What’s on Your Mind? 2020 IT Needs
It’s 2020, the holidays are over and you’re back to managing your organization’s IT needs in support of their core initiatives. So, what’s on your mind? For many of our Clients, this can be summed up by three questions:
Are we adequately protected against Ransomware and can we recover from an attack?
Ransomware is a reality for individuals and businesses alike; no person or entity is immune. To someone responsible for protecting an entire organization from a Ransomware attack, the specter is ever-present. One that requires 24/7 vigilance. But these same individuals are keenly aware of that. Despite all their efforts to keep the attack from happening, they may be called upon to recover from an attack. We hear about this topic so much from our Clients that there are two BLOGS on the Zunesis website focusing on it exclusively. I would encourage you to read both Posts.
Mitigating the risks associated with Ransomware attacks requires a diligent adherence to a set of practices that include (but are not limited to):
- Keeping virus protection software up to date to keep up with the changing profiles of Ransomware attacks.
- Staying current with firmware patches on all devices (firewalls, switches, routers, serves, storage, etc.) to make sure your devices have the most recent protections.
- Staying current on Operating System updates and patches to plug security holes as they are identified.
- Managing usernames and passwords and segmenting authentication domains to reduce spread of an attack.
- Locking down non-essential ports to reduce points of entry.
- Segmenting LANs to minimize spread of an attack.
- Training of end-users to help them understand what to look for in emails and other external entry points. End-users are the most common entry point for attacks and the need for constant training cannot be over-emphasized.
If you are compromised, rather than paying a ransom, you’ll want to provide your organization with their best chance for recovery of your data. To accomplish this, you’ll need to spend time reviewing your backup/recovery and disaster recovery plans.
When reviewing your plans look for how they address the following:
- Are the frequency and retention policies designed to give you acceptable RPO and enough granularity to restore data that has not been compromised?
- Do you test your data for potential compromise?
- When looking at your backups, are they isolated from the rest of the network? Is there a possibility of being a target of attack (corruption or deletion)?
- Do you have multiple copies of your backups, on different media, and offsite?
- Does your backup/recovery software have built-in checks for warning of possible compromise?
- Do you have a standard practice of testing recovery of data?
While not exhaustive, the points outlined above, emphasize the multi-faceted approach an Organization needs to take in order to give themselves the best chance of avoiding the consequences of a Ransomware Attack. As I stated earlier in this post, Ransomware is top of mind for all our Clients and we will likely spend a lot of time working with them on this in 2020.
How will we get all our projects accomplished in 2020 and still manage the day-to-day tasks?
The challenge of not having enough resources and time have been a persistent issue in IT. I’ve been working in the industry for over 35 years and it seems there has never been enough money, time, or people to execute on the strategies developed to evolve and maintain the IT needs of an organization. In 2020 that is certainly not going to change.
The fact is, IT will always compete for the resources of the Organization because, for most organizations, their Mission Statement has nothing to do with building a world-class IT infrastructure. However, organizations across industries are more reliant than ever before on technology to carry out their primary Mission. For this reason, there will be an increasing array of projects that ultimately will need to be carried out by IT; the challenge of efficient resource utilization is not going to abate any time soon.
Is our infrastructure ready to support the needs of the Organization in a world where Digital Transformation is a constant, iterative process?
In the next decade, we will no doubt continue to see the evolution of how and where IT resources are utilized. After all, Digital Transformation is a journey, not a destination. More organizations are moving toward becoming Data-Driven, (leveraging Artificial Intelligence and Data Analytics to glean customer insights and make better decisions).
With this move, we will see the proliferation of Edge Computing devices, leveraging of IoT, and Machine Learning. These technologies will push us to adopt different strategies for on-premise and Cloud-based Compute, Network and Storage resources. For some IT organizations this will be a continuation of what they’ve already begun and for others it may mean a complete revamp of their existing infrastructure.
In the midst of protecting your organization from the bad actors, executing on new projects and maintaining the day-to-day tasks that are part of every IT organization, you and your team need to stay up with a constantly evolving industry that presents you with a myriad of options for continuing your Digital Transformation Journey. You can’t ignore the advances in technology, nor the relevance they might have for your organization, but finding the time to understand them and assess their value won’t be easy.
Our Available Services
 Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Of course, there is no one response that can answer any of the topics mentioned above. However, Zunesis has been partnering with our Clients to navigate difficult problems since 2004. As technologies have evolved, so have our abilities to address the needs of our Clients to support their IT Infrastructure, including the issues summarized here.
Whether you just want to sit down and discuss what’s on your mind, or you have already identified an area we can jump in and help, we are ready to engage. Just to give you an idea of what we have to offer, I’ve included a summary of some of the practices we have developed over 15 years to help our Clients achieve their goals.
NOTE: For any service we provide (one-time or ongoing), there is a standard process and set of deliverables we use as a starting template. From there, we will work with you to customize the service based on your specific needs. If there is one thing we know for certain, you have unique circumstances. We want to make sure our services conform to your specific needs.
Here are a few of our standard offerings:
IT Infrastructure Assessment – The objective for this assessment is to provide an analysis of where your infrastructure is today, where you want to see it in the future, and what will be required to bridge the gap.
Typical Tasks and Deliverables include:
- Discovery of Compute, Network, and Storage environment:
- Inventory/document configuration of on-premise equipment.
- Inventory/document applications (on-premise and cloud-based).
- Document hyper-visor and OS configurations.
- Document the types of data stored on-premise and, in the cloud.
- Review Backup/Recovery Infrastructure and policies.
- Review Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
- Produce a roadmap to go from where you are to where you want to be.
BC/DR Assessment – The objective of this assessment is to provide an analysis of your current Backup Recovery and Disaster Recovery architecture and processes. Because Ransomware is such a threat, we will conduct this assessment with a sub-focus on recovery from Ransomware attacks.
Typical Tasks and Deliverables here include:
- Discovery:
- Inventory/document configuration of backup environment.
- Inventory/document configuration of disaster recovery environment.
- Provide documentation on the types of data stored on-premise and in the cloud.
- Document SLA’s associated with applications and data.
- Log your Backup/Recovery policies.
- List details of Disaster Recovery Policies.
- Conduct stakeholder roundtables.
- Produce Logical and Physical Drawings.
- Document of observations.
- Document actionable recommendations.
Recurring Data Center Advisory Service (RDCAS) – The objective of this service is to provide ongoing management of our Clients HPE environment. We monitor their device firmware and configuration. This helps them maintain best practices per HPE documentation. This service is provided over the course of a 12 Month period.
Typical Tasks and Deliverables include:
- Perform an initial inventory of all HPE devices, documenting firmware, configuration, and alerts.
- Monitor Critical Alerts published by HPE throughout the life of the service. Report these to the Client with recommendations for action.
- Monitor all alerts from HPE and report non-critical alerts in a quarterly report.
- Monitor release of new firmware and report to Client on quarterly basis (unless firmware is deemed critical).
- Offer assistance in deployment of firmware if needed.
- Assist in resolution of configuration if it doesn’t meet best practice per HPE documentation.
- Provide assistance in resolution of HPE support tickets as a Client advocate.
- Provide Quarterly environment reviews with Client.
Again, these are just examples of the ways we have helped our Clients address their challenges over the last 15 years. We have a team of technology professionals that are ready to assist you with all your infrastructure needs.
Have a great 2020. We look forward to hearing from you.
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.
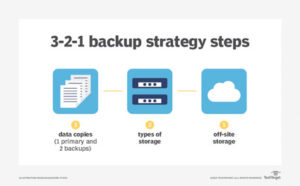
The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
Data Protection
As we get closer to Halloween, I’m sure most IT professionals have a few things that spook them. One of them being – ransomware and securing their data. In fact, it has been reported that new organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021. There will be an estimated $6 trillion in damages to business by 2021.
New organizations will fall victim to ransomware every 14 seconds in 2019 and every 11 seconds in 2021.
As we move to more IoT devices, studies have been found that it takes just 5 minutes to hack into an IoT device.
I could share more stats, but I’m sure you get the point that security of an organization’s data is a big concern now and will be going forward.
So, what can organizations do to help prepare for an attack and save their data? First, let’s talk about what intelligent data protection is and why you need it.
Why Intelligent Data Protection
In today’s digital world, protecting data is becoming more complex every day. More formats, more sources, more access points and longer shelf life for data are just a few of the areas impacting this complexity. Data always needs to be available. Many organizations cannot afford to be off-line.
Intelligent Data Protection is a comprehensive approach to data protection and copy data management that focuses on how the business protects and uses its data (now and in the future).
An organization needs to find the right solution that will integrate the data protection with copy data management technologies with an automated data protection platform.
Benefits to Intelligent Data Protection:
- Eliminates complexity
- Automatically moves data without manual intervention
- Enforces optimal backup policy per data store
- Puts your backup to work
- Protects more data, faster and at a lower cost
- Leverages predictive analytics
- Ensures data recoverability
- Minimizes cost and maximizes investment
- Aligns cost with usage
- Flexible deployment options
Things to consider when Looking for An Intelligent Data Protection Solution
- Self-managing platform- automates data protection infrastructure management
- Delivers on backup and recovery needs: Deliver Recovery Tim Objective (RTO) and Recovery Point Objective (RPO) you need on a per-application basis
- Cloud-Scale infrastructure: manage data growth with scale-out capability and intelligent deduplication
- Threat Mitigation
- Optimizes use of backup copies
- Optimizes cloud investment
- Secures Cloud Backup and Recovery
- Choice of deployment models and pricing
- Support for a hybrid environment
3-2-1 Backup Rule
What may sound like something that you would learn on Sesame Street is the 3-2-1 backup rule. (Imagine the Count counting backups. One backup, two backups, three backups. Ha! Ha! Ha!). The United States Computer Emergency Readiness Team (US-CERT) highly recommends this practice.
This is a common approach to keeping your data safe in almost any failure scenario. The hope is to maximize application uptime and data availability.

The rule is:
- Keep at least 3 copies of your data
- Store 2 backup copies on different storage media
- Have one of them located offsite
How HPE and Veeam Can Help
When looking for an intelligent data protection solution, Veeam and HPE’s industry-leading solutions are fully equipped for businesses of all sizes to combat malicious attacks and protect their data. This solution is a fully integrated solution comprised of existing technology. It enables organizations to rapidly recover from ransomware attacks. It is both flexible and affordable. Another benefit is that it can be quickly deployed and into production.
HPE StoreOnce Catalyst
HPE StoreOnce purpose-built appliance and HPE StoreOnce Catalyst benefit organizations by offering space-efficient backup, deduplication, data lifecycle management and information assurance. The most important benefit of this solution is its ability to isolate data from being tampered unintentionally.
StoreOnce Catalyst does not prevent the rest of the enterprise from being compromised by malware. It does protect the mission-critical data stored from being either targeted or affected. Ransomware cannot encrypt what it does not see. The Catalyst store does not use standard operating system command instructions for its operations so malware cannot become active while inside.
The best backup solution is useless if ransomware can access your backup repositories. StoreOnce Catalyst provides protection for backup repositories. The repository is only visible through the Catalyst API.
Backup Applications: Veeam
Several software vendors have integrated StoreOnce Catalyst technology into their data protection applications. One solution to consider is Veeam Backup and Replication . Veeam has several solutions and applications that can assist with your data protection strategy.
The Veeam Mount Server enables the ability to immediately mount backed up virtual machine files for instant VM recovery and unparalleled RTO efficiency when combined with StoreOnce Catalyst. VMs recovered in this way will be mounted Read-Only by default. This further protects the environment should any malicious software remain within the backup data.
Veeam also offers testing environment where you test and remove ransomware item quickly before restoring VMs to production. This is done with Veeam Data Labs and Veeam SureBackup.
Ask Zunesis about other capabilities that Veeam has to help assess, monitor and more for your data backup needs.
Conclusion
Simply backing up data by making copies is not enough anymore. If an operating system can see your data so can ransomware. Ransomware cannot infect what it cannot see.
By practicing the industry best practices and leveraging the right tools, you can prepare for and avoid potential data loss and downtime from ransomware attacks. Contact Zunesis today for an assessment on your storage and backup plans.
Additional Resources:
Protecting Data from Ransomware with HPE StoreOnce Catalyst
Protect your data from malicious ransomware threats
Veeam Backup and Replication
It never ceases to amaze me. There’re the great big organizations who have million-dollar lobbies and healthy quarterly dividends. The CEO has a jet or six and from the outside looking in, things look like all their ducks are in a row. A facade is misleading. My last date was a facade, but that’s another subject all together. In other words, things are not always what they seem.
A Lack Of Business Continuity
Organizations spend millions and millions on their research & development (as they should), employee retention and many other pertinent tangibles and intangibles. However, I have noticed a significant gap in the investment in their business continuity. They may not even practice business continuity. They pay little or no attention to that gorilla in the room. Also known as a Disaster (Natural or Manual).
Now some of this is due to negligence and some of this is due to that 20-something mentality that one is bullet-proof. The big ‘D’ here is Denial; the fact that it can never happen to us. We’re too big and somebody will know what to do.
Well, that’s not always the case. If a catastrophe does happen (God forbid), an organization needs to have a contingency plan in place. They should also be able to quasi-predict the catastrophe before it actually happens.
The Cost of Downtime
Downtime in an IT infrastructure can cost an organization millions of dollars per every minute the infrastructure is down. That’s why maintenance windows are done at 1 AM and not during peak times. Could you imagine if Amazon went down on Cyber Monday? Yes, it’s an extreme example, but imagine if your organization went down.
Then ask yourself the following questions:
- What would happen?
- Would our clients be adversely affected?
- How much money would you lose?
- How much data would you lose?
- How valuable is that data to your organization?
- How are we going to get it back?
- Who do we call?
The list of questions is infinite. Your organization may not ever be able to be fully down. Imagine if a city’s fire department IT infrastructure went down? It could project total chaos.
Now that I have made my point on the seriousness of an IT infrastructure going down, it’s time to make my other point. That is business continuity.
Business Continuity- What is it?
Wikipedia defines Business Continuity as:
“ The process of creating systems of prevention and recovery to deal with potential threats to a company. In addition to prevention, the goal is to permit ongoing operation, before and during execution of disaster recovery.”
The keywords in that definition is “ongoing operation.” Floods, earthquakes, cyber-attacks, human error can all affect the ‘ongoing operation’ of an organization. Having backups (quite possibly more than one) in place to keep the lights on is vital. This is a worthy investment and by investing in a Disaster Recovery plan may make you cringe, imagine the investment you would have to make if you didn’t.
When did Noah build the ark?
Before the storm….Before the storm….
Zunesis has an IT Health Check service which is quick and not physically painful! Let us come in, understand your infrastructure and help you prevent that 10,000-year flood. Click here for more information!
More and more companies are making the jump to Office 365, moving from their on-premises Exchange, SharePoint, and Skype for Business environments. According to Microsoft, as of October 2017, Office 365 commercial monthly active users was at 120 million, up 20 million from April of 2017. Microsoft expects to have two-thirds of its Office business customers in the cloud by some time in its fiscal 2019.
For the sake of this article, lets focus just on the Exchange Online (or email) service of Office 365.
When implementing Exchange server on-premises, would you include an enterprise backup/restore solution? Of course, you would. In fact, there might be several data protection/high availability strategies you would employ to the environment. Exchange database backup and recovery, single item recovery, Database Availability Group (DAG), business resumption and disaster recovery to name a few.
Let’s take a look at a few of these strategies which are included in Exchange Online natively.
Exchange Online provides Mailbox Replication at Data Centers for high availability of the Exchange database. Exchange Online mailboxes are continually replicated to multiple database copies, in geographically dispersed Microsoft data centers. This provides data restoration capability in the event of site or hardware failure.
Recoverable Items folders are available at both the mailbox and item level.
Deleted Mailbox Recovery – When a mailbox is deleted, Exchange Online retains the mailbox and its contents for 30 days by default. After 30 days, the mailbox is not recoverable. A recovered mailbox contains all of the data stored in it at the time it was deleted. Administrators can recover a deleted mailbox within the retention period setting.
Deleted Item Recovery – Exchange Online enables users to restore items they have deleted from any email folder, including the Deleted Items folder. When an item is deleted, it’s kept in a user’s Deleted Items folder. It remains there until it’s either manually removed by the user or automatically removed by retention policies. After an item is removed from the Deleted Items folder, it’s kept in a Recoverable Items folder for an additional 14 days before being permanently removed (administrators can increase this to a maximum of 30 days).
A user is still in control of the data, i.e. they have the ability to purge their own Recoverable Items folder at any time. Microsoft’s answer to this is Litigation Hold, which copies all mailbox items to an immutable area (hidden from Recoverable Items). The items remain there in an unchanged state until the Litigation Hold age is reached, or in the case where that age is set to indefinite, till the administrator says so.
While these are all great features built-in to Exchange Online, what happens when data loss occurs due to user error, hacking, or malicious acts? There is not a complete backup and restore solution provided by Microsoft for Exchange Online, or Office 365 for that fact. Again, these strategies above will not protect users from data loss. Microsoft puts many safeguards in place so that customers do not lose data, however, they do not specialize in data backup and recovery.
Microsoft published a white paper in April 2017 called Shared Responsibilities for Cloud Computing. Here are a few of the findings from the white paper.
“As organizations consider and evaluate public cloud services, it is essential to explore how different cloud service models will affect cost, ease of use, privacy, security and compliance. It is equally important that customers consider how security and compliance are managed by the cloud solution provider (CSP) who will enable a safe computing solution. In addition, many organizations that consider public cloud computing mistakenly assume that after moving to the cloud their role in securing their data shifts most security and compliance responsibilities to the CSP. “
“Cloud providers by design should provide security for certain elements, such as the physical infrastructure and network elements, but customers must be aware of their own responsibilities. CSPs may provide services to help protect data, but customers must also understand their role in protecting the security and privacy of their data.”
The following table is featured in this white paper which shows the shared responsibilities for different cloud service models:
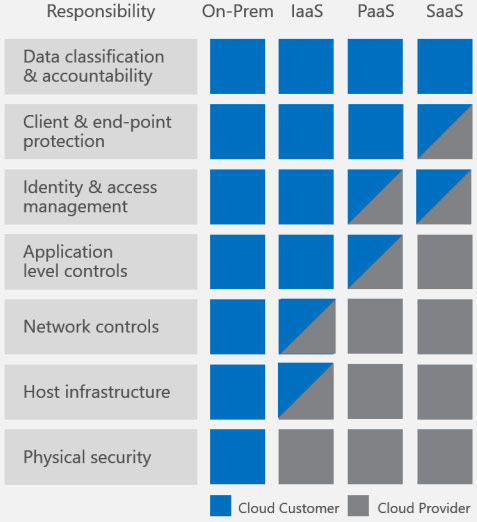
Microsoft has defined the responsibilities of the provider and the customer. Office 365 falls under IaaS (Infrastructure as a Service). Data protection would fall under the Data classification and accountability responsibility. The majority of customers assume that Microsoft is backing up their data. However, just like Exchange on-premises, there is no backup or restore built-in. Microsoft clearly puts the issue of data protection squarely on the customer.
So, what is a customer to do?
Luckily, most of the enterprise backup software providers have compatibility for Office 365. There are also several vendors who make backup and restore specifically for Office 365 which can be found in the Azure Marketplace that provide a wide array of features, such as where to store the backups (cloud vs. on-premises), archive solutions, and single-mailbox recovery.
In conclusion, Microsoft has explicitly stated in their Shared Responsibility for Cloud Computing white paper that they are responsible for keeping the cloud services available, which does not include traditional backup and recovery of the data. Don’t make the same assumption many Office 365 customers have. Treat Office 365 data like any other data; it needs to be backed up.
Data Loss is Increasing and It’s Costly
In today’s digitally active world, small businesses cannot afford to lose their data even for a short amount of time. According to research by Security Week, the total volume of data loss at an enterprise level has increased more than 400% over the past couple years. IT Web suggests that the total cost of data breaches will be more than $2.1 trillion by 2019.
A recent Verizon report found that small data breaches- those with fewer than 100 files — cost a company between $18,120 and $35, 730. Another scary statistic is that more than 90% of companies that experience at least seven days of data center down time will typically go out of business within one year.
Whether the loss of data is due to natural disaster, human error, a cyber attack or hardware failure, data loss is very risky and very expensive. That’s why now more than ever, companies need to invest time and money in a backup and discovery recovery solution to help give peace of mind and minimize costs.
Smaller businesses are actually exposed to a great amount of risk since cyber criminals know they are easy targets since many of them do not take the time or have the internal resources to guard against it. A few days of downtime for a small business can be detrimental to a business surviving.
Here are just a few more stats pulled from an article on LinkedIn in 2016 on how data loss and business continuity in the wake of disasters are highly applicable to both single location businesses storing data onsite and multi-location businesses storing data in a single cloud.
- 86% of server workloads are forecast to be virtualized by 2016 (2014-15 Virtual Server Backup Software Buyer Guide)
- The number one IT priority for mid-market organizations over the next 12 months is to improve data backup and recovery. (ESG Lab Review: Data Protection, Recovery and Business Continuity with SIRIS 2 from Datto)
- 96% of all business workstations are not being backed up (Contingency Planning and Strategic Research Corporation)
- 58% of downtime incidents are caused by human error alone. Natural disaster account for only 10% of downtime(Enterprise and the Cost of Downtime, Independent Oracle User Group, 2012)
- 35% of servers have a downtime tolerance of 15 minutes or less (ESG Research: BC/DR Survey Final Results, Enterprise Strategy Group, 2015)
- The leading cause of incidents and outages is hardware failure/server room failures. Next is environmental disasters, and last is miscellaneous outages (The 2015 Disaster Recovery & Business Continuity Survey)
- 93% of companies that lost their data center for 10 days or more during a disaster, filed for bankruptcy within one year of the disaster (National Archives & Records Administration in Washington)
- Of companies that suffer catastrophic data loss: 43% never reopen and 51% close within two years (University of Texas)
- 30% of all businesses that have a major fire go out of business within a year and 70% fail within five years (Boston Computing Network, Data Loss Statistics)
- The average cost of downtime per hour is $25,000 to $50,000+ (Advertorial Infographic: Why Disaster Recovery in the Cloud Should Be in Your Plans, International Data Group, 2015)
- Companies with 100 – 2,000 employees are likely to experience costs over $20,000 in the event of a disaster(The 2015 Disaster Recovery & Business Continuity Survey)
As we finish up 2017 and head into 2018, if your small business does not have a backup and disaster recovery solution and/or plan, it is a most have resolution for your business.
What is Backup and Disaster Recovery?
Backup and Disaster Recovery or (BDR) can be defined simply as the combination of data backup and disaster recovery solutions that are designed to work together to ensure uptime, diminish data loss, and maximize productivity in the midst of an attack, natural disaster or other compromising situation.
 Five Reasons Why Small Businesses Need a BDR Plan
Five Reasons Why Small Businesses Need a BDR Plan
- Natural Disasters: This year, the United States has been hit by several natural disasters from floods to fires, earthquakes, and more which are uncontrollable circumstances which caused many businesses to experience downtime. Is your small business prepared when natural disaster strikes?
- Cyber Attacks: Cyber criminals are focusing more of their attention on businesses they feel are unprotected which makes small businesses more vulnerable. A BDR plan can limit the impact of an attack and hopefully prevent the business from losing valuable data.
- Protect Client Data: Are you a retailer or online business where you are housing client data? A BDR plan will help ensure that their information is properly stores and controlled. A security breach could ruin the reputation of your brand and business and the future of your business.
- To Err is Human: Sometimes the employees of a business can be at fault for data losses. Not only is it important to train a company’s staff properly but also have backup solutions that are available in case situations like this arise.
- Systems Can Fail: No solution is every perfect. Hardware, machines and other systems can fail. Even systems that come with 99.95 uptime guarantees may falter every once in a while.
Putting Together a Plan and Checklist
You know that you need a disaster recovery plan but do not know where to start. First, make a list of all the technologies your business uses. Then, go through each department in your company and determine what technology that department needs to function on a day-to-day basis. How long realistically can your business be down and still operational?
Identify which items in your business need the most protection. You may not need to backup your entire systems. Create a list detailing crucial data and examine their location. This information will allow you to make decisions on the frequency of backups and how much storage you may need.
Create a Schedule for your Backup and determine your storage needs. Depending on the industry of your business, you may not need to retain every backup created unless there are legal requirements which may require different regulations such as companies in the healthcare and financial industries.
What to look for in a BDR Solution?
How does a company pick the appropriate BDR solution that fits for their business? There are a few things to consider: Hardware Compatability, Scalable pricing, around-the clock support and a strong reputation. A company should do their research to find the right fit for their needs.
Zerto, one of Zunesis’ preferred partners has come up with a guide that has 10 questions that you should ask before choosing a DR solution. Download it here.
TEST TEST TEST
After implementing a backup system, it is important to routinely test your backup system. Periodically test to restore some data and be sure you can still use it. Many managed backup solutions will include test restores as part of the service.
Adjust your backup and recovery strategy as the needs of your company changes. Know what you need and how often it changes to create a strategy that protects core functions without dramatically increasing costs.
Contact Zunesis for a review of your backup and data recovery infrastructure and we can give recommendations on what will work best for the needs of your company and how to implement those solutions.
Ransomware
Ransomware is a form of Malware that, once activated, can deny access to files on smartphones, personal computers, and servers. In some forms, a Ransomware attack will go beyond denial of service; and the Cyber Criminals will threaten to publish your data. As the name suggests, Ransomware offers to unlock your files if you pay a ransom. While modern day Ransomware attacks can be traced back to 2005, the history of Ransomware goes back as far as 1989. The pace of these attacks doesn’t appear to be slowing down. In 2016, many sources had payouts approaching $1 billion by the end of the year.
 As you might imagine, having been around for such a long time, Cyber Criminals have developed several ways to launch Ransomware attacks. Within the data center, our first goal is to keep these attacks out of our systems and away from our production data. IT Professionals protect their production environments by using firewalls, anti-virus software, proper authentication practices, and end-user education, among other measures.
As you might imagine, having been around for such a long time, Cyber Criminals have developed several ways to launch Ransomware attacks. Within the data center, our first goal is to keep these attacks out of our systems and away from our production data. IT Professionals protect their production environments by using firewalls, anti-virus software, proper authentication practices, and end-user education, among other measures.
Despite these efforts, there is always the possibility that an attack is successful and systems are compromised. In the event our corporate files do become impacted by a Ransomware event, we must be able to rely on our data backups to restore systems and not be forced to pay a ransom. However, this begs an important question:
How can we be sure that our backups are protected?
This is a question that is being asked more frequently by our clients.
First, we need to acknowledge that backups are not free from the risk of being attacked by Ransomware. However, there are steps that can be taken to reduce the risk of exposure, even if the Malware has found its way into the Production infrastructure. These steps fall generally into three categories: Security, Replication, and Isolation.
Security
- Provide a dedicated host for the backup application.
- Disable network interfaces not in use on the hosts involved in performing backups.
- Restrict the number of user accounts with access to the backup application and the host onto which it is installed.
- Disable access to communications ports and protocols not needed for the backup operation (i.e., HTTP, FTP, Telnet, etc.).
- Disable accounts not used for operation of the backup process.
- Disable services not used for operation of the backup process.
- Utilize best practices for user credentials (password complexity, aging, etc.).
- Keep Security Patches up to date on the host and the backup application itself.
Replication
 Maintain at least three (3) copies of the backup files on at least two (2) different types of media and keep at least one (1) of those copies offsite. (3-2-1 Rule)
Maintain at least three (3) copies of the backup files on at least two (2) different types of media and keep at least one (1) of those copies offsite. (3-2-1 Rule)- Consider keeping a copy of your backup on tape or on spinning disk that is not connected to the network unless backups are running. The point here is to maintain an offline copy.
- If replicating between backup appliances, consider building a delay into replication to keep from immediately replicating files infected with the Ransomware. This tactic may allow you time to discover the proliferation of an attack and keep it from spreading to your replication target.
- Utilize hardware based snapshots on Production storage arrays and backup appliances (these are not usually presented to a file system and are therefore not subject to attack).
- Maintain multiple restore points using snapshots and the backup software.
Isolation
- Maintain separate hosts for the backup infrastructure.
- Utilize offline backup media (tape or disconnected disk targets).
- Utilize hardware based snapshots.
- Utilize Cloud connected backup targets.
The steps listed above are intended to provide guidelines for protecting your backup data from Ransomware. Execution of these steps is dependent on your own infrastructure, the type of backup targets you employ, the backup software you use, etc.
There are many resources available that delve into this topic in greater detail. The intent of this post is simply to make sure you are including backups in your strategy to protect the enterprise against Ransomware attacks. And, of course, Zunesis is ready to help you design a strategy that fits your needs and is right for your environment.
A flood that damages mission-critical equipment is among the worst scenarios a data center can face, offering little hope for a quick fix. On April 13, 2015, the Zunesis team received a “first responders call” from a long-term public sector customer who had the misfortune to experience a broken water main that left their main data center under 2 feet of standing water.
The call for help came at 4 p.m. on a Thursday afternoon. Zunesis joined forces with HP and immediately responded to assess the damage. By the next morning, it was clear that the data center was living on borrowed time. With 18 racks of equipment compromised, it was imperative that the team immediately instigate a full Data center fail-over. Luckily, a secondary data center had just been completed, along with plans started for a full DR site; but those plans were stalled as the organization waited for additional funding to become available.
A two-fold plan was quickly put into place to swiftly expand the new data center to capacity while keeping the damaged data center up and running. The insurance company was immediately engaged to begin the replacement exercise while Zunesis and HP jumped in to “keep the lights on” in the existing data center. Immediately needed were a large supply of extra drives; power supplies; cables; switches; and, most daunting, an emergency 120TB SAN array to move data to safety.
 By Friday morning, emails had been circulated to the highest levels of HPE and Zunesis requesting emergency assistance. Zunesis quickly moved a 3Par 7200 array from its own internal lab to the customer site and expanded an additional 100TB in an emergency drive order to migrate data. HP called in emergency supplies from all over the Americas. Extra drives, power supplies, cables, switches, and even servers arrived throughout the weekend. Within 48 hours, the teams had built up enough reserves to keep the data center live until all of the data could be migrated.
By Friday morning, emails had been circulated to the highest levels of HPE and Zunesis requesting emergency assistance. Zunesis quickly moved a 3Par 7200 array from its own internal lab to the customer site and expanded an additional 100TB in an emergency drive order to migrate data. HP called in emergency supplies from all over the Americas. Extra drives, power supplies, cables, switches, and even servers arrived throughout the weekend. Within 48 hours, the teams had built up enough reserves to keep the data center live until all of the data could be migrated.
Although all IT organizations know that it’s critical to have a solid DR plan and failover Data center in place, the reality is that the Data center spotlight is on monitoring and compliance; and the loss of a main data center is crippling. The second most common cause of catastrophic failures (after electrical) in the Data center is water leaks. Taking the following three steps can help avoid a flood disaster:
- Initial survey to ensure that the location of our data center is not in a flood plain and that the site is well protected from external water sources. Confirm that the fabric of the building is well enough designed and properly maintained to prevent the ingress of rain (even in extreme storm conditions). Check how sources of water inside the building are routed (hot and cold water storage tanks, pipe runs, waste pipes, WCs, as well as water-based fire suppression systems in the office space). Office space above a data center is almost always dangerous from a water ingress perspective.
- Protection to ensure that any water entering the data center does not have the opportunity to build up and cause a problem. If you are really worried, install drains and a sump pump under the plenum floor. Ensure that the floor space is sealed and that all cable routes through partition walls are stopped up to be air and water tight.
- Monitoring is critical in a data center – we absolutely need to be able to detect water under the plenum floor. Generally, water detection systems use a cable that runs under the floor and causes an alarm to be triggered if it comes into contact with water.
Click to find out more about our Disaster Recovery Assessments.




