Does EMS for Office 365 Address These Issues?
EMS is a rather robust solution. However, in a nutshell, below is a list of the ways in which EMS addresses the organizational concerns listed above.
Identity Management
- Single Sign-On (SSO)
- Cloud applications
- Azure supports SSO for over 2,500 SaaS application
- On-Prem applications
- Using Microsoft Identity Manager
- Cloud applications
- Multi-Factor Authentication
- Provide users an extra layer of security – force users to prove their identity using password in a combination with mobile phone (app/text/email)
- Advanced Reporting
- Track SSO utilization and identify anomalies
- Self-Service Password Reset
- With write-back capabilities
- Users can reset their own passwords, reducing Help Desk calls
Mobile Device Management (MDM)
- Microsoft Intune
- Manage all mobile devices in the mobile ecosystem
- Utilize Mobile Application Management (MAM) without requiring devices to be enrolled
- Manage corporate data on user owned device
- Utilize the same Office Applications used on-prem
Information Protection – Formerly Called Rights Management
- Classify, label, and protect data
- Apply persistent protection which travels with the data
- Enable safe sharing
Identify Driven Security
- Microsoft Threat Advanced Analytics
- Protection from advanced targeted attacks by applying user and entity behavior analytics
If you find yourself facing any of these issues in your IT organization, I strongly suggest looking into EMS from Microsoft. We would be happy to walk you through any questions you might have about the solution or talk about how it could improve your specific environment. Contact us today.
Though not a new phenomenon, ransomware has made some serious headlines this week.
With the recent wave of Ransomware attacks, it is becoming increasingly important for organizations to protect themselves and their sensitive data.
There are different types of ransomware. They can target any PC users – whether it’s a home computer, endpoints in an enterprise network, or servers used by a government agency or healthcare provider.
Ransomware can:
- Prevent you from accessing Windows,
- Encrypt files so you can’t use them,
- Stop certain apps from running (like your web browser).
Ransomware will demand that you pay money (a “ransom”) to get access to your PC or files. However, there is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.
Microsoft provides a complete portfolio of Cloud services to protect your data from these types of attacks. One of our specialties is helping customers transition from on premise to either hybrid or full cloud environments. Often, customers just do not know where to start. We have a complimentary assessment that can establish the basics called a “Cloud Migration Health Check,” by which we can provide you with a report outlining current on premises investments compared to what those same investments would cost in the cloud, highlighting cost savings in the process.
In light of this week’s events, (WannaCry), would it be worth a few minutes of your time to review your current environment and projects to see if Microsoft Cloud and Microsoft Office 365 & Azure would be a good fit for your organization?
Please contact us to learn more on how Microsoft dedicated Office 365 and Azure: Storage, Backup, and Disaster Recovery solutions can help optimize and protect your IT investments.
Studies show that employees are increasingly using their personal devices for more than personal use.
- 66% of employees use personal devices for work purposes.
- 52% of information workers across 17 countries report using three or more devices for work.
- 90% of enterprises will have two or more mobile operating systems to support in 2017.
- 80% of employees admit to using non-approved SaaS applications in their jobs.
So, how do we keep all of these devices secure when they’re working with corporate information?
When you combine Office 365 with the Enterprise Mobility Suite, you give employees the freedom to work securely from virtually anywhere, on any device, with the gold standard of productivity tools: O365.
- Enhance employee productivity in the office or on the road with reliable access to mobile apps, tools, and data.
- Keep sensitive data protected without the need for complex security configurations.
- Seamlessly manage employee devices, apps, and data through one simple IT admin portal.
- Give remote workers access to the familiar Office apps and productivity tools they love.
Maximize productivity with the combined benefits of Microsoft Enterprise Mobility Suite + Office 365
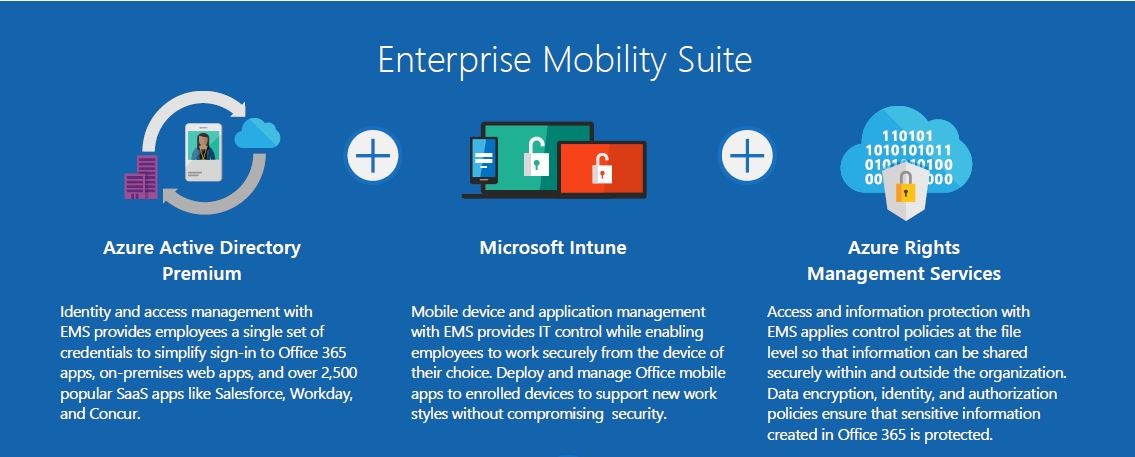
 The Enterprise Mobility Suite (EMS) is the only comprehensive cloud solution that can manage identities, devices, apps, and data. EMS includes three products: Microsoft Azure Active Directory Premium, Microsoft Intune, and Microsoft Azure Rights Management Services.
The Enterprise Mobility Suite (EMS) is the only comprehensive cloud solution that can manage identities, devices, apps, and data. EMS includes three products: Microsoft Azure Active Directory Premium, Microsoft Intune, and Microsoft Azure Rights Management Services.
Office 365 is a cloud-based service that provides users with access to industry-standard Office productivity apps like Word, PowerPoint, Excel, Publisher, and Outlook from any location with a secure internet connection. Office 365 is designed for employees who want the flexibility to take their work with them, wherever they go, without sacrificing the user experience.
Together, the EMS + Office 365 suite offers a complete managed mobile productivity solution that enables your users with the gold standard of productivity and deeply integrated protection for company data.
Synchronized identity management
Improve employee productivity with single sign-on to Office mobile apps, over 2,500 popular SaaS apps, and on-premises web apps. Enable self-service options to allow users to manage groups, passwords, devices, and apps, reducing the need for IT troubleshooting assistance. Now your employees have access to the information, tools, and intuitive Office 365 apps they need, whenever they need it.
Mobile app and device management
Empower BYOD with secure device management that ensures even personal devices are protected and compliant. Deploy the Office mobile apps so that every enrolled device becomes a powerful work tool. Now your employees can work with the Office 365 apps they know, from the devices they love.
Help protect sensitive information
Protect corporate data by allowing more secure access to company resources and enable safe sharing of sensitive information inside and outside of your organization. Easily apply encryption policies at the file level that follow the file within your organization and outside of your organization. Now your data is protected anywhere—even on the go.
Key Business Benefits of Enterprise Mobility Suite + Microsoft Office 365
- Give employees the best productivity experience wherever they happen to be working.
- Unburden your IT department by eliminating typical incompatibility and user experience issues with a simplified user management system.
- Increase business agility by sharing data securely with intended recipients, and completely on your own terms.
Examples of Software Asset Management in action.
Example:
What has been common practice, for as long as licensing vehicles have been around, has been a licensing model tied to discount levels via volume purchasing. The more you buy, the more you save. In most cases, from a purely discount perspective, it’s tough to argue getting the heaviest discount up front. However, upon further review, often the volume license vehicle in question may have clients commit to purchasing products they don’t need.
It’s generally safe to assume, for the most part, most knowledge workers regularly use e-mail. And probably Word Processing. But what about presentation software, or diagram software? Perhaps database software? As we move through the list, consumption begins to wean. As a common practice, many publishers will bundle these products; however, not every user will actually utilize all of these products.
What does this mean for a company’s bottom line? How does this impact budget?
Enter SAM:
SAM takes a look at not only what was purchased but also whether or not the product has been used. If it has been used, how frequently?
Why is this important?
 Say you have a large yearly payment via a structured licensing agreement (True Up or Annual Payment). Or, perhaps, you’ve already made the investment and are looking to renew the agreement maintenance; and after implementing a SAM program, you discover that no more than 10% of the overall TOTAL suite of products purchased have been consumed. In this case, the product suite is $300 per user X 250 users = $75,000. This means dollars have been lost in the investment. In other words, the client has invested $75K; however, they have only consumed $7,500.
Say you have a large yearly payment via a structured licensing agreement (True Up or Annual Payment). Or, perhaps, you’ve already made the investment and are looking to renew the agreement maintenance; and after implementing a SAM program, you discover that no more than 10% of the overall TOTAL suite of products purchased have been consumed. In this case, the product suite is $300 per user X 250 users = $75,000. This means dollars have been lost in the investment. In other words, the client has invested $75K; however, they have only consumed $7,500.
The challenge here is that often licensing is an all up-front investment, and it doesn’t matter whether the product ends up getting used or not. Often this is case. Businesses make the move to dive deep into an agreement to establish discount levels; however, they rarely consume more than a fraction of the product.
What are the alternatives?
Driving Business Value Through Proper Spending
One could, via a solid SAM program, identify software utilization – whether or not an end user is using a product, and if so, how often?
You almost need to re-calibrate your thinking around software consumption. A similar example would be if you were to enter a 3-year car lease; and out of the 3 years, you only use the vehicle a total of 1.5 years. That means you will have paid for a 3-year consumption of the vehicle, regardless of the fact that you didn’t get 3 years of value out of it.
The beauty of SAM is that it provides the data to support consumption behavior as well as the ability to quickly address software non-compliance, and this equals dollars saved on pending software investments. The intelligence you can bring to the negotiating table when renewing a maintenance agreement by understanding exactly what your organization actually needs is a powerful tool to drive value for your business.
Proving that your users only utilize 3 out of the 10 products in a suite allows for greater reduction in unnecessary spending. Why buy what you don’t use? Perhaps this means you buy ala-carte vs. a bundled suite for the 75% of your end-user population who don’t need all the bells and whistles.
The bottom line is that SAM from Microsoft reveals these insights and can drive cost savings in significant way. This means truly paying for what you are using.
Driving Business Value Through Compliance
For those concerned with compliance, having the insight to determine whether or not an organization is under-licensed means limited negative exposure through legal action and/or fines and penalties.
 As an example, I recall a large government entity that recently paid $1.2M in non-compliance penalties back to the software manufacturer. Let me say that again: $1.2 million!
As an example, I recall a large government entity that recently paid $1.2M in non-compliance penalties back to the software manufacturer. Let me say that again: $1.2 million!
Not only was the entity liable to pay the fines, they also needed to true-up and get current on their licensing. This government agency made front page news via the city paper for this catastrophe – and it turns out that not all press is good press. In addition to the dollars spent in penalties and fines, along with the cost of getting current with compliance, the repercussion both internally and externally was disastrous.
The reality is, this story has become an everyday occurrence; and it is becoming increasingly more commonplace throughout IT. However, this situation, as well as other non-compliance situations, could have been avoided with the utilization of a SAM discipline.
These are just a few of the many challenges relieved by SAM. Whether it’s overcoming high dollar renewals, protecting against non-compliance, or revealing usage behaviors to support key buying decisions, there is an important place for Software Asset Management in every organization. As recognized SAM experts, let the Zunesis team help you define where this will be of the most use to you; and you might even be surprised at all of the ways it applies within your business.
By definition, Software Asset Management (SAM) is a business practice that involves managing and optimizing the purchase, deployment, maintenance, utilization, and disposal of software applications within an organization.
To many of our customers, SAM is associated with software compliance, software audits, risk mitigation, risk analysis, and cost savings. All of these ring true.
My experience with SAM as a discipline spans all types of businesses, whether SMB, Corporate, Enterprise, all the way up to Government and Education. SAM, whether we realize it or not, truly is a subject that affects nearly all organizations at some point in time.
 If you’ve ever been faced with a Software audit, or have been tapped on the shoulder for a “voluntary” compliance check by a Software Manufacturer, SAM is typically the discipline utilized to come the rescue.
If you’ve ever been faced with a Software audit, or have been tapped on the shoulder for a “voluntary” compliance check by a Software Manufacturer, SAM is typically the discipline utilized to come the rescue.
Over the course of my 18 years in IT, SAM has been one of the top growth areas across the software segment.
Whether a small-mid sized or large enterprise, the risks and impact to the organization remain the same. Organizations who are found out of compliance can expect to be dealt heavy fines, whether from the BSA (Business Software Alliance) or the software manufacturer; negative internal & external exposure (especially for state/local government and publicly traded organizations); and in many cases I’ve seen, a loss in employment to those directly in charge of managing the software assets in question.
So, yes, SAM is a critical discipline. When we talk about SAM, as a starting point, we consider the following:
- Title
- Version number
- What licensing considerations apply (by user/device/processor/core/etc.)
- Whether or not the license is covered via maintenance
What we understand about SAM goes far beyond being under-licensed. I’ve seen many cases where legacy buying behaviors often reveal over-licensing. By understanding what you’ve purchased, whether or not it’s used, and how often it’s used, we create a business case for future purchases – Or sometimes the opposite: the case to support a NON purchase event.




