An Ounce of Prevention is Worth a Pound of Cure: Ransomware Prevention

As we approach day [xyz] of the plague, I was ready to write another blog post about COVID-19 and technology. It seems that all we can think about lately is the virus. Working from home with three kids under 10 years old certainly has been “fun” for me. I’ll definitely be glad once this thing is gone.
Ransomware Uptick
Instead, I’d like to take some time to talk about ransomware. Another currently rampant plague of the digital variety. Among malware, ransomware is some of the absolute worst of the worst. It certainly has it’s own place in H-E double hockey sticks.
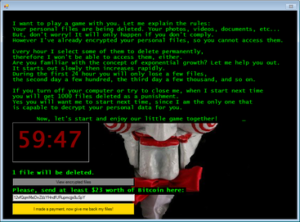
At a time where people and businesses are already suffering, we are seeing an uptick in ransomware attacks. Encryption of your files occurs, and cyber criminals demand a ransom in order to decrypt them. Often times, organizations use military grade encryption. So, the only way to decrypt the files is to pay the ransom.
Since only the criminals have the required decryption keys, it would be nearly impossible to decrypt even with your handy dandy cereal box decoder ring. Unfortunately, paying the ransom is a risky proposition. There is no guarantee that your files will be decrypted. This also validates the cyber criminal business model and encourages bad actors.
Ransomware spreads like fire, and burns the building to the ground if you don’t prepare.
How to deal with ransomware
BACKUP
First of all, you REALLY should have good backups. This doesn’t prevent the ransomware attack, but it certainly prevents you from needing to either a)open up your wallet or b)lose important data.
You might be surprised how many of us don’t follow rule #1 for data. Backups should be available locally, as well as off-site/cloud. You should also make sure that you can restore multiple points in time. This is in case your more recent backups contain ransomware. This isn’t just best practice for ransomware, it is just good practice in general.
Whether it comes in the form of ransomware, hard drive failure, data corruption, or space aliens shooting lasers at your PC, you really should have a plan for your data. How much is your data worth to you? For the ransomware event, skip the heartburn and restore from backup prior to an attack.
Prevent ransomware with good personal cyber hygiene
Be proactive with cyber security. Here are some suggestions:
- Rule #1 – Take regular backups
- Rule #2 – Take regular backups
- Rule #3 – Make sure your backups are good, and validate that you can restore from them.
- THINK BEFORE YOU CLICK
- Make sure that you are using reputable antivirus and malware protection to stop most threats.
- Stop believing that your AV/Malware prevention suite will stop 100% of attacks, zero day exploits will keep coming.
- Do not open files from people that you do not know, or click on random email links from your “bank” asking you to “update” your information.
- Have a good firewall, network segmentation, SPAM filter, etc.
- Don’t re-use the same few passwords for EVERYTHING. Do not use the same password with 1,2,3,etc., to get around password complexity requirements not allowing you to re-use your password.
- Use multi factor authentication where possible.
- Make sure that you are updating your operating system regularly.
- Security patches don’t work if you don’t install them.
What to do if you get hit with Ransomware
Hopefully this will always be theoretical, and you never get hit. First of all, you definitely want to isolate the machine. This stuff will scan your ARP tables, your registry, and a variety of other sources to look for other hosts to infect. I’d say immediately power off, enter the nuclear codes, and kill it with fire. In other words, wipe/erase the machine. You can then move forward with rebuilding the OS and restoring your data once you’ve got a blank canvas. Just because your security scan came up clean does not 100% guarantee a malware free result.
Next, if there are other machines on the network, quarantine and examine them. Ransomware will proactively work to infect everything else it can on the network. If other machines are impacted, they should also be nuked and rebuilt. This includes your business critical servers. Actually, this is especially critical for business critical systems. These systems house critical data, and are often a central point of access(points of infection) by many users. YES, THIS IS PAINFUL. However, if you have good backups to restore from, it isn’t nearly as big of a deal.
Are you prepared?
Much like the human pandemic that we are all too familiar with, hopefully you are “distancing” yourself from the digital pandemic. The best way to beat a ransomware attack is prevention, not reaction after the fact when it’s too late. If you need help preparing, or even just a second set of eyes to review your existing strategy, please contact us for an assessment. We are here to help.
Categories
Search
Blog Categories
Related Resources
Archives
- July 2024
- June 2024
- May 2024
- April 2024
- March 2024
- January 2024
- October 2023
- September 2023
- August 2023
- July 2023
- June 2023
- May 2023
- April 2023
- March 2023
- February 2023
- January 2023
- October 2022
- July 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- August 2021
- July 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- August 2019
- July 2019
- June 2019
- May 2019
- April 2019
- March 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- May 2018
- April 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- August 2017
- July 2017
- June 2017
- May 2017
- April 2017
- March 2017
- February 2017
- January 2017
- December 2016
- November 2016
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- May 2016
- March 2016
- February 2016
- January 2016
- December 2015
- October 2015
- September 2015
- August 2015
- July 2015
- June 2015
- May 2015
- April 2015
- March 2015
- February 2015
- January 2014
- February 2013




