HPE announced HPE OneView almost 5 years ago as the next generation management tool. It is hard to believe that this product has been on the market for 5 years now. This management platform was written from the ground up, with the idea that it is an open, software defined approach to managing your infrastructure. HPE OneView was designed to use software-defined intelligence with a template-driven approach to rapidly provision, update, and deploy servers, storage, and networking, reducing the risk of human errors.
HPE OneView is a next generation management software replacing HPE Systems Insight Manager and Insight Control as the management platform for the HPE Proliant family of servers. In fact, Insight Control does not support the latest generation of servers and will be going obsolete on January 31, 2019. OneView provides the path to composability and the underlying management platform for Hybrid IT.
Recently, HPE announced OneView version 4.1. This release of HPE OneView features several enhancements to lifecycle operations, including new cluster profiles and rolling cluster updates for VMware, and online firmware and BIOS updates for HPE ProLiant DL servers. HPE OneView Remote Technician offers secure, live troubleshooting with an HPE service technician for faster problem resolution. The security has been improved with the added support of CNSA mode and is FIPS 140-2 verified for the highest security protocols.
There are three key features included with HPE OneView:
- Deploy infrastructure faster. OneView allows you to rapidly provision servers with template-based automation. The templates now include a new feature called cluster profiles to improve VMware deployments and rolling cluster updates. Existing VMware clusters can be imported into OneView and managed as a single entity. Rolling cluster updates allow users to automate cluster updates and eliminate downtime by keeping the workload up and running on available resources while other hosts get updated.
- Increase productivity. With extensive API’s available, you can integrate HPE OneView into most scripting languages available for automated deployments, including Chef, Ansible, Puppet, Saltstack, and PowerShell. The HPE Composable infrastructure allows you to programmatically control the infrastructure through a single, open RESTful API and can automate the provisioning, configuration and monitoring.
- Simplify life cycle operations. OneView and OneView Global Dashboard streamlines the management and allows you to see a single, unified view of the health of thousands of servers, profiles, enclosures and frames across multiple data centers. Get near real-time visibility of the health and status of HPE servers and storage across the globe in multiple data centers. OneView and OneView Global Dashboard provides a unified view of HPE Synergy, HPE BladeSystem c-Class, HPE ProLiant DL/ML servers, HPE Hyper Converged 380, HPE Apollo systems, HPE SimpliVity, HPE 3PAR StoreServ, and HPE StoreVirtual VSA storage in a single view.
The new Remote Technician capability provides faster problem resolution. Remote Technician allows you to grant temporary, secure access for live assistance from an HPE certified service technician. This is done on a case-by-case basis.
Contact Zunesis to learn more about HPE OneView and how it can help manage your infrastructure.
Tools Over Process
Over my career, I have worked with thousands of clients, and one thing is consistent across the conversations I have.
The clients are more focused on the tools than the process.
The explosion of tools in the technology market has not helped this fact much either. Now that tools are virtualized, and we see more and more software-defined tools, the tool sprawl is in full growth mode. Need a load balancer? Load up on this virtual appliance. Need a new Firewall? Load up this IOS image. The server sprawl that we saw during the height of virtualization is probably going to be eclipsed by the tool sprawl we are about to see with software-defined infrastructures.
This tool sprawl has and will lead to tool-rich environments that are process poor. The impact of this will be massive security risks due to a lack of knowledge of tools and the increase in the total attack surface within an organization. We will also see outages with trickle down and much larger failure domains due to the lack of process maturity within some IT organizations. I can also see that just like in the past; there will be a tendency to blame the tool and capitulate from one tool/platform to another, and not address the foundational process issues within the organization.
History repeating itself
So why do we keep learning this same lesson over and over again? Mainly because gaining process maturity is hard and even more difficult is staying mature. Also, organizations typically don’t understand the value of process maturity in information technology service delivery. Usually, the time process maturity value is realized is at time of incident. These incidents could be an outage of a critical system, security event, or the competition is outmaneuvering them due to efficiencies gained through mature automated technology service delivery.
Over the last few years, I have been working with clients who want to migrate to the cloud, and my first question to them is why? The next question is what do they mean by “the cloud”? Usually, when I hear this from the client, I start trying to understand how they deliver their technology services today. I find that most have standardized or a common off-the-shelf toolset to simplify their service delivery. The providers of these applications are rapidly moving into a SaaS, delivery model. I encourage clients to migrate to these models for their applications if they are not doing custom development and the applications are not a differentiator for their business.
Right Tool for the Right Job

That brings me to the main point of this post. Use the right tool for the appropriate job. Using the correct tool in the right way is all about the process in which the tool is used. You would never use a powered screwdriver in the same way you would use a manual one or a nail gun as a regular hammer. You would lose the efficiency of the tool.
Many clients are doing this with cloud services today when they “lift and shift” applications on the cloud. Organizations gain efficiency in hyper-scale IaaS platforms like AWS and Azure by turning systems or processes off when they are not in use. This type of capacity management is a major change for most organizations. Most have been trained to “Deploy! Deploy! Deploy!” what happens to the infrastructure after deployment is not the IT departments responsibility or concern. These actions create massive amounts of sprawl, and sprawl in an IaaS cloud platform is a terrible thing. By not utilizing the tool the right way, organizations are not getting the cost efficiencies promised by cloud vendors. This tool use makes the IaaS cloud inefficient for many and leads them to the belief that cloud is not right for them. However, the tool was used the wrong way from the start.
Changing Capacity Management
So, then it is simple, right? Just change the way we do capacity management, and we should be good. I wish it were that simple. The issue is this. Evolving capacity management to align with just in time computing becomes a daunting task. As the organization tries to reduce its amount of compute inventory to realize the efficiency of cloud and deploy systems as thin as possible, the need for new process management around inventory and capacity management becomes critical.
The capacity management is also tied directly to the business need for capacity at the time the business needs it. This leads to the fact that the capacity management of IT resources needs to be directly tied to the business operations and be treated as a constraint to the organization providing its products or services, just like any other raw materials. This redefining of IT resources results in the restructuring of teams, measuring IT service delivery differently, using manufacturing efficiency principals and focusing IT service delivery on business results rather than traditional IT metrics. Therefore, migrating to the cloud is hard and requires a shift in people, process, and lastly tools to be effective. Many organizations migrate (lift and shift) the tool first and then try to fix the process under the duress of the inefficiency. These actions can and often do lead to a failed cloud implementation and a lot of tools and vendors taking the blame.
I will leave you with this final analogy. This situation is very similar to someone wanting to get into shape. One buys the gym membership, exercise equipment, new outfits, shoes and any other technology to get into shape. However, they fail to change their eating habits, he/she does not make time to workout, and sometimes he/she even hires a trainer who makes them sore. Then, the person gives up and blames all the stuff/tools they had around them instead of focusing on the root problem which is that it takes commitment and hard work consistently over time to see real results.
Email scams have been around as long as email has existed. Many use the same techniques that scammers have been using long before the internet was a common tool. In the internet age, email scams have become more deceptive and common, and even seasoned internet users have fallen victim to these scams.
Unfortunately, there is no program or anti-virus to protect us from these scams. They are social engineering attacks, or scams that rely on tricking users, rather than infecting machines with malicious code or software. The only way to protect yourself from these types of scam is to be aware of them and recognize the signs that an email is a scam. Email programs have improved immensely over the years by adding spam filters and junk folders, but no anti-spam filter is perfect. Below are a few ways to recognize email scams.
Fake Links
Among the most common email scams are phishing scams. These are emails designed to look like a product or service you use (Office 365, paypal, etc.) and they include a link for you to click on and enter login credentials. These emails can be revealed as fake by checking the email address and the URL of the link. Often, the email address will be close to something that the actual company would use (support@m1crosoft.com instead of @microsoft.com for example). Check the email closely to see if the address is spelled correctly.

Another part of the email address to check is the domain (the part of the email address after the @ symbol). Check to see that it matches the company’s website. For example, Wells Fargo would be sending emails from an @wellsfargo.com email not wellsfargobank.com as their website is wellsfargo.com. Next, check the URL by hovering over the link with your mouse cursor. Again, it should match the company’s website. Do not click on the link if it doesn’t match the company’s website. If an email seems fishy to you, don’t trust it. If you aren’t sure, send an email or make a call to the company’s support line to verify the email is real.
Advanced Fee Scams
Another common type of scam is the advanced fee scam. Everyone has heard of the Nigerian prince that will pay you millions of dollars. Their money is locked up and can’t be accessed unless you send them a small fee that they will then use to recover their millions. Usually these emails include some sob story, and try to use your emotions against you. The best thing to remember about these types of scams is that if it seems too good to be true, it probably is. This scam has been around a very long time. The best way to deal with it is to just ignore the email, delete it, and move on.
Employment Search Scams
The employment search scam comes in the form of a job offer, requesting that you fill out a job application. These job applications are designed to get as much personal information as possible in order to steal your identity. Or, they may try to get access to your bank account and steal money that way. If you are being solicited by a company that you didn’t contact first, be very wary of a scam. Do your research on the company. Does the job title match the company’s industry? Do the job postings on their website match the information in the email? If the answers to these questions are no, the chances are good that you’ve discovered a scam.
Disaster Relief/Charity Scams
In times of disaster, where people have died or lost everything, donations sites will be set up to raise funds for those in need. Unfortunately, many people take advantage of this situation by setting up fake charities or phishing sites to get you to donate to them instead of the legitimate organizations. Donation requests through email are nearly always a scam, so ignore them all. If you want to donate to a charity or relief foundation, contact them directly through their website or via phone. NEVER click on a link in an email asking for donations.
people take advantage of this situation by setting up fake charities or phishing sites to get you to donate to them instead of the legitimate organizations. Donation requests through email are nearly always a scam, so ignore them all. If you want to donate to a charity or relief foundation, contact them directly through their website or via phone. NEVER click on a link in an email asking for donations.
The best way to avoid getting scammed is to always be skeptical of anyone asking for your private information. Ask yourself some simple questions like:
Do I know these people?
Did I request this email?
If the answer to these questions is “no”, it is most likely a scam.
I am the father of two amazing kids (a girl & boy) and I am now the grandfather of a grandson & a granddaughter. Each time I hear about a school shooting, my heart goes out to the parents, grandparents, brothers, sisters, and the entire community of those injured or killed. Each time, my wife and I talk about the number of lives that are forever crushed by such a senseless act.
I also have the honor of leading an IT Organization (Zunesis, Inc.) and an exceptional group of people who make it their business to help make the lives of people better through the application of information technology. For many years, Zunesis has been providing IT solutions to K12 School Districts in the Western United States. Video surveillance is used widely within K12 schools and is a useful technology in understanding what has happened after the fact. For many school shootings, video surveillance has been used as a tool to document what happened when, where and by whom. These benefits of video surveillance are useful, but they are 100% reactive. What if we could use a combination of video and Internet of Things (IoT) technologies to attack the problem of school shootings proactively?
How Can Technology Help Prevent Tragedy?
 Rapid advancement and innovation in IoT and video analytics may provide a preventative tool to help protect our kids from further senseless shootings. In a nutshell, the idea is to use higher fidelity 4K video cameras and co-resident video analytics software to monitor school activities, entrances, and exits. Advances in IoT allow for computer intelligence to be put at the edge of the network and provide an early warning system, alarm system, or possibly a system that triggers automated functions based on what is seen (like locking a door and preventing a would-be perpetrator from entering the school).
Rapid advancement and innovation in IoT and video analytics may provide a preventative tool to help protect our kids from further senseless shootings. In a nutshell, the idea is to use higher fidelity 4K video cameras and co-resident video analytics software to monitor school activities, entrances, and exits. Advances in IoT allow for computer intelligence to be put at the edge of the network and provide an early warning system, alarm system, or possibly a system that triggers automated functions based on what is seen (like locking a door and preventing a would-be perpetrator from entering the school).
In the past, we have used video to go back and examine what has already happened. Often it is viewed in a central location by someone watching a multitude of screens while likely being asked to do other jobs as well. This new strategy moves the video and intelligence away from a central viewing area and a reactive method, to a proactive, intelligent, at-the-edge approach. Being able to recognize a person or object that doesn’t belong beforehand could provide additional protections for our kids. Ultimately, we want to keep the bad guy(s) out of our schools before they cause harm. In situations where the shooters are students of the school, the video analytics would need to be trained to recognize things that were “out of place” such as large coats (used to conceal weapons) during warm months or students entering the school at unusual times.
Facial Recognition
High-resolution 4K video cameras and video analytics software allow these IoT systems to perform facial recognition or recognize things that are out of place (like a person wearing a trench coat during a warm month of the year). Would it be possible to load up a data repository with graphical pictures of teachers, administrators, students and parents who attend and work at the school? Would it then be possible to implement specific boundaries around allowable entrances and the times those entrances could be used? The key would be to define which people are “safe” and when they are allowed access to the school. The next step would be to define what is normal and what is abnormal for the purpose of triggering alarms and notifications. Over time, machine learning and artificial intelligence could be utilized help monitoring normal behaviors and reacting to behaviors that are inconsistent.
What About Cost?
The next big question is cost? Access to money is always a challenge for our schools. The good news is that 4K video cameras, IoT edge devices, analytics software, and compute and storage solutions (at the edge) are coming down in price. And because video surveillance is being used widely within our school systems already, these new innovations could be used to upgrade the current video systems. It is likely that these new IoT video analytics solutions will be more expensive than the current reactive video surveillance solutions, their cost should not be outside the realm of possibility. Finally, because the K12 market is so large and this need so acute, the technology would surely become more affordable as competition entered the picture and parents, teachers, and politicians became part of the funding discussions.
I recognize that this may sound like a stretch to some, but finding new ways to combat this threat should be considered and IoT and video analytics provide a possible path for that to happen. I for one am encouraged by these new innovative technologies. I believe in the very near future, we will be able to use technology to proactively protect our kids.
Zunesis Earns Distinction through commitment to Academic Customers
DENVER, CO – JUNE 13, 2018
Zunesis today announced it has become a Microsoft Authorized Education Partner (AEP), demonstrating its ability to meet Microsoft academic customers’ evolving needs in today’s dynamic business environment. To earn a Microsoft AEP authorization, partners must complete a test to prove their level of academic licensing and market expertise.
The AEP program is designed to train participating resellers on Microsoft’s Academic licensing, authorize them to purchase and resell Microsoft Academic licenses, and demonstrate to potential customers that they are approved and knowledgeable academic partners.
Academic licenses, and demonstrate to potential customers that they are approved and knowledgeable academic partners.
Zunesis has over 14 years of experience helping education organizations across the West deliver IT services that enable their faculty, staff, and students.
“The Microsoft AEP authorization shows our commitment and specialization in the academic IT marketplace. It demonstrates our knowledge of Microsoft and its academic products.” said Brian Lewis, Director-Cloud Practice at Zunesis. “We hope to accelerate our academic customers’ successes by serving as technology advisors for their ongoing IT service requirements regardless of whether the service is delivered on campus or from cloud-based resources.”
By becoming AEPs, partners show themselves to be committed and trained in providing discounted Microsoft academic products to the education market,” said Anthony Salcito, vice president of Education for Microsoft Corp.’s Worldwide Public Sector. “This authorization, along with our other education partner initiatives, gives our partners recognition of their areas of expertise and our academic customers the confidence that they are buying from academic IT specialists.”
The Microsoft AEP Program is designed to authorize and equip organizations that deliver academic products and services through the Microsoft platform with the training, resources and support they need to provide their customers with superior experiences and outcomes.
About Zunesis:
Zunesis is a prominent IT solutions provider in enterprise infrastructure, cloud practice and on-premise solutions. Our home is in Colorado and we also have a significant business base in Las Vegas, Nevada. Our many years of consistent success can be attributed to the fact that we have been able to attract and retain outstanding people, while making sure that our customers are successful.
We officially have hit the half way point on the year. You may be thinking wasn’t it just January? Or, how has the year flown by already? As many businesses and individuals do each year, we set up resolutions, projects and/or goals to achieve or tackle in the coming year. Resolutions often have a negative connotation to them of being unrealistic goals that most give up on and are considered a waste of time.
Is There Light at the End of the Tunnel?
Did you know that typically only 9% of those resolutions are kept or followed through by this point in the year? As you still see a pile of projects on your desk and deadlines that have not been met, you may be thinking is there light at the end of the tunnel? Can this year still be a success when it comes to achieving your resolutions or goals?
The truth is that many resolutions are often unattainable or need to be modified over time. As you delve into a project that you started at the beginning of the year, I’m sure there were bumps along the road. Possibly other things were discovered that took your project into a completely different direction. Besides giving up on the rest of the year and the goals that you set, what can you do that won’t result in you having a nervous breakdown or having a feeling of being an epic failure?

What can you do at this halfway point?
- Sit Down and Evaluate: Review what progress that you have made in the first 6 months of the year. Are the goals you set for this year still relevant for your company? What challenges have you come upon? Take a truly objective look at the state of your current workload in the office.
- Break it Down: Write down your current goals and our projects and prioritize them all by importance and relevance. Some goals may have already been accomplished this year. Some may no longer be important in the grand scheme of things.
- Look at the Past: Ever heard the saying that history repeats itself? Sometime that can be a good thing.What did work for you and your company and/or department? Why did it work? What can you learn from it? How can you use these lessons for future endeavors?
- Celebrate the Mini Milestones: Maybe you haven’t finished your big project yet or accomplished your major goal but recognize what you have accomplished. You are more likely to achieve the larger milestones if you recognize these smaller milestones along the way. Also, you can usually get more productivity from your staff when they feel encouraged and appreciated. Negativity is usually not the answer when trying to move a project along in your company.
- Training: Is your staff well trained? Can you trust them to take on a project from start to finish? Review your team and see what inefficiencies may be prevalent that can impact your department/company succeeding for the rest of the year.
- Get Laser Focused: What are your top priorities for the remaining six months of the year? Delegate the appropriate items to your staff and set markers for accomplishments that you want to finish. Put your needs before your wants and prioritize your valuable resources so that you are not wasting valuable time.
- Future Meetings: Are you finding not much is being accomplished at your business meetings? Know what you want from future meetings and what needs to be achieved in them. Make sure they are a valuable use of time and think about if the meeting is necessary for your project to succeed.
- Quality Assurance: As you may have noticed bumps in the road in the first half of the year, have you set up checks on your team’s work? Are you looking for bugs and having others critique each other’s look? Setting up a process to review items along the way may save valuable time and money.
- Act to Solve Problems Rather than React to them: Instead of reacting to situations, take a moment to think about what can I do to solve this situation?
- Ask for Help: Swallow your pride and ask for help when needed. There may be a way to resolve a situation that you may never thought of or knew could work. Research to see if what you are proposing is the best way to go. Projects take detours all the time and sometimes the road less traveled may lead to success. Be open to new ideas and ways to do things.
- New Projects: You may have decided that there is a new project that needs to be tackled in the next six months. Make sure you clarify the who, what, where, when, how much, etc before you jump into this next project. The devil truly is in the details.
We all ultimately have the same goal at the end of a year, that we can look back and say “Look what I accomplished!” Take the time to reflect on what has changed, progressed or saved time and money. The key to reaching your goals this year may just be in taking baby steps along the way and taking the time to evaluate what is working and what is not. Be realistic on what can be achieved and ask for help along the way when needed. Realize that no person, department or company is perfect.
Zunesis is honored to share a recent accomplishment of one of our largest vendors: Aruba Networks. In recognition of their Mobile First vision and what they have been able to accomplish, IDC, one of the leading global providers of market intelligence, advisory services, and events for the technology community, has recognized Aruba-HPE as a Leader in the new IDC MarketScape: Worldwide Enterprise WLAN Vendor Assessment.
According to the IDC, “There have been significant advancements in the WLAN market in recent years with vendors offering exciting new features that can help drive new business opportunities for enterprises. As organizations increasingly rely on wireless technologies to address business challenges, the importance of choosing the right vendor has risen considerably.” This IDC MarketScape is a vendor assessment, which profiles 11 vendors in the worldwide enterprise WLAN market and Aruba-HPE is one of only two companies named to the Leaders Category.
Ready for Innovation in a Mobile First World
The IDC MarketScape states “Aruba is well-tuned to the future of enterprise WLAN, wired and WAN innovations.” Aruba’s software-defined Mobile First Architecture is designed for exactly that, rapid innovation in the mobile, IoT and cloud era. We believe that The Mobile First Architecture provides a robust offering that meets all the metrics the IDC MarketScape used to evaluate vendors in this report. Aruba’s Mobile First Architecture gives enterprises a secure, intelligent and automated network, providing IT the visibility and control needed for digital transformation and self-service networking.
Mobile First: Purposefully built for mobility, an Aruba network allows users and things to connect and receive the same policy no matter how they are connected, via wired or wireless. According to the IDC MarketScape, “Aruba is noted for its flexibility of deployment options, which includes Aruba Instant APs with integrated control, the Aruba Central cloud-managed solution, and a broad range of controller-based solutions. Also, since true mobility requires business continuity.” At Aruba, we deliver a non-stop networking experience for environments where mobile, IoT and cloud are mission-critical.
Secure: The IDC MarketScape notes that “It is important to consider the security capabilities of any WLAN solution.” Aruba’s 360 Secure Fabric provides an integrated security framework for IT and security teams to gain back visibility and control of their network, centered around analytics. Starting with infrastructure security capabilities embedded in the foundation of all of Aruba’s APs, Mobility Controllers and switches.
Aruba builds on this foundation by integrating IntroSpect machine learning-based attack detection (UEBA) with Aruba ClearPass network access control. According to the IDC MarketScape, “Aruba is noted for its ClearPass network access control (NAC) and policy management solution.” A critical advantage of the Aruba security framework is an open, multi-vendor integration of Aruba security solutions with over 100 partners in the Aruba 360 Security Exchange Program. Customers can leverage existing security investments by seamlessly integrating them with Aruba solutions.
Autonomous: Aruba delivers AI-powered analytics and provides proactive, prescriptive and adaptive network performance monitoring and optimization. And it’s all driven by machine learning to revolutionize the quality of experience for users, IoT devices and IT staff. The flexibility of deployment for network management is recognized as one of Aruba’s strengths. Aruba’s automated RF optimization in the ArubaOS 8 WLAN portfolio uses machine learning as well to provide the best user experience even in very dense client environments.
If you would like to learn more about what makes Aruba-HPE a Leader in the market, contact an account manager from Zunesis to give you more information.
More and more companies are making the jump to Office 365, moving from their on-premises Exchange, SharePoint, and Skype for Business environments. According to Microsoft, as of October 2017, Office 365 commercial monthly active users was at 120 million, up 20 million from April of 2017. Microsoft expects to have two-thirds of its Office business customers in the cloud by some time in its fiscal 2019.
For the sake of this article, lets focus just on the Exchange Online (or email) service of Office 365.
When implementing Exchange server on-premises, would you include an enterprise backup/restore solution? Of course, you would. In fact, there might be several data protection/high availability strategies you would employ to the environment. Exchange database backup and recovery, single item recovery, Database Availability Group (DAG), business resumption and disaster recovery to name a few.
Let’s take a look at a few of these strategies which are included in Exchange Online natively.
Exchange Online provides Mailbox Replication at Data Centers for high availability of the Exchange database. Exchange Online mailboxes are continually replicated to multiple database copies, in geographically dispersed Microsoft data centers. This provides data restoration capability in the event of site or hardware failure.
Recoverable Items folders are available at both the mailbox and item level.
Deleted Mailbox Recovery – When a mailbox is deleted, Exchange Online retains the mailbox and its contents for 30 days by default. After 30 days, the mailbox is not recoverable. A recovered mailbox contains all of the data stored in it at the time it was deleted. Administrators can recover a deleted mailbox within the retention period setting.
Deleted Item Recovery – Exchange Online enables users to restore items they have deleted from any email folder, including the Deleted Items folder. When an item is deleted, it’s kept in a user’s Deleted Items folder. It remains there until it’s either manually removed by the user or automatically removed by retention policies. After an item is removed from the Deleted Items folder, it’s kept in a Recoverable Items folder for an additional 14 days before being permanently removed (administrators can increase this to a maximum of 30 days).
A user is still in control of the data, i.e. they have the ability to purge their own Recoverable Items folder at any time. Microsoft’s answer to this is Litigation Hold, which copies all mailbox items to an immutable area (hidden from Recoverable Items). The items remain there in an unchanged state until the Litigation Hold age is reached, or in the case where that age is set to indefinite, till the administrator says so.
While these are all great features built-in to Exchange Online, what happens when data loss occurs due to user error, hacking, or malicious acts? There is not a complete backup and restore solution provided by Microsoft for Exchange Online, or Office 365 for that fact. Again, these strategies above will not protect users from data loss. Microsoft puts many safeguards in place so that customers do not lose data, however, they do not specialize in data backup and recovery.
Microsoft published a white paper in April 2017 called Shared Responsibilities for Cloud Computing. Here are a few of the findings from the white paper.
“As organizations consider and evaluate public cloud services, it is essential to explore how different cloud service models will affect cost, ease of use, privacy, security and compliance. It is equally important that customers consider how security and compliance are managed by the cloud solution provider (CSP) who will enable a safe computing solution. In addition, many organizations that consider public cloud computing mistakenly assume that after moving to the cloud their role in securing their data shifts most security and compliance responsibilities to the CSP. “
“Cloud providers by design should provide security for certain elements, such as the physical infrastructure and network elements, but customers must be aware of their own responsibilities. CSPs may provide services to help protect data, but customers must also understand their role in protecting the security and privacy of their data.”
The following table is featured in this white paper which shows the shared responsibilities for different cloud service models:
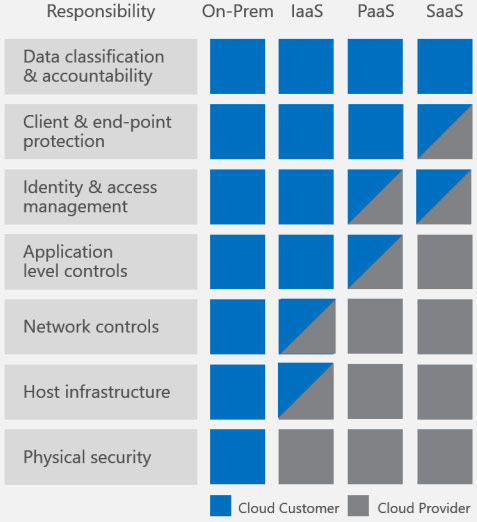
Microsoft has defined the responsibilities of the provider and the customer. Office 365 falls under IaaS (Infrastructure as a Service). Data protection would fall under the Data classification and accountability responsibility. The majority of customers assume that Microsoft is backing up their data. However, just like Exchange on-premises, there is no backup or restore built-in. Microsoft clearly puts the issue of data protection squarely on the customer.
So, what is a customer to do?
Luckily, most of the enterprise backup software providers have compatibility for Office 365. There are also several vendors who make backup and restore specifically for Office 365 which can be found in the Azure Marketplace that provide a wide array of features, such as where to store the backups (cloud vs. on-premises), archive solutions, and single-mailbox recovery.
In conclusion, Microsoft has explicitly stated in their Shared Responsibility for Cloud Computing white paper that they are responsible for keeping the cloud services available, which does not include traditional backup and recovery of the data. Don’t make the same assumption many Office 365 customers have. Treat Office 365 data like any other data; it needs to be backed up.
Last month, Microsoft unveiled details on its latest feature update to the Windows 10 Operating System. Microsoft is calling the release the Windows 10 April 2018 Update. According to Yusuf Mehdi, Corporate Vice President of Microsoft Windows and Device Group, “With Windows 10, we’ve focused on delivering the most modern and most secure operating system. Since its initial launch, we delivered two updates with features designed to enable the creator in each of us. With our latest major release – the Windows 10 April 2018 Update – we want to give you back some of your greatest currency, your time. Our hope is that you’ll have more time to do what matters most to you – create, play, work or simply do what you love.”
Timeline
One major feature on the “make the most of your time” theme is called Timeline. The feature is focused on helping users deal with the problem of having files and web activities spread across numerous devices — and spending time searching for documents they were working on, or restarting web searches when changing devices. The proliferation of devices, combined with the explosion of information, has led to an influx of screen time. In fact, today, practically all free time goes toward screens. Your information is spread across multiple devices – making it increasingly harder to find your stuff. We’ve all had the experience of digging through your email or file folders for the document you know you wrote, but can’t find. Or looking for photos and videos that you know you’ve seen and love, but can no longer locate. Timeline can help you get back this wasted time.
With Timeline, your Windows 10 PC lets you go back in time up to 30 days to find your stuff, whether you were working on it earlier today, last week, or a few weeks ago. Because much of our activity is on the go, you can even pick up what you were doing if signed into your Microsoft account while using Microsoft Edge or Office 365 on your iOS or Android device when you return to your Windows 10 PC. Imagine looking at bathroom vanity options for that home remodel when you’re out and about on your phone, and then finishing that purchase when you’re back at your PC. Or working on a document on the bus during your commute and seamlessly picking it back up when you’re at your desk.
Focus Assist
Today, most of us spend between 3-6 hours – each day – on screens. Much of this time is spent on social media, where the constant stream of distractions across our myriad of devices makes it hard to focus. In many ways, our attention is being hacked, pulling us into continuous scrolls of information, but distracting us from what matters most. This war on attention is real – in the workplace, the average amount of time people spend on any single event before being interrupted or switching tasks is about three minutes (outside of meetings). Since the average person needs about 23 minutes to regroup after being interrupted, we see our productivity and creativity diminished.
With the April 2018 Update, Microsoft introduces Focus Assist to help you stay in the zone. Turn on Focus Assist whenever you want to get things done without distractions, like social media or other notifications. Or set it to turn on automatically at certain times during the day when you want focused time. When you finish, you receive a summary of what came through, whether notifications, emails or updates, while you were heads down. If you’re waiting on a specific call or email, choose people who you want to break through.
Edge Updates
Microsoft is also helping you focus while on the web with updates to Microsoft Edge. You can now click the audio icon to mute and unmute a tab that is playing sound. Books, PDFs and Reading View pages can go full-screen for a distraction-free reading experience. Shopping gets easier as your address, payment and other information can be securely saved with the option to autofill on web payment forms. You can now clear out clutter from your printouts by printing web pages in a cleaner format with the new clutter-free printing option. Finally, anyone needing a little help with reading can use the new Grammar Tools button to enable comprehension aids. Grammar Tools can break the words on the page into syllables, as well as highlight different parts of speech such as nouns, verbs, and adjectives.
Dictation
Natural computing experiences enable us to speak directly to our devices to accomplish tasks, without typing. Microsoft sees potential for voice input to dramatically change how people interact with their devices, far beyond novelty experiences or entertainment.
One-way Microsoft has done this in the April 2018 Update is with Dictation. It is now easier than ever to take a note or write a paper, with just your voice. With your cursor in any text field either in Windows 10 or in an app, simply press Win+H and start talking. The improved Dictation feature in Windows 10 will capture your thoughts quickly and accurately.
Voice
With the April 2018 Update and Cortana enabled on your Windows 10 PC, you can manage your smart home right from your PC using just your voice. For example, want to come home to a warm house from a long day at work? With the April 2018 Update and Cortana, you can control your thermostat and other IoT devices such as a Honeywell or Nest Learning thermostat and more.
There are many great new features in the April 2018 Update including simplified IT management tools for enterprise customers, new ways to create with Photos, 3D and Windows Mixed Reality, new ways to keep you safer online and enhancements to your PC gaming experience.
The April 2018 Update is currently available as a free download as of April 30, 2018.
When your company name is Zunesis (pronounced – zoo-knee-sis) you can count on being asked two questions on a regular basis; “how do you pronounce that?” and “how did you come up with THAT for a company name?” Truth is, I’ve always welcomed that last question because it gives me an opportunity to talk about our beginning and our journey as a company. In fact, one of our Account Managers suggested we post this as a BLOG because he gets asked these questions so often. So, here goes…
The Journey
The journey began for us in 2004. At that time there were eight of us who represented the Rocky Mountain Region of a worldwide computer and electronic components distributor. We had one Operations person at the time and the rest of us were equally divided between Technical and Sales roles. We all worked well together. Life was good. However, because of changes on the horizon with the distributor organization, our current CEO proposed the idea of starting our own company. Of course, we all shared the normal concerns one could imagine when contemplating leaving a relatively secure environment and taking on the risk of starting your own thing. But, the vote for starting our own company was unanimous.
There are all kinds of tasks associated with establishing a business and, of course, one of those is figuring out what the company name is going to be. To that end, each of us was asked to put some thought into possible names and come back to the team with ideas. I honestly don’t remember what any of the other names were, including the one I suggested. It was our Network Engineer at the time who came back with Zunesis. And, after he explained how he came to this name, we were all on board.
The name is based on a Greek word, “Sunesis”. If you get on your browser and search this word you’ll find a few different definitions. You’ll see definitions like “a running together”, “a flowing together with…”, “knowledge”, “understanding”, you get the idea. The definition we apply to our company name is:
“multiple sources of knowledge and understanding flowing together
to create something greater than the sum of the parts.”
We believe the name Zunesis reflects a spirit of team work and synergy with our clients, our suppliers and employees. So, you may be thinking, “alright, but why the “Z”? Well, at the time, if you Googled Zunesis, we were the only reference that would come back. I just Googled the name while writing this post and we are STILL the only reference that pops up.
Our Logo
 As an aside, have you ever looked closely at our logo? When you do, you’ll see that it is a Zebra. And, on even closer examination, you’ll notice that one of the stripes is Blue. The Zebra’s single blue stripe demonstrates that the answers to our customer’s IT challenges are not always black and white. We at Zunesis offer more than a product. We are here to teach, facilitate, validate, and guide our clients toward the optimum solution for their business. Zunesis understands that every IT solution is unique, just like our zebra.
As an aside, have you ever looked closely at our logo? When you do, you’ll see that it is a Zebra. And, on even closer examination, you’ll notice that one of the stripes is Blue. The Zebra’s single blue stripe demonstrates that the answers to our customer’s IT challenges are not always black and white. We at Zunesis offer more than a product. We are here to teach, facilitate, validate, and guide our clients toward the optimum solution for their business. Zunesis understands that every IT solution is unique, just like our zebra.
So, now you know the meaning behind our name AND, even though you didn’t ask, you have the story behind our logo too.




