Though not a new phenomenon, ransomware has made some serious headlines this week.
With the recent wave of Ransomware attacks, it is becoming increasingly important for organizations to protect themselves and their sensitive data.
There are different types of ransomware. They can target any PC users – whether it’s a home computer, endpoints in an enterprise network, or servers used by a government agency or healthcare provider.
Ransomware can:
- Prevent you from accessing Windows,
- Encrypt files so you can’t use them,
- Stop certain apps from running (like your web browser).
Ransomware will demand that you pay money (a “ransom”) to get access to your PC or files. However, there is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.
Microsoft provides a complete portfolio of Cloud services to protect your data from these types of attacks. One of our specialties is helping customers transition from on premise to either hybrid or full cloud environments. Often, customers just do not know where to start. We have a complimentary assessment that can establish the basics called a “Cloud Migration Health Check,” by which we can provide you with a report outlining current on premises investments compared to what those same investments would cost in the cloud, highlighting cost savings in the process.
In light of this week’s events, (WannaCry), would it be worth a few minutes of your time to review your current environment and projects to see if Microsoft Cloud and Microsoft Office 365 & Azure would be a good fit for your organization?
Please contact us to learn more on how Microsoft dedicated Office 365 and Azure: Storage, Backup, and Disaster Recovery solutions can help optimize and protect your IT investments.
Studies show that employees are increasingly using their personal devices for more than personal use.
- 66% of employees use personal devices for work purposes.
- 52% of information workers across 17 countries report using three or more devices for work.
- 90% of enterprises will have two or more mobile operating systems to support in 2017.
- 80% of employees admit to using non-approved SaaS applications in their jobs.
So, how do we keep all of these devices secure when they’re working with corporate information?
When you combine Office 365 with the Enterprise Mobility Suite, you give employees the freedom to work securely from virtually anywhere, on any device, with the gold standard of productivity tools: O365.
- Enhance employee productivity in the office or on the road with reliable access to mobile apps, tools, and data.
- Keep sensitive data protected without the need for complex security configurations.
- Seamlessly manage employee devices, apps, and data through one simple IT admin portal.
- Give remote workers access to the familiar Office apps and productivity tools they love.
Maximize productivity with the combined benefits of Microsoft Enterprise Mobility Suite + Office 365
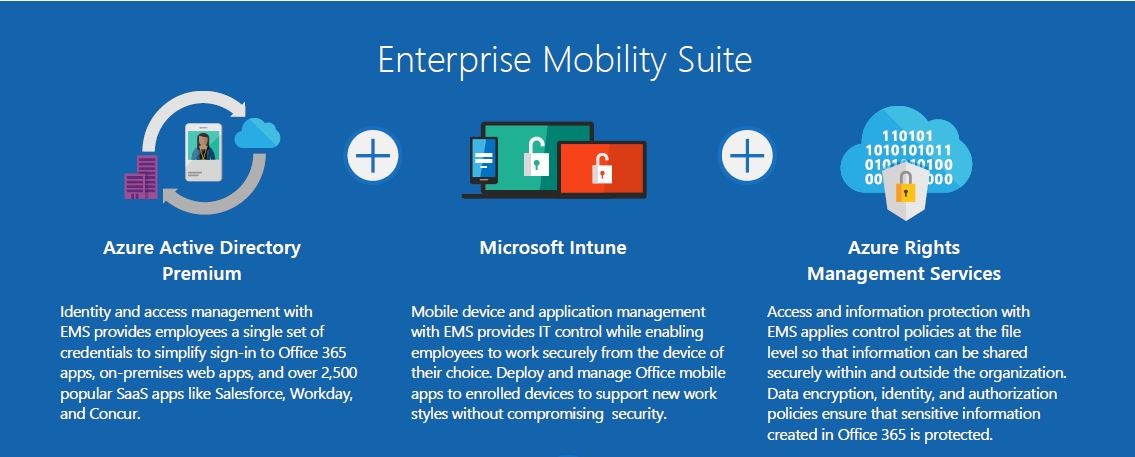
 The Enterprise Mobility Suite (EMS) is the only comprehensive cloud solution that can manage identities, devices, apps, and data. EMS includes three products: Microsoft Azure Active Directory Premium, Microsoft Intune, and Microsoft Azure Rights Management Services.
The Enterprise Mobility Suite (EMS) is the only comprehensive cloud solution that can manage identities, devices, apps, and data. EMS includes three products: Microsoft Azure Active Directory Premium, Microsoft Intune, and Microsoft Azure Rights Management Services.
Office 365 is a cloud-based service that provides users with access to industry-standard Office productivity apps like Word, PowerPoint, Excel, Publisher, and Outlook from any location with a secure internet connection. Office 365 is designed for employees who want the flexibility to take their work with them, wherever they go, without sacrificing the user experience.
Together, the EMS + Office 365 suite offers a complete managed mobile productivity solution that enables your users with the gold standard of productivity and deeply integrated protection for company data.
Synchronized identity management
Improve employee productivity with single sign-on to Office mobile apps, over 2,500 popular SaaS apps, and on-premises web apps. Enable self-service options to allow users to manage groups, passwords, devices, and apps, reducing the need for IT troubleshooting assistance. Now your employees have access to the information, tools, and intuitive Office 365 apps they need, whenever they need it.
Mobile app and device management
Empower BYOD with secure device management that ensures even personal devices are protected and compliant. Deploy the Office mobile apps so that every enrolled device becomes a powerful work tool. Now your employees can work with the Office 365 apps they know, from the devices they love.
Help protect sensitive information
Protect corporate data by allowing more secure access to company resources and enable safe sharing of sensitive information inside and outside of your organization. Easily apply encryption policies at the file level that follow the file within your organization and outside of your organization. Now your data is protected anywhere—even on the go.
Key Business Benefits of Enterprise Mobility Suite + Microsoft Office 365
- Give employees the best productivity experience wherever they happen to be working.
- Unburden your IT department by eliminating typical incompatibility and user experience issues with a simplified user management system.
- Increase business agility by sharing data securely with intended recipients, and completely on your own terms.
Composable
Have you heard the term “composable infrastructure” and aren’t really sure what it is? You’re not alone. There’s a lot of confusion out there about infrastructures of all types, from converged to hyper converged and now composable, so we understand the confusion. First, let’s talk about three types of infrastructures to give you a bit more background:
- Converged Infrastructure. This is a hardware-focused, static (aka it doesn’t change) infrastructure that supports both private and cloud environments.
- Hyper Converged Infrastructure (HCI). In an HCI environment, the infrastructure is software-defined instead of hardware-focused like a converged infrastructure. All of the various technologies (compute, storage, networking, and virtualization) are integrated together into a hardware box from a single vendor.
- Composable Infrastructure. Here, nothing is static. It consists of compute, fabric, and storage modules that you can access and use as you need them.
The main differentiator for a composable infrastructure, specifically one from Hewlett Packard Enterprise, is that it’s completely programmable and software-defined. This means that you can access your composable infrastructure to configure and reconfigure all of the resources—compute, fabric, and storage—for whatever your particular workflow needs are at that moment. Composable infrastructure is hallmarked by these three differentiators:
- Fluid Pool of Resources. Your compute, storage, and fabric resources are pooled together and provisioned to use at will.
- Software-Defined Intelligence. This is where you define the resources you need and manage the resource lifecycle.
- Unified API. The HPE OneView is a programmable interface that you use to set everything up through just one line of code.
Synergy
For composable infrastructure, we work with HPE Synergy. Maybe you’ve heard of that, too, and aren’t sure what it’s all about? Let’s dig in.
Consider this: You need to test something, and in order to do that, you need resources. So, to deploy those necessary resources, you would go to the Synergy template and request the exact resources you need in the form of an infrastructure. Synergy then quickly gets to work to compose the exact infrastructure you need from the pool of resources. When you’re done with what you’re working on, you then go back into Synergy and release those resources back into the pool for others to use.
Now that you know more about it, contact us to learn how we can help you make the move to composable infrastructure.
Examples of Software Asset Management in action.
Example:
What has been common practice, for as long as licensing vehicles have been around, has been a licensing model tied to discount levels via volume purchasing. The more you buy, the more you save. In most cases, from a purely discount perspective, it’s tough to argue getting the heaviest discount up front. However, upon further review, often the volume license vehicle in question may have clients commit to purchasing products they don’t need.
It’s generally safe to assume, for the most part, most knowledge workers regularly use e-mail. And probably Word Processing. But what about presentation software, or diagram software? Perhaps database software? As we move through the list, consumption begins to wean. As a common practice, many publishers will bundle these products; however, not every user will actually utilize all of these products.
What does this mean for a company’s bottom line? How does this impact budget?
Enter SAM:
SAM takes a look at not only what was purchased but also whether or not the product has been used. If it has been used, how frequently?
Why is this important?
 Say you have a large yearly payment via a structured licensing agreement (True Up or Annual Payment). Or, perhaps, you’ve already made the investment and are looking to renew the agreement maintenance; and after implementing a SAM program, you discover that no more than 10% of the overall TOTAL suite of products purchased have been consumed. In this case, the product suite is $300 per user X 250 users = $75,000. This means dollars have been lost in the investment. In other words, the client has invested $75K; however, they have only consumed $7,500.
Say you have a large yearly payment via a structured licensing agreement (True Up or Annual Payment). Or, perhaps, you’ve already made the investment and are looking to renew the agreement maintenance; and after implementing a SAM program, you discover that no more than 10% of the overall TOTAL suite of products purchased have been consumed. In this case, the product suite is $300 per user X 250 users = $75,000. This means dollars have been lost in the investment. In other words, the client has invested $75K; however, they have only consumed $7,500.
The challenge here is that often licensing is an all up-front investment, and it doesn’t matter whether the product ends up getting used or not. Often this is case. Businesses make the move to dive deep into an agreement to establish discount levels; however, they rarely consume more than a fraction of the product.
What are the alternatives?
Driving Business Value Through Proper Spending
One could, via a solid SAM program, identify software utilization – whether or not an end user is using a product, and if so, how often?
You almost need to re-calibrate your thinking around software consumption. A similar example would be if you were to enter a 3-year car lease; and out of the 3 years, you only use the vehicle a total of 1.5 years. That means you will have paid for a 3-year consumption of the vehicle, regardless of the fact that you didn’t get 3 years of value out of it.
The beauty of SAM is that it provides the data to support consumption behavior as well as the ability to quickly address software non-compliance, and this equals dollars saved on pending software investments. The intelligence you can bring to the negotiating table when renewing a maintenance agreement by understanding exactly what your organization actually needs is a powerful tool to drive value for your business.
Proving that your users only utilize 3 out of the 10 products in a suite allows for greater reduction in unnecessary spending. Why buy what you don’t use? Perhaps this means you buy ala-carte vs. a bundled suite for the 75% of your end-user population who don’t need all the bells and whistles.
The bottom line is that SAM from Microsoft reveals these insights and can drive cost savings in significant way. This means truly paying for what you are using.
Driving Business Value Through Compliance
For those concerned with compliance, having the insight to determine whether or not an organization is under-licensed means limited negative exposure through legal action and/or fines and penalties.
 As an example, I recall a large government entity that recently paid $1.2M in non-compliance penalties back to the software manufacturer. Let me say that again: $1.2 million!
As an example, I recall a large government entity that recently paid $1.2M in non-compliance penalties back to the software manufacturer. Let me say that again: $1.2 million!
Not only was the entity liable to pay the fines, they also needed to true-up and get current on their licensing. This government agency made front page news via the city paper for this catastrophe – and it turns out that not all press is good press. In addition to the dollars spent in penalties and fines, along with the cost of getting current with compliance, the repercussion both internally and externally was disastrous.
The reality is, this story has become an everyday occurrence; and it is becoming increasingly more commonplace throughout IT. However, this situation, as well as other non-compliance situations, could have been avoided with the utilization of a SAM discipline.
These are just a few of the many challenges relieved by SAM. Whether it’s overcoming high dollar renewals, protecting against non-compliance, or revealing usage behaviors to support key buying decisions, there is an important place for Software Asset Management in every organization. As recognized SAM experts, let the Zunesis team help you define where this will be of the most use to you; and you might even be surprised at all of the ways it applies within your business.
By definition, Software Asset Management (SAM) is a business practice that involves managing and optimizing the purchase, deployment, maintenance, utilization, and disposal of software applications within an organization.
To many of our customers, SAM is associated with software compliance, software audits, risk mitigation, risk analysis, and cost savings. All of these ring true.
My experience with SAM as a discipline spans all types of businesses, whether SMB, Corporate, Enterprise, all the way up to Government and Education. SAM, whether we realize it or not, truly is a subject that affects nearly all organizations at some point in time.
 If you’ve ever been faced with a Software audit, or have been tapped on the shoulder for a “voluntary” compliance check by a Software Manufacturer, SAM is typically the discipline utilized to come the rescue.
If you’ve ever been faced with a Software audit, or have been tapped on the shoulder for a “voluntary” compliance check by a Software Manufacturer, SAM is typically the discipline utilized to come the rescue.
Over the course of my 18 years in IT, SAM has been one of the top growth areas across the software segment.
Whether a small-mid sized or large enterprise, the risks and impact to the organization remain the same. Organizations who are found out of compliance can expect to be dealt heavy fines, whether from the BSA (Business Software Alliance) or the software manufacturer; negative internal & external exposure (especially for state/local government and publicly traded organizations); and in many cases I’ve seen, a loss in employment to those directly in charge of managing the software assets in question.
So, yes, SAM is a critical discipline. When we talk about SAM, as a starting point, we consider the following:
- Title
- Version number
- What licensing considerations apply (by user/device/processor/core/etc.)
- Whether or not the license is covered via maintenance
What we understand about SAM goes far beyond being under-licensed. I’ve seen many cases where legacy buying behaviors often reveal over-licensing. By understanding what you’ve purchased, whether or not it’s used, and how often it’s used, we create a business case for future purchases – Or sometimes the opposite: the case to support a NON purchase event.
Zunesis recognized by CRN as a top IT solution provider with deep technical expertise and premier certifications for the eighth consecutive year.
Denver, CO (PRWEB) March 27, 2017
Zunesis announced today that CRN®, a brand of The Channel Company, has named Zunesis to the 2017 Tech Elite 250 list. This annual list honors an exclusive group of North American IT solution providers that have earned the highest number of advanced technical certifications from leading technology vendors, scaled to their company size. The 2017 recognition marks the eighth consecutive year that Zunesis has earned this award.
To compile the annual list, The Channel Company’s research group and CRN editors work together to identify the most customer-beneficial technical certifications in the North American IT channel. Solution providers that have obtained these elite designations— which enable them to deliver premium products, services and customer support—are then selected from a pool of online applicants.
![]() Zunesis is a very deserving recipient of this award because they place a significant emphasis on technical expertise and certifications. Over the thirteen years that the company has been in business, they have sought to hire, retain, and equip only the best solution architects who can bring the highest value to their clients. It is this deep commitment to extensive technical knowledge that often sets Zunesis apart from their peers.
Zunesis is a very deserving recipient of this award because they place a significant emphasis on technical expertise and certifications. Over the thirteen years that the company has been in business, they have sought to hire, retain, and equip only the best solution architects who can bring the highest value to their clients. It is this deep commitment to extensive technical knowledge that often sets Zunesis apart from their peers.
“This exclusive, ambitious group of solution providers boasts some of the most advanced IT certifications available from top technology suppliers,” said Robert Faletra, CEO, The Channel Company. “They have adapted impressively to major changes in the IT channel, especially the shift to a more services-driven market, by expanding their skill sets and sharpening both their technical and customer service expertise. Congratulations to our 2017 list, whose robust investment in their organizations has earned them yet another elite designation—the CRN Tech Elite 250.”
“I could not be more proud of our team for achieving this award again this year,” commented Zunesis CEO, Steve Shaffer. “Our solution architects work very diligently to stay on top of, and even ahead of, what is happening in the technology space. Because of their commitment and dedication to be the best at what they do, Zunesis is able to offer top-tier services to our customers.”
Coverage of the Tech Elite 250 will be featured in the April issue of CRN, and online at http://www.crn.com/techelite250.
About Zunesis
Zunesis is a leading IT solution provider with locations in Colorado and Nevada. Our vision centers around an intense focus on serving our customers and bringing value to their business through strategic IT solutions. In 2015 and again in 2016, Zunesis was added to the CRN Next-Gen 250 list, recognizing them for their innovation and forward-thinking in the industry. As of March 2017, Zunesis has been named to the CRN TechElite 250 for 8 consecutive years as a best-of-breed solution provider with deep technical expertise and premier certifications. For more information, visit the Zunesis Blog, or follow us on LinkedIn.
About The Channel Company
The Channel Company enables breakthrough IT channel performance with our dominant media, engaging events, expert consulting and education, and innovative marketing services and platforms. As the channel catalyst, we connect and empower technology suppliers, solution providers and end users. Backed by more than 30 years of unequaled channel experience, we draw from our deep knowledge to envision innovative new solutions for ever-evolving challenges in the technology marketplace. http://www.thechannelco.com.
Copyright ©2017. The Channel Company, LLC. CRN is a registered trademark of The Channel Company, LLC. All rights reserved.
The Evolution of Software Asset Management
 Years ago, Software Asset Management (SAM) was a novelty, as there was very limited visibility around the benefits SAM brought to clients. Probably the easiest way to capture this scenario was almost like selling a bike without a helmet. The client would begin their journey via the licensing vehicle. However, when they ran into a bump in the road, severe trauma was likely. SAM was the helmet – the way to protect clients from said trauma.
Years ago, Software Asset Management (SAM) was a novelty, as there was very limited visibility around the benefits SAM brought to clients. Probably the easiest way to capture this scenario was almost like selling a bike without a helmet. The client would begin their journey via the licensing vehicle. However, when they ran into a bump in the road, severe trauma was likely. SAM was the helmet – the way to protect clients from said trauma.
Before too long, Microsoft, in addition to many Tier 1 Software Vendors, announced mandatory audits for ALL customers. What this meant was if you invested in licensing, you were subject to an audit at any given time by a vendor. I recall these early years as there was a significant spike in partners who obtained proficiency in the SAM discipline.
Today, Software Asset Management is as relevant as it ever has been. Many clients have either gone down the path of an audit; know someone who has; or are uncertain, when the audit does come, whether they will be in compliance.
Non-compliance comes at a high cost:
- Hefty legal fines via the BSA/Vendor,
- Negative internal exposure at an organization,
- Negative public exposure (diminished shareholder value),
- These are just a few. Trust me, there are more.
Thoroughly understanding what’s at stake is why Zunesis incorporates SAM Disciplines during each licensing engagement. Quite simply, it’s ensuring that our clients’ investments in licensing are fully optimized. Whether it means we identify scenarios in which a client is over licensed and can eliminate the need to invest further, under licensed and needs help producing a strategy to address the gap, or ensuring that every license corresponds with the right amount of usage (specific to an end user role or department), are some of the ways we optimize IT investments and shield customers from the effects of non-compliance.
Deploying an enterprise wireless solution can be a challenging task,
especially for IT administrators tasked with supporting multiple sites. In order to ensure good performance, network administrators would often have to perform a site survey at each location to discover areas of RF coverage and interference, and then manually configure each AP according to the results of this survey.
Static site surveys can help you choose channel and power assignments for AP’s. However, these surveys are often time-consuming and expensive, and they only reflect the state of the network at a single point in time. RF environments are always changing, and new sources of interference pop up all the time – whether it’s the microwave in the break room that only gets used around lunch time or a new tenant down the hall who put in a new access point. If your wireless solution is not able to adapt to these changes on the fly, then users will have a poor experience. This means your IT department will experience higher call volumes.
Aruba Networks has developed a feature within their operating system to address these ever-changing wireless environments: Adaptive Radio Management (ARM).
ARM maximizes WLAN performance even in the highest traffic networks by dynamically and intelligently choosing the best 802.11 wireless channel and transmit power for each Aruba Access Point in its current RF environment. ARM solves wireless networking challenges such as large deployments, dense deployments, and installations that must support VoIP or mobile users.
 Deployments with dozens of users per access point can cause network contention and interference, but ARM dynamically monitors and adjusts the network to ensure that all users are allowed ready access. ARM provides the best voice call quality with voice-aware spectrum scanning and call admission control.
Deployments with dozens of users per access point can cause network contention and interference, but ARM dynamically monitors and adjusts the network to ensure that all users are allowed ready access. ARM provides the best voice call quality with voice-aware spectrum scanning and call admission control.
When ARM is enabled it will continuously scan the air on all 802.11 channels and report back what it sees to the controller. You can retrieve this information from the controller or push the data to Airwave to get a quick health check of your WLAN deployment. You can do all of this without having to walk around every part of a building with a network analyzer tool.
In addition to all this, there are some exciting changes coming to the ARM technology and the Aruba Operating System in general with the 8.0 update, make sure you engage your local Aruba resources for more information.
Securing productivity, collaboration and enterprise data is critically important as organizations digitally transform. Microsoft is committed to delivering a new approach to secure this transition, as evidenced with the announcement of their new Secure Productive Enterprise offering.
Microsoft Enterprise Mobility Suite (EMS) provides an identity-driven security solution that offers a holistic approach to the security challenges in this mobile-first, cloud-first era. Microsoft technologies not only help you protect your organization but also identify breaches before they cause damage.
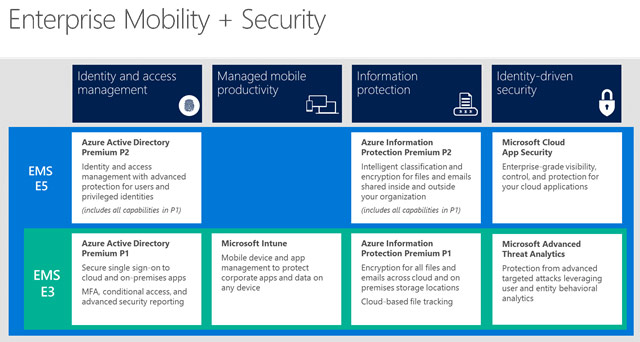
Protect at the “front door”
A solution starts with identity protection capabilities to secure access at the “front door” of your company’s apps and data. Azure Active Directory Identity Protection leverages billions of signals to provide risk-based conditional access to your applications and critical company data, including the option of multi-factor authentication. Microsoft also helps you manage and protect privileged accounts with Azure Active Directory Privileged Identity Management so you can discover, restrict and monitor privileged identities and their access to resources.
Protect your data from user mistakes
Microsoft provides deep visibility into user and data activity, so you can protect your company when users make poor choices as they work with critical company data. Microsoft Cloud App Security provides visibility and controls for cloud apps, including popular SaaS apps like Box, Salesforce, ServiceNow, and, of course, Office 365. With the new Azure Information Protection, Microsoft brings together classification and labeling with persistent data protection to enable secure file sharing, internally and externally. Finally, Microsoft Intune Mobile App Management (MAM) helps you prevent data loss on mobile devices, with the unique ability to manage the Office mobile apps without requiring device enrollment.
Detect attacks before they cause damage
As more organizations move to an assume breach posture, Microsoft EMS identifies attackers in your organization using innovative behavioral analytics and anomaly detection technologies―on-premises with Microsoft Advanced Threat Analytics and in the cloud with Azure Active Directory and Cloud App Security. Threat intelligence is enhanced with the Microsoft Intelligent Security Graph driven by vast datasets and machine learning in the cloud.
In just two years, EMS has grown to lead the market with over 27,000 enterprise customers and more than 1/3 of the Fortune 500 now onboard. Contact Zunesis to find out how your organization can benefit from Microsoft Azure and Microsoft Enterprise Mobility + Security (EMS).
Ocean waters are warming and becoming more acidic, ice caps are melting, and sea levels are rising. Warmer global temperatures affect our water supplies, agriculture, power and transportation systems, the natural environment, and even our own health and safety.
Multiple studies published in peer-reviewed scientific journals show that 97 percent or more of actively publishing climate scientists agree 1: Climate-warming trends over the past century are mostly due to human activities.
While technology has played its part in causing climate change it can also help us get to solutions. Here are five initiatives taking place in the technology community that can fight climate change:
 1. Data centers
1. Data centers
The world’s most influential companies including Apple, NIKE, IKEA, Johnson & Johnson, and Starbucks, representing over US $1 trillion in annual revenue, are committed to 100% renewable power. Much of the energy used in data centers is not from the actual technology. Instead, it’s from cooling the servers. As well as delivering on emission reduction goals, renewable power can help manage fluctuating energy costs, improve reputation and provide energy security. It also shows business leadership on climate change. This could have massive impact if paired alongside robust government policy that boosts confidence and enables long-term investments.
2. Mobile apps
It takes some digging to find apps that will help you create real change on a daily basis, but they’re out there. Here are some examples of apps that can help you monitor and reduce your carbon footprint and waste:
-
- Oroeco is an app that tracks your carbon footprint by placing a carbon value on everything you buy, eat, and do, and then shows you how you compare with your neighbors.
- PaperKarma is an easy way to cut paper waste. Take a photo of your junk mail, send it through the app, and PaperKarma will figure out what it is and take you off the mailing list.
- GiveO2 tracks your carbon footprint as you travel. Turn on the tracker when you start a new trip, and it will automatically calculate a timeline of your carbon usage. At the end, you can “offset” it by supporting a sustainable project of your choice.
 3. IoT
3. IoT
Monitoring our energy usage makes it possible to be smarter about it. Take Nest, for instance. While an un-programmed thermostat can waste 20% of heating and cooling, Nest tackles the issue with a smart thermostat that learns your patterns and automatically adjusts to save energy. The Internet of Things can save energy and carbon footprints with things as simple as using an app to turn off the lights or with apps like IFTTT, which hooks up to many different types of systems. The IoT can also involve monitoring your sprinkler system to save water, or use sensors to tell you to take a different route when driving to avoid idling in traffic and wasting gas.
4. Open source movement
Open data and open source technologies are a huge way to accelerate environmental research and innovation. Take Tesla, for example. By opening the company’s patents to everyone, Elon Musk wanted to make sure electric vehicles succeeded faster.
5. Mapping
Interactive maps really drive home the point of climate change and can lead the way to remedies. Map layers defining vegetation, soil type, geology, precipitation, and human infrastructure can help model and plan for future change. New mapping technology can make us safer and less reliant on fossil fuels. The U.S Geologic Survey’s 3D Elevation Program is being developed to use advanced mapping to better update hazard maps for floods and earthquakes and find out where the best areas for solar and wind farms.
As you can see, many of these things only require small changes from individuals in order to make a difference for our climate. Some will require much more intentional decisions from businesses. The good news, however, is that with this intentionality, individuals and corporations alike can take action to help our climate. If we’re all in this together, perhaps it’s time that we take a look – individually and corporately – at how we can make a difference.
1. J. Cook, et al, “Consensus on consensus: a synthesis of consensus estimates on human-caused global warming,” Environmental Research Letters Vol. 11 No. 4, (13 April 2016); DOI:10.1088/1748-9326/11/4/048002




