Are Personal VPN Services for you?

What VPN services are a Good Fit for you?
I am certain that many people are familiar with the concept of a VPN or virtual private network. They are used to gain access to a corporate network while traveling or at home. I would assert though that few are familiar with the growing market of personal VPN providers who target non-commercial entities and individuals.
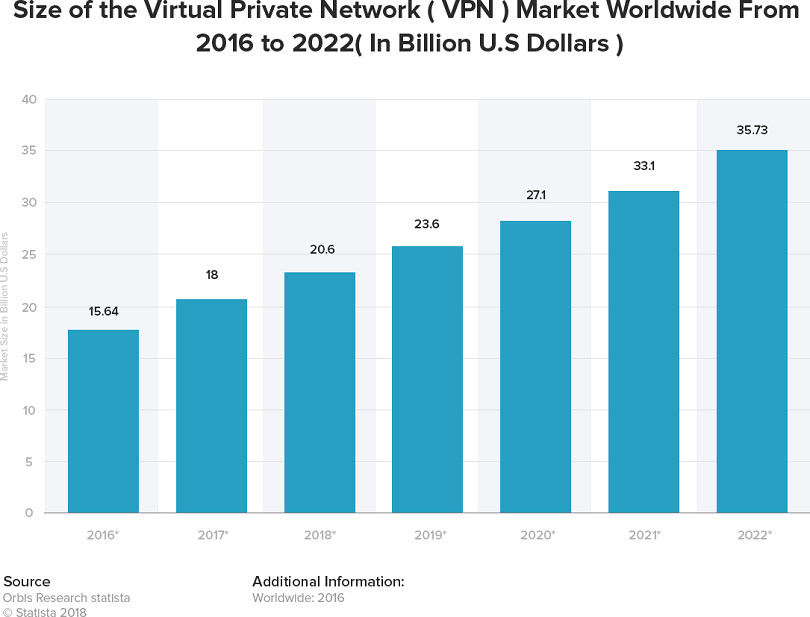
According to Orbis research Statista:
This market has grown eight billion dollars in the past five years
and is expected to grow another twelve billion in the next three years.
This emerging market has many players. Understanding which to use can be quite confusing to someone who is not well informed on the topic.
We will explore the concepts of how they differ from the often-provided corporate VPN’s. As well as discuss how to use them to protect your private information aside from how the company protects itself.
Corporate vs. Personal VPN
Most business travelers do utilize corporate VPN connections to gain access to company files and services. When the traffic is not destined to the business networks, the traffic is not tunneled back to the home office. This configuration is called split tunneling.
It is a very common configuration. Network engineers configure this so that users will not saturate the VPN concentrators with YouTube, Netflix and other non-business-related traffic. Additionally, as business travelers it is incumbent on us to use company assets such as bandwidth in a manner which is in line with our companies’ policies.
How do the personal VPN services work?
Most if not all personal VPNs use a client-based software to encapsulate and encrypt the traffic. This makes it very hard to unscramble if someone is capturing data from an open network.
The other mechanism used is to proxy the traffic to a third party where it is then sent to the eventual destination. The proxy or redirect mechanism ensures that the transmitted information doesn’t contain the public IP of the coffee shop or public network but the source IP address of the proxy service. This is important when connecting to financial institutions that monitor the public IP address that you normally connect from.
If for some reason another person attempts to connect to your bank account through the bank’s web portal, the bank would notice that it is not the normal public IP address that you would typically connect from and disallow the login attempt.
Who are they for?
Firstly, who should use a personal VPN? The answer is anyone who regularly uses free and open Wi-Fi at public places. Anytime you connect to the coffee shop Wi-Fi or to a hotels guest network connection, you are often at risk of someone intercepting the unencrypted traffic you are sending and receiving. This vulnerability has existed for many years and is called a, “man in the middle attack”.
This sort of intrusion used to be carried out by very skilled hackers but these days the attack is very well documented. Toolkits to exploit these common scenarios are being used by very unskilled characters.
Personal VPNs circumvent the vulnerabilities of open networks by using encapsulation and traffic proxying so that the connection is more secure and free from prying eyes.
Good rules to live by regarding when you should use a VPN include:
- Are you logging in to a private or personal account of any kind?
- Are you transmitting information that is proprietary?
- Is there personal or customer information being transmitted?
- Is banking or financial information being received?
If any of these conditions exist, I would recommend using a personal VPN to protect yourself. The many protective and anonymizing mechanisms that the VPNs employ would allow you to safely transmit and receive any data without the risk of intrusion.
Current major players in this market
I will not make any direct recommendation since at Zunesis do not sell these products directly. We can help with the implementation of them if requested. I would recommend that you find a solution that does satisfy the conditions I have covered.
This article from PCMag.com gives a great overview of how VPNs work and how each VPN company compared to the others.
How can Zunesis help?
At Zunesis, our expertise and offerings focus on corporate VPNs and other firewall services. We find it equally important that our clients and partners understand the risks involved when not utilizing some protective measures when they connect to open public Wi-Fi systems.
We have all heard of the unlucky Hollywood stars who have had their personal accounts targeted or hacked at great expense to themselves. Reputations are very important in business and in private life. Remember that the weakest link is not the traffic we monitor, it is the traffic we do not.
Categories
Search
Blog Categories
Related Resources
Archives
- July 2024
- June 2024
- May 2024
- April 2024
- March 2024
- January 2024
- October 2023
- September 2023
- August 2023
- July 2023
- June 2023
- May 2023
- April 2023
- March 2023
- February 2023
- January 2023
- October 2022
- July 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- August 2021
- July 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- August 2019
- July 2019
- June 2019
- May 2019
- April 2019
- March 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- May 2018
- April 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- August 2017
- July 2017
- June 2017
- May 2017
- April 2017
- March 2017
- February 2017
- January 2017
- December 2016
- November 2016
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- May 2016
- March 2016
- February 2016
- January 2016
- December 2015
- October 2015
- September 2015
- August 2015
- July 2015
- June 2015
- May 2015
- April 2015
- March 2015
- February 2015
- January 2014
- February 2013




